154:
4447:
596:.) Unlike previous versions of Windows, Vista's "diskpart" command-line tool includes the ability to shrink the size of an NTFS volume so that this volume may be created from already allocated space. A tool called the BitLocker Drive Preparation Tool is also available from Microsoft that allows an existing volume on Windows Vista to be shrunk to make room for a new boot volume and for the necessary
4458:
615:(EFS) may be used in conjunction with BitLocker to provide protection once the operating system is running. Protection of the files from processes and users within the operating system can only be performed using encryption software that operates within Windows, such as EFS. BitLocker and EFS, therefore, offer protection against different classes of attacks.
533:: The user must insert a USB device that contains a startup key into the computer to be able to boot the protected OS. Note that this mode requires that the BIOS on the protected machine supports the reading of USB devices in the pre-OS environment. BitLocker does not support smart cards for pre-boot authentication.
797:
Starting with
Windows 8 and Windows Server 2012, Microsoft removed the Elephant Diffuser from the BitLocker scheme for no declared reason. Dan Rosendorf's research shows that removing the Elephant Diffuser had an "undeniably negative impact" on the security of BitLocker encryption against a targeted
484:
In
September 2019 a new update was released (KB4516071) changing the default setting for BitLocker when encrypting a self-encrypting hard drive. Now, the default is to use software encryption for newly encrypted drives. This is due to hardware encryption flaws and security concerns related to those
226:
architecture in 2004 as a feature tentatively codenamed "Cornerstone" and was designed to protect information on devices, particularly if a device was lost or stolen. Another feature, titled "Code
Integrity Rooting", was designed to validate the integrity of Microsoft Windows boot and system files.
608:
are configured. The volume is then encrypted as a background task, something that may take a considerable amount of time with a large disk as every logical sector is read, encrypted and rewritten back to disk. The keys are only protected after the whole volume has been encrypted when the volume is
421:
Starting with
Windows Server 2012 and Windows 8, Microsoft has complemented BitLocker with the Microsoft Encrypted Hard Drive specification, which allows the cryptographic operations of BitLocker encryption to be offloaded to the storage device's hardware. In addition, BitLocker can now be managed
386:
volume. Starting with
Windows Vista with Service Pack 1 and Windows Server 2008, volumes other than the operating system volume could be encrypted using the graphical tool. Still, some aspects of the BitLocker (such as turning autolocking on or off) had to be managed through a command-line tool
49:
504:
is sealed (encrypted) by the TPM chip and will only be released to the OS loader code if the early boot files appear to be unmodified. The pre-OS components of BitLocker achieve this by implementing a Static Root of Trust
Measurement—a methodology specified by the
626:. Once the malicious bootloader captures the secret, it can decrypt the Volume Master Key (VMK), which would then allow access to decrypt or modify any information on an encrypted hard disk. By configuring a TPM to protect the trusted boot pathway, including the
618:
In Active
Directory environments, BitLocker supports optional key escrow to Active Directory, although a schema update may be required for this to work (i.e. if the Active Directory Services are hosted on a Windows version previous to Windows Server 2008).
231:(TPM), BitLocker can validate the integrity of boot and system files before decrypting a protected volume; an unsuccessful validation will prohibit access to a protected system. BitLocker was briefly called Secure Startup before Windows Vista's
2746:
577:, the whole drive or more than one drive.) When enabled, TPM and BitLocker can ensure the integrity of the trusted boot path (e.g. BIOS and boot sector), in order to prevent most offline physical attacks and boot sector malware.
603:
Once an alternate boot partition has been created, the TPM module needs to be initialized (assuming that this feature is being used), after which the required disk-encryption key protection mechanisms such as TPM, PIN or
461:
requires Pro editions of
Windows), allowing it to be retrieved from any computer. While device encryption is offered on all editions of Windows 8.1, unlike BitLocker, device encryption requires that the device meet the
1708:
609:
considered secure. BitLocker uses a low-level device driver to encrypt and decrypt all file operations, making interaction with the encrypted volume transparent to applications running on the platform.
759:
agents also put pressure on them in numerous meetings to add a backdoor, although no formal, written request was ever made; Microsoft engineers eventually suggested that agents should look for the
1023:
806:
encryption algorithm to BitLocker. Starting with
Windows 10 version 1803, Microsoft added a new feature called "Kernel Direct Memory access (DMA) Protection" to BitLocker, to protect against
651:
The "Transparent operation mode" and "User authentication mode" of BitLocker use TPM hardware to detect whether there are unauthorized changes to the pre-boot environment, including the
989:
659:. If any unauthorized changes are detected, BitLocker requests a recovery key on a USB device. This cryptographic secret is used to decrypt the Volume Master Key (VMK) and allow the
2726:
671:" that allows full disk encryption systems such as BitLocker to be compromised by booting the machine from removable media, such as a USB drive, into another operating system, then
822:
Device, which can in turn write directly to the memory and bypass the
Windows login. To protect again this type of attack, Microsoft introduced "Virtualization-based Security".
701:
On 10 November 2015, Microsoft released a security update to mitigate a security vulnerability in BitLocker that allowed authentication to be bypassed by employing a malicious
708:
BitLocker still does not properly support TPM 2.0 security features which, as a result, can lead to a complete bypass of privacy protection when keys are transmitted over
2466:
1816:
1119:
1526:
686:, described in US Patent 9,514,789, can accomplish this type of attack. Similar full disk encryption mechanisms of other vendors and other operating systems, including
1716:
517:
by an attacker. It is also vulnerable to a sniffing attack, as the volume encryption key is transferred in plain text from the TPM to the CPU during a successful boot.
500:: This mode uses the capabilities of TPM 1.2 hardware to provide for transparent user experience—the user powers up and logs into Windows as usual. The key used for
1894:
5430:
1842:
2635:
5649:
1231:
1429:
3462:
2667:
1868:
694:, are vulnerable to the same attack. The authors recommend that computers be powered down when not in physical control of the owner (rather than be left in a
1790:
1739:
3477:
705:
key distribution center, if the attacker had physical access to the machine, the machine was part of a domain and had no PIN or USB flash drive protection.
2524:
4495:
3642:
2719:
584:-formatted volumes are required: one for the operating system (usually C:) and another with a minimum size of 100 MB, which remains unencrypted and
1035:
751:
expressed concern over the lack of a backdoor and tried entering into talks with Microsoft to get one introduced. Microsoft developer and cryptographer
2079:
814:
ports. "Kernel Direct Memory access (DMA) Protection" only protects against attacks through Thunderbolt. Direct Memory Access is also possible through
2694:
2439:
1365:
1179:
1149:
829:, which could allow an attacker to bypass BitLocker encryption when an affected TPM chip is used. The flaw is the Return of Coppersmith's Attack or
799:
5174:
3299:
1560:
2546:
957:
5520:
4333:
2712:
2054:
2021:
865:
223:
1258:
997:
4462:
2735:
1092:
1064:
855:
477:
Starting with Windows 10 1703, the requirements for device encryption have changed, requiring a TPM 1.2 or 2.0 module with PCR 7 support,
453:
with administrative privileges automatically begins the encryption process. The recovery key is stored to either the Microsoft account or
128:
716:
All these attacks require physical access to the system and are thwarted by a secondary protector such as a USB flash drive or PIN code.
3712:
3352:
2936:
2771:
1460:
5128:
3884:
3793:
3309:
2941:
1985:
1595:
1953:
1681:
927:
1764:
394:
The version of BitLocker included in Windows 7 and Windows Server 2008 Release 2 adds the ability to encrypt removable drives. On
1925:
1333:
893:
802:(FIPS), to justify the diffuser's removal. Starting with Windows 10 version 1511, however, Microsoft added a new FIPS-compliant
40:
5644:
3632:
3612:
3575:
3537:
3522:
2184:"Systems and methods for safely moving short term memory devices while preserving, protecting and examining their digital data"
1397:
841:
and TPMs. Microsoft released an updated version of the firmware for Infineon TPM chips that fixes the flaw via Windows Update.
756:
1307:
5425:
5148:
4488:
4378:
3960:
3487:
860:
524:
374:
2473:
2261:
1629:
3502:
2111:
1281:
850:
5614:
5254:
4343:
4212:
3899:
3889:
3763:
3667:
3527:
2884:
2839:
676:
187:
2612:
2234:
398:
or Windows Vista, read-only access to these drives can be achieved through a program called BitLocker To Go Reader, if
5565:
5169:
4751:
4451:
3819:
3778:
3677:
3532:
3329:
3044:
2994:
709:
2153:
523:: This mode requires that the user provide some authentication to the pre-boot environment in the form of a pre-boot
4041:
3921:
3627:
3126:
2766:
2759:
2754:
2525:"Blocking the SBP-2 driver and Thunderbolt controllers to reduce 1394 DMA and Thunderbolt DMA threats to BitLocker"
5609:
5294:
5289:
5229:
4481:
4373:
4338:
3768:
3758:
3697:
3607:
3497:
3467:
3116:
2814:
771:
597:
5654:
3738:
3682:
3662:
3507:
3276:
3161:
1655:
733:
683:
232:
195:
117:
3051:
4323:
4318:
4162:
4157:
4117:
4077:
4027:
3773:
3517:
3512:
3387:
3362:
3324:
3294:
3244:
3056:
2979:
2904:
2824:
2799:
2311:
826:
785:
Since 2020, BitLocker's method and data structure is public knowledge due to reverse engineering; the Linux
755:
denied the backdoor request and said, "over my dead body". Microsoft engineers have said that United States
635:
506:
228:
5639:
5143:
4882:
4600:
4507:
4303:
4267:
3879:
3864:
3622:
3580:
3472:
3402:
3319:
3304:
2899:
803:
612:
246:
242:
199:
167:
1495:
634:, BitLocker can mitigate this threat. (Note that some non-malicious changes to the boot path may cause a
5588:
5093:
4715:
4710:
4705:
4700:
4432:
4252:
4197:
4137:
4122:
3931:
3602:
3557:
3414:
3367:
191:
1572:
782:
should be secure, even if everything about the system, except the encryption key, is public knowledge.
537:
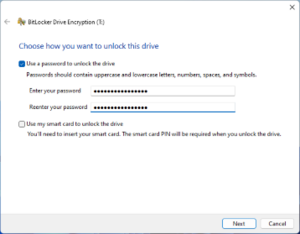
The following combinations of the above authentication mechanisms are supported, all with an optional
48:
5583:
5578:
5476:
5244:
4994:
4984:
4887:
4417:
4412:
4257:
4227:
4192:
4082:
3788:
3783:
3687:
3637:
3595:
3565:
3452:
3039:
3004:
2951:
2889:
2162:
1157:
740:
729:
361:
2394:
5624:
5619:
5375:
5153:
5098:
4605:
4473:
4358:
4217:
4172:
4147:
4102:
4048:
3847:
3702:
3585:
3034:
3019:
2959:
2879:
2849:
702:
589:
364:
349:
344:
272:
112:
732:; however, the code is available for scrutiny by Microsoft partners and enterprises, subject to a
493:
Three authentication mechanisms can be used as building blocks to implement BitLocker encryption:
153:
5634:
5629:
5080:
5070:
4821:
4363:
4313:
4087:
4006:
3992:
3911:
3617:
3457:
3424:
3397:
3392:
3066:
2969:
2964:
2864:
2499:
2367:
830:
775:
656:
570:
438:
423:
207:
183:
2148:; Clarkson, William; Paul, William; Calandrino, Joseph A.; Feldman, Ariel J.; Appelbaum, Jacob;
5345:
4746:
4663:
4652:
4504:
4427:
4353:
4308:
4207:
4202:
4177:
4132:
4097:
3967:
3271:
3081:
2914:
2420:
2060:
2050:
2027:
2017:
1958:
1930:
1465:
1434:
1370:
1338:
898:
471:
467:
450:
337:
171:
105:
1205:
5550:
5088:
4933:
4928:
4918:
4791:
4537:
4368:
4277:
4112:
4055:
4013:
3874:
3842:
3798:
3753:
3672:
3432:
3229:
3106:
3096:
2859:
2854:
1031:
770:
Niels Ferguson's position that "back doors are simply not acceptable" is in accordance with
682:
for up to several minutes (or even longer, if cooled) after the power has been removed. The
668:
510:
478:
458:
454:
383:
356:
332:
100:
1607:
698:) and that the encryption software be configured to require a password to boot the machine.
449:, a feature-limited version of BitLocker that encrypts the whole system. Logging in with a
5510:
5484:
5239:
5138:
5065:
5014:
5004:
4979:
4892:
4877:
4801:
4725:
4404:
4287:
4262:
4247:
4237:
4187:
4182:
3936:
3570:
3286:
3151:
3141:
3086:
3071:
2929:
2819:
2699:
2338:
2204:
2089:
744:
574:
501:
580:
In order for BitLocker to encrypt the volume holding the operating system, at least two
5540:
5320:
5133:
5108:
5055:
5035:
4999:
4974:
4964:
4954:
4862:
4857:
4642:
4610:
4574:
4569:
4564:
3894:
3437:
3249:
3239:
3224:
3156:
3024:
2999:
2974:
2924:
2894:
2804:
2183:
2145:
764:
752:
679:
825:
In October 2017, it was reported that a flaw enabled private keys to be inferred from
5603:
5515:
5204:
5040:
5009:
4831:
4826:
4720:
4657:
4615:
4559:
4511:
4383:
4242:
4142:
3482:
3442:
3219:
3194:
3186:
3121:
2989:
2789:
2645:
2149:
1536:
811:
739:
According to Microsoft sources, BitLocker does not contain an intentionally built-in
725:
427:
382:
Initially, the graphical BitLocker interface in Windows Vista could only encrypt the
250:
175:
789:
program is capable of reading and writing BitLocker-protected drives given the key.
728:, its implementation in BitLocker, as well as other components of the software, are
667:
In February 2008, a group of security researchers published details of a so-called "
5535:
5530:
5330:
5325:
5050:
4852:
4553:
4152:
4107:
4034:
3999:
3707:
3657:
3447:
3199:
3146:
3111:
3029:
3009:
2829:
2809:
2640:
2084:
2080:"Prevent data theft with Windows Vista's Encrypted File System (EFS) and BitLocker"
1603:
1531:
1311:
985:
779:
593:
1817:"ProtectKeyWithTPMAndPINAndStartupKey method of the Win32_EncryptableVolume class"
2590:
1527:"Windows 8.1 includes seamless, automatic disk encryption—if your PC supports it"
5355:
5184:
4836:
4776:
4522:
4222:
4167:
4072:
3926:
3814:
3692:
3547:
3339:
3314:
2909:
2286:
2141:
819:
815:
748:
631:
264:
211:
2704:
798:
attack. Microsoft later cited performance concerns, and noncompliance with the
5385:
5284:
5274:
4532:
4127:
3951:
3492:
3382:
3256:
3176:
3101:
2919:
807:
786:
695:
538:
442:
395:
302:
285:
279:
179:
70:
54:
2064:
2031:
1895:"ProtectKeyWithNumericalPassword method of the Win32_EncryptableVolume class"
5560:
5269:
4647:
3743:
3377:
3266:
3214:
2984:
2212:
1963:
1843:"ProtectKeyWithTPMAndStartupKey method of the Win32_EncryptableVolume class"
1568:
1503:
1470:
1439:
1407:
1375:
1343:
1127:
1088:
1060:
993:
958:"AES-CBC + Elephant Diffuser: A Disk Encryption Algorithm for Windows Vista"
903:
870:
838:
760:
672:
481:, and that the device meets Modern Standby requirements or HSTI validation.
463:
307:
260:
254:
75:
39:
5456:
5415:
5395:
5390:
5380:
5365:
5350:
5315:
5310:
5224:
5219:
5194:
5189:
5118:
5113:
4969:
4938:
4902:
4897:
4867:
4811:
4781:
4771:
4766:
4761:
4756:
4674:
4328:
4232:
4092:
3852:
3717:
3347:
3204:
3091:
3076:
3014:
2874:
2834:
2636:"Millions of high-security crypto keys crippled by newly discovered flaw"
1740:"Using BitLocker with other programs FAQ (Windows 10) - Windows security"
834:
17:
210:. CBC is not used over the whole disk; it is applied to each individual
5555:
5489:
5461:
5451:
5446:
5420:
5410:
5405:
5360:
5340:
5279:
5264:
5259:
5234:
5214:
5199:
5060:
4679:
4621:
4527:
4348:
4282:
4020:
3906:
3869:
3857:
3542:
3261:
3234:
3209:
3171:
2869:
2794:
2467:"Bitlocker: A little about the internals and what changed in Windows 8"
1869:"ProtectKeyWithExternalKey method of the Win32_EncryptableVolume class"
660:
623:
605:
585:
514:
2395:"Did the FBI Lean On Microsoft for Access to Its Encryption Software?"
2262:"No Back Doors: Microsoft Opens Windows Source Code to EU Governments"
747:
to have guaranteed access to the data on a user's drive. In 2006, the
622:
BitLocker and other full disk encryption systems can be attacked by a
5545:
5494:
5466:
5335:
5249:
5103:
5019:
4989:
4959:
4796:
4741:
4637:
4590:
4422:
4272:
3941:
3722:
3647:
2568:
1926:"BitLocker Drive Encryption in Windows 7: Frequently Asked Questions"
1791:"ProtectKeyWithTPMAndPIN method of the Win32_EncryptableVolume class"
1682:"Flaws in self-encrypting SSDs let attackers bypass disk encryption"
675:
the contents of pre-boot memory. The attack relies on the fact that
5525:
5400:
5370:
5209:
5045:
4923:
4872:
4816:
4786:
4684:
4668:
4631:
4626:
4595:
4388:
3824:
3652:
3357:
3131:
2844:
1686:
724:
Although the AES encryption algorithm used in BitLocker is in the
691:
687:
410:
filesystems are used. In addition, a new command-line tool called
407:
403:
399:
2591:"Securing BitLocker: Initial Setup and Defending Against Attacks"
2500:"Microsoft Gives Details About Its Controversial Disk Encryption"
5179:
5123:
3916:
3590:
3409:
3372:
1402:
652:
627:
581:
4477:
2708:
1765:"ProtectKeyWithTPM method of the Win32_EncryptableVolume class"
928:"Windows BitLocker Drive Encryption Frequently Asked Questions"
818:. In this type of attack an attacker would connect a malicious
592:, however, the volume's minimum size is 1.5 GB and must have a
3834:
3166:
3136:
3061:
2668:"Infineon says has fixed encryption flaw found by researchers"
2342:
203:
1093:"Secure Startup – Full Volume Encryption: Executive Overview"
837:
and had been in widespread use in security products such as
1065:"Secure Startup–Full Volume Encryption: Technical Overview"
2112:"Keys to Protecting Data with BitLocker Drive Encryption"
1713:
Data Encryption Toolkit for Mobile PCs: Security Analysis
767:
that the BitLocker program suggests that its users make.
1490:
1488:
430:
in its Enterprise edition, which BitLocker can protect.
2047:
Introducing Windows 8: An Overview for IT professionals
1954:"Windows BitLocker Drive Encryption Step-by-Step Guide"
663:
process to continue. However, TPM alone is not enough:
2155:
Lest We Remember: Cold Boot Attacks on Encryption Keys
638:
check to fail, and thereby generate a false warning.)
2393:
Franceschi-Bicchierai, Lorenzo (September 11, 2013).
1986:"Description of the BitLocker Drive Preparation Tool"
200:-based Tweaked codebook mode with ciphertext Stealing
1656:"September 24, 2019—KB4516071 (OS Build 16299.1420)"
1055:
1053:
588:
the operating system. (In case of Windows Vista and
5503:
5475:
5439:
5303:
5162:
5079:
5028:
4947:
4911:
4845:
4734:
4693:
4583:
4546:
4401:
4296:
4065:
3984:
3977:
3950:
3833:
3807:
3731:
3556:
3423:
3338:
3285:
3185:
2950:
2780:
1630:"BitLocker drive encryption in Windows 10 for OEMs"
1024:"Pre-PDC Exclusive: Windows Vista Product Editions"
370:
355:
343:
331:
313:
301:
123:
111:
99:
81:
69:
61:
2235:"From Stolen Laptop to Inside the Company Network"
2205:"Microsoft Security Bulletin MS15-122 – Important"
894:"What's new in Windows 10, versions 1507 and 1511"
1561:"Help protect your files with device encryption"
1232:"Finding your BitLocker recovery key in Windows"
778:in the 19th century, the principle holds that a
980:
978:
269:Windows Embedded Standard 7 and Windows Thin PC
1555:
1553:
1334:"Enabling BitLocker by Using the Command Line"
1114:
1112:
222:BitLocker originated as a part of Microsoft's
178:. It is designed to protect data by providing
27:Disk encryption software for Microsoft Windows
4489:
2720:
2695:BitLocker Drive Encryption Technical Overview
1150:"BitLocker Drive Encryption in Windows Vista"
573:encryption system. (A volume spans part of a
8:
2135:
2133:
2016:(1 ed.). Microsoft Press. p. 307.
743:, so there is no Microsoft-provided way for
513:, as it allows a powered-down machine to be
296:
32:
1461:"Windows To Go: Frequently Asked Questions"
774:. Stated by Netherlands-born cryptographer
284:Pro, Enterprise, and Education editions of
278:Pro, Enterprise, and Education editions of
227:When used in conjunction with a compatible
4496:
4482:
4474:
4457:
3981:
2727:
2713:
2705:
2007:
2005:
2003:
1920:
1918:
1916:
1715:. Microsoft. April 4, 2007. Archived from
887:
885:
295:
152:
31:
2547:"Kernel DMA Protection for Thunderbolt 3"
951:
949:
445:and core editions of Windows 8.1 include
1282:"Advances in BitLocker Drive Encryption"
833:which is in a code library developed by
800:Federal Information Processing Standards
2368:"Microsoft: Vista won't get a backdoor"
1525:Cunningham, Andrew (October 17, 2013).
1308:"Description of BitLocker To Go Reader"
990:"Next-Generation Secure Computing Base"
881:
2337:Stone-Lee, Ollie (February 16, 2006).
2014:Exam Ref 70-687: Configuring Windows 8
2012:Andrew, Bettany; Halsey, Mike (2013).
53:BitLocker Drive Encryption utility on
5650:Microsoft Windows security technology
4334:Next-Generation Secure Computing Base
2666:Busvine, Douglas (October 16, 2017).
2361:
2359:
1680:Cimpanu, Catalin (November 5, 2018).
1600:Paul Thurrott's SuperSite for Windows
1180:"BitLocker Drive Encryption Overview"
922:
920:
866:Next-Generation Secure Computing Base
224:Next-Generation Secure Computing Base
7:
2419:Trefny, Vojtech (January 25, 2020).
1022:Thurrott, Paul (September 9, 2005).
856:List of Microsoft Windows components
509:(TCG). This mode is vulnerable to a
3463:Distributed Transaction Coordinator
2339:"UK holds Microsoft security talks"
1398:"Encrypted Hard Drive Device Guide"
1257:Yegulalp, Serdar (August 7, 2007).
3794:User Interface Privilege Isolation
2422:BitLocker disk encryption on Linux
2110:Byron, Hynes (September 7, 2016).
1280:Hynes, Byron (September 8, 2016).
892:Hakala, Trudy (January 29, 2020).
25:
470:) specifications, which requires
4456:
4446:
4445:
2634:Goodin, Dan (October 16, 2017).
2260:Thurrott, Paul (June 10, 2015).
2078:Ou, George (February 28, 2007).
720:Upholding Kerckhoffs's principle
426:. Finally, Windows 8 introduced
47:
38:
3523:Remote Differential Compression
2465:Rosendorf, Dan (May 23, 2013).
1934:. Microsoft. September 12, 2012
1594:Thurrott, Paul (June 4, 2013).
956:Ferguson, Niels (August 2006).
757:Federal Bureau of Investigation
636:Platform Configuration Register
600:files to be transferred to it.
259:Pro and Enterprise editions of
4379:Windows System Assessment Tool
2366:Evers, Joris (March 6, 2006).
1988:. Microsoft. December 21, 2011
1259:"Vista's BitLocker Encryption"
1186:. Microsoft. November 17, 2009
861:Windows Vista I/O technologies
1:
2527:. Microsoft. November 7, 2018
1206:"Compare Windows 10 Editions"
851:Features new to Windows Vista
3668:Open XML Paper Specification
3528:Remote Installation Services
2736:Microsoft Windows components
1709:"BitLocker Drive Encryption"
1596:"In Blue: Device Encryption"
188:Advanced Encryption Standard
3820:Windows Subsystem for Linux
3779:Mandatory Integrity Control
3533:Windows Deployment Services
3330:Wireless Zero Configuration
2615:. Microsoft. March 20, 2023
2549:. Microsoft. March 26, 2019
2498:Lee, Micah (June 4, 2015).
1901:. Microsoft. March 31, 2018
1875:. Microsoft. March 31, 2018
1849:. Microsoft. March 31, 2018
1823:. Microsoft. March 31, 2018
1797:. Microsoft. March 31, 2018
1771:. Microsoft. March 31, 2018
1310:. Microsoft. Archived from
1156:. Microsoft. Archived from
934:. Microsoft. March 22, 2012
710:Serial Peripheral Interface
238:BitLocker is available on:
5671:
3922:Universal Windows Platform
3628:Kernel Transaction Manager
3613:Hardware Abstraction Layer
3310:Multimedia Class Scheduler
2700:System Integrity Team Blog
2593:. VidraSec. March 15, 2024
2318:. Microsoft. March 2, 2006
2316:System Integrity Team Blog
2287:"Shared Source Initiative"
2049:. Microsoft. p. 121.
498:Transparent operation mode
186:. By default, it uses the
141:/operating-system-security
5574:
4518:
4441:
4374:Windows Services for UNIX
3759:Data Execution Prevention
3608:Graphics Device Interface
3498:Network Access Protection
3117:Remote Desktop Connection
2742:
2571:. Ulf Frisk. June 6, 2024
2045:Jerry, Honeycutt (2012).
1120:"What's New in BitLocker"
719:
46:
37:
3739:Security and Maintenance
3683:Security Account Manager
3277:Windows XP visual styles
734:non-disclosure agreement
521:User authentication mode
233:release to manufacturing
202:" (XTS) mode with a 128-
118:Disk encryption software
4324:Media Control Interface
4158:Help and Support Center
3774:Kernel Patch Protection
3538:System Resource Manager
3518:Remote Desktop Services
3513:Print Services for UNIX
3295:Service Control Manager
2905:Windows Error Reporting
2825:DirectX Diagnostic Tool
647:TPM alone is not enough
507:Trusted Computing Group
229:Trusted Platform Module
174:versions starting with
5645:Cryptographic software
4547:File system navigation
4304:Desktop Cleanup Wizard
3880:COM Structured storage
3581:Desktop Window Manager
3473:Windows Media Services
1366:"Encrypted Hard Drive"
772:Kerckhoffs's principle
613:Encrypting File System
319:; 17 years ago
170:feature included with
168:full volume encryption
87:; 17 years ago
5589:Windows Support Tools
5584:Environment variables
3932:Windows Mixed Reality
3603:Enhanced Write Filter
3453:Roaming user profiles
2444:technet.microsoft.com
2152:(February 21, 2008).
1660:support.microsoft.com
1314:on September 24, 2019
1028:Supersite for Windows
317:January 30, 2007
192:cipher block chaining
85:January 30, 2007
5579:List of DOS commands
5477:Software development
5304:Maintenance and care
4213:Mobile Device Center
4163:Health & Fitness
3961:Solitaire Collection
3789:User Account Control
3784:Protected Media Path
3688:Server Message Block
3638:Logical Disk Manager
2890:System Policy Editor
2875:System Configuration
2440:"BitLocker Overview"
2312:"Back-door nonsense"
2163:Princeton University
2140:Halderman, J. Alex;
1346:. September 12, 2012
1210:Windows for Business
1160:on November 17, 2016
474:and a TPM 2.0 chip.
5615:Windows Server 2008
4359:Virtual DOS machine
3703:System Idle Process
3678:Resource Protection
3586:Portable Executable
3478:Active DRM Services
2880:System File Checker
2850:Performance Monitor
2479:on October 22, 2021
2209:Security TechCenter
1719:on October 23, 2007
1636:. November 16, 2018
1565:Windows Help portal
1506:. November 18, 2015
1496:"Device Encryption"
680:retains information
590:Windows Server 2008
551:TPM + PIN + USB Key
365:commercial software
298:
273:Windows Server 2008
190:(AES) algorithm in
34:
4533:Windows PowerShell
4364:Windows on Windows
4088:Backup and Restore
3900:Transaction Server
3618:I/O request packet
3458:Folder redirection
3127:Speech Recognition
2885:System Information
2840:Management Console
2215:. October 11, 2017
1744:docs.microsoft.com
1634:docs.microsoft.com
1473:. October 23, 2013
1091:(April 21, 2005).
1063:(April 22, 2005).
1003:on August 27, 2006
831:ROCA vulnerability
776:Auguste Kerckhoffs
624:rogue boot manager
472:solid-state drives
439:Windows Mobile 6.5
424:Windows PowerShell
5597:
5596:
4471:
4470:
4397:
4396:
4354:Video for Windows
4309:Games for Windows
4178:Internet Explorer
3272:Windows Spotlight
2915:Windows Installer
2446:. August 31, 2016
2374:. CBS Interactive
2291:www.microsoft.com
2056:978-0-7356-7050-1
2023:978-0-7356-7392-2
1500:Device Encryption
1378:. August 31, 2016
1130:. August 31, 2016
712:in a motherboard.
684:Bress/Menz device
642:Security concerns
468:Connected Standby
451:Microsoft account
447:device encryption
434:Device encryption
414:replaced the old
380:
379:
338:Microsoft Windows
172:Microsoft Windows
161:
160:
106:Microsoft Windows
65:Device Encryption
16:(Redirected from
5662:
5610:Windows commands
4948:User environment
4538:Recovery Console
4498:
4491:
4484:
4475:
4460:
4459:
4449:
4448:
4369:Windows SideShow
4148:Food & Drink
4042:Spider Solitaire
3982:
3875:ActiveX Document
3843:Active Scripting
3799:Windows Firewall
3754:Credential Guard
3433:Active Directory
3230:Indexing Service
2860:Resource Monitor
2855:Recovery Console
2729:
2722:
2715:
2706:
2683:
2682:
2680:
2678:
2663:
2657:
2656:
2654:
2652:
2631:
2625:
2624:
2622:
2620:
2609:
2603:
2602:
2600:
2598:
2587:
2581:
2580:
2578:
2576:
2565:
2559:
2558:
2556:
2554:
2543:
2537:
2536:
2534:
2532:
2521:
2515:
2514:
2512:
2510:
2495:
2489:
2488:
2486:
2484:
2478:
2472:. Archived from
2471:
2462:
2456:
2455:
2453:
2451:
2436:
2430:
2429:
2427:
2416:
2410:
2409:
2407:
2405:
2390:
2384:
2383:
2381:
2379:
2363:
2354:
2353:
2351:
2349:
2334:
2328:
2327:
2325:
2323:
2308:
2302:
2301:
2299:
2297:
2283:
2277:
2276:
2274:
2272:
2257:
2251:
2250:
2248:
2246:
2231:
2225:
2224:
2222:
2220:
2201:
2195:
2194:
2192:
2190:
2180:
2174:
2173:
2171:
2169:
2160:
2150:Felten, Edward W
2137:
2128:
2127:
2125:
2123:
2116:TechNet Magazine
2107:
2101:
2100:
2098:
2096:
2075:
2069:
2068:
2042:
2036:
2035:
2009:
1998:
1997:
1995:
1993:
1982:
1976:
1975:
1973:
1971:
1950:
1944:
1943:
1941:
1939:
1922:
1911:
1910:
1908:
1906:
1891:
1885:
1884:
1882:
1880:
1865:
1859:
1858:
1856:
1854:
1839:
1833:
1832:
1830:
1828:
1813:
1807:
1806:
1804:
1802:
1787:
1781:
1780:
1778:
1776:
1761:
1755:
1754:
1752:
1750:
1735:
1729:
1728:
1726:
1724:
1705:
1699:
1698:
1696:
1694:
1677:
1671:
1670:
1668:
1666:
1652:
1646:
1645:
1643:
1641:
1626:
1620:
1619:
1617:
1615:
1606:. Archived from
1591:
1585:
1584:
1582:
1580:
1571:. Archived from
1557:
1548:
1547:
1545:
1543:
1522:
1516:
1515:
1513:
1511:
1492:
1483:
1482:
1480:
1478:
1457:
1451:
1450:
1448:
1446:
1426:
1420:
1419:
1417:
1415:
1394:
1388:
1387:
1385:
1383:
1362:
1356:
1355:
1353:
1351:
1330:
1324:
1323:
1321:
1319:
1304:
1298:
1297:
1295:
1293:
1286:TechNet Magazine
1277:
1271:
1270:
1268:
1266:
1254:
1248:
1247:
1245:
1243:
1228:
1222:
1221:
1219:
1217:
1202:
1196:
1195:
1193:
1191:
1176:
1170:
1169:
1167:
1165:
1146:
1140:
1139:
1137:
1135:
1116:
1107:
1106:
1104:
1102:
1097:
1085:
1079:
1078:
1076:
1074:
1069:
1057:
1048:
1047:
1045:
1043:
1038:on April 2, 2015
1034:. Archived from
1019:
1013:
1012:
1010:
1008:
1002:
996:. Archived from
982:
973:
972:
970:
968:
962:
953:
944:
943:
941:
939:
924:
915:
914:
912:
910:
889:
669:cold boot attack
511:cold boot attack
489:Encryption modes
479:UEFI Secure Boot
459:Active Directory
455:Active Directory
417:
413:
390:
384:operating system
333:Operating system
327:
325:
320:
299:
157:
156:
149:
146:
144:
143:/data-protection
142:
140:
138:
136:
134:
132:
130:
101:Operating system
95:
93:
88:
51:
42:
35:
21:
5670:
5669:
5665:
5664:
5663:
5661:
5660:
5659:
5655:Disk encryption
5600:
5599:
5598:
5593:
5570:
5499:
5471:
5440:Boot management
5435:
5299:
5158:
5075:
5024:
4943:
4907:
4841:
4735:Disk management
4730:
4689:
4584:File management
4579:
4542:
4514:
4502:
4472:
4467:
4437:
4405:Microsoft Store
4403:
4393:
4339:POSIX subsystem
4319:File Protection
4292:
4263:Program Manager
4248:Phone Companion
4238:Outlook Express
4188:Make Compatible
4118:Desktop Gadgets
4078:Anytime Upgrade
4061:
3973:
3946:
3937:Windows Runtime
3829:
3803:
3769:Family features
3727:
3552:
3508:DFS Replication
3419:
3334:
3325:Error Reporting
3281:
3181:
3057:Mobility Center
3052:Movies & TV
2946:
2930:Windows Insider
2820:Driver Verifier
2815:Drive Optimizer
2782:
2776:
2767:Booting process
2738:
2733:
2691:
2686:
2676:
2674:
2665:
2664:
2660:
2650:
2648:
2633:
2632:
2628:
2618:
2616:
2611:
2610:
2606:
2596:
2594:
2589:
2588:
2584:
2574:
2572:
2567:
2566:
2562:
2552:
2550:
2545:
2544:
2540:
2530:
2528:
2523:
2522:
2518:
2508:
2506:
2497:
2496:
2492:
2482:
2480:
2476:
2469:
2464:
2463:
2459:
2449:
2447:
2438:
2437:
2433:
2425:
2418:
2417:
2413:
2403:
2401:
2392:
2391:
2387:
2377:
2375:
2365:
2364:
2357:
2347:
2345:
2336:
2335:
2331:
2321:
2319:
2310:
2309:
2305:
2295:
2293:
2285:
2284:
2280:
2270:
2268:
2259:
2258:
2254:
2244:
2242:
2241:. July 28, 2021
2233:
2232:
2228:
2218:
2216:
2203:
2202:
2198:
2188:
2186:
2182:
2181:
2177:
2167:
2165:
2158:
2146:Heninger, Nadia
2142:Schoen, Seth D.
2139:
2138:
2131:
2121:
2119:
2109:
2108:
2104:
2094:
2092:
2090:CBS Interactive
2077:
2076:
2072:
2057:
2044:
2043:
2039:
2024:
2011:
2010:
2001:
1991:
1989:
1984:
1983:
1979:
1969:
1967:
1952:
1951:
1947:
1937:
1935:
1924:
1923:
1914:
1904:
1902:
1893:
1892:
1888:
1878:
1876:
1867:
1866:
1862:
1852:
1850:
1841:
1840:
1836:
1826:
1824:
1815:
1814:
1810:
1800:
1798:
1789:
1788:
1784:
1774:
1772:
1763:
1762:
1758:
1748:
1746:
1737:
1736:
1732:
1722:
1720:
1707:
1706:
1702:
1692:
1690:
1679:
1678:
1674:
1664:
1662:
1654:
1653:
1649:
1639:
1637:
1628:
1627:
1623:
1613:
1611:
1610:on June 9, 2013
1593:
1592:
1588:
1578:
1576:
1559:
1558:
1551:
1541:
1539:
1524:
1523:
1519:
1509:
1507:
1494:
1493:
1486:
1476:
1474:
1459:
1458:
1454:
1444:
1442:
1428:
1427:
1423:
1413:
1411:
1396:
1395:
1391:
1381:
1379:
1364:
1363:
1359:
1349:
1347:
1332:
1331:
1327:
1317:
1315:
1306:
1305:
1301:
1291:
1289:
1279:
1278:
1274:
1264:
1262:
1261:. Computerworld
1256:
1255:
1251:
1241:
1239:
1236:Windows support
1230:
1229:
1225:
1215:
1213:
1204:
1203:
1199:
1189:
1187:
1178:
1177:
1173:
1163:
1161:
1148:
1147:
1143:
1133:
1131:
1124:TechNet Library
1118:
1117:
1110:
1100:
1098:
1095:
1087:
1086:
1082:
1072:
1070:
1067:
1059:
1058:
1051:
1041:
1039:
1021:
1020:
1016:
1006:
1004:
1000:
984:
983:
976:
966:
964:
960:
955:
954:
947:
937:
935:
932:TechNet Library
926:
925:
918:
908:
906:
891:
890:
883:
879:
847:
795:
745:law enforcement
722:
649:
644:
575:hard disk drive
569:BitLocker is a
567:
502:disk encryption
491:
436:
415:
411:
388:
323:
321:
318:
314:Initial release
294:
220:
196:xor–encrypt–xor
151:
127:
91:
89:
86:
82:Initial release
57:
28:
23:
22:
15:
12:
11:
5:
5668:
5666:
5658:
5657:
5652:
5647:
5642:
5637:
5632:
5627:
5622:
5617:
5612:
5602:
5601:
5595:
5594:
5592:
5591:
5586:
5581:
5575:
5572:
5571:
5569:
5568:
5563:
5558:
5553:
5548:
5543:
5538:
5533:
5528:
5523:
5518:
5513:
5507:
5505:
5501:
5500:
5498:
5497:
5492:
5487:
5481:
5479:
5473:
5472:
5470:
5469:
5464:
5459:
5454:
5449:
5443:
5441:
5437:
5436:
5434:
5433:
5428:
5423:
5418:
5413:
5408:
5403:
5398:
5393:
5388:
5383:
5378:
5373:
5368:
5363:
5358:
5353:
5348:
5343:
5338:
5333:
5328:
5323:
5318:
5313:
5307:
5305:
5301:
5300:
5298:
5297:
5292:
5287:
5282:
5277:
5272:
5267:
5262:
5257:
5252:
5247:
5242:
5237:
5232:
5227:
5222:
5217:
5212:
5207:
5202:
5197:
5192:
5187:
5182:
5177:
5172:
5166:
5164:
5160:
5159:
5157:
5156:
5151:
5146:
5141:
5136:
5131:
5126:
5121:
5116:
5111:
5106:
5101:
5096:
5091:
5085:
5083:
5077:
5076:
5074:
5073:
5068:
5063:
5058:
5053:
5048:
5043:
5038:
5032:
5030:
5026:
5025:
5023:
5022:
5017:
5012:
5007:
5002:
4997:
4992:
4987:
4982:
4977:
4972:
4967:
4962:
4957:
4951:
4949:
4945:
4944:
4942:
4941:
4936:
4931:
4926:
4921:
4915:
4913:
4909:
4908:
4906:
4905:
4900:
4895:
4890:
4885:
4880:
4875:
4870:
4865:
4860:
4855:
4849:
4847:
4843:
4842:
4840:
4839:
4834:
4829:
4824:
4819:
4814:
4809:
4804:
4799:
4794:
4789:
4784:
4779:
4774:
4769:
4764:
4759:
4754:
4749:
4744:
4738:
4736:
4732:
4731:
4729:
4728:
4723:
4718:
4713:
4708:
4703:
4697:
4695:
4691:
4690:
4688:
4687:
4682:
4677:
4672:
4666:
4661:
4655:
4650:
4645:
4640:
4635:
4629:
4624:
4619:
4613:
4608:
4603:
4598:
4593:
4587:
4585:
4581:
4580:
4578:
4577:
4572:
4567:
4562:
4557:
4550:
4548:
4544:
4543:
4541:
4540:
4535:
4530:
4528:Command Prompt
4525:
4519:
4516:
4515:
4512:shell builtins
4503:
4501:
4500:
4493:
4486:
4478:
4469:
4468:
4466:
4465:
4454:
4442:
4439:
4438:
4436:
4435:
4430:
4425:
4420:
4415:
4409:
4407:
4399:
4398:
4395:
4394:
4392:
4391:
4386:
4381:
4376:
4371:
4366:
4361:
4356:
4351:
4346:
4341:
4336:
4331:
4326:
4321:
4316:
4311:
4306:
4300:
4298:
4294:
4293:
4291:
4290:
4285:
4280:
4275:
4270:
4268:Steps Recorder
4265:
4260:
4255:
4250:
4245:
4240:
4235:
4230:
4225:
4220:
4215:
4210:
4205:
4200:
4195:
4190:
4185:
4180:
4175:
4170:
4165:
4160:
4155:
4150:
4145:
4140:
4135:
4130:
4125:
4120:
4115:
4110:
4105:
4100:
4095:
4090:
4085:
4080:
4075:
4069:
4067:
4063:
4062:
4060:
4059:
4052:
4045:
4038:
4031:
4024:
4017:
4010:
4003:
3996:
3988:
3986:
3979:
3975:
3974:
3972:
3971:
3964:
3956:
3954:
3948:
3947:
3945:
3944:
3939:
3934:
3929:
3924:
3919:
3914:
3909:
3904:
3903:
3902:
3897:
3895:OLE Automation
3892:
3887:
3882:
3877:
3872:
3862:
3861:
3860:
3855:
3850:
3839:
3837:
3831:
3830:
3828:
3827:
3822:
3817:
3811:
3809:
3805:
3804:
3802:
3801:
3796:
3791:
3786:
3781:
3776:
3771:
3766:
3761:
3756:
3751:
3746:
3741:
3735:
3733:
3729:
3728:
3726:
3725:
3720:
3715:
3710:
3705:
3700:
3695:
3690:
3685:
3680:
3675:
3670:
3665:
3663:Object Manager
3660:
3655:
3650:
3645:
3640:
3635:
3630:
3625:
3623:Imaging Format
3620:
3615:
3610:
3605:
3600:
3599:
3598:
3593:
3583:
3578:
3573:
3568:
3562:
3560:
3554:
3553:
3551:
3550:
3545:
3540:
3535:
3530:
3525:
3520:
3515:
3510:
3505:
3500:
3495:
3490:
3485:
3480:
3475:
3470:
3465:
3460:
3455:
3450:
3445:
3440:
3435:
3429:
3427:
3421:
3420:
3418:
3417:
3412:
3407:
3406:
3405:
3400:
3395:
3390:
3385:
3380:
3370:
3365:
3360:
3355:
3350:
3344:
3342:
3336:
3335:
3333:
3332:
3327:
3322:
3320:Task Scheduler
3317:
3312:
3307:
3302:
3297:
3291:
3289:
3283:
3282:
3280:
3279:
3274:
3269:
3264:
3259:
3254:
3253:
3252:
3250:Special folder
3247:
3242:
3237:
3232:
3222:
3217:
3212:
3207:
3202:
3197:
3191:
3189:
3183:
3182:
3180:
3179:
3174:
3169:
3164:
3162:Voice Recorder
3159:
3154:
3149:
3144:
3139:
3134:
3129:
3124:
3119:
3114:
3109:
3104:
3099:
3094:
3089:
3084:
3079:
3074:
3069:
3064:
3059:
3054:
3049:
3048:
3047:
3037:
3032:
3027:
3022:
3017:
3012:
3007:
3002:
2997:
2992:
2987:
2982:
2977:
2972:
2967:
2962:
2956:
2954:
2948:
2947:
2945:
2944:
2939:
2934:
2933:
2932:
2925:Windows Update
2922:
2917:
2912:
2907:
2902:
2897:
2895:System Restore
2892:
2887:
2882:
2877:
2872:
2867:
2862:
2857:
2852:
2847:
2842:
2837:
2832:
2827:
2822:
2817:
2812:
2807:
2805:Device Manager
2802:
2797:
2795:Command Prompt
2792:
2786:
2784:
2778:
2777:
2775:
2774:
2769:
2764:
2763:
2762:
2757:
2749:
2743:
2740:
2739:
2734:
2732:
2731:
2724:
2717:
2709:
2703:
2702:
2697:
2690:
2689:External links
2687:
2685:
2684:
2658:
2626:
2604:
2582:
2560:
2538:
2516:
2490:
2457:
2431:
2411:
2385:
2355:
2329:
2303:
2278:
2252:
2226:
2196:
2175:
2129:
2102:
2070:
2055:
2037:
2022:
1999:
1977:
1966:. July 2, 2012
1945:
1912:
1886:
1860:
1834:
1808:
1782:
1756:
1730:
1700:
1672:
1647:
1621:
1586:
1575:on May 2, 2016
1549:
1517:
1484:
1452:
1421:
1410:. June 1, 2017
1389:
1357:
1325:
1299:
1272:
1249:
1223:
1197:
1171:
1141:
1108:
1080:
1049:
1014:
974:
945:
916:
880:
878:
875:
874:
873:
868:
863:
858:
853:
846:
843:
794:
793:Other concerns
791:
765:encryption key
753:Niels Ferguson
749:UK Home Office
721:
718:
714:
713:
706:
699:
648:
645:
643:
640:
571:logical volume
566:
563:
562:
561:
558:
555:
552:
549:
546:
541:recovery key:
535:
534:
528:
518:
490:
487:
435:
432:
416:manage-bde.wsf
389:manage-bde.wsf
378:
377:
372:
368:
367:
359:
353:
352:
347:
341:
340:
335:
329:
328:
315:
311:
310:
305:
293:
290:
289:
288:
282:
276:
270:
267:
257:
219:
216:
159:
158:
125:
121:
120:
115:
109:
108:
103:
97:
96:
83:
79:
78:
73:
67:
66:
63:
59:
58:
52:
44:
43:
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
5667:
5656:
5653:
5651:
5648:
5646:
5643:
5641:
5640:Windows Vista
5638:
5636:
5633:
5631:
5628:
5626:
5623:
5621:
5618:
5616:
5613:
5611:
5608:
5607:
5605:
5590:
5587:
5585:
5582:
5580:
5577:
5576:
5573:
5567:
5564:
5562:
5559:
5557:
5554:
5552:
5549:
5547:
5544:
5542:
5539:
5537:
5534:
5532:
5529:
5527:
5524:
5522:
5519:
5517:
5514:
5512:
5509:
5508:
5506:
5504:Miscellaneous
5502:
5496:
5493:
5491:
5488:
5486:
5483:
5482:
5480:
5478:
5474:
5468:
5465:
5463:
5460:
5458:
5455:
5453:
5450:
5448:
5445:
5444:
5442:
5438:
5432:
5429:
5427:
5424:
5422:
5419:
5417:
5414:
5412:
5409:
5407:
5404:
5402:
5399:
5397:
5394:
5392:
5389:
5387:
5384:
5382:
5379:
5377:
5374:
5372:
5369:
5367:
5364:
5362:
5359:
5357:
5354:
5352:
5349:
5347:
5344:
5342:
5339:
5337:
5334:
5332:
5331:eventtriggers
5329:
5327:
5324:
5322:
5319:
5317:
5314:
5312:
5309:
5308:
5306:
5302:
5296:
5293:
5291:
5288:
5286:
5283:
5281:
5278:
5276:
5273:
5271:
5268:
5266:
5263:
5261:
5258:
5256:
5253:
5251:
5248:
5246:
5243:
5241:
5238:
5236:
5233:
5231:
5228:
5226:
5223:
5221:
5218:
5216:
5213:
5211:
5208:
5206:
5203:
5201:
5198:
5196:
5193:
5191:
5188:
5186:
5183:
5181:
5178:
5176:
5173:
5171:
5168:
5167:
5165:
5161:
5155:
5152:
5150:
5147:
5145:
5142:
5140:
5137:
5135:
5132:
5130:
5127:
5125:
5122:
5120:
5117:
5115:
5112:
5110:
5107:
5105:
5102:
5100:
5097:
5095:
5092:
5090:
5087:
5086:
5084:
5082:
5078:
5072:
5069:
5067:
5064:
5062:
5059:
5057:
5054:
5052:
5049:
5047:
5044:
5042:
5039:
5037:
5034:
5033:
5031:
5029:File contents
5027:
5021:
5018:
5016:
5013:
5011:
5008:
5006:
5003:
5001:
4998:
4996:
4993:
4991:
4988:
4986:
4983:
4981:
4978:
4976:
4973:
4971:
4968:
4966:
4963:
4961:
4958:
4956:
4953:
4952:
4950:
4946:
4940:
4937:
4935:
4932:
4930:
4927:
4925:
4922:
4920:
4917:
4916:
4914:
4910:
4904:
4901:
4899:
4896:
4894:
4891:
4889:
4886:
4884:
4881:
4879:
4876:
4874:
4871:
4869:
4866:
4864:
4861:
4859:
4856:
4854:
4851:
4850:
4848:
4844:
4838:
4835:
4833:
4830:
4828:
4825:
4823:
4820:
4818:
4815:
4813:
4810:
4808:
4805:
4803:
4800:
4798:
4795:
4793:
4790:
4788:
4785:
4783:
4780:
4778:
4775:
4773:
4770:
4768:
4765:
4763:
4760:
4758:
4755:
4753:
4750:
4748:
4745:
4743:
4740:
4739:
4737:
4733:
4727:
4724:
4722:
4719:
4717:
4714:
4712:
4709:
4707:
4704:
4702:
4699:
4698:
4696:
4692:
4686:
4683:
4681:
4678:
4676:
4673:
4670:
4667:
4665:
4662:
4659:
4656:
4654:
4651:
4649:
4646:
4644:
4641:
4639:
4636:
4633:
4630:
4628:
4625:
4623:
4620:
4617:
4614:
4612:
4609:
4607:
4604:
4602:
4599:
4597:
4594:
4592:
4589:
4588:
4586:
4582:
4576:
4573:
4571:
4568:
4566:
4563:
4561:
4558:
4555:
4552:
4551:
4549:
4545:
4539:
4536:
4534:
4531:
4529:
4526:
4524:
4521:
4520:
4517:
4513:
4510:programs and
4509:
4506:
4499:
4494:
4492:
4487:
4485:
4480:
4479:
4476:
4464:
4455:
4453:
4444:
4443:
4440:
4434:
4431:
4429:
4426:
4424:
4421:
4419:
4416:
4414:
4411:
4410:
4408:
4406:
4400:
4390:
4387:
4385:
4384:Windows To Go
4382:
4380:
4377:
4375:
4372:
4370:
4367:
4365:
4362:
4360:
4357:
4355:
4352:
4350:
4347:
4345:
4342:
4340:
4337:
4335:
4332:
4330:
4327:
4325:
4322:
4320:
4317:
4315:
4312:
4310:
4307:
4305:
4302:
4301:
4299:
4295:
4289:
4286:
4284:
4281:
4279:
4276:
4274:
4271:
4269:
4266:
4264:
4261:
4259:
4256:
4254:
4253:Photo Gallery
4251:
4249:
4246:
4244:
4241:
4239:
4236:
4234:
4231:
4229:
4226:
4224:
4221:
4219:
4216:
4214:
4211:
4209:
4206:
4204:
4201:
4199:
4198:Meeting Space
4196:
4194:
4191:
4189:
4186:
4184:
4181:
4179:
4176:
4174:
4171:
4169:
4168:HyperTerminal
4166:
4164:
4161:
4159:
4156:
4154:
4151:
4149:
4146:
4144:
4141:
4139:
4138:Easy Transfer
4136:
4134:
4131:
4129:
4126:
4124:
4121:
4119:
4116:
4114:
4111:
4109:
4106:
4104:
4101:
4099:
4096:
4094:
4091:
4089:
4086:
4084:
4081:
4079:
4076:
4074:
4071:
4070:
4068:
4064:
4058:
4057:
4053:
4051:
4050:
4046:
4044:
4043:
4039:
4037:
4036:
4032:
4030:
4029:
4025:
4023:
4022:
4018:
4016:
4015:
4011:
4009:
4008:
4004:
4002:
4001:
3997:
3995:
3994:
3990:
3989:
3987:
3983:
3980:
3976:
3970:
3969:
3965:
3963:
3962:
3958:
3957:
3955:
3953:
3949:
3943:
3940:
3938:
3935:
3933:
3930:
3928:
3925:
3923:
3920:
3918:
3915:
3913:
3910:
3908:
3905:
3901:
3898:
3896:
3893:
3891:
3888:
3886:
3883:
3881:
3878:
3876:
3873:
3871:
3868:
3867:
3866:
3863:
3859:
3856:
3854:
3851:
3849:
3846:
3845:
3844:
3841:
3840:
3838:
3836:
3832:
3826:
3823:
3821:
3818:
3816:
3813:
3812:
3810:
3808:Compatibility
3806:
3800:
3797:
3795:
3792:
3790:
3787:
3785:
3782:
3780:
3777:
3775:
3772:
3770:
3767:
3765:
3762:
3760:
3757:
3755:
3752:
3750:
3747:
3745:
3742:
3740:
3737:
3736:
3734:
3730:
3724:
3721:
3719:
3716:
3714:
3711:
3709:
3706:
3704:
3701:
3699:
3696:
3694:
3691:
3689:
3686:
3684:
3681:
3679:
3676:
3674:
3671:
3669:
3666:
3664:
3661:
3659:
3656:
3654:
3651:
3649:
3646:
3644:
3641:
3639:
3636:
3634:
3633:Library files
3631:
3629:
3626:
3624:
3621:
3619:
3616:
3614:
3611:
3609:
3606:
3604:
3601:
3597:
3594:
3592:
3589:
3588:
3587:
3584:
3582:
3579:
3577:
3574:
3572:
3569:
3567:
3564:
3563:
3561:
3559:
3555:
3549:
3546:
3544:
3541:
3539:
3536:
3534:
3531:
3529:
3526:
3524:
3521:
3519:
3516:
3514:
3511:
3509:
3506:
3504:
3501:
3499:
3496:
3494:
3491:
3489:
3486:
3484:
3481:
3479:
3476:
3474:
3471:
3469:
3466:
3464:
3461:
3459:
3456:
3454:
3451:
3449:
3446:
3444:
3441:
3439:
3436:
3434:
3431:
3430:
3428:
3426:
3422:
3416:
3413:
3411:
3408:
3404:
3401:
3399:
3396:
3394:
3393:Reparse point
3391:
3389:
3386:
3384:
3381:
3379:
3376:
3375:
3374:
3371:
3369:
3366:
3364:
3361:
3359:
3356:
3354:
3351:
3349:
3346:
3345:
3343:
3341:
3337:
3331:
3328:
3326:
3323:
3321:
3318:
3316:
3313:
3311:
3308:
3306:
3303:
3301:
3298:
3296:
3293:
3292:
3290:
3288:
3284:
3278:
3275:
3273:
3270:
3268:
3265:
3263:
3260:
3258:
3255:
3251:
3248:
3246:
3243:
3241:
3238:
3236:
3233:
3231:
3228:
3227:
3226:
3223:
3221:
3218:
3216:
3213:
3211:
3208:
3206:
3203:
3201:
3198:
3196:
3195:Action Center
3193:
3192:
3190:
3188:
3184:
3178:
3175:
3173:
3170:
3168:
3165:
3163:
3160:
3158:
3155:
3153:
3150:
3148:
3145:
3143:
3140:
3138:
3135:
3133:
3130:
3128:
3125:
3123:
3122:Snipping Tool
3120:
3118:
3115:
3113:
3110:
3108:
3105:
3103:
3100:
3098:
3095:
3093:
3090:
3088:
3085:
3083:
3080:
3078:
3075:
3073:
3070:
3068:
3065:
3063:
3060:
3058:
3055:
3053:
3050:
3046:
3043:
3042:
3041:
3038:
3036:
3033:
3031:
3028:
3026:
3023:
3021:
3018:
3016:
3013:
3011:
3008:
3006:
3003:
3001:
2998:
2996:
2993:
2991:
2988:
2986:
2983:
2981:
2980:Character Map
2978:
2976:
2973:
2971:
2968:
2966:
2963:
2961:
2958:
2957:
2955:
2953:
2949:
2943:
2940:
2938:
2935:
2931:
2928:
2927:
2926:
2923:
2921:
2918:
2916:
2913:
2911:
2908:
2906:
2903:
2901:
2898:
2896:
2893:
2891:
2888:
2886:
2883:
2881:
2878:
2876:
2873:
2871:
2868:
2866:
2863:
2861:
2858:
2856:
2853:
2851:
2848:
2846:
2843:
2841:
2838:
2836:
2833:
2831:
2828:
2826:
2823:
2821:
2818:
2816:
2813:
2811:
2808:
2806:
2803:
2801:
2800:Control Panel
2798:
2796:
2793:
2791:
2790:App Installer
2788:
2787:
2785:
2779:
2773:
2770:
2768:
2765:
2761:
2758:
2756:
2753:
2752:
2751:Architecture
2750:
2748:
2745:
2744:
2741:
2737:
2730:
2725:
2723:
2718:
2716:
2711:
2710:
2707:
2701:
2698:
2696:
2693:
2692:
2688:
2673:
2669:
2662:
2659:
2647:
2643:
2642:
2637:
2630:
2627:
2614:
2608:
2605:
2592:
2586:
2583:
2570:
2564:
2561:
2548:
2542:
2539:
2526:
2520:
2517:
2505:
2504:The Intercept
2501:
2494:
2491:
2475:
2468:
2461:
2458:
2445:
2441:
2435:
2432:
2428:. DevConf CZ.
2424:
2423:
2415:
2412:
2400:
2396:
2389:
2386:
2373:
2369:
2362:
2360:
2356:
2344:
2340:
2333:
2330:
2317:
2313:
2307:
2304:
2292:
2288:
2282:
2279:
2267:
2263:
2256:
2253:
2240:
2236:
2230:
2227:
2214:
2210:
2206:
2200:
2197:
2185:
2179:
2176:
2164:
2157:
2156:
2151:
2147:
2143:
2136:
2134:
2130:
2117:
2113:
2106:
2103:
2091:
2087:
2086:
2081:
2074:
2071:
2066:
2062:
2058:
2052:
2048:
2041:
2038:
2033:
2029:
2025:
2019:
2015:
2008:
2006:
2004:
2000:
1987:
1981:
1978:
1965:
1961:
1960:
1955:
1949:
1946:
1933:
1932:
1927:
1921:
1919:
1917:
1913:
1900:
1896:
1890:
1887:
1874:
1870:
1864:
1861:
1848:
1844:
1838:
1835:
1822:
1818:
1812:
1809:
1796:
1792:
1786:
1783:
1770:
1766:
1760:
1757:
1745:
1741:
1734:
1731:
1718:
1714:
1710:
1704:
1701:
1689:
1688:
1683:
1676:
1673:
1661:
1657:
1651:
1648:
1635:
1631:
1625:
1622:
1609:
1605:
1601:
1597:
1590:
1587:
1574:
1570:
1566:
1562:
1556:
1554:
1550:
1538:
1534:
1533:
1528:
1521:
1518:
1505:
1501:
1497:
1491:
1489:
1485:
1472:
1468:
1467:
1462:
1456:
1453:
1441:
1437:
1436:
1431:
1425:
1422:
1409:
1405:
1404:
1399:
1393:
1390:
1377:
1373:
1372:
1367:
1361:
1358:
1345:
1341:
1340:
1335:
1329:
1326:
1313:
1309:
1303:
1300:
1287:
1283:
1276:
1273:
1260:
1253:
1250:
1237:
1233:
1227:
1224:
1211:
1207:
1201:
1198:
1185:
1181:
1175:
1172:
1159:
1155:
1151:
1145:
1142:
1129:
1125:
1121:
1115:
1113:
1109:
1094:
1090:
1084:
1081:
1066:
1062:
1056:
1054:
1050:
1037:
1033:
1029:
1025:
1018:
1015:
999:
995:
991:
987:
986:Biddle, Peter
981:
979:
975:
959:
952:
950:
946:
933:
929:
923:
921:
917:
905:
901:
900:
895:
888:
886:
882:
876:
872:
869:
867:
864:
862:
859:
857:
854:
852:
849:
848:
844:
842:
840:
836:
832:
828:
823:
821:
817:
813:
812:Thunderbolt 3
809:
805:
801:
792:
790:
788:
783:
781:
777:
773:
768:
766:
762:
758:
754:
750:
746:
742:
737:
735:
731:
727:
726:public domain
717:
711:
707:
704:
700:
697:
693:
689:
685:
681:
678:
674:
670:
666:
665:
664:
662:
658:
654:
646:
641:
639:
637:
633:
629:
625:
620:
616:
614:
610:
607:
601:
599:
598:bootstrapping
595:
591:
587:
583:
578:
576:
572:
564:
560:Password only
559:
556:
554:TPM + USB Key
553:
550:
547:
544:
543:
542:
540:
532:
529:
526:
522:
519:
516:
512:
508:
503:
499:
496:
495:
494:
488:
486:
482:
480:
475:
473:
469:
465:
460:
456:
452:
448:
444:
440:
433:
431:
429:
428:Windows To Go
425:
419:
409:
405:
401:
397:
392:
385:
376:
373:
369:
366:
363:
360:
358:
354:
351:
348:
346:
342:
339:
336:
334:
330:
316:
312:
309:
306:
304:
300:
291:
287:
283:
281:
277:
274:
271:
268:
266:
262:
258:
256:
252:
251:Windows Vista
248:
244:
241:
240:
239:
236:
234:
230:
225:
217:
215:
213:
209:
205:
201:
197:
193:
189:
185:
181:
177:
176:Windows Vista
173:
169:
165:
155:
148:
126:
122:
119:
116:
114:
110:
107:
104:
102:
98:
84:
80:
77:
74:
72:
68:
64:
60:
56:
50:
45:
41:
36:
30:
19:
4806:
4508:command-line
4418:File Manager
4258:Photo Viewer
4193:Media Center
4153:Groove Music
4083:Address Book
4054:
4047:
4040:
4035:Purble Place
4033:
4026:
4019:
4012:
4005:
4000:Chess Titans
3998:
3991:
3978:Discontinued
3966:
3959:
3748:
3658:Ntoskrnl.exe
3566:Boot Manager
3558:Architecture
3448:Group Policy
3340:File systems
3240:Saved search
3147:Sticky Notes
3112:Quick Assist
3040:Media Player
3010:Feedback Hub
3005:Fax and Scan
2900:Task Manager
2830:Event Viewer
2810:Disk Cleanup
2675:. Retrieved
2671:
2661:
2649:. Retrieved
2641:Ars Technica
2639:
2629:
2617:. Retrieved
2607:
2595:. Retrieved
2585:
2573:. Retrieved
2563:
2551:. Retrieved
2541:
2529:. Retrieved
2519:
2507:. Retrieved
2503:
2493:
2481:. Retrieved
2474:the original
2460:
2448:. Retrieved
2443:
2434:
2421:
2414:
2402:. Retrieved
2398:
2388:
2376:. Retrieved
2371:
2346:. Retrieved
2332:
2320:. Retrieved
2315:
2306:
2294:. Retrieved
2290:
2281:
2269:. Retrieved
2265:
2255:
2243:. Retrieved
2238:
2229:
2217:. Retrieved
2208:
2199:
2187:. Retrieved
2178:
2166:. Retrieved
2154:
2120:. Retrieved
2115:
2105:
2093:. Retrieved
2085:TechRepublic
2083:
2073:
2046:
2040:
2013:
1990:. Retrieved
1980:
1968:. Retrieved
1957:
1948:
1936:. Retrieved
1929:
1903:. Retrieved
1899:MSDN Library
1898:
1889:
1877:. Retrieved
1873:MSDN Library
1872:
1863:
1851:. Retrieved
1847:MSDN Library
1846:
1837:
1825:. Retrieved
1821:MSDN Library
1820:
1811:
1799:. Retrieved
1795:MSDN Library
1794:
1785:
1773:. Retrieved
1769:MSDN Library
1768:
1759:
1747:. Retrieved
1743:
1733:
1721:. Retrieved
1717:the original
1712:
1703:
1691:. Retrieved
1685:
1675:
1663:. Retrieved
1659:
1650:
1638:. Retrieved
1633:
1624:
1612:. Retrieved
1608:the original
1604:Penton Media
1599:
1589:
1577:. Retrieved
1573:the original
1564:
1540:. Retrieved
1532:Ars Technica
1530:
1520:
1508:. Retrieved
1499:
1475:. Retrieved
1464:
1455:
1443:. Retrieved
1433:
1424:
1412:. Retrieved
1401:
1392:
1380:. Retrieved
1369:
1360:
1348:. Retrieved
1337:
1328:
1316:. Retrieved
1312:the original
1302:
1290:. Retrieved
1285:
1275:
1263:. Retrieved
1252:
1240:. Retrieved
1235:
1226:
1214:. Retrieved
1209:
1200:
1188:. Retrieved
1183:
1174:
1162:. Retrieved
1158:the original
1153:
1144:
1132:. Retrieved
1123:
1099:. Retrieved
1083:
1071:. Retrieved
1040:. Retrieved
1036:the original
1027:
1017:
1005:. Retrieved
998:the original
965:. Retrieved
936:. Retrieved
931:
907:. Retrieved
897:
824:
796:
784:
780:cryptosystem
769:
738:
723:
715:
650:
621:
617:
611:
602:
594:drive letter
579:
568:
536:
531:USB Key Mode
530:
527:or password.
520:
497:
492:
483:
476:
446:
437:
420:
393:
381:
303:Developer(s)
249:editions of
237:
221:
163:
162:
71:Developer(s)
29:
5356:pnpunattend
5326:eventcreate
5321:driverquery
5280:ssh-keyscan
4523:COMMAND.COM
4433:Minesweeper
4402:Spun off to
4223:MSN Dial-up
4218:Movie Maker
4123:Diagnostics
4073:ActiveMovie
3815:COMMAND.COM
3693:Shadow Copy
3548:Server Core
3388:Mount Point
3315:Shadow Copy
2910:Windows Ink
2245:December 2,
2239:Dolos Group
2118:. Microsoft
1430:"BitLocker"
1288:. Microsoft
1242:December 2,
1238:. Microsoft
1212:. Microsoft
963:. Microsoft
827:public keys
820:PCI Express
816:PCI Express
808:DMA attacks
730:proprietary
632:boot sector
362:Proprietary
206:or 256-bit
182:for entire
62:Other names
5625:Windows 10
5620:Windows 11
5604:Categories
5386:systeminfo
5275:ssh-keygen
5163:Networking
4807:manage-bde
4777:diskshadow
4413:DVD Player
4228:NetMeeting
4128:DriveSpace
3993:3D Pinball
3493:SharePoint
3257:Start menu
3102:Phone Link
2965:Calculator
2920:PowerShell
2781:Management
2646:Condé Nast
2613:"PCILeech"
2569:"PCILeech"
2161:(Thesis).
1537:Condé Nast
877:References
839:smartcards
787:cryptsetup
696:sleep mode
466:(formerly
443:Windows RT
412:manage-bde
396:Windows XP
375:manage-bde
324:2007-01-30
297:manage-bde
286:Windows 11
280:Windows 10
243:Enterprise
194:(CBC) or "
180:encryption
145:/bitlocker
131:.microsoft
92:2007-01-30
55:Windows 11
5635:Windows 7
5630:Windows 8
5561:tpmvscmgr
5270:ssh-agent
5175:bitsadmin
5081:Scripting
4846:Processes
4694:Archiving
4648:openfiles
4208:Messenger
4203:Messaging
4133:DVD Maker
4103:CD Player
4098:CardSpace
4049:Solitaire
3749:BitLocker
3744:AppLocker
3378:Hard link
3267:Task View
3245:Namespace
3215:ClearType
3035:Messaging
3020:Magnifier
2985:Clipchamp
2960:3D Viewer
2553:March 16,
2213:Microsoft
2065:819519777
2032:851209981
1964:Microsoft
1738:Dansimp.
1569:Microsoft
1504:Microsoft
1471:Microsoft
1440:Microsoft
1408:Microsoft
1376:Microsoft
1344:Microsoft
1318:April 25,
1128:Microsoft
1089:Microsoft
1061:Microsoft
994:Microsoft
904:Microsoft
871:FileVault
761:hard copy
565:Operation
548:TPM + PIN
464:InstantGo
308:Microsoft
275:and later
261:Windows 8
255:Windows 7
164:BitLocker
139:/security
76:Microsoft
33:BitLocker
18:Bitlocker
5536:gpupdate
5531:gpresult
5457:bootsect
5416:wevtutil
5396:typeperf
5391:tracerpt
5381:sxstrace
5366:REAgentC
5351:ntbackup
5316:dispdiag
5311:auditpol
5225:PathPing
5220:nslookup
5195:ipconfig
5190:hostname
5119:forfiles
4970:graftabl
4939:regsvr32
4912:Registry
4903:tasklist
4898:taskkill
4888:shutdown
4883:schtasks
4868:powercfg
4837:vssadmin
4822:scandisk
4812:refsutil
4782:drvspace
4772:diskraid
4767:diskpart
4762:diskcopy
4757:diskcomp
4706:extrac32
4675:robocopy
4660:(rename)
4452:Category
4329:MS-DOS 7
4314:ScanDisk
4233:NTBackup
4113:Contacts
4093:Cardfile
4028:Hold 'Em
4007:FreeCell
3853:VBScript
3764:Defender
3732:Security
3718:Winlogon
3673:Registry
3287:Services
3220:Explorer
3205:AutoPlay
3092:Paint 3D
3077:OneDrive
3067:Narrator
3015:Get Help
2970:Calendar
2865:Settings
2835:IExpress
2677:March 7,
2651:March 7,
2619:June 13,
2597:June 13,
2575:June 13,
2531:March 7,
2509:March 7,
2483:March 7,
2450:March 7,
2404:March 7,
2399:Mashable
2378:March 7,
2348:March 7,
2322:March 7,
2296:March 7,
2271:March 7,
2219:March 7,
2189:March 7,
2168:March 7,
2122:March 7,
2095:March 7,
1992:March 7,
1970:March 7,
1938:March 7,
1905:March 7,
1879:March 7,
1853:March 7,
1827:March 7,
1801:March 7,
1775:March 7,
1749:July 27,
1723:March 7,
1693:March 7,
1665:March 7,
1640:March 7,
1614:March 7,
1579:March 7,
1542:March 7,
1510:March 7,
1477:March 7,
1445:March 7,
1414:March 7,
1382:March 7,
1350:March 7,
1292:March 7,
1216:March 7,
1190:March 7,
1164:March 7,
1134:March 7,
1101:March 7,
1073:March 7,
1042:March 7,
1007:March 7,
988:(2004).
967:March 7,
938:March 7,
909:March 7,
845:See also
835:Infineon
741:backdoor
703:Kerberos
692:Mac OS X
545:TPM only
485:issues.
422:through
292:Features
247:Ultimate
137:/windows
5556:tpmtool
5490:exe2bin
5462:fixboot
5452:bootcfg
5447:bcdedit
5421:winmgmt
5411:wecutil
5406:WBAdmin
5361:pnputil
5346:msiexec
5341:mofcomp
5285:tracert
5265:ssh-add
5235:rpcping
5215:netstat
5200:nbtstat
5154:timeout
5099:cscript
5061:findstr
4747:convert
4716:makecab
4711:extract
4680:takeown
4664:replace
4653:recover
4622:deltree
4618:(erase)
4606:compact
4556:(chdir)
4505:Windows
4428:Mahjong
4349:Interix
4283:WinHelp
4183:Journal
4173:Imaging
4021:InkBall
3907:DirectX
3870:ActiveX
3858:JScript
3571:Console
3543:Hyper-V
3438:Domains
3262:Taskbar
3235:IFilter
3210:AutoRun
3172:WordPad
3167:Weather
3082:OneNote
3072:Notepad
2995:Cortana
2870:Sysprep
2672:Reuters
1959:TechNet
1931:TechNet
1466:TechNet
1435:TechNet
1371:TechNet
1339:TechNet
1265:May 15,
1184:TechNet
1154:TechNet
899:TechNet
804:XTS-AES
763:of the
673:dumping
606:USB key
557:USB Key
387:called
371:Website
357:License
350:Command
322: (
218:History
184:volumes
124:Website
90: (
5551:pentnt
5546:MSCDEX
5495:QBasic
5467:fixmbr
5426:winsat
5336:logman
5250:setspn
5185:getmac
5144:prompt
5104:doskey
5089:choice
5020:whoami
4990:setver
4960:cmdkey
4934:regini
4797:fsutil
4792:format
4752:defrag
4742:chkdsk
4701:expand
4638:mklink
4627:icacls
4601:cipher
4591:attrib
4461:
4450:
4423:Hover!
4297:Others
4278:Travel
4273:Syskey
4056:Tinker
4014:Hearts
3942:WinUSB
3927:WinAPI
3912:Native
3723:WinUSB
3648:MinWin
3425:Server
3225:Search
3137:Sports
3107:Photos
3097:People
2975:Camera
2063:
2053:
2030:
2020:
1032:Penton
661:bootup
539:escrow
515:booted
212:sector
150:
135:/en-us
5526:dpath
5511:break
5485:debug
5401:w32tm
5371:relog
5295:winrs
5290:winrm
5240:route
5210:netsh
5139:pause
5066:print
5046:edlin
5015:where
5005:title
4924:ftype
4919:assoc
4893:start
4873:runas
4817:subst
4802:label
4787:fdisk
4685:xcopy
4669:rmdir
4632:mkdir
4596:cacls
4570:pushd
4389:WinFS
4288:Write
3985:Games
3952:Games
3825:WoW64
3653:NTLDR
3643:LSASS
3576:CSRSS
3383:links
3358:exFAT
3187:Shell
3152:Store
3142:Start
3132:Skype
3087:Paint
3062:Money
2990:Clock
2937:WinRE
2845:Netsh
2783:tools
2772:Games
2477:(PDF)
2470:(PDF)
2426:(PDF)
2266:Petri
2159:(PDF)
1687:ZDNet
1096:(DOC)
1068:(DOC)
1001:(PPT)
961:(PDF)
688:Linux
586:boots
408:exFAT
404:FAT32
400:FAT16
198:(XEX)
166:is a
129:learn
5541:help
5521:dism
5431:wmic
5255:sftp
5230:ping
5180:curl
5134:more
5124:goto
5109:echo
5094:clip
5071:type
5056:find
5041:edit
5036:comp
5000:time
4995:setx
4980:path
4975:mode
4965:date
4955:chcp
4863:kill
4858:exit
4671:(rd)
4643:move
4634:(md)
4611:copy
4575:tree
4565:popd
4463:List
4344:HPFS
4108:Chat
4066:Apps
3968:Surf
3917:.NET
3885:DCOM
3713:WHEA
3708:USER
3698:SMSS
3488:WSUS
3468:MSMQ
3410:ReFS
3373:NTFS
3348:CDFS
3305:CLFS
3300:BITS
3200:Aero
3177:Xbox
3157:Tips
3045:2022
3030:Maps
3025:Mail
3000:Edge
2952:Apps
2747:APIs
2679:2020
2653:2020
2621:2024
2599:2024
2577:2024
2555:2020
2533:2020
2511:2020
2485:2020
2452:2020
2406:2020
2380:2020
2372:CNET
2350:2020
2324:2020
2298:2020
2273:2020
2247:2021
2221:2020
2191:2020
2170:2020
2124:2020
2097:2020
2061:OCLC
2051:ISBN
2028:OCLC
2018:ISBN
1994:2020
1972:2020
1940:2020
1907:2020
1881:2020
1855:2020
1829:2020
1803:2020
1777:2020
1751:2022
1725:2020
1695:2020
1667:2020
1642:2020
1616:2020
1581:2020
1544:2020
1512:2020
1479:2020
1447:2020
1416:2020
1403:MSDN
1384:2020
1352:2020
1320:2017
1294:2020
1267:2024
1244:2021
1218:2020
1192:2020
1166:2020
1136:2020
1103:2020
1075:2020
1044:2020
1009:2020
969:2020
940:2020
911:2020
810:via
690:and
677:DRAM
655:and
653:BIOS
630:and
628:BIOS
582:NTFS
345:Type
263:and
253:and
245:and
133:.com
113:Type
5566:wsl
5516:cls
5376:sfc
5260:ssh
5245:scp
5205:net
5170:arp
5149:rem
5114:for
5010:ver
4985:set
4929:reg
4832:vol
4827:sys
4726:tar
4721:pax
4658:ren
4616:del
4560:dir
4243:Pay
4143:Fax
3890:OLE
3865:COM
3848:WSH
3835:API
3596:DLL
3591:EXE
3503:PWS
3483:IIS
3443:DNS
3415:UDF
3403:EFS
3398:TxF
3368:FAT
3363:IFS
3353:DFS
2942:WMI
2343:BBC
657:MBR
525:PIN
406:or
265:8.1
208:key
204:bit
5606::
5129:if
5051:fc
4878:sc
4853:at
4554:cd
2760:NT
2755:9x
2670:.
2644:.
2638:.
2502:.
2442:.
2397:.
2370:.
2358:^
2341:.
2314:.
2289:.
2264:.
2237:.
2211:.
2207:.
2144:;
2132:^
2114:.
2088:.
2082:.
2059:.
2026:.
2002:^
1962:.
1956:.
1928:.
1915:^
1897:.
1871:.
1845:.
1819:.
1793:.
1767:.
1742:.
1711:.
1684:.
1658:.
1632:.
1602:.
1598:.
1567:.
1563:.
1552:^
1535:.
1529:.
1502:.
1498:.
1487:^
1469:.
1463:.
1438:.
1432:.
1406:.
1400:.
1374:.
1368:.
1342:.
1336:.
1284:.
1234:.
1208:.
1182:.
1152:.
1126:.
1122:.
1111:^
1052:^
1030:.
1026:.
992:.
977:^
948:^
930:.
919:^
902:.
896:.
884:^
736:.
441:,
418:.
402:,
391:.
235:.
214:.
4497:e
4490:t
4483:v
2728:e
2721:t
2714:v
2681:.
2655:.
2623:.
2601:.
2579:.
2557:.
2535:.
2513:.
2487:.
2454:.
2408:.
2382:.
2352:.
2326:.
2300:.
2275:.
2249:.
2223:.
2193:.
2172:.
2126:.
2099:.
2067:.
2034:.
1996:.
1974:.
1942:.
1909:.
1883:.
1857:.
1831:.
1805:.
1779:.
1753:.
1727:.
1697:.
1669:.
1644:.
1618:.
1583:.
1546:.
1514:.
1481:.
1449:.
1418:.
1386:.
1354:.
1322:.
1296:.
1269:.
1246:.
1220:.
1194:.
1168:.
1138:.
1105:.
1077:.
1046:.
1011:.
971:.
942:.
913:.
457:(
326:)
147:/
94:)
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.