1015:
uniform distribution from a Galois field. If the field size is sufficiently large, the probability that the receiver(s) will obtain linearly independent combinations (and therefore obtain innovative information) approaches 1. It should however be noted that, although random linear network coding has excellent throughput performance, if a receiver obtains an insufficient number of packets, it is extremely unlikely that they can recover any of the original packets. This can be addressed by sending additional random linear combinations until the receiver obtains the appropriate number of packets.
1975:), then the expected number of linearly dependent packets per generation is practically zero. Since it is the last packets the major contributor to the overhead due to linear dependencies, there are RLNC-based protocols such as tunable sparse network coding that exploit this knowledge. These protocols introduce sparsity (zero-elements) in the coding coefficients at the beginning of the transmission to reduce the decoding complexity, and reduce the sparsity at the end of the transmission to reduce the overhead due to linear dependencies.
1132:
over traditional block codes is that it allows the recombination of previously coded packets into new and valid coded packets. This process is usually called recoding. After a recoding operation, the size of the appended coding coefficients does not change. Since all the operations are linear, the state of the recoded packet can be preserved by applying the same operations of addition and multiplication to the payload and the appended coding coefficients. In the following example, we will illustrate this process.
1124:). In the binary field, each element is one bit long, while in the binary-8, it is one byte long. Since the packet size is usually larger than the field size, each packet is seen as a set of elements from the Galois field (usually referred to as symbols) appended together. The packets have a fixed amount of symbols (Galois field elements), and since all the operations are performed over Galois fields, then the size of the packets does not change with subsequent linear combinations.
1744:
1704:
987:
5247:
2023:
together with the coded packets, a source can achieve bundling without much planning just by sending coded packets through all its network interfaces. The destination can decode the information once enough coded packets arrive, irrespectively of the network interface. A video demonstrating the channel bundling capabilities of RLNC is available at.
1185:
2495:
1997:
traffic in terms of delay, packet loss, and jitter over wireless networks prone to packet erasures can be improved with RLNC. In the case of audio streaming over wireless mesh networks, the packet delivery ratio, latency, and jitter performance of the network can be significantly increased when using
1645:
coding coefficients. The size of each coefficient is the number of bits needed to represent one element of the Galois field. In practice, most network coding applications use a generation size of no more than 32 packets per generation and Galois fields of 256 elements (binary-8). With these numbers,
1131:
To preserve the statelessness of the code, the coding coefficients used to generate the coded packets are appended to the packets transmitted over the network. Therefore, each node in the network can see what coefficients were used to generate each coded packet. One novelty of linear network coding
1044:
packets form a block, usually called a generation. The number of original packets combined and recombined together is the generation size. The second parameter is the packet size. Usually, the size of the original packets is fixed. In the case of unequally-sized packets, these can be zero-padded if
1127:
The sources and the intermediate nodes can combine any subset of the original and previously coded packets performing linear operations. To form a coded packet in RLNC, the original and previously coded packets are multiplied by randomly chosen coefficients and added together. Since each packet is
1014:
Random linear network coding (RLNC) is a simple yet powerful encoding scheme, which in broadcast transmission schemes allows close to optimal throughput using a decentralized algorithm. Nodes transmit random linear combinations of the packets they receive, with coefficients chosen randomly, with a
1624:
It is usually thought that the transmission overhead of network coding is high due to the need to append the coding coefficients to each coded packet. In reality, this overhead is negligible in most applications. The overhead due to coding coefficients can be computed as follows. Each packet has
1001:
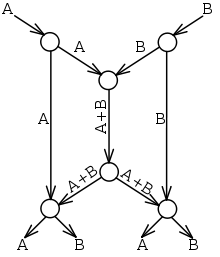
If only routing were allowed, then the central link would be only able to carry A or B, but not both. Supposing we send A through the center; then the left destination would receive A twice and not know B at all. Sending B poses a similar problem for the right destination. We say that routing is
998:. Two source nodes (at the top of the picture) have information A and B that must be transmitted to the two destination nodes (at the bottom). Each destination node wants to know both A and B. Each edge can carry only a single value (we can think of an edge transmitting a bit in each time slot).
1754:
Since the coding coefficients are chosen randomly in RLNC, there is a chance that some transmitted coded packets are not beneficial to the destination because they are formed using a linearly dependent combination of packets. However, this overhead is negligible in most applications. The linear
2022:
Channel bundling: Due to the statelessness characteristics of RLNC, it can be used to efficiently perform channel bundling, i.e., the transmission of information through multiple network interfaces. Since the coded packets are randomly generated, and the state of the code traverses the network
1188:
Coding and recoding process in linear network coding. Each packet is seen as a set of elements from a Galois field. Therefore, multiplying and adding two packets means multiplying each of its symbols by a coding coefficient chosen from the Galois field and then adding the two packets together,
1005:
Using a simple code, as shown, A and B can be transmitted to both destinations simultaneously by sending the sum of the symbols through the two relay nodes – encoding A and B using the formula "A+B". The left destination receives A and A + B, and can calculate B by subtracting the two values.
1135:
Any destination node must collect enough linearly independent coded packets to be able to reconstruct the original data. Each coded packet can be understood as a linear equation where the coefficients are known since they are appended to the packet. In these equations, each of the original
1023:
There are three key parameters in RLNC. The first one is the generation size. In RLNC, the original data transmitted over the network is divided into packets. The source and intermediate nodes in the network can combine and recombine the set of original and coded packets. The original
1998:
RLNC instead of packet forwarding-based protocols such as simplified multicast forwarding and partial dominant pruning. The performance improvements of network coding for video conferencing are not only theoretical. In 2016, the authors of built a real-world testbed of 15 wireless
1617:
instructions enabled, the decoding goodput of network coding was 750 MB/s for a generation size of 16 packets and 250 MB/s for a generation size of 64 packets. Furthermore, today's algorithms can be vastly parallelizable, increasing the encoding and decoding goodput even further.
2002:
devices to evaluate the feasibility of network-coding-based video conference systems. Their results showed large improvements in packet delivery ratio and overall user experience, especially over poor quality links compared to multicasting technologies based on packet
4134:
2103:.: Linear network coding can improve the network efficiency of information-centric networking solutions by exploiting the multi-source multi-cast nature of such systems. It has been shown, that RLNC can be integrated into distributed content delivery networks such as
1815:
degrees of freedom, and then almost any coded packet will be useful and innovative. In fact, only the zero-packet (only zeroes in the coding coefficients) will be non-innovative. The probability of generating the zero-packet is equal to the probability of each of the
2014:
wireless networks can benefit from network coding. Researchers showed that network coding and its channel bundling capabilities improved the performance of SD-WANs with a large number of nodes with multiple cellular connections. Nowadays, companies such as
3467:
Noor-A-Rahim, Md; Liu, Zilong; Lee, Haeyoung; Khyam, M. Omar; He, Jianhua; Pesch, Dirk; Moessner, Klaus; Saad, Walid; Poor, H. Vincent (2022-05-01). "6G for
Vehicle-to-Everything (V2X) Communications: Enabling Technologies, Challenges, and Opportunities".
1949:), the expected number of linearly dependent packets per generation is of 1.6 extra packets. If our generation size if of 32 or 64 packets, this represents an overhead of 5% or 2.5%, respectively. If we use the binary-8 field (
966:
was proposed to find such paths in polynomial time. Then, Edmonds proved in the paper "Edge-Disjoint
Branchings" the upper bound in the broadcast scenario is also achievable, and proposed a polynomial time algorithm.
1128:
just an appended set of Galois field elements, the operations of multiplication and addition are performed symbol-wise over each of the individual symbols of the packets, as shown in the picture from the example.
3268:
Torres Vega, Maria; Liaskos, Christos; Abadal, Sergi; Papapetrou, Evangelos; Jain, Akshay; Mouhouche, Belkacem; Kalem, Gökhan; Ergüt, Salih; Mach, Marian; Sabol, Tomas; Cabellos-Aparicio, Albert (October 2020).
1331:, which means that they are constructed by a linear combination of zero times one of the packets plus one time the other packet. Any coded packet would have appended other coefficients. In our example, packet
1606:
Linear network coding is still a relatively new subject. However, the topic has been vastly researched over the last twenty years. Nevertheless, there are still some misconceptions that are no longer valid:
1053:. The third key parameter is the Galois field used. In practice, the most commonly used Galois fields are binary extension fields. And the most commonly used sizes for the Galois fields are the binary field
1755:
dependencies depend on the Galois fields' size and are practically independent of the generation size used. We can illustrate this with the following example. Let us assume we are using a Galois field of
5224:
Ali
Farzamnia, Sharifah K. Syed-Yusof, Norsheila Fisa "Multicasting Multiple Description Coding Using p-Cycle Network Coding", KSII Transactions on Internet and Information Systems, Vol 7, No 12, 2013.
1006:
Similarly, the right destination will receive B and A + B, and will also be able to determine both A and B. Therefore, with network coding, it takes only three time slots and improves the throughput.
452:
1739:
and a generation size of 16 packets. At the beginning of the transmission, the linear dependencies are minimal. It is the last packet of the transmission that is more likely to be linearly dependent.
3692:
1983:
Over the years, multiple researchers and companies have integrated network coding solutions into their applications. We can list some of the applications of network coding in different areas:
978:
ideas. Ahlswede et al. proved that it can be achieved if additional computing tasks (incoming packets are combined into one or several outgoing packets) can be done in the intermediate nodes.
1598:. Then, it will add the results symbol-wise to produce the new coded data. It will perform the same operations of multiplication and addition to the coding coefficients of the coded packets.
1002:
insufficient because no routing scheme can transmit both A and B to both destinations simultaneously. Meanwhile, it takes four time slots in total for both destination nodes to know A and B.
1923:. We can use this knowledge to calculate the expected number of linearly dependent packets per generation. In the worst-case scenario, when the Galois field used contains only two elements (
1399:. Since network coding can be applied at any layter of the communication protocol, these packets can have a header from the other layers, which is ignored in the network coding operations.
4205:. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering. Vol. 256. Cham: Springer International Publishing. pp. 68–77.
1870:. With each successive innovative transmission, it can be shown that the exponent of the probability of a non innovative packet is reduced by one. When the destination has received
748:
75:
is enough to achieve the upper bound in multicast problems with one source. However linear coding is not sufficient in general; even for more general versions of linearity such as
4548:
INFOCOM 2008. 27th IEEE International
Conference on Computer Communications, Joint Conference of the IEEE Computer and Communications Societies, 13–18 April 2008, Phoenix, AZ, USA
370:
1868:
1698:
1921:
292:
612:
1613:
Network coding decoders have been improved over the years. Nowadays, the algorithms are highly efficient and parallelizable. In 2016, with Intel Core i5 processors with
1122:
644:
585:
526:
487:
204:
1267:) appended. The appended coefficients can take any value from the Galois field. However, an original, uncoded data packet would have appended the coding coefficients
1265:
942:
863:
690:
1973:
1737:
1595:
1546:
1497:
1468:
1083:
553:
319:
234:
5314:
4132:, Buga, Wladyslaw Jan & Trent, Tracy Raymond, "Systems and methods for prioritizing wireless communication of aircraft", issued 2013-03-19
3738:
2547:
1947:
1894:
3583:
Dammak, Marwa; Andriyanova, Iryna; Boujelben, Yassine; Sellami, Noura (2018-03-29). "Routing and
Network Coding over a Cyclic Network for Online Video Gaming".
1834:
1813:
1793:
1773:
1643:
1567:
1518:
1440:
1420:
1350:
1234:
1212:
1174:
1154:
1042:
903:
883:
828:
808:
788:
768:
157:
137:
117:
1397:
1329:
1297:
528:. Since operations are computed in a finite field, the generated message is of the same length as the original messages. Each node forwards the computed value
1990:: The performance of streaming services such as VoIP over wireless mesh networks can be improved with network coding by reducing the network delay and jitter.
4783:
4667:
Krigslund, Jeppe; Hansen, Jonas; Hundeboll, Martin; Lucani, Daniel E.; Fitzek, Frank H. P. (2013). "CORE: COPE with MORE in
Wireless Meshed Networks".
3604:
Lajtha, Balázs; Biczók, Gergely; Szabó, Róbert (2010). "Enabling P2P Gaming with
Network Coding". In Aagesen, Finn Arve; Knapskog, Svein Johan (eds.).
2192:
2165:
Wireless broadcast: RLNC can reduce the number of packet transmission for a single-hop wireless multicast network, and hence improve network bandwidth
4297:
Darif, Anouar; Chaibi, Hasna; Saadane, Rachid (2020). Ben Ahmed, Mohamed; Boudhir, Anouar
Abdelhakim; Santos, Domingos; El Aroussi, Mohamed (eds.).
3656:
Lajtha, Balázs; Biczók, Gergely; Szabó, Róbert (2010). Aagesen, Finn Arve; Knapskog, Svein Johan (eds.). "Enabling P2P Gaming with
Network Coding".
2238:
1193:
In the figure, we can see an example of two packets linearly combined into a new coded packet. In the example, we have two packets, namely packet
5368:
5093:
5051:
5006:
4729:
4684:
4643:
4427:
4318:
4273:
4218:
4173:
4066:
3997:
3885:
3840:
3714:
3675:
3623:
3510:
3347:
3187:
3063:
2961:
2916:
2868:
2789:
2741:
2693:
2624:
2518:
2234:
5269:
2988:
2648:
4761:
1896:
innovative packets (i.e., it needs only one more packet to fully decode the data). Then the probability of a non innovative packet is of
2494:
Sørensen, Chres W.; Paramanathan, Achuthan; Cabrera, Juan A.; Pedersen, Morten V.; Lucani, Daniel E.; Fitzek, Frank H.P. (April 2016).
1700:
bytes of appended overhead. If each packet is 1500 bytes long (i.e. the
Ethernet MTU), then 32 bytes represent an overhead of only 2%.
2305:
Li, C. T. (2023). "Undecidability of Network Coding, Conditional Information Inequalities, and Conditional Independence Implication".
5295:
4803:
4493:
1614:
649:
Sink nodes receive these network coded messages, and collect them in a matrix. The original messages can be recovered by performing
5119:"A Two-Level Game Theory Approach for Joint Relay Selection and Resource Allocation in Network Coding Assisted D2D Communications"
3166:
Gabriel, Frank; Nguyen, Giang T.; Schmoll, Robert-Steve; Cabrera, Juan A.; Muehleisen, Maciej; Fitzek, Frank H.P. (January 2018).
2019:
are employing RLNC-based solutions due to their advantages in low latency, small footprint on computing devices, and low overhead.
5409:
2038:
1836:
coding coefficient to be equal to the zero-element of the Galois field. I.e., the probability of a non-innovative packet is of
378:
5357:
5309:
4305:. Lecture Notes in Intelligent Transportation and Infrastructure. Cham: Springer International Publishing. pp. 663–674.
2096:
3870:
2017 IEEE International Workshop of Electronics, Control, Measurement, Signals and their Application to Mechatronics (ECMSM)
4628:
Proceedings of the 2006 conference on Applications, technologies, architectures, and protocols for computer communications
2352:
159:
sink nodes. Each node generates new packets which are linear combinations of past received packets by multiplying them by
963:
5404:
2072:
1045:
they are shorter or split into multiple packets if they are longer. In practice, the packet size can be the size of the
2586:
83:. Finding optimal coding solutions for general network problems with arbitrary demands is a hard problem, which can be
5394:
3536:"Instantly decodable network coding–assisted data dissemination for prioritized services in vehicular ad hoc networks"
2042:
5277:
5273:
5257:
3660:. Lecture Notes in Computer Science. Vol. 6164. Berlin, Heidelberg: Springer Berlin Heidelberg. pp. 76–86.
2895:
Rachuri, Sri Pramodh; Ansari, Ahtisham Ali; Tandur, Deepaknath; Kherani, Arzad A.; Chouksey, Sameer (December 2019).
5345:
2470:
4875:
Firooz, Mohammad Hamed; Roy, Sumit (24 March 2012). "Data Dissemination in Wireless Networks with Network Coding".
4154:"An Attribute & Network Coding-Based Secure Multicast Protocol for Firmware Updates in Smart Grid AMI Networks"
2104:
1999:
1747:
The expected number of linearly dependent packets per generation is practically independent of the generation size.
4090:
Camilli, Alberto; Cugnasca, Carlos E.; Saraiva, Antonio M.; Hirakawa, André R.; Corrêa, Pedro L. P. (2007-08-01).
3042:
Pedersen, Morten V.; Lucani, Daniel E.; Fitzek, Frank H. P.; Sorensen, Chres W.; Badr, Arash S. (September 2013).
2678:
2010 7th International Symposium on Communication Systems, Networks & Digital Signal Processing (CSNDSP 2010)
2197:
2160:
2034:
1046:
2115:
2111:
959:
906:
5363:
4021:
3864:
Peralta, Goiuri; Iglesias-Urkia, Markel; Barcelo, Marc; Gomez, Raul; Moran, Adrian; Bilbao, Josu (May 2017).
2548:"Network Coding in Heterogeneous Multicore IoT Nodes With DAG Scheduling of Parallel Matrix Block Operations"
3911:"On the Combination of Multi-Cloud and Network Coding for Cost-Efficient Storage in Industrial Applications"
2187:
705:
5069:"Network coding schemes for Device-to-Device communications based relaying for cellular coverage extension"
2146:
2142:
1237:. The generation size of our example is two. We know this because each packet has two coding coefficients (
5399:
5389:
5032:"Physical Layer Network Coding Aided Two-Way Device-to-Device Communication Underlaying Cellular Networks"
4928:
Fiandrotti, Attilio; Bioglio, Valerio; Grangetto, Marco; Gaeta, Rossano; Magli, Enrico (11 October 2013).
4839:
4248:
2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC)
3754:"A Cloud-Assisted Random Linear Network Coding Medium Access Control Protocol for Healthcare Applications"
2435:
2150:
2649:"Coding the Network: Next Generation Coding for Flexible Network Operation | IEEE Communications Society"
324:
4619:
Katti, Sachin; Rahul, Hariharan; Hu, Wenjun; Katabi, Dina; Médard, Muriel; Crowcroft, Jon (2006-08-11).
3016:"Barracuda Networks optimizes SD-WAN traffic with patented erasure correction technology from Steinwurf"
2100:
2033:
standard to improve the performance of video delivery over 5G systems. In 2018, a demo presented at the
1839:
80:
5339:
5077:
2015 IEEE 16th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC)
4091:
4372:
3922:
3765:
2132:
1649:
650:
76:
4844:
4570:
3825:
2010 IEEE 21st International Symposium on Personal, Indoor and Mobile Radio Communications Workshops
2440:
2123:
1899:
243:
5068:
4353:
Bilal, Muhammad; et al. (2019). "Network-Coding Approach for Information-Centric Networking".
3608:. Lecture Notes in Computer Science. Vol. 6164. Berlin, Heidelberg: Springer. pp. 76–86.
2940:
Ansari, Ahtisham Ali; Rachuri, Sri Pramodh; Kherani, Arzad A.; Tandur, Deepaknath (December 2019).
590:
88:
38:
is a program in which intermediate nodes transmit data from source nodes to sink nodes by means of
31:
5332:
4830:
Dong Nguyen; Tuan Tran; Thinh Nguyen; Bose, B. (2009). "Wireless Broadcast Using Network Coding".
2603:
Feizi, Soheil; Lucani, Daniel E.; Sørensen, Chres W.; Makhdoumi, Ali; Médard, Muriel (June 2014).
2403:
Any receiver can then recover the source vectors using Gaussian elimination on the vectors in its
974:
scenario is more complicated, and in fact, such an upper bound can't be reached using traditional
5198:
5149:
5099:
5012:
4967:
4941:
4910:
4884:
4857:
4809:
4735:
4690:
4649:
4599:
4499:
4452:
4433:
4388:
4362:
4324:
4279:
4224:
4179:
4072:
4003:
3891:
3846:
3732:
3645:(phdthesis thesis). Université de Cergy Pontoise; École nationale d'ingénieurs de Sfax (Tunisie).
3584:
3565:
3516:
3469:
3449:
3400:
3353:
3332:
2017 6th International Conference on Space Mission Challenges for Information Technology (SMC-IT)
3308:
3250:
3224:
3193:
3125:
3069:
2967:
2922:
2874:
2817:
2795:
2747:
2699:
2630:
2578:
2524:
2379:
2361:
2332:
2314:
2287:
2016:
2011:
945:
39:
4710:"An Analysis of Wireless Network Coding for Unicast Sessions: The Case for Coding-Aware Routing"
4198:
2045:
technologies to improve video quality against packet loss due to congestion at the core network.
1156:
packets is the unknown. To solve the linear system of equations, the destination needs at least
4244:"Physical-layer network coding with multiple antennas: An enabling technology for smart cities"
4022:"DLR - Institute of Communications and Navigation - NEXT - Network Coding Satellite Experiment"
2350:
Kühne, L.; Yashfe, G. (2022). "Representability of Matroids by c-Arrangements is Undecidable".
2128:
Protection against network attacks such as snooping, eavesdropping, replay, or data corruption.
2119:
1088:
653:
on the matrix. In reduced row echelon form, decoded packets correspond to the rows of the form
617:
558:
492:
460:
170:
5326:
5190:
5141:
5089:
5047:
5002:
4959:
4902:
4799:
4753:
4725:
4680:
4639:
4543:
4489:
4423:
4314:
4269:
4214:
4169:
4111:
4062:
3993:
3958:
3940:
3881:
3836:
3801:
3783:
3720:
3710:
3671:
3619:
3557:
3506:
3441:
3392:
3343:
3300:
3242:
3183:
3145:
3059:
3044:"Network coding designs suited for the real world: What works, what doesn't, what's promising"
2957:
2912:
2864:
2818:"NCVCS: Network-coding-based video conference system for mobile devices in multicast networks"
2785:
2737:
2689:
2620:
2570:
2514:
2051:
57:
packets and combine for transmission. This process may be used to attain the maximum possible
50:
4092:"From wireless sensors to field mapping: Anatomy of an application for precision agriculture"
2946:
2019 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS)
2237:), in IEEE Transactions on Information Theory, Vol. 51, No. 8, pp. 2745-2759, August 2005 (
5226:
5180:
5133:
5081:
5039:
4994:
4951:
4894:
4849:
4791:
4788:
Proceedings IEEE INFOCOM 2006. 25TH IEEE International Conference on Computer Communications
4717:
4672:
4631:
4551:
4481:
4415:
4406:
Zimmermann, Sandra; Rischke, Justus; Cabrera, Juan A.; Fitzek, Frank H. P. (December 2020).
4380:
4306:
4299:"Network Coding for Energy Optimization of SWIMAC in Smart Cities Using WSN Based on IR-UWB"
4259:
4251:
4206:
4161:
4103:
4054:
3985:
3948:
3930:
3873:
3828:
3791:
3773:
3702:
3661:
3609:
3547:
3498:
3431:
3384:
3335:
3290:
3282:
3234:
3175:
3135:
3051:
2949:
2904:
2856:
2829:
2777:
2729:
2681:
2612:
2562:
2506:
2478:
2463:
2445:
2371:
2324:
2279:
2174:
1402:
Now, lets assume that the network node wants to produce a new coded packet combining packet
1240:
912:
833:
656:
4544:"An efficient signature-based scheme for securing network coding against pollution attacks"
2546:
Wunderlich, Simon; Cabrera, Juan A.; Fitzek, Frank H. P.; Reisslein, Martin (August 2017).
2267:
1952:
1710:
1707:
Expected linearly dependent packets at different stages of transmission for a Galois field
1573:
1524:
1475:
1446:
1056:
994:
The butterfly network is often used to illustrate how linear network coding can outperform
531:
297:
212:
5358:
https://web.archive.org/web/20081011124616/http://arena.cse.sc.edu/papers/rocx.secon06.pdf
5075:
3909:
Peralta, Goiuri; Garrido, Pablo; Bilbao, Josu; Agüero, Ramón; Crespo, Pedro (2019-04-08).
2474:
2423:
1743:
4930:"Band Codes for Energy-Efficient Network Coding With Application to P2P Mobile Streaming"
4630:. SIGCOMM '06. New York, NY, USA: Association for Computing Machinery. pp. 243–254.
3752:
Kartsakli, Elli; Antonopoulos, Angelos; Alonso, Luis; Verikoukis, Christos (2014-03-10).
1926:
1873:
1049:(MTU) of the underlying network protocol. For example, it can be around 1500 bytes in an
4376:
4298:
4053:. ICEEL 2018. New York, NY, USA: Association for Computing Machinery. pp. 212–216.
3926:
3769:
954:
proved that there is always a set of edge-disjoint paths achieving the upper bound in a
4987:"Network coding in device-to-device (D2D) communications underlaying cellular networks"
4419:
3953:
3910:
3796:
3753:
3691:
Ilyas, Mohammad; Alwakeel, Sami S.; Alwakeel, Mohammed M.; Aggoune, el-Hadi M. (2014).
3270:
2230:
2060:
1819:
1798:
1778:
1758:
1628:
1552:
1503:
1425:
1405:
1335:
1219:
1197:
1159:
1139:
1050:
1027:
888:
868:
813:
793:
773:
753:
700:
142:
122:
102:
65:
1703:
1356:
1302:
1270:
5383:
4898:
4653:
4620:
4437:
4328:
4149:
4007:
3569:
3491:"Network Coding scheme behavior in a Vehicle-to-Vehicle safety message dissemination"
3372:
3312:
2971:
2926:
2685:
2532:
2397:
Chou, Philip A.; Wu, Yunnan; Jain, Kamal (October 2003). "Practical network coding".
2383:
2336:
1987:
948:, which is the sum of the capacities of the edges on a cut, between these two nodes.
45:
Linear network coding may be used to improve a network's throughput, efficiency, and
5214:
Fragouli, C.; Le Boudec, J. & Widmer, J. "Network coding: An instant primer" in
5202:
5169:"User-specific link adaptation scheme for device-to-device network coding multicast"
5153:
5016:
4971:
4861:
4503:
4392:
4228:
4183:
4076:
3895:
3850:
3520:
3404:
3371:
Jamil, Farhan; Javaid, Anam; Umer, Tariq; Rehmani, Mubashir Husain (November 2017).
3015:
2634:
2582:
2528:
5103:
4739:
4694:
4676:
4129:
3453:
3357:
3254:
3197:
2953:
2908:
2878:
2799:
2751:
2703:
2291:
2154:
164:
61:
5118:
4813:
4283:
4047:"Implementation of Agricultural Monitoring System Based on the Internet of Things"
3984:. IoT 2019. New York, NY, USA: Association for Computing Machinery. pp. 1–4.
3271:"Immersive Interconnected Virtual and Augmented Reality: A 5G and IoT Perspective"
3168:"Practical deployment of network coding for real-time applications in 5G networks"
3073:
2942:"An SD-WAN Controller for Delay Jitter Minimization in Coded Multi-access Systems"
2674:"VoIP design and implementation with network coding schemes for wireless networks"
2217:
5346:
https://web.archive.org/web/20060618083034/http://www.mit.edu/~medard/coding1.htm
4914:
4714:
IEEE INFOCOM 2007 - 26th IEEE International Conference on Computer Communications
4310:
4158:
2017 26th International Conference on Computer Communication and Networks (ICCCN)
4107:
2768:
Saeed, Basil; Lung, Chung-Horng; Kunz, Thomas; Srinivasan, Anand (October 2011).
2733:
5331:
Christina Fragouli et al., Network Coding: An Instant Primer, ACM SIGCOMM 2006,
5043:
4485:
4210:
4051:
Proceedings of the 2018 2nd International Conference on Education and E-Learning
3832:
3666:
3640:
3614:
3172:
2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC)
3112:
Vukobratovic, Dejan; Tassi, Andrea; Delic, Savo; Khirallah, Chadi (April 2018).
2833:
2616:
986:
951:
160:
72:
58:
46:
5085:
5031:
4986:
4929:
4709:
4473:
4407:
4384:
4255:
4243:
4199:"A Smart Meter Firmware Update Strategy Through Network Coding for AMI Network"
4165:
4153:
3877:
3865:
3820:
3490:
3327:
3286:
3212:
3211:
Magli, Enrico; Wang, Mea; Frossard, Pascal; Markopoulou, Athina (August 2013).
3167:
3043:
2941:
2896:
2848:
2769:
2721:
2673:
2604:
2220:), in IEEE Transactions on Information Theory, Vol 49, No. 2, pp. 371–381, 2003
2066:
Gaming applications such as low latency streaming and multiplayer connectivity.
5320:
5185:
5168:
5167:
Zhou, Ting; Xu, Bin; Xu, Tianheng; Hu, Honglin; Xiong, Lei (1 February 2015).
4598:
Dimakis, Alexandros (2007). "Network Coding for Distributed Storage Systems".
4201:. In Pathan, Al-Sakib Khan; Fadlullah, Zubair Md.; Guerroumi, Mohamed (eds.).
3502:
3495:
2017 IEEE International Conference on Communications Workshops (ICC Workshops)
3436:
3419:
3388:
3179:
3087:
2901:
2019 International Conference on contemporary Computing and Informatics (IC3I)
2860:
2566:
2510:
2482:
2375:
2233:, and K. Zeger, "Insufficiency of Linear Coding in Network Information Flow" (
2090:
17:
5230:
5194:
5145:
5137:
4998:
4963:
4955:
4906:
4795:
4555:
4115:
3944:
3787:
3724:
3561:
3552:
3535:
3489:
Achour, Imen; Bejaoui, Tarek; Busson, Anthony; Tabbane, Sami (October 2017).
3445:
3396:
3304:
3246:
3238:
3149:
3055:
2989:"Steinwurf's next-gen FECs aren't a choice for SD-WAN, they're an imperative"
2574:
2328:
1795:
packets. If the destination has not received any coded packet, we say it has
4853:
4721:
4635:
4058:
3989:
2781:
2283:
971:
3962:
3805:
3339:
1184:
5219:
4517:
4046:
3977:
3976:
Zverev, Mihail; Agüero, Ramón; Garrido, Pablo; Bilbao, Josu (2019-10-22).
3819:
Taparugssanagorn, Attaphongse; Ono, Fumie; Kohno, Ryuji (September 2010).
3696:
3328:"Simulation Environment for Network Coding Research in Ring Road Networks"
3982:
Proceedings of the 9th International Conference on the Internet of Things
3658:
Networked Services and Applications - Engineering, Control and Management
3606:
Networked Services and Applications - Engineering, Control and Management
2467:
237:
5374:
5319:
Raymond W. Yeung, Information Theory and Network Coding, Springer 2008,
3140:
3113:
2770:"Audio streaming for ad hoc wireless mesh networks using network coding"
2722:"A survey on MPEG-4 streaming using network coding in wireless networks"
4985:
Wu, Yue; Liu, Wuling; Wang, Siyi; Guo, Weisi; Chu, Xiaoli (June 2015).
4571:"How Good is Random Linear Coding Based Distributed Networked Storage?"
4264:
3778:
3373:"A comprehensive survey of network coding in vehicular ad-hoc networks"
3326:
De Jonckere, Olivier; Chorin, Jean; Feldmann, Marius (September 2017).
3295:
2726:
2012 Nirma University International Conference on Engineering (NUiCONE)
2426:; N. Cai; S.-Y. R. Li; R. W. Yeung (2000). "Network Information Flow".
995:
975:
955:
84:
5351:
5325:
Raymond W. Yeung et al., Network Coding Theory, now Publishers, 2005,
4197:
Jalil, Syed Qaisar; Chalup, Stephan; Rehmani, Mubashir Husain (2019).
3935:
3706:
3420:"Vehicular communications: emergency video streams and network coding"
2496:"Leaner and meaner: Network coding in SIMD enabled commercial devices"
2449:
2007:
1994:
5340:
http://research.microsoft.com/en-us/projects/avalanche/default.aspx
5276:
external links, and converting useful links where appropriate into
4604:
4367:
3589:
3474:
3130:
2366:
2319:
4946:
4889:
4457:
4242:
Kumar, Vaibhav; Cardiff, Barry; Flanagan, Mark F. (October 2017).
3229:
2030:
985:
4569:
Acedański, Szymon; Deb, Supratim; Médard, Muriel; Koetter, Ralf.
4542:
Yu, Zhen; Wei, Yawen; Ramkumar, Bhuvaneswari; Guan, Yong (2008).
4348:
4346:
4344:
5117:
Gao, Chuhan; Li, Yong; Zhao, Yulei; Chen, Sheng (October 2017).
2897:"Network-Coded SD-WAN in Multi-Access Systems for Delay Control"
2087:
Major security and firmware updates for mobile product families.
5333:
http://infoscience.epfl.ch/getfile.py?mode=best&recid=58339
4480:. Vol. 4. Melbourne, Australia: IEEE. pp. 2052–2057.
3866:"Fog computing based efficient IoT scheme for the Industry 4.0"
2118:
in traditional and wireless networks with packet loss, such as
2107:
to increase data availability while reducing storage resources.
1993:
Video and audio streaming and conferencing: The performance of
5240:
4045:
Hsu, Hsiao-Tzu; Wang, Tzu-Ming; Kuo, Yuan-Cheng (2018-11-05).
2253:
Complexity classification of network information flow problems
3821:"Network coding for non-invasive Wireless Body Area Networks"
2849:"Wireless Multi-party video conferencing with network coding"
2468:"The Benefits of Coding over Routing in a Randomized Setting"
1500:
in the example. The node will multiply each symbol of packet
4518:"Welcome to Network Coding Security - Secure Network Coding"
2816:
Wang, Lei; Yang, Zhen; Xu, Lijie; Yang, Yuwang (July 2016).
2477:
in 2003 IEEE International Symposium on Information Theory.
2399:
Allerton Conference on Communication, Control, and Computing
1442:. In RLNC, it will randomly choose two coding coefficients,
711:
5327:
http://iest2.ie.cuhk.edu.hk/~whyeung/netcode/monograph.html
4669:
2013 IEEE 77th Vehicular Technology Conference (VTC Spring)
4408:"Journey to MARS: Interplanetary Coding for relieving CDNS"
3114:"Random Linear Network Coding for 5G Mobile Video Delivery"
2503:
2016 IEEE Wireless Communications and Networking Conference
2026:
4991:
2015 IEEE International Conference on Communications (ICC)
4412:
GLOBECOM 2020 - 2020 IEEE Global Communications Conference
2672:
Lopetegui, I.; Carrasco, R.A.; Boussakta, S. (July 2010).
2853:
2009 IEEE International Conference on Multimedia and Expo
2847:
Wang, Hui; Chang, Ronald Y.; Kuo, C.-C. Jay (June 2009).
447:{\displaystyle X_{k}=\sum _{i=1}^{S}g_{k}^{i}\cdot M_{i}}
5265:
5260:
may not follow Knowledge (XXG)'s policies or guidelines
3534:
Wang, Shujuan; Lu, Shuguang; Zhang, Qian (April 2019).
3418:
Park, Joon-Sang; Lee, Uichin; Gerla, Mario (May 2010).
2609:
2014 International Symposium on Network Coding (NetCod)
2159:
Buffer and delay reduction in spatial sensor networks:
3872:. Donostia, San Sebastian, Spain: IEEE. pp. 1–6.
3642:
Network coding application for online games platformes
2605:"Tunable sparse network coding for multicast networks"
49:, as well as reducing attacks and eavesdropping. The
5036:
2015 IEEE Global Communications Conference (GLOBECOM)
4708:
Sengupta, S.; Rayanchu, S.; Banerjee, S. (May 2007).
2216:
S. Li, R. Yeung, and N. Cai, "Linear Network Coding"(
2141:
Throughput increase in wireless mesh networks, e.g.:
2131:
Digital file distribution and P2P file sharing, e.g.
1955:
1929:
1902:
1876:
1842:
1822:
1801:
1781:
1761:
1713:
1652:
1631:
1576:
1555:
1527:
1506:
1478:
1449:
1428:
1408:
1359:
1338:
1305:
1273:
1243:
1222:
1200:
1162:
1142:
1091:
1059:
1030:
915:
891:
871:
836:
816:
796:
776:
756:
708:
659:
620:
593:
561:
534:
495:
463:
381:
327:
300:
246:
215:
173:
145:
125:
105:
99:
In a linear network coding problem, a group of nodes
5373:
Coding-aware protocol design for wireless networks:
5067:
Abrardo, Andrea; Fodor, Gábor; Tola, Besmir (2015).
3540:
International Journal of Distributed Sensor Networks
3089:
Channel Bundling Using Random Linear Network Coding
4303:Innovations in Smart Cities Applications Edition 3
3978:"Network Coding for IIoT Multi-Cloud Environments"
2029:private networks: RLNC can be integrated into the
1967:
1941:
1915:
1888:
1862:
1828:
1807:
1787:
1767:
1731:
1692:
1637:
1589:
1561:
1540:
1512:
1491:
1462:
1434:
1414:
1391:
1344:
1323:
1291:
1259:
1228:
1206:
1168:
1148:
1116:
1077:
1036:
936:
897:
877:
857:
822:
802:
782:
762:
742:
684:
638:
606:
579:
547:
520:
481:
446:
364:
313:
286:
228:
198:
151:
131:
111:
5030:Zhao, Yulei; Li, Yong; Ge, Ning (December 2015).
2037:demonstrated a practical deployment of RLNC with
321:from the linear combination of received messages
4784:"Looking at Large Networks: Coding vs. Queueing"
3693:"Exploiting Network Coding for Smart Healthcare"
944:is upper bounded by the minimum capacity of all
4451:Kim, Minji (2012). "Network Coded TCP (CTCP)".
2680:. Newcastle upon Tyne: IEEE. pp. 857–861.
2266:Langberg, M.; Sprintson, A.; Bruck, J. (2006).
2171:Low-complexity video streaming to mobile device
4478:2006 IEEE 63rd Vehicular Technology Conference
4148:Tonyali, Samet; Akkaya, Kemal; Saputro, Nico;
2903:. Singapore, Singapore: IEEE. pp. 32–37.
2418:
2416:
5369:Network coding: Networking's next revolution?
4160:. Vancouver, BC, Canada: IEEE. pp. 1–9.
3424:Journal of Internet Services and Applications
3334:. Alcala de Henares: IEEE. pp. 128–131.
2720:Shrimali, R.; Narmawala, Z. (December 2012).
865:be the maximum possible throughput from node
790:is the set of directed links (or edges), and
8:
342:
328:
5321:http://iest2.ie.cuhk.edu.hk/~whyeung/book2/
3698:Sensor networks for sustainable development
3213:"Network Coding Meets Multimedia: A Review"
3048:2013 IEEE Information Theory Workshop (ITW)
2268:"The encoding complexity of network coding"
1353:for instance has appended the coefficients
4098:. Precision Agriculture in Latin America.
3737:: CS1 maint: location missing publisher (
1176:linearly independent equations (packets).
5296:Learn how and when to remove this message
5184:
4945:
4888:
4843:
4832:IEEE Transactions on Vehicular Technology
4782:Bhadra, S.; Shakkottai, S. (April 2006).
4603:
4456:
4366:
4263:
3952:
3934:
3795:
3777:
3665:
3613:
3588:
3551:
3497:. Paris, France: IEEE. pp. 441–446.
3473:
3435:
3294:
3275:Journal of Network and Systems Management
3228:
3139:
3129:
2439:
2365:
2318:
2193:Homomorphic signatures for network coding
1954:
1928:
1903:
1901:
1875:
1852:
1843:
1841:
1821:
1800:
1780:
1760:
1712:
1669:
1651:
1630:
1581:
1575:
1554:
1532:
1526:
1505:
1483:
1477:
1454:
1448:
1427:
1407:
1380:
1367:
1358:
1337:
1304:
1272:
1248:
1242:
1221:
1199:
1161:
1141:
1105:
1090:
1058:
1029:
914:
890:
870:
835:
815:
795:
775:
755:
710:
709:
707:
664:
658:
630:
625:
619:
598:
592:
571:
566:
560:
539:
533:
509:
494:
473:
468:
462:
438:
425:
420:
410:
399:
386:
380:
356:
345:
335:
326:
305:
299:
269:
245:
220:
214:
187:
172:
144:
124:
104:
4754:"NetworkCoding - batman-adv - Open Mesh"
4096:Computers and Electronics in Agriculture
1742:
1702:
1183:
71:It has been proven that, theoretically,
5220:https://doi.org/10.1145/1111322.1111337
2428:IEEE Transactions on Information Theory
2307:IEEE Transactions on Information Theory
2272:IEEE Transactions on Information Theory
2255:. 15th ACM-SIAM SODA. pp. 142–150.
2209:
4825:
4823:
4414:. Taipei, Taiwan: IEEE. pp. 1–6.
3730:
3161:
3159:
2251:Rasala Lehman, A.; Lehman, E. (2004).
743:{\displaystyle {\mathcal {G}}=(V,E,C)}
5375:http://scholarcommons.sc.edu/etd/230/
5126:IEEE Transactions on Mobile Computing
3174:. Las Vegas, NV: IEEE. pp. 1–2.
3107:
3105:
3037:
3035:
3010:
3008:
2983:
2981:
2890:
2888:
2811:
2809:
2763:
2761:
2715:
2713:
2006:Software-defined wide area networks (
119:are involved in moving the data from
7:
4250:. Montreal, QC: IEEE. pp. 1–6.
2057:Remote vehicle driving applications.
1752:Overhead due to linear dependencies:
5352:http://www.icsi.berkeley.edu/~luby/
4472:Larsson, P.; Johansson, N. (2006).
810:gives the capacity of each link of
365:{\displaystyle \{M_{i}\}_{i=1}^{S}}
4420:10.1109/GLOBECOM42002.2020.9322478
1863:{\displaystyle {\frac {1}{q^{M}}}}
1775:elements and a generation size of
1611:Decoding computational complexity:
25:
4203:Smart Grid and Internet of Things
2084:In-flight entertainment networks.
770:is the set of nodes or vertices,
5245:
4899:10.1109/LCOMM.2013.031313.121994
4764:from the original on 12 May 2021
2686:10.1109/CSNDSP16145.2010.5580304
4934:IEEE Transactions on Multimedia
4522:securenetworkcoding.wikidot.com
3217:IEEE Transactions on Multimedia
3050:. Sevilla: IEEE. pp. 1–5.
2555:IEEE Internet of Things Journal
1693:{\displaystyle M*log_{2}(s)=32}
489:are coefficients selected from
5364:Introduction to Network Coding
4677:10.1109/VTCSpring.2013.6692495
2954:10.1109/ANTS47819.2019.9117981
2909:10.1109/IC3I46837.2019.9055565
2466:, D. R. Karger and M. Effros,
2097:Information-centric networking
1916:{\displaystyle {\frac {1}{q}}}
1726:
1720:
1681:
1675:
1386:
1360:
1318:
1306:
1286:
1274:
1111:
1098:
1072:
1066:
970:However, the situation in the
931:
919:
852:
840:
737:
719:
699:A network is represented by a
679:
673:
515:
502:
287:{\displaystyle InDeg(p_{k})=S}
275:
262:
193:
180:
1:
5315:A network coding bibliography
5216:Computer Communication Review
2353:Israel Journal of Mathematics
607:{\displaystyle k^{\text{th}}}
555:along with the coefficients,
4550:. IEEE. pp. 1409–1417.
4311:10.1007/978-3-030-37629-1_48
4108:10.1016/j.compag.2007.01.019
3639:Dammak, Marwa (2018-11-20).
2774:2011 IFIP Wireless Days (WD)
2734:10.1109/NUICONE.2012.6493203
2054:remote support and training.
1549:, and each symbol of packet
1085:and the so-called binary-8 (
1019:Operation and key parameters
1010:Random Linear Network Coding
5044:10.1109/GLOCOM.2015.7417590
4877:IEEE Communications Letters
4486:10.1109/VETECS.2006.1683207
4211:10.1007/978-3-030-05928-6_7
3833:10.1109/PIMRCW.2010.5670413
3667:10.1007/978-3-642-13971-0_8
3615:10.1007/978-3-642-13971-0_8
2834:10.1016/j.adhoc.2016.03.002
2617:10.1109/NETCOD.2014.6892129
2161:Spatial buffer multiplexing
2081:Agricultural sensor fields.
27:Computer Networking Program
5426:
5086:10.1109/SPAWC.2015.7227122
4385:10.1109/JSYST.2018.2862913
4256:10.1109/PIMRC.2017.8292785
4166:10.1109/ICCCN.2017.8038415
3878:10.1109/ECMSM.2017.7945879
3287:10.1007/s10922-020-09545-w
2407:(or more) received packets
209:More formally, each node,
5186:10.1049/iet-com.2014.0323
3503:10.1109/ICCW.2017.7962697
3437:10.1007/s13174-010-0006-7
3389:10.1007/s11276-016-1294-z
3180:10.1109/CCNC.2018.8319320
2861:10.1109/ICME.2009.5202786
2567:10.1109/JIOT.2017.2703813
2511:10.1109/WCNC.2016.7565066
2483:10.1109/ISIT.2003.1228459
2376:10.1007/s11856-022-2345-z
2198:Triangular network coding
2116:automatic repeat requests
2035:Consumer Electronics Show
1117:{\displaystyle GF(2^{8})}
1047:maximum transmission unit
639:{\displaystyle g_{k}^{i}}
580:{\displaystyle g_{k}^{i}}
521:{\displaystyle GF(2^{s})}
482:{\displaystyle g_{k}^{i}}
199:{\displaystyle GF(2^{s})}
5350:Digital Fountain Codes,
5231:10.3837/tiis.2013.12.009
5138:10.1109/TMC.2016.2642190
4999:10.1109/ICC.2015.7248631
4956:10.1109/TMM.2013.2285518
4796:10.1109/INFOCOM.2006.266
4556:10.1109/INFOCOM.2008.199
3553:10.1177/1550147719842137
3239:10.1109/TMM.2013.2241415
3056:10.1109/ITW.2013.6691231
2329:10.1109/TIT.2023.3247570
2168:Distributed file sharing
2112:forward error correction
2069:Healthcare applications.
964:Ford–Fulkerson algorithm
960:max-flow min-cut theorem
907:max-flow min-cut theorem
5410:Wireless sensor network
5344:Random Network Coding,
5310:Network Coding Homepage
4854:10.1109/TVT.2008.927729
4722:10.1109/INFCOM.2007.124
4636:10.1145/1159913.1159942
4059:10.1145/3291078.3291098
3990:10.1145/3365871.3365903
2782:10.1109/WD.2011.6098167
2284:10.1109/TIT.2006.874434
2188:Secret sharing protocol
958:scenario, known as the
5356:Coding-Aware Routing,
5338:Avalanche Filesystem,
4993:. pp. 2072–2077.
4716:. pp. 1028–1036.
3546:(4): 155014771984213.
3340:10.1109/SMC-IT.2017.29
2855:. pp. 1492–1495.
1969:
1943:
1917:
1890:
1864:
1830:
1809:
1789:
1769:
1748:
1740:
1733:
1694:
1639:
1622:Transmission Overhead:
1591:
1563:
1542:
1514:
1493:
1464:
1436:
1416:
1393:
1346:
1325:
1293:
1261:
1260:{\displaystyle C_{ij}}
1230:
1208:
1190:
1170:
1150:
1118:
1079:
1038:
991:
938:
937:{\displaystyle T(s,t)}
899:
879:
859:
858:{\displaystyle T(s,t)}
824:
804:
784:
764:
744:
686:
685:{\displaystyle e_{i}=}
640:
608:
581:
549:
522:
483:
448:
415:
366:
315:
294:, generates a message
288:
230:
200:
153:
133:
113:
5362:MIT offers a course:
2101:named data networking
2048:Remote collaboration.
1970:
1968:{\displaystyle q=256}
1944:
1918:
1891:
1865:
1831:
1810:
1790:
1770:
1746:
1734:
1732:{\displaystyle GF(2)}
1706:
1695:
1640:
1592:
1590:{\displaystyle d_{2}}
1564:
1543:
1541:{\displaystyle d_{1}}
1515:
1494:
1492:{\displaystyle d_{2}}
1465:
1463:{\displaystyle d_{1}}
1437:
1417:
1394:
1347:
1326:
1294:
1262:
1231:
1209:
1187:
1171:
1151:
1119:
1080:
1078:{\displaystyle GF(2)}
1039:
989:
982:The Butterfly Network
939:
900:
880:
860:
825:
805:
785:
765:
745:
687:
641:
609:
582:
550:
548:{\displaystyle X_{k}}
523:
484:
449:
395:
367:
316:
314:{\displaystyle X_{k}}
289:
231:
229:{\displaystyle p_{k}}
201:
154:
134:
114:
95:Encoding and decoding
36:linear network coding
5266:improve this article
5080:. pp. 670–674.
4355:IEEE Systems Journal
3827:. pp. 134–138.
2151:Coding-aware routing
2133:Avalanche filesystem
2010:): Large industrial
1953:
1927:
1900:
1874:
1840:
1820:
1799:
1779:
1759:
1711:
1650:
1629:
1574:
1553:
1525:
1504:
1476:
1447:
1426:
1406:
1357:
1336:
1303:
1271:
1241:
1220:
1198:
1160:
1140:
1089:
1057:
1028:
913:
889:
869:
834:
814:
794:
774:
754:
706:
657:
651:Gaussian elimination
618:
591:
559:
532:
493:
461:
379:
325:
298:
244:
213:
171:
167:, typically of size
143:
123:
103:
77:convolutional coding
5405:Network performance
5278:footnote references
4377:2019ISysJ..13.1376B
3927:2019Senso..19.1673P
3770:2014Senso..14.4806K
3141:10.3390/info9040072
2462:T. Ho, R. Koetter,
2138:Distributed storage
2078:Satellite networks.
1942:{\displaystyle q=2}
1889:{\displaystyle M-1}
635:
576:
478:
430:
361:
40:linear combinations
32:computer networking
5395:Information theory
5173:IET Communications
3779:10.3390/s140304806
3701:. Boca Raton, FL.
2473:2017-10-31 at the
1965:
1939:
1913:
1886:
1860:
1826:
1805:
1785:
1765:
1749:
1741:
1729:
1690:
1646:each packet needs
1635:
1587:
1559:
1538:
1510:
1489:
1460:
1432:
1412:
1389:
1342:
1321:
1289:
1257:
1226:
1204:
1191:
1166:
1146:
1114:
1075:
1034:
992:
990:Butterfly Network.
934:
895:
875:
855:
820:
800:
780:
760:
740:
682:
636:
621:
604:
577:
562:
545:
518:
479:
464:
444:
416:
362:
341:
311:
284:
226:
196:
149:
129:
109:
81:filter-bank coding
53:of a network take
5306:
5305:
5298:
5132:(10): 2697–2711.
5095:978-1-4799-1931-4
5053:978-1-4799-5952-5
5008:978-1-4673-6432-4
4790:. pp. 1–12.
4758:www.open-mesh.org
4731:978-1-4244-1047-7
4686:978-1-4673-6337-2
4645:978-1-59593-308-9
4621:"XORs in the air"
4429:978-1-7281-8298-8
4320:978-3-030-37628-4
4275:978-1-5386-3529-2
4220:978-3-030-05928-6
4175:978-1-5090-2991-4
4068:978-1-4503-6577-2
3999:978-1-4503-7207-7
3936:10.3390/s19071673
3887:978-1-5090-5582-1
3842:978-1-4244-9117-9
3716:978-1-4665-8207-1
3707:10.1201/b17124-13
3677:978-3-642-13970-3
3625:978-3-642-13971-0
3512:978-1-5090-1525-2
3377:Wireless Networks
3349:978-1-5386-3462-2
3189:978-1-5386-4790-5
3065:978-1-4799-1321-3
2963:978-1-7281-3715-5
2918:978-1-7281-5529-6
2870:978-1-4244-4290-4
2791:978-1-4577-2028-4
2743:978-1-4673-1719-1
2695:978-1-4244-8858-2
2626:978-1-4799-6217-4
2520:978-1-4673-9814-5
2450:10.1109/18.850663
2052:Augmented reality
1911:
1858:
1829:{\displaystyle M}
1808:{\displaystyle M}
1788:{\displaystyle M}
1768:{\displaystyle q}
1638:{\displaystyle M}
1562:{\displaystyle e}
1513:{\displaystyle f}
1435:{\displaystyle e}
1415:{\displaystyle f}
1345:{\displaystyle f}
1229:{\displaystyle e}
1207:{\displaystyle f}
1169:{\displaystyle M}
1149:{\displaystyle M}
1037:{\displaystyle M}
898:{\displaystyle t}
878:{\displaystyle s}
823:{\displaystyle E}
803:{\displaystyle C}
783:{\displaystyle E}
763:{\displaystyle V}
601:
457:Where the values
152:{\displaystyle K}
132:{\displaystyle S}
112:{\displaystyle P}
16:(Redirected from
5417:
5301:
5294:
5290:
5287:
5281:
5249:
5248:
5241:
5207:
5206:
5188:
5164:
5158:
5157:
5123:
5114:
5108:
5107:
5073:
5064:
5058:
5057:
5038:. pp. 1–6.
5027:
5021:
5020:
4982:
4976:
4975:
4949:
4925:
4919:
4918:
4892:
4872:
4866:
4865:
4847:
4827:
4818:
4817:
4779:
4773:
4772:
4770:
4769:
4750:
4744:
4743:
4705:
4699:
4698:
4671:. pp. 1–6.
4664:
4658:
4657:
4625:
4616:
4610:
4609:
4607:
4595:
4589:
4588:
4586:
4584:
4575:
4566:
4560:
4559:
4539:
4533:
4532:
4530:
4528:
4514:
4508:
4507:
4474:"Multi-User ARQ"
4469:
4463:
4462:
4460:
4448:
4442:
4441:
4403:
4397:
4396:
4370:
4361:(2): 1376–1385.
4350:
4339:
4338:
4336:
4335:
4294:
4288:
4287:
4267:
4239:
4233:
4232:
4194:
4188:
4187:
4145:
4139:
4138:
4137:
4133:
4126:
4120:
4119:
4087:
4081:
4080:
4042:
4036:
4035:
4033:
4032:
4018:
4012:
4011:
3973:
3967:
3966:
3956:
3938:
3906:
3900:
3899:
3861:
3855:
3854:
3816:
3810:
3809:
3799:
3781:
3764:(3): 4806–4830.
3749:
3743:
3742:
3736:
3728:
3688:
3682:
3681:
3669:
3653:
3647:
3646:
3636:
3630:
3629:
3617:
3601:
3595:
3594:
3592:
3580:
3574:
3573:
3555:
3531:
3525:
3524:
3486:
3480:
3479:
3477:
3464:
3458:
3457:
3439:
3415:
3409:
3408:
3383:(8): 2395–2414.
3368:
3362:
3361:
3323:
3317:
3316:
3298:
3265:
3259:
3258:
3232:
3223:(5): 1195–1212.
3208:
3202:
3201:
3163:
3154:
3153:
3143:
3133:
3109:
3100:
3099:
3097:
3096:
3084:
3078:
3077:
3039:
3030:
3029:
3027:
3026:
3012:
3003:
3002:
3000:
2999:
2993:www.linkedin.com
2985:
2976:
2975:
2948:. pp. 1–6.
2937:
2931:
2930:
2892:
2883:
2882:
2844:
2838:
2837:
2813:
2804:
2803:
2776:. pp. 1–5.
2765:
2756:
2755:
2728:. pp. 1–5.
2717:
2708:
2707:
2669:
2663:
2662:
2660:
2659:
2645:
2639:
2638:
2611:. pp. 1–6.
2600:
2594:
2593:
2591:
2585:. Archived from
2552:
2543:
2537:
2536:
2531:. Archived from
2505:. pp. 1–6.
2500:
2491:
2485:
2460:
2454:
2453:
2443:
2434:(4): 1204–1216.
2424:Ahlswede, Rudolf
2420:
2411:
2409:
2394:
2388:
2387:
2369:
2347:
2341:
2340:
2322:
2302:
2296:
2295:
2278:(6): 2386–2397.
2263:
2257:
2256:
2248:
2242:
2227:
2221:
2214:
2175:Device-to-device
1974:
1972:
1971:
1966:
1948:
1946:
1945:
1940:
1922:
1920:
1919:
1914:
1912:
1904:
1895:
1893:
1892:
1887:
1869:
1867:
1866:
1861:
1859:
1857:
1856:
1844:
1835:
1833:
1832:
1827:
1814:
1812:
1811:
1806:
1794:
1792:
1791:
1786:
1774:
1772:
1771:
1766:
1738:
1736:
1735:
1730:
1699:
1697:
1696:
1691:
1674:
1673:
1644:
1642:
1641:
1636:
1596:
1594:
1593:
1588:
1586:
1585:
1568:
1566:
1565:
1560:
1547:
1545:
1544:
1539:
1537:
1536:
1519:
1517:
1516:
1511:
1498:
1496:
1495:
1490:
1488:
1487:
1469:
1467:
1466:
1461:
1459:
1458:
1441:
1439:
1438:
1433:
1421:
1419:
1418:
1413:
1398:
1396:
1395:
1392:{\displaystyle }
1390:
1385:
1384:
1372:
1371:
1351:
1349:
1348:
1343:
1330:
1328:
1327:
1324:{\displaystyle }
1322:
1298:
1296:
1295:
1292:{\displaystyle }
1290:
1266:
1264:
1263:
1258:
1256:
1255:
1235:
1233:
1232:
1227:
1213:
1211:
1210:
1205:
1175:
1173:
1172:
1167:
1155:
1153:
1152:
1147:
1123:
1121:
1120:
1115:
1110:
1109:
1084:
1082:
1081:
1076:
1043:
1041:
1040:
1035:
943:
941:
940:
935:
904:
902:
901:
896:
884:
882:
881:
876:
864:
862:
861:
856:
829:
827:
826:
821:
809:
807:
806:
801:
789:
787:
786:
781:
769:
767:
766:
761:
749:
747:
746:
741:
715:
714:
691:
689:
688:
683:
669:
668:
645:
643:
642:
637:
634:
629:
613:
611:
610:
605:
603:
602:
599:
586:
584:
583:
578:
575:
570:
554:
552:
551:
546:
544:
543:
527:
525:
524:
519:
514:
513:
488:
486:
485:
480:
477:
472:
453:
451:
450:
445:
443:
442:
429:
424:
414:
409:
391:
390:
372:by the formula:
371:
369:
368:
363:
360:
355:
340:
339:
320:
318:
317:
312:
310:
309:
293:
291:
290:
285:
274:
273:
235:
233:
232:
227:
225:
224:
205:
203:
202:
197:
192:
191:
158:
156:
155:
150:
139:source nodes to
138:
136:
135:
130:
118:
116:
115:
110:
21:
5425:
5424:
5420:
5419:
5418:
5416:
5415:
5414:
5380:
5379:
5302:
5291:
5285:
5282:
5263:
5254:This article's
5250:
5246:
5239:
5211:
5210:
5166:
5165:
5161:
5121:
5116:
5115:
5111:
5096:
5071:
5066:
5065:
5061:
5054:
5029:
5028:
5024:
5009:
4984:
4983:
4979:
4927:
4926:
4922:
4874:
4873:
4869:
4845:10.1.1.321.1962
4829:
4828:
4821:
4806:
4781:
4780:
4776:
4767:
4765:
4752:
4751:
4747:
4732:
4707:
4706:
4702:
4687:
4666:
4665:
4661:
4646:
4623:
4618:
4617:
4613:
4597:
4596:
4592:
4582:
4580:
4573:
4568:
4567:
4563:
4541:
4540:
4536:
4526:
4524:
4516:
4515:
4511:
4496:
4471:
4470:
4466:
4450:
4449:
4445:
4430:
4405:
4404:
4400:
4352:
4351:
4342:
4333:
4331:
4321:
4296:
4295:
4291:
4276:
4241:
4240:
4236:
4221:
4196:
4195:
4191:
4176:
4147:
4146:
4142:
4135:
4128:
4127:
4123:
4089:
4088:
4084:
4069:
4044:
4043:
4039:
4030:
4028:
4020:
4019:
4015:
4000:
3975:
3974:
3970:
3908:
3907:
3903:
3888:
3863:
3862:
3858:
3843:
3818:
3817:
3813:
3751:
3750:
3746:
3729:
3717:
3690:
3689:
3685:
3678:
3655:
3654:
3650:
3638:
3637:
3633:
3626:
3603:
3602:
3598:
3582:
3581:
3577:
3533:
3532:
3528:
3513:
3488:
3487:
3483:
3466:
3465:
3461:
3417:
3416:
3412:
3370:
3369:
3365:
3350:
3325:
3324:
3320:
3267:
3266:
3262:
3210:
3209:
3205:
3190:
3165:
3164:
3157:
3111:
3110:
3103:
3094:
3092:
3086:
3085:
3081:
3066:
3041:
3040:
3033:
3024:
3022:
3014:
3013:
3006:
2997:
2995:
2987:
2986:
2979:
2964:
2939:
2938:
2934:
2919:
2894:
2893:
2886:
2871:
2846:
2845:
2841:
2822:Ad Hoc Networks
2815:
2814:
2807:
2792:
2767:
2766:
2759:
2744:
2719:
2718:
2711:
2696:
2671:
2670:
2666:
2657:
2655:
2647:
2646:
2642:
2627:
2602:
2601:
2597:
2589:
2550:
2545:
2544:
2540:
2521:
2498:
2493:
2492:
2488:
2475:Wayback Machine
2461:
2457:
2441:10.1.1.722.1409
2422:
2421:
2414:
2396:
2395:
2391:
2349:
2348:
2344:
2304:
2303:
2299:
2265:
2264:
2260:
2250:
2249:
2245:
2228:
2224:
2215:
2211:
2206:
2184:
2110:Alternative to
2093:infrastructure.
1981:
1951:
1950:
1925:
1924:
1898:
1897:
1872:
1871:
1848:
1838:
1837:
1818:
1817:
1797:
1796:
1777:
1776:
1757:
1756:
1709:
1708:
1665:
1648:
1647:
1627:
1626:
1604:
1577:
1572:
1571:
1551:
1550:
1528:
1523:
1522:
1502:
1501:
1479:
1474:
1473:
1450:
1445:
1444:
1424:
1423:
1404:
1403:
1376:
1363:
1355:
1354:
1334:
1333:
1301:
1300:
1269:
1268:
1244:
1239:
1238:
1218:
1217:
1196:
1195:
1182:
1158:
1157:
1138:
1137:
1101:
1087:
1086:
1055:
1054:
1026:
1025:
1021:
1012:
984:
911:
910:
887:
886:
867:
866:
832:
831:
812:
811:
792:
791:
772:
771:
752:
751:
704:
703:
697:
660:
655:
654:
616:
615:
594:
589:
588:
557:
556:
535:
530:
529:
505:
491:
490:
459:
458:
434:
382:
377:
376:
331:
323:
322:
301:
296:
295:
265:
242:
241:
216:
211:
210:
183:
169:
168:
141:
140:
121:
120:
101:
100:
97:
28:
23:
22:
15:
12:
11:
5:
5423:
5421:
5413:
5412:
5407:
5402:
5397:
5392:
5382:
5381:
5378:
5377:
5371:
5366:
5360:
5354:
5348:
5342:
5336:
5329:
5323:
5317:
5312:
5304:
5303:
5258:external links
5253:
5251:
5244:
5238:
5237:External links
5235:
5234:
5233:
5222:
5209:
5208:
5179:(3): 367–374.
5159:
5109:
5094:
5059:
5052:
5022:
5007:
4977:
4940:(2): 521–532.
4920:
4883:(5): 944–947.
4867:
4838:(2): 914–925.
4819:
4804:
4774:
4745:
4730:
4700:
4685:
4659:
4644:
4611:
4590:
4561:
4534:
4509:
4494:
4464:
4443:
4428:
4398:
4340:
4319:
4289:
4274:
4234:
4219:
4189:
4174:
4150:Cheng, Xiuzhen
4140:
4121:
4082:
4067:
4037:
4013:
3998:
3968:
3901:
3886:
3856:
3841:
3811:
3744:
3715:
3683:
3676:
3648:
3631:
3624:
3596:
3575:
3526:
3511:
3481:
3459:
3410:
3363:
3348:
3318:
3281:(4): 796–826.
3260:
3203:
3188:
3155:
3101:
3079:
3064:
3031:
3004:
2977:
2962:
2932:
2917:
2884:
2869:
2839:
2805:
2790:
2757:
2742:
2709:
2694:
2664:
2653:www.comsoc.org
2640:
2625:
2595:
2592:on 8 Apr 2022.
2561:(4): 917–933.
2538:
2535:on 2022-04-08.
2519:
2486:
2455:
2412:
2389:
2342:
2297:
2258:
2243:
2229:R. Dougherty,
2222:
2208:
2207:
2205:
2202:
2201:
2200:
2195:
2190:
2183:
2180:
2179:
2178:
2172:
2169:
2166:
2163:
2157:
2139:
2136:
2135:from Microsoft
2129:
2126:
2124:Multi-user ARQ
2108:
2094:
2088:
2085:
2082:
2079:
2076:
2070:
2067:
2064:
2061:Connected cars
2058:
2055:
2049:
2046:
2024:
2020:
2004:
1991:
1980:
1977:
1964:
1961:
1958:
1938:
1935:
1932:
1910:
1907:
1885:
1882:
1879:
1855:
1851:
1847:
1825:
1804:
1784:
1764:
1728:
1725:
1722:
1719:
1716:
1689:
1686:
1683:
1680:
1677:
1672:
1668:
1664:
1661:
1658:
1655:
1634:
1603:
1602:Misconceptions
1600:
1584:
1580:
1558:
1535:
1531:
1509:
1486:
1482:
1457:
1453:
1431:
1411:
1388:
1383:
1379:
1375:
1370:
1366:
1362:
1341:
1320:
1317:
1314:
1311:
1308:
1288:
1285:
1282:
1279:
1276:
1254:
1251:
1247:
1225:
1203:
1181:
1178:
1165:
1145:
1113:
1108:
1104:
1100:
1097:
1094:
1074:
1071:
1068:
1065:
1062:
1051:Ethernet frame
1033:
1020:
1017:
1011:
1008:
983:
980:
933:
930:
927:
924:
921:
918:
894:
874:
854:
851:
848:
845:
842:
839:
819:
799:
779:
759:
739:
736:
733:
730:
727:
724:
721:
718:
713:
701:directed graph
696:
693:
681:
678:
675:
672:
667:
663:
633:
628:
624:
597:
587:, used in the
574:
569:
565:
542:
538:
517:
512:
508:
504:
501:
498:
476:
471:
467:
455:
454:
441:
437:
433:
428:
423:
419:
413:
408:
405:
402:
398:
394:
389:
385:
359:
354:
351:
348:
344:
338:
334:
330:
308:
304:
283:
280:
277:
272:
268:
264:
261:
258:
255:
252:
249:
223:
219:
195:
190:
186:
182:
179:
176:
163:chosen from a
148:
128:
108:
96:
93:
26:
24:
18:Network coding
14:
13:
10:
9:
6:
4:
3:
2:
5422:
5411:
5408:
5406:
5403:
5401:
5400:Finite fields
5398:
5396:
5393:
5391:
5390:Coding theory
5388:
5387:
5385:
5376:
5372:
5370:
5367:
5365:
5361:
5359:
5355:
5353:
5349:
5347:
5343:
5341:
5337:
5334:
5330:
5328:
5324:
5322:
5318:
5316:
5313:
5311:
5308:
5307:
5300:
5297:
5289:
5279:
5275:
5274:inappropriate
5271:
5267:
5261:
5259:
5252:
5243:
5242:
5236:
5232:
5228:
5223:
5221:
5217:
5213:
5212:
5204:
5200:
5196:
5192:
5187:
5182:
5178:
5174:
5170:
5163:
5160:
5155:
5151:
5147:
5143:
5139:
5135:
5131:
5127:
5120:
5113:
5110:
5105:
5101:
5097:
5091:
5087:
5083:
5079:
5078:
5070:
5063:
5060:
5055:
5049:
5045:
5041:
5037:
5033:
5026:
5023:
5018:
5014:
5010:
5004:
5000:
4996:
4992:
4988:
4981:
4978:
4973:
4969:
4965:
4961:
4957:
4953:
4948:
4943:
4939:
4935:
4931:
4924:
4921:
4916:
4912:
4908:
4904:
4900:
4896:
4891:
4886:
4882:
4878:
4871:
4868:
4863:
4859:
4855:
4851:
4846:
4841:
4837:
4833:
4826:
4824:
4820:
4815:
4811:
4807:
4805:1-4244-0221-2
4801:
4797:
4793:
4789:
4785:
4778:
4775:
4763:
4759:
4755:
4749:
4746:
4741:
4737:
4733:
4727:
4723:
4719:
4715:
4711:
4704:
4701:
4696:
4692:
4688:
4682:
4678:
4674:
4670:
4663:
4660:
4655:
4651:
4647:
4641:
4637:
4633:
4629:
4622:
4615:
4612:
4606:
4601:
4594:
4591:
4579:
4572:
4565:
4562:
4557:
4553:
4549:
4545:
4538:
4535:
4523:
4519:
4513:
4510:
4505:
4501:
4497:
4495:0-7803-9392-9
4491:
4487:
4483:
4479:
4475:
4468:
4465:
4459:
4454:
4447:
4444:
4439:
4435:
4431:
4425:
4421:
4417:
4413:
4409:
4402:
4399:
4394:
4390:
4386:
4382:
4378:
4374:
4369:
4364:
4360:
4356:
4349:
4347:
4345:
4341:
4330:
4326:
4322:
4316:
4312:
4308:
4304:
4300:
4293:
4290:
4285:
4281:
4277:
4271:
4266:
4261:
4257:
4253:
4249:
4245:
4238:
4235:
4230:
4226:
4222:
4216:
4212:
4208:
4204:
4200:
4193:
4190:
4185:
4181:
4177:
4171:
4167:
4163:
4159:
4155:
4152:(July 2017).
4151:
4144:
4141:
4131:
4125:
4122:
4117:
4113:
4109:
4105:
4101:
4097:
4093:
4086:
4083:
4078:
4074:
4070:
4064:
4060:
4056:
4052:
4048:
4041:
4038:
4027:
4023:
4017:
4014:
4009:
4005:
4001:
3995:
3991:
3987:
3983:
3979:
3972:
3969:
3964:
3960:
3955:
3950:
3946:
3942:
3937:
3932:
3928:
3924:
3920:
3916:
3912:
3905:
3902:
3897:
3893:
3889:
3883:
3879:
3875:
3871:
3867:
3860:
3857:
3852:
3848:
3844:
3838:
3834:
3830:
3826:
3822:
3815:
3812:
3807:
3803:
3798:
3793:
3789:
3785:
3780:
3775:
3771:
3767:
3763:
3759:
3755:
3748:
3745:
3740:
3734:
3726:
3722:
3718:
3712:
3708:
3704:
3700:
3699:
3694:
3687:
3684:
3679:
3673:
3668:
3663:
3659:
3652:
3649:
3644:
3643:
3635:
3632:
3627:
3621:
3616:
3611:
3607:
3600:
3597:
3591:
3586:
3579:
3576:
3571:
3567:
3563:
3559:
3554:
3549:
3545:
3541:
3537:
3530:
3527:
3522:
3518:
3514:
3508:
3504:
3500:
3496:
3492:
3485:
3482:
3476:
3471:
3463:
3460:
3455:
3451:
3447:
3443:
3438:
3433:
3429:
3425:
3421:
3414:
3411:
3406:
3402:
3398:
3394:
3390:
3386:
3382:
3378:
3374:
3367:
3364:
3359:
3355:
3351:
3345:
3341:
3337:
3333:
3329:
3322:
3319:
3314:
3310:
3306:
3302:
3297:
3292:
3288:
3284:
3280:
3276:
3272:
3264:
3261:
3256:
3252:
3248:
3244:
3240:
3236:
3231:
3226:
3222:
3218:
3214:
3207:
3204:
3199:
3195:
3191:
3185:
3181:
3177:
3173:
3169:
3162:
3160:
3156:
3151:
3147:
3142:
3137:
3132:
3127:
3123:
3119:
3115:
3108:
3106:
3102:
3091:
3090:
3083:
3080:
3075:
3071:
3067:
3061:
3057:
3053:
3049:
3045:
3038:
3036:
3032:
3021:
3017:
3011:
3009:
3005:
2994:
2990:
2984:
2982:
2978:
2973:
2969:
2965:
2959:
2955:
2951:
2947:
2943:
2936:
2933:
2928:
2924:
2920:
2914:
2910:
2906:
2902:
2898:
2891:
2889:
2885:
2880:
2876:
2872:
2866:
2862:
2858:
2854:
2850:
2843:
2840:
2835:
2831:
2827:
2823:
2819:
2812:
2810:
2806:
2801:
2797:
2793:
2787:
2783:
2779:
2775:
2771:
2764:
2762:
2758:
2753:
2749:
2745:
2739:
2735:
2731:
2727:
2723:
2716:
2714:
2710:
2705:
2701:
2697:
2691:
2687:
2683:
2679:
2675:
2668:
2665:
2654:
2650:
2644:
2641:
2636:
2632:
2628:
2622:
2618:
2614:
2610:
2606:
2599:
2596:
2588:
2584:
2580:
2576:
2572:
2568:
2564:
2560:
2556:
2549:
2542:
2539:
2534:
2530:
2526:
2522:
2516:
2512:
2508:
2504:
2497:
2490:
2487:
2484:
2480:
2476:
2472:
2469:
2465:
2459:
2456:
2451:
2447:
2442:
2437:
2433:
2429:
2425:
2419:
2417:
2413:
2408:
2406:
2400:
2393:
2390:
2385:
2381:
2377:
2373:
2368:
2363:
2359:
2355:
2354:
2346:
2343:
2338:
2334:
2330:
2326:
2321:
2316:
2312:
2308:
2301:
2298:
2293:
2289:
2285:
2281:
2277:
2273:
2269:
2262:
2259:
2254:
2247:
2244:
2240:
2236:
2232:
2226:
2223:
2219:
2213:
2210:
2203:
2199:
2196:
2194:
2191:
2189:
2186:
2185:
2181:
2176:
2173:
2170:
2167:
2164:
2162:
2158:
2156:
2152:
2148:
2144:
2140:
2137:
2134:
2130:
2127:
2125:
2121:
2117:
2113:
2109:
2106:
2102:
2098:
2095:
2092:
2089:
2086:
2083:
2080:
2077:
2074:
2071:
2068:
2065:
2062:
2059:
2056:
2053:
2050:
2047:
2044:
2040:
2036:
2032:
2028:
2025:
2021:
2018:
2013:
2009:
2005:
2001:
1996:
1992:
1989:
1986:
1985:
1984:
1978:
1976:
1962:
1959:
1956:
1936:
1933:
1930:
1908:
1905:
1883:
1880:
1877:
1853:
1849:
1845:
1823:
1802:
1782:
1762:
1753:
1745:
1723:
1717:
1714:
1705:
1701:
1687:
1684:
1678:
1670:
1666:
1662:
1659:
1656:
1653:
1632:
1623:
1619:
1616:
1612:
1608:
1601:
1599:
1597:
1582:
1578:
1556:
1548:
1533:
1529:
1507:
1499:
1484:
1480:
1470:
1455:
1451:
1429:
1409:
1400:
1381:
1377:
1373:
1368:
1364:
1352:
1339:
1315:
1312:
1309:
1283:
1280:
1277:
1252:
1249:
1245:
1236:
1223:
1214:
1201:
1186:
1179:
1177:
1163:
1143:
1133:
1129:
1125:
1106:
1102:
1095:
1092:
1069:
1063:
1060:
1052:
1048:
1031:
1018:
1016:
1009:
1007:
1003:
999:
997:
988:
981:
979:
977:
973:
968:
965:
962:. Later, the
961:
957:
953:
949:
947:
928:
925:
922:
916:
908:
892:
872:
849:
846:
843:
837:
817:
797:
777:
757:
734:
731:
728:
725:
722:
716:
702:
694:
692:
676:
670:
665:
661:
652:
647:
631:
626:
622:
595:
572:
567:
563:
540:
536:
510:
506:
499:
496:
474:
469:
465:
439:
435:
431:
426:
421:
417:
411:
406:
403:
400:
396:
392:
387:
383:
375:
374:
373:
357:
352:
349:
346:
336:
332:
306:
302:
281:
278:
270:
266:
259:
256:
253:
250:
247:
239:
221:
217:
207:
188:
184:
177:
174:
166:
162:
146:
126:
106:
94:
92:
90:
86:
82:
78:
74:
73:linear coding
69:
67:
63:
60:
56:
52:
48:
43:
41:
37:
33:
19:
5292:
5283:
5268:by removing
5255:
5215:
5176:
5172:
5162:
5129:
5125:
5112:
5076:
5062:
5035:
5025:
4990:
4980:
4937:
4933:
4923:
4880:
4876:
4870:
4835:
4831:
4787:
4777:
4766:. Retrieved
4757:
4748:
4713:
4703:
4668:
4662:
4627:
4614:
4593:
4581:. Retrieved
4577:
4564:
4547:
4537:
4525:. Retrieved
4521:
4512:
4477:
4467:
4446:
4411:
4401:
4358:
4354:
4332:. Retrieved
4302:
4292:
4247:
4237:
4202:
4192:
4157:
4143:
4124:
4102:(1): 25–36.
4099:
4095:
4085:
4050:
4040:
4029:. Retrieved
4025:
4016:
3981:
3971:
3918:
3914:
3904:
3869:
3859:
3824:
3814:
3761:
3757:
3747:
3697:
3686:
3657:
3651:
3641:
3634:
3605:
3599:
3578:
3543:
3539:
3529:
3494:
3484:
3462:
3430:(1): 57–68.
3427:
3423:
3413:
3380:
3376:
3366:
3331:
3321:
3278:
3274:
3263:
3220:
3216:
3206:
3171:
3121:
3117:
3093:. Retrieved
3088:
3082:
3047:
3023:. Retrieved
3019:
2996:. Retrieved
2992:
2945:
2935:
2900:
2852:
2842:
2825:
2821:
2773:
2725:
2677:
2667:
2656:. Retrieved
2652:
2643:
2608:
2598:
2587:the original
2558:
2554:
2541:
2533:the original
2502:
2489:
2458:
2431:
2427:
2404:
2402:
2398:
2392:
2357:
2351:
2345:
2310:
2306:
2300:
2275:
2271:
2261:
2252:
2246:
2225:
2212:
2155:B.A.T.M.A.N.
2073:Industry 4.0
1982:
1979:Applications
1751:
1750:
1621:
1620:
1610:
1609:
1605:
1570:
1521:
1472:
1443:
1401:
1332:
1216:
1194:
1192:
1189:symbol-wise.
1134:
1130:
1126:
1022:
1013:
1004:
1000:
993:
969:
950:
698:
648:
456:
208:
165:finite field
161:coefficients
98:
70:
54:
44:
35:
29:
4578:web.mit.edu
4265:10197/11114
4130:US8401021B2
3921:(7): 1673.
3296:2117/330129
3118:Information
2231:C. Freiling
2003:forwarding.
1422:and packet
1215:and packet
952:Karl Menger
677:0...010...0
89:undecidable
59:information
47:scalability
5384:Categories
5286:March 2022
4768:2015-10-28
4605:cs/0702015
4368:1808.00348
4334:2022-06-06
4031:2022-06-06
4026:www.dlr.de
3590:1803.11102
3475:2012.07753
3131:1802.04873
3095:2022-06-06
3025:2022-06-06
2998:2022-06-06
2658:2022-06-06
2367:1912.06123
2360:: 95–147.
2320:2205.11461
2204:References
2177:extensions
2091:Smart city
695:Background
5270:excessive
5195:1751-8636
5146:1558-0660
4964:1941-0077
4947:1309.0316
4907:1089-7798
4890:1203.5395
4840:CiteSeerX
4654:207160426
4458:1212.2291
4438:231725197
4329:214486109
4116:0168-1699
4008:207940281
3945:1424-8220
3788:1424-8220
3733:cite book
3725:881429695
3570:145983739
3562:1550-1477
3446:1867-4828
3397:1022-0038
3313:219589307
3305:1064-7570
3247:1520-9210
3230:1211.4206
3150:2078-2489
3124:(4): 72.
3020:Steinwurf
2972:219853700
2927:215723197
2828:: 13–21.
2575:2327-4662
2464:M. Médard
2436:CiteSeerX
2384:209324252
2337:248986512
2120:Coded TCP
2063:networks.
2017:Barracuda
1881:−
1657:∗
1625:appended
972:multicast
905:. By the
432:⋅
397:∑
87:and even
5218:, 2006.
5203:27108894
5154:22233426
5017:19637201
4972:10548996
4862:16989586
4762:Archived
4583:26 March
4527:26 March
4504:38823300
4393:51894197
4229:59561476
4184:25131878
4077:59337140
3963:30965629
3896:37985560
3851:25872472
3806:24618727
3521:22423560
3405:13624914
2635:18256950
2583:30243498
2529:10468008
2471:Archived
2313:(6): 1.
2182:See also
885:to node
238:indegree
5264:Please
5256:use of
5104:9591953
4740:3056111
4695:1319567
4373:Bibcode
3954:6479523
3923:Bibcode
3915:Sensors
3797:4003969
3766:Bibcode
3758:Sensors
3454:2143201
3358:6180560
3255:3200945
3198:3982619
2879:8234088
2800:8052927
2752:7791774
2704:1761089
2292:1414385
2239:erratum
2000:Android
1180:Example
996:routing
976:routing
956:unicast
614:level,
85:NP-hard
66:network
55:several
5201:
5193:
5152:
5144:
5102:
5092:
5050:
5015:
5005:
4970:
4962:
4913:
4905:
4860:
4842:
4814:730706
4812:
4802:
4738:
4728:
4693:
4683:
4652:
4642:
4502:
4492:
4436:
4426:
4391:
4327:
4317:
4284:748535
4282:
4272:
4227:
4217:
4182:
4172:
4136:
4114:
4075:
4065:
4006:
3996:
3961:
3951:
3943:
3894:
3884:
3849:
3839:
3804:
3794:
3786:
3723:
3713:
3674:
3622:
3568:
3560:
3519:
3509:
3452:
3444:
3403:
3395:
3356:
3346:
3311:
3303:
3253:
3245:
3196:
3186:
3148:
3074:286822
3072:
3062:
2970:
2960:
2925:
2915:
2877:
2867:
2798:
2788:
2750:
2740:
2702:
2692:
2633:
2623:
2581:
2573:
2527:
2517:
2438:
2382:
2335:
2290:
2153:, and
2008:SD-WAN
1995:MPEG-4
830:. Let
5199:S2CID
5150:S2CID
5122:(PDF)
5100:S2CID
5072:(PDF)
5013:S2CID
4968:S2CID
4942:arXiv
4915:13576
4911:S2CID
4885:arXiv
4858:S2CID
4810:S2CID
4736:S2CID
4691:S2CID
4650:S2CID
4624:(PDF)
4600:arXiv
4574:(PDF)
4500:S2CID
4453:arXiv
4434:S2CID
4389:S2CID
4363:arXiv
4325:S2CID
4280:S2CID
4225:S2CID
4180:S2CID
4073:S2CID
4004:S2CID
3892:S2CID
3847:S2CID
3585:arXiv
3566:S2CID
3517:S2CID
3470:arXiv
3450:S2CID
3401:S2CID
3354:S2CID
3309:S2CID
3251:S2CID
3225:arXiv
3194:S2CID
3126:arXiv
3070:S2CID
2968:S2CID
2923:S2CID
2875:S2CID
2796:S2CID
2748:S2CID
2700:S2CID
2631:S2CID
2590:(PDF)
2579:S2CID
2551:(PDF)
2525:S2CID
2499:(PDF)
2380:S2CID
2362:arXiv
2333:S2CID
2315:arXiv
2288:S2CID
2031:5G NR
236:with
64:in a
51:nodes
5191:ISSN
5142:ISSN
5090:ISBN
5048:ISBN
5003:ISBN
4960:ISSN
4903:ISSN
4800:ISBN
4726:ISBN
4681:ISBN
4640:ISBN
4585:2022
4529:2022
4490:ISBN
4424:ISBN
4315:ISBN
4270:ISBN
4215:ISBN
4170:ISBN
4112:ISSN
4063:ISBN
3994:ISBN
3959:PMID
3941:ISSN
3882:ISBN
3837:ISBN
3802:PMID
3784:ISSN
3739:link
3721:OCLC
3711:ISBN
3672:ISBN
3620:ISBN
3558:ISSN
3507:ISBN
3442:ISSN
3393:ISSN
3344:ISBN
3301:ISSN
3243:ISSN
3184:ISBN
3146:ISSN
3060:ISBN
2958:ISBN
2913:ISBN
2865:ISBN
2786:ISBN
2738:ISBN
2690:ISBN
2621:ISBN
2571:ISSN
2515:ISBN
2147:CORE
2143:COPE
2122:and
2114:and
2105:IPFS
2099:and
2041:and
1988:VoIP
1615:SIMD
1471:and
946:cuts
79:and
62:flow
5272:or
5227:doi
5181:doi
5134:doi
5082:doi
5040:doi
4995:doi
4952:doi
4895:doi
4850:doi
4792:doi
4718:doi
4673:doi
4632:doi
4552:doi
4482:doi
4416:doi
4381:doi
4307:doi
4260:hdl
4252:doi
4207:doi
4162:doi
4104:doi
4055:doi
3986:doi
3949:PMC
3931:doi
3874:doi
3829:doi
3792:PMC
3774:doi
3703:doi
3662:doi
3610:doi
3548:doi
3499:doi
3432:doi
3385:doi
3336:doi
3291:hdl
3283:doi
3235:doi
3176:doi
3136:doi
3052:doi
2950:doi
2905:doi
2857:doi
2830:doi
2778:doi
2730:doi
2682:doi
2613:doi
2563:doi
2507:doi
2479:doi
2446:doi
2372:doi
2358:252
2325:doi
2280:doi
2235:PDF
2218:PDF
2043:SDN
2039:NFV
2012:IoT
1963:256
1569:by
1520:by
1299:or
30:In
5386::
5197:.
5189:.
5175:.
5171:.
5148:.
5140:.
5130:16
5128:.
5124:.
5098:.
5088:.
5074:.
5046:.
5034:.
5011:.
5001:.
4989:.
4966:.
4958:.
4950:.
4938:16
4936:.
4932:.
4909:.
4901:.
4893:.
4881:17
4879:.
4856:.
4848:.
4836:58
4834:.
4822:^
4808:.
4798:.
4786:.
4760:.
4756:.
4734:.
4724:.
4712:.
4689:.
4679:.
4648:.
4638:.
4626:.
4576:.
4546:.
4520:.
4498:.
4488:.
4476:.
4432:.
4422:.
4410:.
4387:.
4379:.
4371:.
4359:13
4357:.
4343:^
4323:.
4313:.
4301:.
4278:.
4268:.
4258:.
4246:.
4223:.
4213:.
4178:.
4168:.
4156:.
4110:.
4100:58
4094:.
4071:.
4061:.
4049:.
4024:.
4002:.
3992:.
3980:.
3957:.
3947:.
3939:.
3929:.
3919:19
3917:.
3913:.
3890:.
3880:.
3868:.
3845:.
3835:.
3823:.
3800:.
3790:.
3782:.
3772:.
3762:14
3760:.
3756:.
3735:}}
3731:{{
3719:.
3709:.
3695:.
3670:.
3618:.
3564:.
3556:.
3544:15
3542:.
3538:.
3515:.
3505:.
3493:.
3448:.
3440:.
3426:.
3422:.
3399:.
3391:.
3381:23
3379:.
3375:.
3352:.
3342:.
3330:.
3307:.
3299:.
3289:.
3279:28
3277:.
3273:.
3249:.
3241:.
3233:.
3221:15
3219:.
3215:.
3192:.
3182:.
3170:.
3158:^
3144:.
3134:.
3120:.
3116:.
3104:^
3068:.
3058:.
3046:.
3034:^
3018:.
3007:^
2991:.
2980:^
2966:.
2956:.
2944:.
2921:.
2911:.
2899:.
2887:^
2873:.
2863:.
2851:.
2826:45
2824:.
2820:.
2808:^
2794:.
2784:.
2772:.
2760:^
2746:.
2736:.
2724:.
2712:^
2698:.
2688:.
2676:.
2651:.
2629:.
2619:.
2607:.
2577:.
2569:.
2557:.
2553:.
2523:.
2513:.
2501:.
2444:.
2432:46
2430:.
2415:^
2401:.
2378:.
2370:.
2356:.
2331:.
2323:.
2311:69
2309:.
2286:.
2276:52
2274:.
2270:.
2149:,
2145:,
2027:5G
1688:32
1382:12
1369:11
909:,
750:.
646:.
600:th
240:,
206:.
91:.
68:.
42:.
34:,
5335:.
5299:)
5293:(
5288:)
5284:(
5280:.
5262:.
5229::
5205:.
5183::
5177:9
5156:.
5136::
5106:.
5084::
5056:.
5042::
5019:.
4997::
4974:.
4954::
4944::
4917:.
4897::
4887::
4864:.
4852::
4816:.
4794::
4771:.
4742:.
4720::
4697:.
4675::
4656:.
4634::
4608:.
4602::
4587:.
4558:.
4554::
4531:.
4506:.
4484::
4461:.
4455::
4440:.
4418::
4395:.
4383::
4375::
4365::
4337:.
4309::
4286:.
4262::
4254::
4231:.
4209::
4186:.
4164::
4118:.
4106::
4079:.
4057::
4034:.
4010:.
3988::
3965:.
3933::
3925::
3898:.
3876::
3853:.
3831::
3808:.
3776::
3768::
3741:)
3727:.
3705::
3680:.
3664::
3628:.
3612::
3593:.
3587::
3572:.
3550::
3523:.
3501::
3478:.
3472::
3456:.
3434::
3428:1
3407:.
3387::
3360:.
3338::
3315:.
3293::
3285::
3257:.
3237::
3227::
3200:.
3178::
3152:.
3138::
3128::
3122:9
3098:.
3076:.
3054::
3028:.
3001:.
2974:.
2952::
2929:.
2907::
2881:.
2859::
2836:.
2832::
2802:.
2780::
2754:.
2732::
2706:.
2684::
2661:.
2637:.
2615::
2565::
2559:4
2509::
2481::
2452:.
2448::
2410:.
2405:h
2386:.
2374::
2364::
2339:.
2327::
2317::
2294:.
2282::
2241:)
2075:.
1960:=
1957:q
1937:2
1934:=
1931:q
1909:q
1906:1
1884:1
1878:M
1854:M
1850:q
1846:1
1824:M
1803:M
1783:M
1763:q
1727:)
1724:2
1721:(
1718:F
1715:G
1685:=
1682:)
1679:s
1676:(
1671:2
1667:g
1663:o
1660:l
1654:M
1633:M
1583:2
1579:d
1557:e
1534:1
1530:d
1508:f
1485:2
1481:d
1456:1
1452:d
1430:e
1410:f
1387:]
1378:C
1374:,
1365:C
1361:[
1340:f
1319:]
1316:0
1313:,
1310:1
1307:[
1287:]
1284:1
1281:,
1278:0
1275:[
1253:j
1250:i
1246:C
1224:e
1202:f
1164:M
1144:M
1112:)
1107:8
1103:2
1099:(
1096:F
1093:G
1073:)
1070:2
1067:(
1064:F
1061:G
1032:M
932:)
929:t
926:,
923:s
920:(
917:T
893:t
873:s
853:)
850:t
847:,
844:s
841:(
838:T
818:E
798:C
778:E
758:V
738:)
735:C
732:,
729:E
726:,
723:V
720:(
717:=
712:G
680:]
674:[
671:=
666:i
662:e
632:i
627:k
623:g
596:k
573:i
568:k
564:g
541:k
537:X
516:)
511:s
507:2
503:(
500:F
497:G
475:i
470:k
466:g
440:i
436:M
427:i
422:k
418:g
412:S
407:1
404:=
401:i
393:=
388:k
384:X
358:S
353:1
350:=
347:i
343:}
337:i
333:M
329:{
307:k
303:X
282:S
279:=
276:)
271:k
267:p
263:(
260:g
257:e
254:D
251:n
248:I
222:k
218:p
194:)
189:s
185:2
181:(
178:F
175:G
147:K
127:S
107:P
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.