1138:
42:
2084:, who uses it as the default time program in their distributions. Being written from scratch, chrony has a simpler codebase allowing for better security and lower resource consumption. It does not however compromise on accuracy, instead syncing faster and better than the reference ntpd in many circumstances. It is versatile enough for ordinary computers, which are unstable, go into sleep mode or have intermittent connection to the Internet. It is also designed for virtual machines, a more unstable environment.
5502:
2028:, an NTPv3/SNTPv4 implementation with a focus on security and encompassing a privilege separated design. Whilst it is aimed more closely at the simpler generic needs of OpenBSD users, it also includes some protocol security improvements while still being compatible with existing NTP servers. The simpler code base sacrifices accuracy, deemed unnecessary in this use case. A portable version is available in Linux package repositories.
2063:
1513:
1930:
2044:. The fork point was in June 2015 and was in response to a series of compromises in 2014. The first production release shipped in October 2017. Between removal of unsafe features, removal of support for obsolete hardware, and removal of support for obsolete Unix variants, NTPsec has been able to pare away 75% of the original codebase, making the remainder easier to
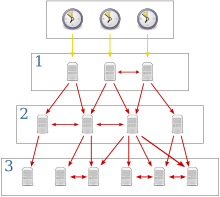
1157:+ 1. The number represents the distance from the reference clock and is used to prevent cyclical dependencies in the hierarchy. Stratum is not always an indication of quality or reliability; it is common to find stratum 3 time sources that are higher quality than other stratum 2 time sources. A brief description of strata 0, 1, 2 and 3 is provided below.
593:
1122:
1946:, along with the protocol, has been continuously developed for over 20 years. Backwards compatibility has been maintained as new features have been added. It contains several sensitive algorithms, especially to discipline the clock, that can misbehave when synchronized to servers that use different algorithms. The software has been
2296:. The main improvement over previous attempts is that a separate "key establishment" server handles the heavy asymmetric cryptography, which needs to be done only once. If the server goes down, previous users would still be able to fetch time without fear of MITM. NTS is currently supported by several time servers, including
2001:, the NTP provider for W32Time became compatible with a significant subset of NTPv3. Microsoft states that W32Time cannot reliably maintain time synchronization with one second accuracy. If higher accuracy is desired, Microsoft recommends using a newer version of Windows or different NTP implementation.
1503:
which resolves rollover ambiguity in most cases. According to Mills, "The 64-bit value for the fraction is enough to resolve the amount of time it takes a photon to pass an electron at the speed of light. The 64-bit second value is enough to provide unambiguous time representation until the universe
1468:
For servers on stratum 2 and below, the refid is an encoded form of the upstream time server's IP address. For IPv4, this is simply the 32-bit address; for IPv6, it would be the first 32 bits of the MD5 hash of the source address. Refids serve to detect and prevent timing loops to the first degree.
3637:
Primary servers and clients complying with a subset of NTP, called the Simple
Network Time Protocol (SNTPv4) , do not need to implement the mitigation algorithms The fully developed NTPv4 implementation is intended for servers with multiple upstream servers and multiple downstream servers Other
1112:
over extended periods of time is needed. The topology becomes essentially the same as with the Time
Protocol, as only one server is used. In 1996, SNTP was updated to SNTPv4 with some features of the then-in-development NTPv4. The current version of SNTPv4 is merged into the main NTPv4 standard in
3410:
The clock-selection procedure was modified to remove the first of the two sorting/discarding steps and replace with an algorithm first proposed by
Marzullo and later incorporated in the Digital Time Service. These changes do not significantly affect the ordinary operation of or compatibility with
2171:
An alternative implementation, called leap smearing, consists in introducing the leap second incrementally during a period of 24 hours, from noon to noon in UTC time. This implementation is used by Google (both internally and on their public NTP servers), Amazon AWS, and
Facebook. Chrony supports
2194:
Because adjusting system time is generally a privileged operation, part or all of NTP code has to be run with some privileges in order to support its core functionality. Only a few other security problems have been identified in the reference implementation of the NTP codebase, but those that
1472:
The refid field is filled with status words in the case of kiss-o'-death (KoD) packets, which tell the client to stop sending requests so that the server can rest. Some examples are INIT (initialization), STEP (step time change), and RATE (client requesting too fast). The program output may
2087:
Chrony has been evaluated as "trustworthy", with only a few incidents. It is able to achieve improved precision on LAN connections, using hardware timestamping on the network adapter. Support for
Network Time Security (NTS) was added on version 4.0. chrony is available under
1213:
These are computers that are synchronized over a network to stratum 1 servers. Often a stratum 2 computer queries several stratum 1 servers. Stratum 2 computers may also peer with other stratum 2 computers to provide more stable and robust time for all devices in the peer
2258:, the server responds with a much larger reply that allows an attacker to substantially increase the amount of data being sent to the target. To avoid participating in an attack, NTP server software can be upgraded or servers can be configured to ignore external queries.
2206:
was concerned enough about this vulnerability that it used its auto-update capability for the first time. On systems using the reference implementation, which is running with root user's credential, this could allow unlimited access. Some other implementations, such as
4944:
4924:
1962:
under
Windows. Reference clocks are supported and their offsets are filtered and analysed in the same way as remote servers, although they are usually polled more frequently. This implementation was audited in 2017, finding 14 potential security issues.
2195:
appeared in 2009 were cause for significant concern. The protocol has been undergoing revision and review throughout its history. The codebase for the reference implementation has undergone security audits from several sources for several years.
3524:
2048:. A 2017 audit of the code showed eight security issues, including two that were not present in the original reference implementation, but NTPsec did not suffer from eight other issues that remained in the reference implementation.
2167:
that query the system time cause it to increase by a tiny amount, preserving the order of events. If a negative leap second should ever become necessary, it would be deleted with the sequence 23:59:58, 00:00:00, skipping 23:59:59.
2230:
from a man-in-the-middle attack can be used to alter clocks on client computers and allow a number of attacks based on bypassing of cryptographic key expiration. Some of the services affected by fake NTP messages identified are
2214:
A 2017 security audit of three NTP implementations, conducted on behalf of the Linux
Foundation's Core Infrastructure Initiative, suggested that both NTP and NTPsec were more problematic than Chrony from a security standpoint.
1088:). Mills had mentioned plans for a "NTPv5" on his page, but one was never published. An unrelated draft termed "NTPv5" by M. Lichvar of chrony was initiated in 2020 and includes security, accuracy, and scaling changes.
1914:
exists of half the difference between the forward and backward travel times. A number of approaches have been proposed to measure asymmetry, but among practical implementations only chrony seems to have one included.
3658:
Programs from the linuxptp package can be used in a combination with an NTP daemon. A PTP clock on a NIC is synchronized by ptp4l and is used as a reference clock by chronyd or ntpd for synchronization of the system
4941:
4921:
1192:
and timestamp on a connected computer. Stratum 0 devices are also known as reference clocks. NTP servers cannot advertise themselves as stratum 0. A stratum field set to 0 in NTP packet indicates an unspecified
1113:
2010. SNTP is fully interoperable with NTP since it does not define a new protocol. However, the simple algorithms provide times of reduced accuracy and thus it is inadvisable to sync time from an SNTP source.
4142:
1628:
4908:
1220:
These are computers that are synchronized to stratum 2 servers. They employ the same algorithms for peering and data sampling as stratum 2, and can themselves act as servers for stratum 4 computers, and so
1079:
The protocol has significantly progressed since NTPv4. As of 2022, three RFC documents describing updates to the protocol have been published, not counting the numerous peripheral standards such as NTS
3514:
3492:
1910:
Accurate synchronization is achieved when both the incoming and outgoing routes between the client and the server have symmetrical nominal delay. If the routes do not have a common nominal delay, a
1721:
1903:
are discarded and an estimate of time offset is derived from the best three remaining candidates. The clock frequency is then adjusted to reduce the offset gradually ("discipline"), creating a
5158:
2278:
offers useful authentication, but is not practical for a busy server. Autokey was also later found to suffer from several design flaws, with no correction published, save for a change in the
3846:
1882:
1822:
1990:. The network time server in Windows 2000 Server (and Windows XP) does not implement NTP disciplined synchronization, only locally disciplined synchronization with NTP/SNTP correction.
5052:
4839:
4862:
5521:
4355:
4762:
4113:
442:
3684:
2159:, an attached reference clock, or a remote server. Although the NTP clock is actually halted during the event, because of the requirement that time must appear to be
4134:
993:
modes. In 1991, the NTPv1 architecture, protocol and algorithms were brought to the attention of a wider engineering community with the publication of an article by
2222:
unless packets are cryptographically signed for authentication. The computational overhead involved can make this impractical on busy servers, particularly during
894:
in New York. The technology was later described in the 1981 Internet
Engineering Note (IEN) 173 and a public protocol was developed from it that was documented in
5213:
4961:
4380:
Starting with Red Hat
Enterprise Linux 7.0 (and now in Red Hat Enterprise Linux 6.8) a more versatile NTP implementation is also provided via the chrony package
1225:
The upper limit for stratum is 15; stratum 16 is used to indicate that a device is unsynchronized. The NTP algorithms on each computer interact to construct a
3482:
202:
1056:
In subsequent years, as new features were added and algorithm improvements were made, it became apparent that a new protocol version was required. In 2010,
4392:
1499:
NTPv4 introduces a 128-bit date format: 64 bits for the second and 64 bits for the fractional-second. The most-significant 32 bits of this format is the
1537:
4250:
4197:
It implements the Simple
Network Time Protocol version 4, as described in RFC 5905, and the Network Time Protocol version 3, as described in RFC 1305.
5150:
2180:
configurations, but such use is not to be mixed with a public NTP pool as leap smear is non-standard and will throw off client calculation in a mix.
3842:
1236:
In addition to stratum, the protocol is able to identify the synchronization source for each server in terms of a reference identifier (refid).
5580:
4520:
Withstanding eleven full days of on-remote testing in August of 2017 means that Chrony is robust, strong, and developed with security in mind.
3354:
1203:
is synchronized to within a few microseconds of their attached stratum 0 devices. Stratum 1 servers may peer with other stratum 1 servers for
5394:
4307:
4051:
3997:
3815:
3433:
2449:
2382:
435:
162:
5059:
1637:
5570:
3747:
Refid codes are used in kiss-o'-death (KoD) packets, the reference identifier field in ntpq and ntpmon billboard displays and log messages.
2247:
2089:
565:, where clients passively listen to time updates after an initial round-trip calibrating exchange. NTP supplies a warning of any impending
292:
287:
257:
4835:
3821:
1026:
scheme which have both survived into NTPv4, along with the bulk of the algorithm. However the design of NTPv2 was criticized for lacking
4026:
999:
117:
4866:
2518:
2455:
364:
307:
232:
3879:
Gotoh, T.; Imamura, K.; Kaneko, A. (2002). "Improvement of NTP time offset under the asymmetric network with double packets method".
4813:
4493:
4470:
4330:
3896:
374:
344:
4210:
4164:
1827:
1767:
4891:
3969:
3280:
428:
359:
152:
5517:
5285:
5084:
4367:
3603:
3232:
3178:
2587:
1126:
479:
data networks. In operation since before 1985, NTP is one of the oldest Internet protocols in current use. NTP was designed by
5025:
4754:
3717:
1488:
timestamps used by NTP consist of a 32-bit part for seconds and a 32-bit part for fractional second, giving a time scale that
929:). More complete synchronization systems, although lacking NTP's data analysis and clock disciplining algorithms, include the
3680:
1274:
1027:
177:
167:
2012:, W32Time can be configured to reach time accuracy of 1 s, 50 ms or 1 ms under certain specified operating conditions.
1532:
is positive or negative (client time > server time) difference in absolute time between the two clocks. It is defined by
5184:
2543:
4644:
4105:
1473:
additionally use codes not transmitted in the packet to indicate error, such as XFAC to indicate a network disconnection.
297:
277:
227:
5120:
902:. The technology was first deployed in a local area network as part of the Hello routing protocol and implemented in the
3782:
3308:
2486:
2211:, have smaller code base and adopted other mitigation measures like privilege separation, are not subject to this flaw.
891:
217:
212:
207:
5205:
4965:
3461:
5575:
4711:
4670:
4627:
So in effect, systemd-timesyncd became the default NTP daemon in Debian in bookworm, which I find somewhat surprising.
3932:
This directive enables hardware timestamping of NTP packets sent to and received from the specified network interface.
2279:
2189:
2037:
1979:
include the Windows Time service (W32Time), which has the ability to synchronize the computer clock to an NTP server.
848:
394:
354:
222:
4083:
2045:
1521:
1149:
and is assigned a number starting with zero for the reference clock at the top. A server synchronized to a stratum
499:
4565:
545:
relationships where both peers consider the other to be a potential time source. Implementations send and receive
4240:
2332:
1264:
558:
1137:
969:
In 1988, a much more complete specification of the NTPv1 protocol, with associated algorithms, was published in
41:
4596:
3638:
than these considerations, NTP and SNTP servers and clients are completely interoperable and can be intermixed
2293:
2289:
2255:
2232:
2219:
1943:
1130:
1109:
247:
187:
4400:
1986:
version 5 authentication protocol, which required time to be within 5 minutes of the correct value to prevent
1053:
that helps choose the best server where several candidates appear to disagree. Broadcast mode was introduced.
538:
4693:
2361:
2240:
1181:
1108:) was defined to fill this niche. The SNTPv3 standard describes a way to use NTPv3, such that no storage of
1031:
507:
414:
404:
197:
112:
96:
4428:
1476:
The IANA maintains a registry for refid source names and KoD codes. Informal assignments can still appear.
3866:
1485:
1065:
550:
503:
484:
282:
132:
5531:
3649:
2199:
2041:
1064:
was published containing a proposed specification for NTPv4. Following the retirement of Mills from the
958:. Despite the relatively slow computers and networks available at the time, accuracy of better than 100
946:
In 1985, NTP version 0 (NTPv0) was implemented in both Fuzzball and Unix, and the NTP packet header and
468:
409:
4047:
3993:
3944:
3759:
1145:
NTP uses a hierarchical, semi-layered system of time sources. Each level of this hierarchy is termed a
3425:
Computer Network Time Synchronization: The Network Time Protocol on Earth and in Space, Second Edition
2097:
5476:
5449:
5307:
5005:
3625:
3398:
3254:
3200:
3143:
3094:
3037:
2985:
2933:
2888:
2832:
2783:
2730:
2673:
2609:
1492:
every 2 seconds (136 years) and a theoretical resolution of 2 seconds (233 picoseconds). NTP uses an
883:
608:
574:
192:
5235:
3916:
2093:
3575:
2251:
2164:
2009:
1994:
1983:
1396:
1384:
1338:
581:
464:
4532:
4275:
3330:
2160:
2156:
1951:
531:
523:
399:
127:
5543:
5507:
5328:
986:
2307:
identity, known as MS-SNTP. This system is implemented in the reference ntpd and chrony, using
5299:
4303:
4018:
3892:
3811:
3805:
3617:
3429:
3423:
3246:
3192:
3135:
2601:
2445:
2223:
2115:
1972:
1326:
1023:
327:
103:
4297:
2439:
1933:
The NTP management protocol utility ntpq being used to query the state of a stratum 2 server.
1233:, to minimize the accumulated round-trip delay to the stratum 1 servers for all the clients.
1226:
906:, an experimental operating system used in network prototyping, where it ran for many years.
5466:
5439:
5289:
4995:
3884:
3607:
3411:
various versions of NTP, but they do provide the basis for formal statements of correctness.
3388:
3346:
3329:
3236:
3182:
3125:
3084:
3027:
2975:
2923:
2878:
2822:
2773:
2720:
2663:
2591:
2514:
2403:
2308:
2123:
1525:
1489:
1185:
1081:
1057:
1038:
1007:
978:
970:
951:
947:
922:
910:
895:
52:
20:
5352:
4948:
4928:
4895:
3519:
3487:
2227:
2067:
1959:
1911:
1373:
1050:
962:
was usually obtained on Atlantic spanning links, with accuracy of tens of milliseconds on
903:
515:
476:
472:
268:
4809:
4504:
4462:
4323:
5536:
4218:
5501:
5376:
5083:
Aanchal Malhotra; Isaac E. Cohen; Erik Brakke & Sharon Goldberg (20 October 2015).
4076:"Support boundary to configure the Windows Time service for high accuracy environments"
3593:
3378:
3070:
3017:
2965:
2913:
2868:
2812:
2763:
2710:
2653:
2577:
2320:
2304:
994:
918:
597:
480:
318:
66:
4888:
3962:
3286:
2062:
5564:
4758:
4245:
2338:
2326:
2267:
1998:
1987:
1904:
1230:
1141:
Yellow arrows indicate a direct connection; red arrows indicate a network connection.
1097:
1030:
by the DTSS community, and the clock selection procedure was modified to incorporate
1015:
914:
24:
5095:
2266:
NTP itself includes support for authenticating servers to clients. NTPv3 supports a
939:, which uses an election algorithm to appoint a server for all the clients; and the
3709:
1976:
1204:
1165:
1046:
990:
562:
542:
237:
3738:
5180:
5029:
3549:
1899:
are passed through filters and subjected to statistical analysis ("mitigation").
5479:
5460:
5452:
5433:
5310:
5279:
5008:
4989:
3628:
3597:
3401:
3382:
3266:
3257:
3226:
3212:
3203:
3172:
3155:
3146:
3115:
3057:
3053:
3049:
3040:
3021:
3001:
2997:
2988:
2969:
2949:
2945:
2936:
2917:
2900:
2891:
2872:
2852:
2844:
2835:
2816:
2799:
2795:
2786:
2767:
2750:
2746:
2742:
2697:
2693:
2685:
2676:
2657:
2637:
2633:
2629:
2625:
2621:
2612:
2581:
2539:
2399:
2352: – Dynamic collection of networked computers providing time synchronization
2152:
1200:
1177:
1100:, some use-cases nevertheless found the full protocol too complicated. In 1992,
1085:
1069:
1061:
1042:
1011:
974:
959:
566:
554:
511:
495:
491:
56:
5512:
5408:
3097:
3074:
2848:
2733:
2714:
2689:
2329: – Set of clocks that are automatically synchronized to show the same time
1950:
to almost every computing platform, including personal computers. It runs as a
982:
977:. It drew on the experimental results and clock filter algorithm documented in
955:
926:
909:
Other related network tools were available both then and now. They include the
899:
518:. NTP can usually maintain time to within tens of milliseconds over the public
5128:
3888:
3384:
Network Time Protocol (Version 3) - Specification, Implementation and Analysis
2659:
Network Time Protocol (Version 3) - Specification, Implementation and Analysis
2297:
2271:
2203:
2071:
2005:
1496:
of January 1, 1900. Therefore, the first rollover occurs on February 7, 2036.
1045:
defined NTPv3. The RFC included an analysis of all sources of error, from the
1019:
385:
5303:
5278:
D. Franke; D. Sibold; K. Teichel; M. Dansarie; R. Sundblad (September 2020).
4640:
3843:"A look at the Year 2036/2038 problems and time proofness in various systems"
3778:
3621:
3455:
3300:
3250:
3196:
3139:
2605:
2482:
950:
and offset calculations, which have persisted into NTPv4, were documented in
4109:
4079:
2303:
Microsoft also has an approach to authenticate NTPv3/SNTPv4 packets using a
1189:
943:(DTSS), which uses a hierarchy of servers similar to the NTP stratum model.
570:
546:
4666:
4618:
4413:
In sum, the Chrony NTP software stands solid and can be seen as trustworthy
1929:
1764:
To derive the expression for the offset, note that for the request packet,
1512:
886:
technology was used in what was possibly the first public demonstration of
5435:
Definitions of Managed Objects for Network Time Protocol Version 4 (NTPv4)
5395:"[MS-SNTP]: Network Time Protocol (NTP) Authentication Extensions"
3883:. Conference on Precision Electromagnetic Measurements. pp. 448–449.
5151:"New DoS attacks taking down game sites deliver crippling 100Gbps floods"
4075:
2395:
2349:
2208:
2025:
1462:(Unofficial) Google Refid used by Google NTP servers as time4.google.com
963:
887:
519:
4784:
4449:
The software is supported on Linux, FreeBSD, NetBSD, macOS, and Solaris.
4397:
Core Infrastructure Initiative, a Linux Foundation Collaborative Project
4363:
2355:
2135:
2122:
in 2014 and abandoned in 2015. The implementation was sponsored by the
2119:
2081:
2021:
1900:
1362:
592:
527:
4557:
3881:
Conference Digest Conference on Precision Electromagnetic Measurements
3599:
Network Time Protocol Version 4: Protocol and Algorithms Specification
3350:
2583:
Network Time Protocol Version 4: Protocol and Algorithms Specification
5471:
5444:
5294:
5000:
4211:"FAQ 6.12.1: 'But OpenNTPD isn't as accurate as the ntp.org daemon!'"
3612:
3393:
3241:
3187:
3130:
3089:
3032:
2980:
2928:
2883:
2827:
2778:
2725:
2668:
2596:
2236:
2139:
2077:
2057:
1947:
1524:
one or more NTP servers. The client must compute its time offset and
348:
242:
141:
121:
4533:"chrony/chrony.git - Official Git repository for the Chrony project"
3023:
Simple Network Time Protocol (SNTP) Version 4 for IPv4, IPv6 and OSI
2971:
Simple Network Time Protocol (SNTP) Version 4 for IPv4, IPv6 and OSI
1121:
4588:
4399:. Core Infrastructure Initiative. 27 September 2017. Archived from
1072:
project led by Harlan Stenn. On the IANA side, a ntp (network time
1022:
to describe its operation. It introduced a management protocol and
5545:
A Brief History of NTP Time: Confessions of an Internet Timekeeper
4836:"Apple automatically patches Macs to fix severe NTP security flaw"
4810:"Network Time Protocol Vulnerabilities (Update C) | ICS-CERT"
4729:
2818:
Network Time Protocol (Version 2) Specification and Implementation
2769:
Network Time Protocol (Version 1) Specification and Implementation
2275:
2061:
1928:
1511:
1493:
1314:
1136:
1120:
935:
591:
369:
147:
1751:
is the server's timestamp of the response packet transmission and
1623:{\displaystyle \theta ={\frac {(t_{1}-t_{0})+(t_{2}-t_{3})}{2}},}
890:
services running over a trans-Atlantic satellite network, at the
4436:
3121:
3080:
2441:
Computer Network Time Synchronization: The Network Time Protocol
2344:
2323: – Measure of frequency stability in clocks and oscillators
1955:
1924:
1419:
1408:
1302:
1169:
930:
337:
332:
302:
252:
172:
137:
28:
4755:"Cisco IOS Software Network Time Protocol Packet Vulnerability"
4241:"NTPsec: a Secure, Hardened NTP Implementation | Linux Journal"
4188:
3869:
Digital Systems Seminar presentation by David Mills, 2006-04-26
2398:(light would travel 16.26 picometers, or approximately 0.31 ×
1350:
1207:
and backup. They are also referred to as primary time servers.
1173:
603:
157:
4503:. wiki.mozilla.org, AKA MozillaWiki or WikiMO. Archived from
2040:
of the reference implementation that has been systematically
1733:
is the client's timestamp of the request packet transmission,
1068:, the reference implementation is currently maintained as an
1049:
down to the final client, which enabled the calculation of a
5526:
1760:
is the client's timestamp of the response packet reception.
917:
protocols for recording the time of events, as well as the
5206:"DRDoS / Amplification Attack using ntpdc monlist command"
4964:. The Linux Foundation. September 28, 2017. Archived from
3804:
W. Richard Stevens; Bill Fenner; Andrew M. Rudoff (2004).
3331:"Internet Time Synchronization: The Network Time Protocol"
2483:"Executive Summary: Computer Network Time Synchronization"
2341: – Standard formats for transferring time information
1982:
W32Time was originally implemented for the purpose of the
1742:
is the server's timestamp of the request packet reception,
522:, and can achieve better than one millisecond accuracy in
4694:"Building a more accurate time service at Facebook scale"
4589:"Network time synchronization software, NTPD replacement"
3174:
Message Authentication Code for the Network Time Protocol
2381:
Telecommunication systems use a different definition for
2250:. A small query is sent to an NTP server with the return
2243:(BGP), Bitcoin and a number of persistent login schemes.
2080:
is an independent NTP implementation mainly sponsored by
4272:"The Secure Network Time Protocol (NTPsec) Distribution"
3117:
Network Time Protocol Version 4 (NTPv4) Extension Fields
1076:) work group is in charge of reviewing proposed drafts.
5495:
5377:"Network Time Security · Cloudflare Time Services docs"
5254:
4356:"Combining PTP with NTP to Get the Best of Both Worlds"
3650:"Combining PTP with NTP to Get the Best of Both Worlds"
3596:; J. Burbank; W. Kasch (August 2010). J. Martin (ed.).
2580:; J. Burbank; W. Kasch (August 2010). J. Martin (ed.).
2358: – A computer program to synchronize computer time
16:
Standard protocol for synchronizing time across devices
5181:"Huge Hack 'Ugly Sign of Future' for Internet Threats"
4991:
Network Time Protocol Version 4: Autokey Specification
1716:{\displaystyle \delta ={(t_{3}-t_{0})-(t_{2}-t_{1})},}
4962:"CII Audit Identifies Most Secure NTP Implementation"
4271:
1830:
1770:
1640:
1540:
1164:
These are high-precision timekeeping devices such as
5462:
Network Time Protocol (NTP) Server Option for DHCPv6
580:
The current protocol is version 4 (NTPv4), which is
514:
and is designed to mitigate the effects of variable
5537:
Current NIST leap seconds file compatible with ntpd
5281:
Network Time Security for the Network Time Protocol
3681:"Network Time Protocol: Best Practices White Paper"
3228:
Network Time Protocol Version 4: Port Randomization
2142:
since version "bookworm" and the downstream Ubuntu.
2066:chronyc, showing sources and activity information.
1184:-synchronized clock. They generate a very accurate
73:
62:
48:
2542:. The Internet Assigned Numbers Authority (IANA).
1876:
1816:
1715:
1622:
2274:system known as "autokey" in NTPv4 adapted from
2155:event, ntpd receives notification from either a
1353:Fukushima, JP 40 kHz, Saga, JP 60 kHz
1240:Common time reference identifiers (refid) codes
537:The protocol is usually described in terms of a
2239:, various caching schemes (such as DNS cache),
3945:"sourcestats.c, function estimate_asymmetry()"
3810:. Addison-Wesley Professional. pp. 582–.
3483:"NTP Needs Money: Is A Foundation The Answer?"
2874:Type of Service in the Internet Protocol Suite
4863:"NTP The Latest Open Source Security Problem"
4619:"Switching from OpenNTPd to Chrony - anarcat"
3457:Network Time Synchronization Research Project
2364: – Network time synchronization protocol
1877:{\displaystyle t_{3}+\theta -\delta /2=t_{2}}
1817:{\displaystyle t_{0}+\theta +\delta /2=t_{1}}
436:
8:
3544:
3542:
3225:F. Gont; G. Gont; M. Lichvar (August 2021).
2335: – Time standard based on atomic clocks
2270:mode, which is not useful against MITM. The
2202:exploit was discovered and patched in 2014.
1329:Prangins, HB 75 kHz (ceased operation)
34:
4070:
4068:
2433:
2431:
2429:
2427:
2425:
2423:
1256:Geosynchronous Orbit Environment Satellite
1014:was published defining NTPv2 by means of a
569:adjustment, but no information about local
5500:
5053:"Bypassing HTTP Strict Transport Security"
3994:"Windows Time Service Technical Reference"
3166:
3164:
3012:
3010:
2960:
2958:
2863:
2861:
1888:yields the definition of the time offset.
1238:
985:and was the first version to describe the
443:
429:
92:
40:
33:
5470:
5443:
5293:
4999:
4165:"Support boundary for high-accuracy time"
3611:
3550:"Network Time Protocols (ntp): Documents"
3392:
3240:
3186:
3129:
3088:
3031:
2979:
2927:
2882:
2826:
2777:
2724:
2667:
2648:
2646:
2595:
2572:
2570:
2568:
2566:
2564:
2562:
2560:
2477:
2475:
2473:
2254:to be the target address. Similar to the
1868:
1853:
1835:
1829:
1808:
1793:
1775:
1769:
1700:
1687:
1668:
1655:
1647:
1639:
1602:
1589:
1570:
1557:
1547:
1539:
1446:German PTB time standard telephone modem
534:can cause errors of 100 ms or more.
5329:"Setting up NTS-Secured NTP with NTPsec"
5020:
5018:
4984:
4982:
4423:
4421:
3910:
3908:
3760:"Network Time Protocol (NTP) Parameters"
3704:
3702:
3449:
3447:
3445:
2300:. It is supported by NTPSec and chrony.
2288:(NTS) is a secure version of NTPv4 with
494:participating computers to within a few
5234:Dieter Sibold; Stephen Röttger (2012).
3915:Lichvar, Miroslav (18 September 2018).
2419:
2374:
2096:in 1997 and is currently maintained by
384:
317:
267:
102:
95:
69:, Harlan Stenn, Network Time Foundation
5508:Official Stratum One Time Servers list
4209:The OpenBSD Project (21 August 2006).
4019:"Windows Time Service page at NTP.org"
3171:A. Malhotra; S. Goldberg (June 2019).
2444:. Taylor & Francis. pp. 12–.
5121:"Attacking the Network Time Protocol"
5085:"Attacking the Network Time Protocol"
4712:"chrony – Frequently Asked Questions"
4647:from the original on 7 September 2013
4568:from the original on 20 December 2019
4050:. technet.microsoft.com. 2010-03-12.
3996:. technet.microsoft.com. 2011-08-17.
3574:Lichvar, Miroslav (6 December 2022).
3464:from the original on 23 December 2014
2509:
2507:
2505:
2503:
2248:distributed denial of service attacks
7:
5518:Microsft Windows accurate time guide
4861:Fairhead, Harry (23 December 2014).
4641:"The NTP Timescale and Leap Seconds"
4558:"20140926 – Playing with time again"
4433:TuxFamily, a non-profit organization
4106:"High Accuracy W32time Requirements"
4048:"How the Windows Time Service Works"
3785:from the original on 26 October 2016
3515:"NTP's Fate Hinges On 'Father Time'"
2090:GNU General Public License version 2
941:Digital Time Synchronization Service
857:
838:
822:
806:
790:
774:
5409:"Comparison of NTP implementations"
4842:from the original on April 15, 2015
4834:Cunningham, Andrew (Dec 23, 2014).
4135:"Windows Server 2016 Accurate Time"
3687:from the original on 1 October 2013
3527:from the original on April 10, 2015
3495:from the original on April 10, 2015
3422:David L. Mills (15 November 2010).
3339:IEEE Transactions on Communications
3282:Time Synchronization in DCNET Hosts
3114:T. Mizrahi; D. Mayer (March 2016).
2919:Simple Network Time Protocol (SNTP)
2438:David L. Mills (12 December 2010).
1454:(Informal) Multi Reference Sources
1305:Fort Collins, Colorado 60 kHz
1096:As NTP replaced the use of the old
1000:IEEE Transactions on Communications
526:under ideal conditions. Asymmetric
5237:Analysis of NTP's Autokey Protocol
4599:from the original on 2 August 2015
4354:Lichvar, Miroslav (20 July 2016).
4296:Liska, Allan (December 10, 2016).
2218:NTP servers can be susceptible to
1293:Inter-Range Instrumentation Group
921:messages and IP Timestamp option (
14:
4765:from the original on 11 June 2020
4692:Obleukhov, Oleg (18 March 2020).
4673:from the original on 4 April 2019
4593:ntimed git repository README file
4473:from the original on 29 June 2019
4299:NTP Security: A Quick-Start Guide
3739:"Event Messages and Status Words"
3576:"Network Time Protocol Version 5"
2458:from the original on 18 July 2014
4492:Heiderich, Mario (August 2017).
4189:"ntpd(8) - OpenBSD manual pages"
5286:Internet Engineering Task Force
5216:from the original on 2014-03-30
5187:from the original on 2014-02-11
5161:from the original on 2014-01-24
4816:from the original on 2014-12-20
4494:"Pentest-Report Chrony 08.2017"
4336:from the original on 2019-07-04
4324:"Pentest-Report NTPsec 01.2017"
4278:from the original on 2019-01-13
4253:from the original on 2024-01-26
4239:Raymond, Eric S. (2017-03-30).
4145:from the original on 2016-12-02
4116:from the original on 2012-10-17
4086:from the original on 2009-01-12
4054:from the original on 2011-09-24
4029:from the original on 2017-05-14
4000:from the original on 2011-09-06
3975:from the original on 2018-12-01
3849:from the original on 2018-07-21
3824:from the original on 2019-03-30
3779:"The NTP Era and Era Numbering"
3720:from the original on 2018-11-12
3604:Internet Engineering Task Force
3360:from the original on 2016-06-10
3328:David L. Mills (October 1991).
3311:from the original on 2011-07-22
3279:D.L. Mills (25 February 1981),
3233:Internet Engineering Task Force
3179:Internet Engineering Task Force
2588:Internet Engineering Task Force
2546:from the original on 2001-06-04
2521:from the original on 2011-09-06
2489:from the original on 2011-11-02
1520:A typical NTP client regularly
1508:Clock synchronization algorithm
541:, but can as easily be used in
4942:NVD NIST Product Search Chrony
4922:NVD NIST Product Search NTPsec
4865:. I Programmer. Archived from
4667:"Google Developers Leap Smear"
3777:David L. Mills (12 May 2012).
2134:is the SNTP client built into
1706:
1680:
1674:
1648:
1608:
1582:
1576:
1550:
1317:Mainflingen, DE 77.5 kHz
471:between computer systems over
1:
5581:Network time-related software
5327:Langer, Martin (2019-12-05).
4360:Red Hat Enterprise Linux Blog
1824:and for the response packet,
1133:is a stratum 0 source for NTP
3963:"Pentest-Report NTP 01.2017"
3305:UNIX System Manager's Manual
3076:DCNET Internet Clock Service
2311:for the domain connection.
1374:MF Radio Allouis, FR 162 kHz
1102:Simple Network Time Protocol
1024:cryptographic authentication
892:National Computer Conference
784:DCNET Internet Clock Service
5571:Application layer protocols
4909:NVD NIST Product Search NTP
2716:Network Time Protocol (NTP)
2280:message authentication code
2190:NTP server misuse and abuse
2020:In 2004, Henning Brauer of
1925:ntpd § Implementations
79:; 39 years ago
5597:
5149:Goodin, Dan (2014-01-13).
3949:git.tuxfamily.org (chrony)
3428:. CRC Press. p. 377.
3269:.
3215:.
3158:.
3060:.
3004:.
2952:.
2903:.
2855:.
2802:.
2753:.
2700:.
2640:.
2402:), and 2 seconds is about
2187:
2055:
1922:
1199:These are computers whose
1129:Alternate Master Clock at
500:Coordinated Universal Time
18:
5381:developers.cloudflare.com
5353:"How to use NTS | Netnod"
5051:Jose Selvi (2014-10-16).
3917:"chrony – chrony.conf(5)"
3889:10.1109/CPEM.2002.1034915
3387:. Network Working Group.
3026:. Network Working Group.
2974:. Network Working Group.
2922:. Network Working Group.
2877:. Network Working Group.
2821:. Network Working Group.
2772:. Network Working Group.
2719:. Network Working Group.
2662:. Network Working Group.
2333:International Atomic Time
2220:man-in-the-middle attacks
1630:and the round-trip delay
1285:Generic pulse-per-second
1265:Global Positioning System
876:
606:
39:
5179:Lee, Dave (2014-02-11).
4812:. Ics-cert.us-cert.gov.
4463:"Manage NTP with Chrony"
4435:. chrony. Archived from
4302:. Apress. pp. 80–.
3807:UNIX Network Programming
3056:. Obsoleted by RFC
2256:DNS amplification attack
1944:reference implementation
1938:Reference implementation
1919:Software implementations
1341:Anthorn, UK 60 kHz
1188:signal that triggers an
1131:Schriever AFB (Colorado)
506:, a modified version of
19:Not to be confused with
5026:"NTP Security Analysis"
4889:NTP SecurityNotice Page
4393:"Securing Network Time"
4104:Ned Pyle (2007-10-23).
2362:Precision Time Protocol
2241:Border Gateway Protocol
1516:Round-trip delay time δ
1399:Fort Collins, Colorado
1153:server runs at stratum
557:123. They can also use
97:Internet protocol suite
5513:IETF NTP working group
5411:. chrony.tuxfamily.org
5255:"nts.time.nl homepage"
3867:University of Delaware
2996:Obsoleted by RFC
2944:Obsoleted by RFC
2899:Obsoleted by RFC
2843:Obsoleted by RFC
2794:Obsoleted by RFC
2741:Obsoleted by RFC
2684:Obsoleted by RFC
2628:. Updated by RFC
2074:
1934:
1878:
1818:
1717:
1624:
1517:
1142:
1134:
1127:U.S. Naval Observatory
1066:University of Delaware
601:
551:User Datagram Protocol
504:intersection algorithm
485:University of Delaware
49:International standard
4761:. 23 September 2009.
4429:"chrony introduction"
4139:technet.microsoft.com
3000:. Obsoletes RFC
2948:. Obsoletes RFC
2847:. Obsoletes RFC
2688:. Obsoletes RFC
2286:Network Time Security
2246:NTP has been used in
2226:attacks. NTP message
2200:stack buffer overflow
2065:
1932:
1923:Further information:
1879:
1819:
1718:
1625:
1515:
1438:USNO telephone modem
1430:NIST telephone modem
1140:
1124:
595:
510:, to select accurate
469:clock synchronization
457:Network Time Protocol
35:Network Time Protocol
4716:chrony.tuxfamily.org
4587:Poul-Henning, Kamp.
4556:Poul-Henning, Kamp.
3554:datatracker.ietf.org
1828:
1768:
1638:
1538:
1032:Marzullo's algorithm
884:time synchronization
596:NTP was designed by
575:daylight saving time
508:Marzullo's algorithm
5032:on 7 September 2013
4994:. IETF. June 2010.
4869:on 24 December 2014
4698:Engineering at Meta
4215:The OpenBSD Project
3048:Obsoletes RFC
2620:Obsoletes RFC
2517:. The NTP Project.
2394:2 seconds is about
2161:strictly increasing
2010:Windows Server 2016
1995:Windows Server 2003
1958:under Unix or as a
1277:Positioning System
1241:
1034:for NTPv3 onwards.
582:backward compatible
539:client–server model
524:local area networks
502:(UTC). It uses the
490:NTP is intended to
465:networking protocol
36:
5576:Internet Standards
5527:Time and NTP paper
5383:. 5 February 2024.
5316:Proposed Standard.
5101:on 22 October 2015
4947:2020-06-26 at the
4927:2020-06-26 at the
4894:2014-02-19 at the
4439:on 9 December 2009
4403:on 28 October 2017
4169:docs.microsoft.com
3710:"'ntpq -p' output"
3634:Proposed Standard.
3523:. March 11, 2015.
3491:. March 23, 2015.
3263:Proposed Standard.
3209:Proposed Standard.
2815:(September 1989).
2713:(September 1985).
2618:Proposed Standard.
2252:IP address spoofed
2157:configuration file
2075:
1935:
1874:
1814:
1713:
1620:
1518:
1486:binary fixed-point
1239:
1143:
1135:
1028:formal correctness
867:Port randomization
602:
532:network congestion
4730:"Security Notice"
4537:git.tuxfamily.org
4510:on 5 October 2017
4309:978-1-4842-2412-0
3845:. 14 March 2017.
3817:978-0-13-141155-5
3435:978-1-4398-1464-2
3351:10.1109/26.103043
3345:(10): 1482–1493.
3265:Updates RFC
3211:Updates RFC
3154:Updates RFC
2451:978-0-8493-5805-0
2404:585 billion years
2262:Secure extensions
2224:denial of service
2184:Security concerns
2131:systemd-timesyncd
2116:Poul-Henning Kamp
2092:, was created by
2042:security-hardened
2008:version 1607 and
1973:Microsoft Windows
1615:
1466:
1465:
1365:station, 100 kHz
882:In 1979, network
880:
879:
872:
871:
856:
855:
837:
836:
821:
820:
805:
804:
789:
788:
768:v4, RFC 4330
761:v4, RFC 2030
754:v3, RFC 1769
747:v3, RFC 1361
740:v4, RFC 5905
733:v3, RFC 1305
726:v2, RFC 1119
719:v1, RFC 1059
699:2020 —
689:2015 —
679:2010 —
669:2005 —
659:2000 —
649:1995 —
639:1990 —
629:1985 —
619:1980 —
611:evolution for NTP
453:
452:
104:Application layer
91:
90:
5588:
5557:
5556:
5555:
5550:
5542:David L. Mills,
5504:
5499:
5498:
5496:Official website
5483:
5474:
5472:10.17487/RFC5908
5456:
5447:
5445:10.17487/RFC5907
5420:
5419:
5417:
5416:
5405:
5399:
5398:
5391:
5385:
5384:
5373:
5367:
5366:
5364:
5363:
5349:
5343:
5342:
5340:
5339:
5324:
5318:
5314:
5297:
5295:10.17487/RFC8915
5275:
5269:
5268:
5266:
5265:
5251:
5245:
5244:
5242:
5231:
5225:
5224:
5222:
5221:
5202:
5196:
5195:
5193:
5192:
5176:
5170:
5169:
5167:
5166:
5146:
5140:
5139:
5137:
5136:
5127:. Archived from
5117:
5111:
5110:
5108:
5106:
5100:
5094:. Archived from
5089:
5080:
5074:
5073:
5071:
5070:
5064:
5058:. Archived from
5057:
5048:
5042:
5041:
5039:
5037:
5028:. Archived from
5022:
5013:
5012:
5003:
5001:10.17487/RFC5906
4986:
4977:
4976:
4974:
4973:
4958:
4952:
4938:
4932:
4918:
4912:
4905:
4899:
4885:
4879:
4878:
4876:
4874:
4858:
4852:
4851:
4849:
4847:
4831:
4825:
4824:
4822:
4821:
4806:
4800:
4799:
4797:
4796:
4781:
4775:
4774:
4772:
4770:
4751:
4745:
4744:
4742:
4741:
4726:
4720:
4719:
4708:
4702:
4701:
4689:
4683:
4682:
4680:
4678:
4663:
4657:
4656:
4654:
4652:
4636:
4630:
4629:
4615:
4609:
4608:
4606:
4604:
4584:
4578:
4577:
4575:
4573:
4553:
4547:
4546:
4544:
4543:
4529:
4523:
4522:
4517:
4515:
4509:
4498:
4489:
4483:
4482:
4480:
4478:
4458:
4452:
4451:
4446:
4444:
4425:
4416:
4415:
4410:
4408:
4389:
4383:
4382:
4377:
4375:
4366:. Archived from
4351:
4345:
4344:
4342:
4341:
4335:
4329:. Cure53. 2017.
4328:
4320:
4314:
4313:
4293:
4287:
4286:
4284:
4283:
4268:
4262:
4261:
4259:
4258:
4236:
4230:
4229:
4227:
4226:
4217:. Archived from
4206:
4200:
4199:
4185:
4179:
4178:
4176:
4175:
4160:
4154:
4153:
4151:
4150:
4131:
4125:
4124:
4122:
4121:
4101:
4095:
4094:
4092:
4091:
4072:
4063:
4062:
4060:
4059:
4044:
4038:
4037:
4035:
4034:
4015:
4009:
4008:
4006:
4005:
3990:
3984:
3983:
3981:
3980:
3974:
3968:. Cure53. 2017.
3967:
3959:
3953:
3952:
3941:
3935:
3934:
3929:
3927:
3912:
3903:
3902:
3876:
3870:
3864:
3858:
3857:
3855:
3854:
3839:
3833:
3832:
3830:
3829:
3801:
3795:
3794:
3792:
3790:
3774:
3768:
3767:
3756:
3750:
3749:
3735:
3729:
3728:
3726:
3725:
3706:
3697:
3696:
3694:
3692:
3677:
3671:
3668:
3662:
3661:
3646:
3640:
3632:
3615:
3613:10.17487/RFC5905
3590:
3584:
3583:
3571:
3565:
3564:
3562:
3560:
3546:
3537:
3536:
3534:
3532:
3511:
3505:
3504:
3502:
3500:
3479:
3473:
3472:
3471:
3469:
3454:"Future Plans",
3451:
3440:
3439:
3419:
3413:
3405:
3396:
3394:10.17487/RFC1305
3375:
3369:
3368:
3366:
3365:
3359:
3336:
3333:
3325:
3319:
3318:
3317:
3316:
3297:
3291:
3290:
3285:, archived from
3276:
3270:
3261:
3244:
3242:10.17487/RFC9109
3222:
3216:
3207:
3190:
3188:10.17487/RFC8573
3168:
3159:
3150:
3133:
3131:10.17487/RFC7822
3111:
3105:
3101:
3092:
3090:10.17487/RFC0778
3067:
3061:
3044:
3035:
3033:10.17487/RFC4330
3020:(January 2006).
3014:
3005:
2992:
2983:
2981:10.17487/RFC2030
2968:(October 1996).
2962:
2953:
2940:
2931:
2929:10.17487/RFC1769
2910:
2904:
2895:
2886:
2884:10.17487/RFC1361
2865:
2856:
2839:
2830:
2828:10.17487/RFC1119
2809:
2803:
2790:
2781:
2779:10.17487/RFC1059
2760:
2754:
2737:
2728:
2726:10.17487/RFC0958
2707:
2701:
2680:
2671:
2669:10.17487/RFC1305
2650:
2641:
2616:
2599:
2597:10.17487/RFC5905
2574:
2555:
2554:
2552:
2551:
2536:
2530:
2529:
2527:
2526:
2511:
2498:
2497:
2495:
2494:
2479:
2468:
2467:
2465:
2463:
2435:
2407:
2392:
2386:
2379:
2179:
2175:
2151:On the day of a
2138:. It is used by
2133:
2132:
2124:Linux Foundation
2113:
2112:
2098:Miroslav Lichvar
1883:
1881:
1880:
1875:
1873:
1872:
1857:
1840:
1839:
1823:
1821:
1820:
1815:
1813:
1812:
1797:
1780:
1779:
1722:
1720:
1719:
1714:
1709:
1705:
1704:
1692:
1691:
1673:
1672:
1660:
1659:
1629:
1627:
1626:
1621:
1616:
1611:
1607:
1606:
1594:
1593:
1575:
1574:
1562:
1561:
1548:
1526:round-trip delay
1422:telephone modem
1387:Ottawa, Ontario
1242:
1186:pulse per second
948:round-trip delay
863:
858:
844:
839:
828:
823:
812:
807:
796:
791:
780:
775:
769:
762:
755:
748:
741:
734:
727:
720:
713:
712:v0, RFC 958
705:
700:
695:
690:
685:
680:
675:
670:
665:
660:
655:
650:
645:
640:
635:
630:
625:
620:
604:
584:with version 3.
577:is transmitted.
445:
438:
431:
93:
87:
85:
80:
44:
37:
21:Daytime Protocol
5596:
5595:
5591:
5590:
5589:
5587:
5586:
5585:
5561:
5560:
5553:
5551:
5548:
5541:
5532:NTP Survey 2005
5494:
5493:
5490:
5459:
5432:
5429:
5427:Further reading
5424:
5423:
5414:
5412:
5407:
5406:
5402:
5397:. 24 June 2021.
5393:
5392:
5388:
5375:
5374:
5370:
5361:
5359:
5351:
5350:
5346:
5337:
5335:
5326:
5325:
5321:
5277:
5276:
5272:
5263:
5261:
5253:
5252:
5248:
5240:
5233:
5232:
5228:
5219:
5217:
5210:support.NTP.org
5204:
5203:
5199:
5190:
5188:
5178:
5177:
5173:
5164:
5162:
5148:
5147:
5143:
5134:
5132:
5119:
5118:
5114:
5104:
5102:
5098:
5087:
5082:
5081:
5077:
5068:
5066:
5062:
5055:
5050:
5049:
5045:
5035:
5033:
5024:
5023:
5016:
4988:
4987:
4980:
4971:
4969:
4960:
4959:
4955:
4949:Wayback Machine
4939:
4935:
4929:Wayback Machine
4919:
4915:
4906:
4902:
4896:Wayback Machine
4886:
4882:
4872:
4870:
4860:
4859:
4855:
4845:
4843:
4838:. arstechnica.
4833:
4832:
4828:
4819:
4817:
4808:
4807:
4803:
4794:
4792:
4789:Support.NTP.org
4783:
4782:
4778:
4768:
4766:
4753:
4752:
4748:
4739:
4737:
4734:Support.NTP.org
4728:
4727:
4723:
4710:
4709:
4705:
4691:
4690:
4686:
4676:
4674:
4665:
4664:
4660:
4650:
4648:
4638:
4637:
4633:
4617:
4616:
4612:
4602:
4600:
4586:
4585:
4581:
4571:
4569:
4555:
4554:
4550:
4541:
4539:
4531:
4530:
4526:
4513:
4511:
4507:
4496:
4491:
4490:
4486:
4476:
4474:
4460:
4459:
4455:
4442:
4440:
4427:
4426:
4419:
4406:
4404:
4391:
4390:
4386:
4373:
4371:
4370:on 30 July 2016
4353:
4352:
4348:
4339:
4337:
4333:
4326:
4322:
4321:
4317:
4310:
4295:
4294:
4290:
4281:
4279:
4270:
4269:
4265:
4256:
4254:
4238:
4237:
4233:
4224:
4222:
4208:
4207:
4203:
4193:man.openbsd.org
4187:
4186:
4182:
4173:
4171:
4162:
4161:
4157:
4148:
4146:
4133:
4132:
4128:
4119:
4117:
4103:
4102:
4098:
4089:
4087:
4074:
4073:
4066:
4057:
4055:
4046:
4045:
4041:
4032:
4030:
4023:Support.NTP.org
4017:
4016:
4012:
4003:
4001:
3992:
3991:
3987:
3978:
3976:
3972:
3965:
3961:
3960:
3956:
3943:
3942:
3938:
3925:
3923:
3914:
3913:
3906:
3899:
3878:
3877:
3873:
3865:
3861:
3852:
3850:
3841:
3840:
3836:
3827:
3825:
3818:
3803:
3802:
3798:
3788:
3786:
3776:
3775:
3771:
3758:
3757:
3753:
3743:docs.ntpsec.org
3737:
3736:
3732:
3723:
3721:
3708:
3707:
3700:
3690:
3688:
3679:
3678:
3674:
3670:RFC 5905, p. 21
3669:
3665:
3648:
3647:
3643:
3592:
3591:
3587:
3573:
3572:
3568:
3558:
3556:
3548:
3547:
3540:
3530:
3528:
3520:InformationWeek
3513:
3512:
3508:
3498:
3496:
3488:InformationWeek
3481:
3480:
3476:
3467:
3465:
3453:
3452:
3443:
3436:
3421:
3420:
3416:
3377:
3376:
3372:
3363:
3361:
3357:
3334:
3327:
3326:
3322:
3314:
3312:
3299:
3298:
3294:
3278:
3277:
3273:
3224:
3223:
3219:
3170:
3169:
3162:
3113:
3112:
3108:
3069:
3068:
3064:
3016:
3015:
3008:
2964:
2963:
2956:
2912:
2911:
2907:
2871:(August 1992).
2867:
2866:
2859:
2811:
2810:
2806:
2762:
2761:
2757:
2709:
2708:
2704:
2652:
2651:
2644:
2576:
2575:
2558:
2549:
2547:
2538:
2537:
2533:
2524:
2522:
2513:
2512:
2501:
2492:
2490:
2481:
2480:
2471:
2461:
2459:
2452:
2437:
2436:
2421:
2416:
2411:
2410:
2396:54 zeptoseconds
2393:
2389:
2380:
2376:
2371:
2317:
2264:
2192:
2186:
2177:
2173:
2149:
2130:
2129:
2114:was started by
2110:
2109:
2106:
2068:Terminal window
2060:
2054:
2034:
2018:
2004:Beginning with
1993:Beginning with
1975:versions since
1969:
1940:
1927:
1921:
1912:systematic bias
1891:The values for
1864:
1831:
1826:
1825:
1804:
1771:
1766:
1765:
1759:
1750:
1741:
1732:
1696:
1683:
1664:
1651:
1636:
1635:
1598:
1585:
1566:
1553:
1549:
1536:
1535:
1510:
1482:
1119:
1094:
1047:reference clock
904:Fuzzball router
868:
861:
852:
842:
833:
826:
817:
810:
801:
794:
785:
778:
771:
770:
767:
764:
763:
760:
757:
756:
753:
750:
749:
746:
743:
742:
739:
736:
735:
732:
729:
728:
725:
722:
721:
718:
715:
714:
711:
706:
703:
701:
698:
696:
693:
691:
688:
686:
683:
681:
678:
676:
673:
671:
668:
666:
663:
661:
658:
656:
653:
651:
648:
646:
643:
641:
638:
636:
633:
631:
628:
626:
623:
621:
618:
612:
590:
516:network latency
473:packet-switched
449:
269:Transport layer
83:
81:
78:
32:
17:
12:
11:
5:
5594:
5592:
5584:
5583:
5578:
5573:
5563:
5562:
5559:
5558:
5539:
5534:
5529:
5524:
5515:
5510:
5505:
5489:
5488:External links
5486:
5485:
5484:
5457:
5428:
5425:
5422:
5421:
5400:
5386:
5368:
5344:
5319:
5270:
5246:
5226:
5212:. 2010-04-24.
5197:
5171:
5141:
5112:
5075:
5043:
5014:
4978:
4953:
4933:
4913:
4900:
4880:
4853:
4826:
4801:
4776:
4746:
4721:
4703:
4684:
4658:
4631:
4610:
4579:
4562:PHK's Bikeshed
4548:
4524:
4501:Cure53.de Team
4484:
4467:Opensource.com
4453:
4417:
4384:
4346:
4315:
4308:
4288:
4263:
4231:
4201:
4180:
4155:
4126:
4096:
4082:. 2011-10-19.
4064:
4039:
4025:. 2008-02-25.
4010:
3985:
3954:
3936:
3921:Chrony project
3904:
3897:
3871:
3859:
3834:
3816:
3796:
3769:
3751:
3730:
3714:NLUG.ML1.co.uk
3698:
3672:
3663:
3654:www.redhat.com
3641:
3585:
3566:
3538:
3506:
3474:
3441:
3434:
3414:
3381:(March 1992).
3379:David L. Mills
3370:
3320:
3292:
3271:
3217:
3160:
3152:Informational.
3106:
3073:(April 1981).
3062:
3006:
2954:
2916:(March 1995).
2905:
2857:
2804:
2755:
2702:
2656:(March 1992).
2654:David L. Mills
2642:
2556:
2540:"Port Numbers"
2531:
2499:
2469:
2450:
2418:
2417:
2415:
2412:
2409:
2408:
2387:
2373:
2372:
2370:
2367:
2366:
2365:
2359:
2353:
2347:
2342:
2336:
2330:
2324:
2321:Allan variance
2316:
2313:
2305:Windows domain
2263:
2260:
2185:
2182:
2172:leap smear in
2148:
2145:
2144:
2143:
2127:
2105:
2102:
2094:Richard Curnow
2056:Main article:
2053:
2050:
2033:
2030:
2017:
2014:
1988:replay attacks
1968:
1965:
1939:
1936:
1920:
1917:
1871:
1867:
1863:
1860:
1856:
1852:
1849:
1846:
1843:
1838:
1834:
1811:
1807:
1803:
1800:
1796:
1792:
1789:
1786:
1783:
1778:
1774:
1762:
1761:
1757:
1752:
1748:
1743:
1739:
1734:
1730:
1712:
1708:
1703:
1699:
1695:
1690:
1686:
1682:
1679:
1676:
1671:
1667:
1663:
1658:
1654:
1650:
1646:
1643:
1619:
1614:
1610:
1605:
1601:
1597:
1592:
1588:
1584:
1581:
1578:
1573:
1569:
1565:
1560:
1556:
1552:
1546:
1543:
1528:. Time offset
1509:
1506:
1481:
1478:
1464:
1463:
1460:
1456:
1455:
1452:
1448:
1447:
1444:
1440:
1439:
1436:
1432:
1431:
1428:
1424:
1423:
1417:
1413:
1412:
1411:Kauai, Hawaii
1405:
1401:
1400:
1393:
1389:
1388:
1381:
1377:
1376:
1371:
1367:
1366:
1359:
1355:
1354:
1347:
1343:
1342:
1335:
1331:
1330:
1323:
1319:
1318:
1311:
1307:
1306:
1299:
1295:
1294:
1291:
1287:
1286:
1283:
1279:
1278:
1272:
1268:
1267:
1262:
1258:
1257:
1254:
1250:
1249:
1246:
1229:shortest-path
1223:
1222:
1218:
1215:
1211:
1208:
1197:
1194:
1162:
1118:
1115:
1093:
1090:
995:David L. Mills
919:ICMP Timestamp
878:
877:
874:
873:
870:
869:
866:
864:
854:
853:
847:
845:
835:
834:
831:
829:
819:
818:
815:
813:
803:
802:
799:
797:
787:
786:
783:
781:
772:
766:
765:
759:
758:
752:
751:
745:
744:
738:
737:
731:
730:
724:
723:
717:
716:
710:
709:
707:
702:
697:
692:
687:
682:
677:
672:
667:
662:
657:
652:
647:
642:
637:
632:
627:
622:
617:
614:
613:
607:
598:David L. Mills
589:
586:
481:David L. Mills
451:
450:
448:
447:
440:
433:
425:
422:
421:
420:
419:
412:
407:
402:
397:
389:
388:
382:
381:
380:
379:
372:
367:
362:
357:
352:
342:
341:
340:
335:
322:
321:
319:Internet layer
315:
314:
313:
312:
305:
300:
295:
290:
285:
280:
272:
271:
265:
264:
263:
262:
255:
250:
245:
240:
235:
230:
225:
220:
215:
210:
205:
200:
195:
190:
185:
180:
175:
170:
165:
160:
155:
150:
145:
135:
130:
125:
115:
107:
106:
100:
99:
89:
88:
75:
71:
70:
67:David L. Mills
64:
60:
59:
50:
46:
45:
15:
13:
10:
9:
6:
4:
3:
2:
5593:
5582:
5579:
5577:
5574:
5572:
5569:
5568:
5566:
5547:
5546:
5540:
5538:
5535:
5533:
5530:
5528:
5525:
5523:
5519:
5516:
5514:
5511:
5509:
5506:
5503:
5497:
5492:
5491:
5487:
5481:
5478:
5473:
5468:
5464:
5463:
5458:
5454:
5451:
5446:
5441:
5437:
5436:
5431:
5430:
5426:
5410:
5404:
5401:
5396:
5390:
5387:
5382:
5378:
5372:
5369:
5358:
5354:
5348:
5345:
5334:
5333:Weberblog.net
5330:
5323:
5320:
5317:
5312:
5309:
5305:
5301:
5296:
5291:
5287:
5283:
5282:
5274:
5271:
5260:
5256:
5250:
5247:
5239:
5238:
5230:
5227:
5215:
5211:
5207:
5201:
5198:
5186:
5182:
5175:
5172:
5160:
5156:
5152:
5145:
5142:
5131:on 2015-10-24
5130:
5126:
5125:www.cs.bu.edu
5122:
5116:
5113:
5097:
5093:
5086:
5079:
5076:
5065:on 2014-10-18
5061:
5054:
5047:
5044:
5031:
5027:
5021:
5019:
5015:
5010:
5007:
5002:
4997:
4993:
4992:
4985:
4983:
4979:
4968:on 2018-02-03
4967:
4963:
4957:
4954:
4951:
4950:
4946:
4943:
4937:
4934:
4931:
4930:
4926:
4923:
4917:
4914:
4911:
4910:
4904:
4901:
4898:
4897:
4893:
4890:
4884:
4881:
4868:
4864:
4857:
4854:
4841:
4837:
4830:
4827:
4815:
4811:
4805:
4802:
4790:
4786:
4780:
4777:
4764:
4760:
4759:Cisco Systems
4756:
4750:
4747:
4735:
4731:
4725:
4722:
4717:
4713:
4707:
4704:
4699:
4695:
4688:
4685:
4672:
4668:
4662:
4659:
4646:
4642:
4639:David Mills.
4635:
4632:
4628:
4624:
4620:
4614:
4611:
4598:
4594:
4590:
4583:
4580:
4567:
4563:
4559:
4552:
4549:
4538:
4534:
4528:
4525:
4521:
4506:
4502:
4495:
4488:
4485:
4472:
4468:
4464:
4461:Both, David.
4457:
4454:
4450:
4438:
4434:
4430:
4424:
4422:
4418:
4414:
4402:
4398:
4394:
4388:
4385:
4381:
4369:
4365:
4361:
4357:
4350:
4347:
4332:
4325:
4319:
4316:
4311:
4305:
4301:
4300:
4292:
4289:
4277:
4273:
4267:
4264:
4252:
4248:
4247:
4246:Linux Journal
4242:
4235:
4232:
4221:on 2016-02-05
4220:
4216:
4212:
4205:
4202:
4198:
4194:
4190:
4184:
4181:
4170:
4166:
4159:
4156:
4144:
4140:
4136:
4130:
4127:
4115:
4111:
4107:
4100:
4097:
4085:
4081:
4077:
4071:
4069:
4065:
4053:
4049:
4043:
4040:
4028:
4024:
4020:
4014:
4011:
3999:
3995:
3989:
3986:
3971:
3964:
3958:
3955:
3950:
3946:
3940:
3937:
3933:
3922:
3918:
3911:
3909:
3905:
3900:
3898:0-7803-7242-5
3894:
3890:
3886:
3882:
3875:
3872:
3868:
3863:
3860:
3848:
3844:
3838:
3835:
3823:
3819:
3813:
3809:
3808:
3800:
3797:
3784:
3780:
3773:
3770:
3765:
3761:
3755:
3752:
3748:
3744:
3740:
3734:
3731:
3719:
3715:
3711:
3705:
3703:
3699:
3686:
3682:
3676:
3673:
3667:
3664:
3660:
3655:
3651:
3645:
3642:
3639:
3635:
3630:
3627:
3623:
3619:
3614:
3609:
3605:
3601:
3600:
3595:
3589:
3586:
3581:
3577:
3570:
3567:
3555:
3551:
3545:
3543:
3539:
3526:
3522:
3521:
3516:
3510:
3507:
3494:
3490:
3489:
3484:
3478:
3475:
3463:
3459:
3458:
3450:
3448:
3446:
3442:
3437:
3431:
3427:
3426:
3418:
3415:
3412:
3408:
3403:
3400:
3395:
3390:
3386:
3385:
3380:
3374:
3371:
3356:
3352:
3348:
3344:
3340:
3332:
3324:
3321:
3310:
3306:
3302:
3296:
3293:
3289:on 1996-12-30
3288:
3284:
3283:
3275:
3272:
3268:
3264:
3259:
3256:
3252:
3248:
3243:
3238:
3234:
3230:
3229:
3221:
3218:
3214:
3210:
3205:
3202:
3198:
3194:
3189:
3184:
3180:
3176:
3175:
3167:
3165:
3161:
3157:
3153:
3148:
3145:
3141:
3137:
3132:
3127:
3123:
3119:
3118:
3110:
3107:
3104:
3099:
3096:
3091:
3086:
3082:
3078:
3077:
3072:
3066:
3063:
3059:
3055:
3051:
3047:
3042:
3039:
3034:
3029:
3025:
3024:
3019:
3013:
3011:
3007:
3003:
2999:
2995:
2990:
2987:
2982:
2977:
2973:
2972:
2967:
2961:
2959:
2955:
2951:
2947:
2943:
2938:
2935:
2930:
2925:
2921:
2920:
2915:
2909:
2906:
2902:
2898:
2893:
2890:
2885:
2880:
2876:
2875:
2870:
2864:
2862:
2858:
2854:
2850:
2846:
2842:
2837:
2834:
2829:
2824:
2820:
2819:
2814:
2808:
2805:
2801:
2797:
2793:
2788:
2785:
2780:
2775:
2771:
2770:
2766:(July 1988).
2765:
2759:
2756:
2752:
2748:
2744:
2740:
2735:
2732:
2727:
2722:
2718:
2717:
2712:
2706:
2703:
2699:
2695:
2691:
2687:
2683:
2678:
2675:
2670:
2665:
2661:
2660:
2655:
2649:
2647:
2643:
2639:
2635:
2631:
2627:
2623:
2619:
2614:
2611:
2607:
2603:
2598:
2593:
2589:
2585:
2584:
2579:
2573:
2571:
2569:
2567:
2565:
2563:
2561:
2557:
2545:
2541:
2535:
2532:
2520:
2516:
2510:
2508:
2506:
2504:
2500:
2488:
2484:
2478:
2476:
2474:
2470:
2457:
2453:
2447:
2443:
2442:
2434:
2432:
2430:
2428:
2426:
2424:
2420:
2413:
2405:
2401:
2397:
2391:
2388:
2384:
2378:
2375:
2368:
2363:
2360:
2357:
2354:
2351:
2348:
2346:
2343:
2340:
2339:IRIG timecode
2337:
2334:
2331:
2328:
2327:Clock network
2325:
2322:
2319:
2318:
2314:
2312:
2310:
2306:
2301:
2299:
2295:
2291:
2287:
2283:
2281:
2277:
2273:
2269:
2268:symmetric key
2261:
2259:
2257:
2253:
2249:
2244:
2242:
2238:
2234:
2229:
2225:
2221:
2216:
2212:
2210:
2205:
2201:
2196:
2191:
2183:
2181:
2169:
2166:
2162:
2158:
2154:
2146:
2141:
2137:
2128:
2125:
2121:
2117:
2108:
2107:
2103:
2101:
2099:
2095:
2091:
2085:
2083:
2079:
2073:
2069:
2064:
2059:
2051:
2049:
2047:
2043:
2039:
2031:
2029:
2027:
2023:
2015:
2013:
2011:
2007:
2002:
2000:
1999:Windows Vista
1996:
1991:
1989:
1985:
1980:
1978:
1974:
1966:
1964:
1961:
1957:
1953:
1949:
1945:
1937:
1931:
1926:
1918:
1916:
1913:
1908:
1906:
1905:feedback loop
1902:
1898:
1894:
1889:
1887:
1869:
1865:
1861:
1858:
1854:
1850:
1847:
1844:
1841:
1836:
1832:
1809:
1805:
1801:
1798:
1794:
1790:
1787:
1784:
1781:
1776:
1772:
1756:
1753:
1747:
1744:
1738:
1735:
1729:
1726:
1725:
1724:
1710:
1701:
1697:
1693:
1688:
1684:
1677:
1669:
1665:
1661:
1656:
1652:
1644:
1641:
1633:
1617:
1612:
1603:
1599:
1595:
1590:
1586:
1579:
1571:
1567:
1563:
1558:
1554:
1544:
1541:
1533:
1531:
1527:
1523:
1514:
1507:
1505:
1502:
1497:
1495:
1491:
1487:
1479:
1477:
1474:
1470:
1461:
1458:
1457:
1453:
1450:
1449:
1445:
1442:
1441:
1437:
1434:
1433:
1429:
1426:
1425:
1421:
1418:
1415:
1414:
1410:
1406:
1403:
1402:
1398:
1394:
1391:
1390:
1386:
1382:
1379:
1378:
1375:
1372:
1369:
1368:
1364:
1360:
1357:
1356:
1352:
1348:
1345:
1344:
1340:
1336:
1333:
1332:
1328:
1324:
1321:
1320:
1316:
1312:
1309:
1308:
1304:
1300:
1297:
1296:
1292:
1289:
1288:
1284:
1281:
1280:
1276:
1273:
1270:
1269:
1266:
1263:
1260:
1259:
1255:
1252:
1251:
1248:Clock Source
1247:
1244:
1243:
1237:
1234:
1232:
1231:spanning tree
1228:
1219:
1216:
1212:
1209:
1206:
1202:
1198:
1195:
1191:
1187:
1183:
1179:
1175:
1171:
1167:
1166:atomic clocks
1163:
1160:
1159:
1158:
1156:
1152:
1148:
1139:
1132:
1128:
1123:
1116:
1114:
1111:
1107:
1103:
1099:
1098:Time Protocol
1091:
1089:
1087:
1083:
1077:
1075:
1071:
1067:
1063:
1059:
1054:
1052:
1048:
1044:
1040:
1035:
1033:
1029:
1025:
1021:
1017:
1016:state machine
1013:
1009:
1004:
1002:
1001:
996:
992:
988:
987:client–server
984:
980:
976:
972:
967:
965:
961:
957:
953:
949:
944:
942:
938:
937:
932:
928:
924:
920:
916:
912:
907:
905:
901:
897:
893:
889:
885:
875:
865:
860:
859:
850:
846:
841:
840:
830:
825:
824:
814:
809:
808:
798:
793:
792:
782:
777:
776:
773:
708:
616:
615:
610:
605:
599:
594:
587:
585:
583:
578:
576:
572:
568:
564:
560:
556:
552:
548:
544:
540:
535:
533:
529:
525:
521:
517:
513:
509:
505:
501:
497:
493:
488:
486:
482:
478:
474:
470:
466:
462:
458:
446:
441:
439:
434:
432:
427:
426:
424:
423:
418:
417:
413:
411:
408:
406:
403:
401:
398:
396:
393:
392:
391:
390:
387:
383:
378:
377:
373:
371:
368:
366:
363:
361:
358:
356:
353:
350:
346:
343:
339:
336:
334:
331:
330:
329:
326:
325:
324:
323:
320:
316:
311:
310:
306:
304:
301:
299:
296:
294:
291:
289:
286:
284:
281:
279:
276:
275:
274:
273:
270:
266:
261:
260:
256:
254:
251:
249:
246:
244:
241:
239:
236:
234:
231:
229:
226:
224:
221:
219:
216:
214:
211:
209:
206:
204:
201:
199:
196:
194:
191:
189:
186:
184:
181:
179:
176:
174:
171:
169:
166:
164:
161:
159:
156:
154:
151:
149:
146:
143:
139:
136:
134:
131:
129:
126:
123:
119:
116:
114:
111:
110:
109:
108:
105:
101:
98:
94:
76:
72:
68:
65:
61:
58:
54:
51:
47:
43:
38:
30:
26:
25:Time Protocol
22:
5552:, retrieved
5544:
5461:
5434:
5413:. Retrieved
5403:
5389:
5380:
5371:
5360:. Retrieved
5356:
5347:
5336:. Retrieved
5332:
5322:
5315:
5280:
5273:
5262:. Retrieved
5258:
5249:
5236:
5229:
5218:. Retrieved
5209:
5200:
5189:. Retrieved
5174:
5163:. Retrieved
5155:Ars Technica
5154:
5144:
5133:. Retrieved
5129:the original
5124:
5115:
5103:. Retrieved
5096:the original
5091:
5078:
5067:. Retrieved
5060:the original
5046:
5034:. Retrieved
5030:the original
4990:
4970:. Retrieved
4966:the original
4956:
4940:
4936:
4920:
4916:
4907:
4903:
4887:
4883:
4871:. Retrieved
4867:the original
4856:
4844:. Retrieved
4829:
4818:. Retrieved
4804:
4793:. Retrieved
4791:. 2009-06-13
4788:
4785:"Code Audit"
4779:
4767:. Retrieved
4749:
4738:. Retrieved
4736:. 2009-12-10
4733:
4724:
4715:
4706:
4697:
4687:
4675:. Retrieved
4661:
4649:. Retrieved
4634:
4626:
4622:
4613:
4601:. Retrieved
4592:
4582:
4570:. Retrieved
4561:
4551:
4540:. Retrieved
4536:
4527:
4519:
4512:. Retrieved
4505:the original
4500:
4487:
4475:. Retrieved
4466:
4456:
4448:
4441:. Retrieved
4437:the original
4432:
4412:
4405:. Retrieved
4401:the original
4396:
4387:
4379:
4372:. Retrieved
4368:the original
4359:
4349:
4338:. Retrieved
4318:
4298:
4291:
4280:. Retrieved
4266:
4255:. Retrieved
4244:
4234:
4223:. Retrieved
4219:the original
4214:
4204:
4196:
4192:
4183:
4172:. Retrieved
4168:
4158:
4147:. Retrieved
4138:
4129:
4118:. Retrieved
4099:
4088:. Retrieved
4056:. Retrieved
4042:
4031:. Retrieved
4022:
4013:
4002:. Retrieved
3988:
3977:. Retrieved
3957:
3948:
3939:
3931:
3924:. Retrieved
3920:
3880:
3874:
3862:
3851:. Retrieved
3837:
3826:. Retrieved
3806:
3799:
3789:24 September
3787:. Retrieved
3772:
3764:www.iana.org
3763:
3754:
3746:
3742:
3733:
3722:. Retrieved
3713:
3689:. Retrieved
3675:
3666:
3657:
3653:
3644:
3636:
3633:
3598:
3588:
3580:www.ietf.org
3579:
3569:
3557:. Retrieved
3553:
3529:. Retrieved
3518:
3509:
3497:. Retrieved
3486:
3477:
3466:, retrieved
3456:
3424:
3417:
3409:
3406:
3383:
3373:
3362:. Retrieved
3342:
3338:
3323:
3313:, retrieved
3304:
3295:
3287:the original
3281:
3274:
3262:
3227:
3220:
3208:
3173:
3151:
3116:
3109:
3102:
3075:
3065:
3045:
3022:
2993:
2970:
2941:
2918:
2908:
2896:
2873:
2840:
2817:
2807:
2791:
2768:
2758:
2738:
2715:
2705:
2681:
2658:
2617:
2582:
2548:. Retrieved
2534:
2523:. Retrieved
2491:. Retrieved
2460:. Retrieved
2440:
2390:
2383:clock strata
2377:
2302:
2285:
2284:
2265:
2245:
2217:
2213:
2197:
2193:
2170:
2150:
2147:Leap seconds
2086:
2076:
2036:NTPsec is a
2035:
2019:
2003:
1992:
1981:
1977:Windows 2000
1970:
1967:Windows Time
1941:
1909:
1896:
1892:
1890:
1885:
1884:Solving for
1763:
1754:
1745:
1736:
1727:
1631:
1534:
1529:
1519:
1500:
1498:
1483:
1475:
1471:
1467:
1235:
1227:Bellman–Ford
1224:
1205:sanity check
1178:radio clocks
1154:
1150:
1146:
1144:
1117:Clock strata
1105:
1101:
1095:
1078:
1073:
1055:
1036:
1005:
998:
991:peer-to-peer
968:
960:milliseconds
945:
940:
934:
908:
881:
579:
563:multicasting
559:broadcasting
543:peer-to-peer
536:
512:time servers
496:milliseconds
489:
460:
456:
454:
415:
375:
308:
258:
182:
63:Developed by
5259:nts.time.nl
4873:24 December
4514:19 November
4443:19 November
4407:19 November
4374:19 November
3559:27 December
3468:24 December
2400:Bohr radius
2178:leapsecmode
2153:leap second
1504:goes dim."
1484:The 64-bit
1201:system time
1176:) or other
1172:(including
1070:open source
832:Ext. fields
816:SNTP merged
567:leap second
555:port number
492:synchronize
475:, variable-
5565:Categories
5554:2021-02-07
5415:2019-10-08
5362:2021-08-19
5338:2021-08-19
5264:2021-08-19
5243:. IETF 83.
5220:2014-04-13
5191:2014-02-12
5165:2014-01-25
5135:2015-10-27
5105:27 October
5069:2014-10-16
5036:11 October
4972:2019-07-03
4820:2015-04-15
4795:2011-01-12
4740:2011-01-12
4651:15 October
4595:. Github.
4542:2021-07-31
4340:2019-07-03
4282:2019-01-12
4257:2024-01-26
4225:2020-05-14
4174:2021-07-24
4149:2016-12-07
4120:2012-08-26
4090:2008-12-10
4058:2011-09-19
4033:2017-05-01
4004:2011-09-19
3979:2019-07-03
3853:2018-07-20
3828:2016-10-16
3724:2018-11-12
3691:15 October
3364:2017-11-06
3315:2017-09-12
3301:"TIMED(8)"
3071:D.L. Mills
2550:2011-01-19
2525:2011-08-27
2493:2011-11-21
2462:16 October
2414:References
2298:Cloudflare
2272:public key
2188:See also:
2174:smoothtime
2072:Arch Linux
2024:presented
2006:Windows 10
1501:Era Number
1490:rolls over
1480:Timestamps
1020:pseudocode
966:networks.
571:time zones
549:using the
547:timestamps
386:Link layer
74:Introduced
5304:2070-1721
4163:dahavey.
4110:Microsoft
4080:Microsoft
3622:2070-1721
3407:Obsolete.
3251:2070-1721
3197:2070-1721
3140:2070-1721
3103:Historic.
3046:Obsolete.
2994:Obsolete.
2942:Obsolete.
2897:Obsolete.
2841:Obsolete.
2792:Obsolete.
2739:Obsolete.
2682:Obsolete.
2606:2070-1721
2515:"NTP FAQ"
2165:processes
1851:δ
1848:−
1845:θ
1791:δ
1785:θ
1694:−
1678:−
1662:−
1642:δ
1596:−
1564:−
1542:θ
1407:HF Radio
1395:HF Radio
1383:HF Radio
1361:MF Radio
1349:LF Radio
1337:LF Radio
1325:LF Radio
1313:LF Radio
1301:LF Radio
1217:Stratum 3
1210:Stratum 2
1196:Stratum 1
1190:interrupt
1161:Stratum 0
1074:protocols
1037:In 1992,
1006:In 1989,
553:(UDP) on
5214:Archived
5185:Archived
5159:Archived
4945:Archived
4925:Archived
4892:Archived
4840:Archived
4814:Archived
4763:Archived
4671:Archived
4645:Archived
4623:anarc.at
4597:Archived
4566:Archived
4471:Archived
4331:Archived
4276:Archived
4251:Archived
4143:Archived
4114:Archived
4084:Archived
4052:Archived
4027:Archived
3998:Archived
3970:Archived
3926:2 August
3847:Archived
3822:Archived
3783:Archived
3718:Archived
3685:Archived
3606:(IETF).
3594:D. Mills
3531:April 4,
3525:Archived
3499:April 4,
3493:Archived
3462:archived
3355:Archived
3309:archived
3018:D. Mills
2966:D. Mills
2914:D. Mills
2869:D. Mills
2813:D. Mills
2764:D. Mills
2711:D. Mills
2590:(IETF).
2578:D. Mills
2544:Archived
2519:Archived
2487:Archived
2456:Archived
2350:NTP pool
2315:See also
2228:spoofing
2209:OpenNTPD
2026:OpenNTPD
2016:OpenNTPD
1984:Kerberos
1942:The NTP
1901:Outliers
1193:stratum.
964:Ethernet
888:Internet
520:Internet
5183:. BBC.
4846:Apr 29,
4769:11 June
4677:4 April
4477:29 June
4364:Red Hat
2356:Ntpdate
2136:systemd
2120:FreeBSD
2082:Red Hat
2022:OpenBSD
1960:service
1954:called
1363:Loran-C
1275:Galileo
1180:, or a
1147:stratum
1018:, with
997:in the
933:daemon
911:Daytime
862:←
843:←
827:←
811:←
795:←
779:←
704:–
694:–
684:–
674:–
664:–
654:–
644:–
634:–
624:–
588:History
483:of the
477:latency
463:) is a
416:more...
400:Tunnels
376:more...
309:more...
259:more...
248:TLS/SSL
203:ONC/RPC
140: (
82: (
5357:Netnod
5302:
4603:4 June
4572:4 June
4306:
3895:
3814:
3659:clock.
3620:
3432:
3249:
3195:
3138:
2604:
2448:
2237:DNSSEC
2163:, any
2140:Debian
2111:Ntimed
2104:Others
2078:chrony
2070:under
2058:chrony
2052:chrony
2032:NTPsec
1952:daemon
1948:ported
1723:where
1214:group.
1084:
1060:
1051:metric
1041:
1010:
981:
973:
954:
925:
898:
851:change
528:routes
243:Telnet
142:HTTP/3
55:
5549:(PDF)
5241:(PDF)
5099:(PDF)
5088:(PDF)
5063:(PDF)
5056:(PDF)
4508:(PDF)
4497:(PDF)
4334:(PDF)
4327:(PDF)
3973:(PDF)
3966:(PDF)
3358:(PDF)
3335:(PDF)
2369:Notes
2309:samba
2276:IPSec
2204:Apple
2046:audit
1522:polls
1494:epoch
1315:DCF77
1245:Refid
1110:state
936:timed
370:IPsec
148:HTTPS
27:, or
5522:more
5520:and
5480:5908
5453:5907
5311:8915
5300:ISSN
5107:2015
5092:NDSS
5038:2013
5009:5906
4875:2014
4848:2015
4771:2020
4679:2019
4653:2013
4605:2015
4574:2015
4516:2017
4479:2019
4445:2017
4409:2017
4376:2017
4304:ISBN
3928:2020
3893:ISBN
3812:ISBN
3791:2016
3693:2013
3629:5905
3618:ISSN
3561:2022
3533:2015
3501:2015
3470:2014
3430:ISBN
3402:1305
3267:5905
3258:9109
3247:ISSN
3213:5905
3204:8573
3193:ISSN
3156:5905
3147:7822
3136:ISSN
3122:IETF
3081:IETF
3058:5905
3054:1769
3052:and
3050:2030
3041:4330
3002:1769
2998:4330
2989:2030
2950:1361
2946:2030
2937:1769
2901:1769
2892:1361
2853:1059
2851:and
2845:1305
2836:1119
2800:1305
2798:and
2796:1119
2787:1059
2751:1305
2749:and
2747:1119
2743:1059
2698:1119
2696:and
2694:1059
2686:5905
2677:1305
2638:9109
2636:and
2634:8573
2630:7822
2626:4330
2622:1305
2613:5905
2602:ISSN
2464:2016
2446:ISBN
2345:NITZ
2294:AEAD
2292:and
2176:and
2038:fork
1997:and
1971:All
1956:ntpd
1895:and
1459:GOOG
1435:USNO
1427:ACTS
1420:NIST
1416:NIST
1409:WWVH
1404:WWVH
1358:LORC
1303:WWVB
1298:WWVB
1290:IRIG
1253:GOES
1170:GNSS
1125:The
1106:SNTP
1092:SNTP
1086:8915
1062:5905
1043:1305
1012:1119
989:and
975:1059
931:Unix
915:Time
913:and
800:SNTP
530:and
467:for
455:The
365:IGMP
345:ICMP
303:QUIC
298:RSVP
293:SCTP
288:DCCP
253:XMPP
233:SNMP
228:SMTP
213:RTSP
188:OSPF
178:NNTP
173:MQTT
168:MGCP
163:LDAP
153:IMAP
138:HTTP
118:DHCP
84:1985
77:1985
57:5905
29:NNTP
5477:RFC
5467:doi
5450:RFC
5440:doi
5308:RFC
5290:doi
5006:RFC
4996:doi
3885:doi
3626:RFC
3608:doi
3399:RFC
3389:doi
3347:doi
3255:RFC
3237:doi
3201:RFC
3183:doi
3144:RFC
3126:doi
3098:778
3095:RFC
3085:doi
3038:RFC
3028:doi
2986:RFC
2976:doi
2934:RFC
2924:doi
2889:RFC
2879:doi
2849:958
2833:RFC
2823:doi
2784:RFC
2774:doi
2734:958
2731:RFC
2721:doi
2690:958
2674:RFC
2664:doi
2610:RFC
2592:doi
2290:TLS
2233:TLS
2118:of
1634:by
1451:MRS
1443:PTB
1397:WWV
1392:WWV
1385:CHU
1380:CHU
1370:TDF
1351:JJY
1346:JJY
1339:MSF
1334:MSF
1327:HBG
1322:HBG
1310:DCF
1282:PPS
1271:GAL
1261:GPS
1221:on.
1182:PTP
1174:GPS
1082:RFC
1058:RFC
1039:RFC
1008:RFC
983:956
979:RFC
971:RFC
956:958
952:RFC
927:781
923:RFC
900:778
896:RFC
849:MAC
609:RFC
573:or
561:or
498:of
461:NTP
410:MAC
405:PPP
395:ARP
360:ECN
355:NDP
283:UDP
278:TCP
238:SSH
223:SIP
218:RIP
208:RTP
198:PTP
193:POP
183:NTP
158:IRC
133:FTP
128:DNS
113:BGP
53:RFC
5567::
5475:.
5465:.
5448:.
5438:.
5379:.
5355:.
5331:.
5306:.
5298:.
5288:.
5284:.
5257:.
5208:.
5157:.
5153:.
5123:.
5090:.
5017:^
5004:.
4981:^
4787:.
4757:.
4732:.
4714:.
4696:.
4669:.
4643:.
4625:.
4621:.
4591:.
4564:.
4560:.
4535:.
4518:.
4499:.
4469:.
4465:.
4447:.
4431:.
4420:^
4411:.
4395:.
4378:.
4362:.
4358:.
4274:.
4249:.
4243:.
4213:.
4195:.
4191:.
4167:.
4141:.
4137:.
4112:.
4108:.
4078:.
4067:^
4021:.
3947:.
3930:.
3919:.
3907:^
3891:.
3820:.
3781:.
3762:.
3745:.
3741:.
3716:.
3712:.
3701:^
3683:.
3656:.
3652:.
3624:.
3616:.
3602:.
3578:.
3552:.
3541:^
3517:.
3485:.
3460:,
3444:^
3397:.
3353:.
3343:39
3341:.
3337:.
3307:,
3303:,
3253:.
3245:.
3235:.
3231:.
3199:.
3191:.
3181:.
3177:.
3163:^
3142:.
3134:.
3124:.
3120:.
3093:.
3083:.
3079:.
3036:.
3009:^
2984:.
2957:^
2932:.
2887:.
2860:^
2831:.
2782:.
2745:,
2729:.
2692:,
2672:.
2645:^
2632:,
2624:,
2608:.
2600:.
2586:.
2559:^
2502:^
2485:.
2472:^
2454:.
2422:^
2282:.
2235:,
2198:A
2100:.
1907:.
1168:,
1003:.
487:.
349:v6
338:v6
333:v4
328:IP
122:v6
23:,
5482:.
5469::
5455:.
5442::
5418:.
5365:.
5341:.
5313:.
5292::
5267:.
5223:.
5194:.
5168:.
5138:.
5109:.
5072:.
5040:.
5011:.
4998::
4975:.
4877:.
4850:.
4823:.
4798:.
4773:.
4743:.
4718:.
4700:.
4681:.
4655:.
4607:.
4576:.
4545:.
4481:.
4343:.
4312:.
4285:.
4260:.
4228:.
4177:.
4152:.
4123:.
4093:.
4061:.
4036:.
4007:.
3982:.
3951:.
3901:.
3887::
3856:.
3831:.
3793:.
3766:.
3727:.
3695:.
3631:.
3610::
3582:.
3563:.
3535:.
3503:.
3438:.
3404:.
3391::
3367:.
3349::
3260:.
3239::
3206:.
3185::
3149:.
3128::
3100:.
3087::
3043:.
3030::
2991:.
2978::
2939:.
2926::
2894:.
2881::
2838:.
2825::
2789:.
2776::
2736:.
2723::
2679:.
2666::
2615:.
2594::
2553:.
2528:.
2496:.
2466:.
2406:.
2385:.
2126:.
1897:δ
1893:θ
1886:θ
1870:2
1866:t
1862:=
1859:2
1855:/
1842:+
1837:3
1833:t
1810:1
1806:t
1802:=
1799:2
1795:/
1788:+
1782:+
1777:0
1773:t
1758:3
1755:t
1749:2
1746:t
1740:1
1737:t
1731:0
1728:t
1711:,
1707:)
1702:1
1698:t
1689:2
1685:t
1681:(
1675:)
1670:0
1666:t
1657:3
1653:t
1649:(
1645:=
1632:δ
1618:,
1613:2
1609:)
1604:3
1600:t
1591:2
1587:t
1583:(
1580:+
1577:)
1572:0
1568:t
1559:1
1555:t
1551:(
1545:=
1530:θ
1155:n
1151:n
1104:(
1080:(
600:.
459:(
444:e
437:t
430:v
351:)
347:(
144:)
124:)
120:(
86:)
31:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.