473:. In particular, the worm does not spread in Windows Server 2003 because Windows Server 2003 was compiled with the /GS switch, which detected the buffer overflow and shut the RPCSS process down. When infection occurs, the buffer overflow causes the RPC service to crash, leading Windows to display the following message and then automatically reboot, usually after 60 seconds.
238:
The worm was first noticed and started spreading on August 11, 2003. The rate that it spread increased until the number of infections peaked on August 13, 2003. Once a network (such as a company or university) was infected, it spread more quickly within the network because firewalls typically did not
276:
service on the affected operating systems, for which a patch had been released one month earlier in MS03-026 and later in MS03-039. This allowed the worm to spread without users opening attachments simply by spamming itself to large numbers of random IP addresses. Four versions have been detected in
493:
This was the first indication many users had an infection; it often occurred a few minutes after every startup on compromised machines. A simple resolution to stop countdown is to run the "shutdown /a" command, causing some side effects such as an empty (without users) Welcome Screen. The
292:(DDoS) against the site. The damage to Microsoft was minimal as the site targeted was windowsupdate.com, rather than windowsupdate.microsoft.com, to which the former was redirected. Microsoft temporarily shut down the targeted site to minimize potential effects from the worm.
106:
350:
used. (Welchia used the same exploit as MSBlast but had an additional method of propagation that was fixed in this patch. This method was only used after 200,000 RPC DCOM attacks - the form that MSBlast
277:
the wild. These are the most well-known exploits of the original flaw in RPC, but there were in fact another 12 different vulnerabilities that did not see as much media attention.
396:
August 16, 2003: DDoS attack against windowsupdate.com starts. (Largely unsuccessful because that URL is merely a redirect to the real site, windowsupdate.microsoft.com.)
357:
July 16, 2003: Microsoft releases a patch that would protect users from the yet unknown MSBlast. At the same time they also released a bulletin describing the exploit.
1300:
752:
480:
This system is shutting down. Please save all work in progress and log off. Any unsaved changes will be lost. This shutdown was initiated by NT AUTHORITY\SYSTEM
1229:
1491:
1326:
626:
390:
August 13, 2003: Two new worms appear and begin to spread. (Sophos, a variant of MSBlast and W32/RpcSpybot-A, a totally new worm that used the same exploit)
1230:"Blaster Worm-Virus or Its Variants Cause the Computer to Shutdown with an NT AUTHORITY\SYSTEM Error Message Regarding Remote Procedure Call (RPC) Service"
1157:
1421:
1892:
1379:
360:
Around July 16, 2003: White hat hackers create proof-of-concept code verifying that the unpatched systems are vulnerable. The code was not released.
1132:
1026:
724:
953:
516:
1183:
239:
prevent internal machines from using a certain port. Filtering by ISPs and widespread publicity about the worm curbed the spread of
Blaster.
521:
289:
783:
575:
928:
604:
470:
1293:
870:
545:
270:
1503:
1431:
1052:
1763:
1602:
1104:"A tool is available to remove Blaster worm and Nachi worm infections from computers that are running Windows 2000 or Windows XP"
895:
246:, was indicted for creating the B variant of the Blaster worm; he admitted responsibility and was sentenced to an 18-month
2036:
1331:
1321:
1286:
369:
July 25, 2003: xFocus releases information on how to exploit the RPC bug that
Microsoft released the July 16 patch to fix.
1208:
600:
2031:
1395:
288:
if the system date is after August 15 and before
December 31 and after the 15th day of other months, thereby creating a
1158:"Minnesota Man Sentenced to 18 Months in Prison for Creating and Unleashing a Variant of the MS Blaster Computer Worm"
759:
601:"Minnesota Man Sentenced to 18 Months in Prison for Creating and Unleashing a Variant of the MS Blaster Computer Worm"
975:
258:
According to court papers, the original
Blaster was created after security researchers from the Chinese group Xfocus
1241:
1103:
829:
699:
681:
1518:
1498:
1694:
1161:
849:
634:
2026:
1768:
1528:
1794:
1543:
1861:
1856:
1447:
1426:
499:
1851:
1825:
1566:
458:
273:
197:
1136:
1030:
728:
1887:
1400:
425:
January 13, 2004: Microsoft releases a stand-alone tool to remove the MSBlast worm and its variants.
1592:
466:
431:
February 26, 2004: Symantec lowers their risk assessment of the
Welchia worm to "Low" (category 2).
259:
1658:
332:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ windows auto update=msblast.exe
1363:
1078:
489:
Windows must now restart because the Remote
Procedure Call (RPC) Service terminated unexpectedly.
372:
August 1, 2003: The U.S. issues an alert to be on the lookout for malware exploiting the RPC bug.
243:
1684:
1679:
440:
January 28, 2005: The creator of the B variant of MSBlaster is sentenced to 18 months in prison.
1716:
1674:
1576:
1486:
1416:
830:"Buffer Overrun in Windows Kernel Message Handling could Lead to Elevated Privileges (811493)"
343:
419:
August 27, 2003: A potential DDoS attack against HP is discovered in one variant of the worm.
1571:
1452:
325:
285:
225:
1508:
1262:
874:
413:
August 19, 2003: Symantec upgrades their risk assessment of
Welchia to "high" (category 4).
384:
August 11, 2003, evening: Antivirus and security firms issued alerts to run
Windows Update.
1975:
1637:
1617:
1597:
1587:
1237:
805:
266:
2001:
1944:
1908:
1704:
1523:
630:
526:
428:
February 15, 2004: A variant of the related worm
Welchia is discovered on the internet.
50:
2020:
1965:
1747:
1612:
1538:
221:
144:
1939:
1710:
1627:
1622:
1473:
450:
232:
187:
996:
549:
1949:
1913:
1810:
1632:
1561:
1481:
899:
93:
381:
August 11, 2003: Symantec
Antivirus releases a rapid release protection update.
269:
discovered by the Polish security research group Last Stage of Delirium in the
105:
1918:
1533:
1458:
1357:
462:
454:
399:
August 18, 2003: Microsoft issues an alert regarding MSBlast and its variants.
318:
314:
303:
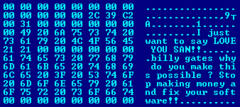
This message gave the worm the alternative name of Lovesan. The second reads:
228:
183:
121:
375:
Sometime prior to August 11, 2003: Other viruses using the RPC exploit exist.
1991:
1970:
511:
403:
295:
The worm's executable, MSBlast.exe, contains two messages. The first reads:
281:
250:
term in January 2005. The author of the original A variant remains unknown.
117:
354:
July 5, 2003: Timestamp for the patch that Microsoft releases on the 16th.
1996:
1923:
1882:
1830:
1742:
1642:
1513:
1111:
363:
July 17, 2003: CERT/CC releases a warning and suggests blocking port 135.
113:
65:
1815:
1727:
1278:
495:
407:
393:
August 15, 2003: The number of infected systems is reported at 423,000.
347:
262:
the original Microsoft patch that allowed for execution of the attack.
853:
660:
387:
August 12, 2003: The number of infected systems is reported at 30,000.
378:
August 11, 2003: Original version of the worm appears on the Internet.
1866:
1607:
1553:
1082:
247:
72:
43:
1073:
1071:
1069:
1820:
1773:
307:
billy gates why do you make this possible ? Stop making money
416:
August 25, 2003: McAfee lowers their risk assessment to "Medium".
1778:
661:"MSBlast W32.Blaster.Worm / LovSan :: removal instructions"
366:
July 21, 2003: CERT/CC suggests also blocking ports 139 and 445.
1282:
896:"The Analysis of LSD's Buffer Overrun in Windows RPC Interface"
434:
March 12, 2004: McAfee lowers their risk assessment to "Low".
242:
In September 2003, Jeffrey Lee Parson, an 18-year-old from
576:"MS03-026: Buffer Overrun in RPC May Allow Code Execution"
346:
that would protect users from an exploit in WebDAV that
328:
entry so that it is launched every time Windows starts:
570:
568:
566:
758:. internet Security Systems, Inc. 2005. Archived from
997:"Virus alert about the Blaster worm and its variants"
449:
Although the worm can only spread on systems running
502:
surfaced, which caused a similar message to appear.
1984:
1958:
1932:
1901:
1875:
1844:
1803:
1787:
1756:
1735:
1726:
1693:
1667:
1651:
1552:
1472:
1440:
1409:
1388:
1372:
1350:
1343:
193:
179:
174:
166:
158:
150:
140:
132:
26:
21:
1021:
1019:
1017:
700:"Microsoft Security Bulletin MS03-039 - Critical"
682:"Microsoft Security Bulletin MS03-026 - Critical"
1184:"Why Blaster did not infect Windows Server 2003"
929:"Blaster worm spreading, experts warn of attack"
922:
920:
918:
916:
116:of the Blaster worm, showing a message left for
475:
850:"Flaw In Microsoft Windows RPC Implementation"
747:
745:
1294:
498:worm had a similar effect. Months later, the
461:service on systems running other versions of
8:
546:"CERT Advisory CA-2003-20: W32/Blaster worm"
483:Time before shutdown: hours:minutes:seconds
437:April 21, 2004: A "B" variant is discovered.
865:
863:
655:
653:
651:
1732:
1347:
1301:
1287:
1279:
719:
717:
715:
713:
104:
321:of Microsoft and the target of the worm.
1380:Sony BMG copy protection rootkit scandal
1053:"'Friendly' Welchia Worm Wreaking Havoc"
627:"FBI arrests 'stupid' Blaster.B suspect"
422:January 1, 2004: Welchia deletes itself.
1110:. Microsoft Corporation. Archived from
954:"New Blaster worm variant on the loose"
537:
1135:. Symantec. 2007-02-13. Archived from
1029:. Symantec. 2017-08-11. Archived from
727:. Symantec. 2003-12-09. Archived from
517:Timeline of computer viruses and worms
18:
548:. CERT/CC. 2003-08-14. Archived from
7:
522:List of convicted computer criminals
324:The worm also creates the following
290:distributed denial of service attack
605:United States Department of Justice
471:Windows XP Professional x64 Edition
342:May 28, 2003: Microsoft releases a
280:The worm was programmed to start a
170:Jeffrey Lee Parson (B variant only)
1079:"Virus Profile: W32/Lovsan.worm.a"
871:"Buffer Overflow in Microsoft RPC"
753:"The Lifecycle of a Vulnerability"
457:, it can cause instability in the
299:I just want to say LOVE YOU SAN!!
14:
265:The worm spreads by exploiting a
224:that spread on computers running
86:Worm.Win32.Blaster (Global Hauri)
36:Worm.Win32.Blaster (Global Hauri)
974:Roberts, Paul F. (2003-08-18).
952:Roberts, Paul F. (2003-08-13).
927:Roberts, Paul F. (2003-08-12).
804:Bransfield, Gene (2003-12-18).
99:Win32.Poza (CA) Blaster (Panda)
1182:Howard, Michael (2004-05-23).
1:
402:August 18, 2003: The related
1711:Kaminsky DNS cache poisoning
1455:(findings published in 2010)
1160:. 2005-01-28. Archived from
1051:Naraine, Ryan (2003-08-19).
976:"Blaster worm attack a bust"
898:. 2003-07-25. Archived from
873:. 2003-08-08. Archived from
852:. 2003-07-16. Archived from
625:Thomson, Iain (2003-09-01).
663:. able2know.org. 2003-08-12
2053:
410:, appears on the internet.
162:Minnesota (B variant only)
16:2003 Windows computer worm
1314:
128:
112:
103:
89:Win32/Msblast (Microsoft)
309:and fix your software!!
136:Lovsan, Lovesan, MSBlast
1432:US military cyberattack
1422:Cyberattacks on Georgia
1396:Cyberattacks on Estonia
1190:. Microsoft Corporation
1003:. Microsoft Corporation
786:. Microsoft Corporation
582:. Microsoft Corporation
1427:Sarah Palin email hack
784:"Worm:Win32/Msblast.A"
491:
334:
311:
301:
1567:Jeanson James Ancheta
330:
313:This is a message to
305:
297:
198:Remote Procedure Call
2037:Hacking in the 2000s
1401:Operation: Bot Roast
1309:Hacking in the 2000s
1133:"W32.Welchia.C.Worm"
1033:on September 3, 2018
254:Creation and effects
235:during August 2003.
39:W32/Blaster (Norman)
2032:Exploit-based worms
1234:HP Consumer Support
1188:Microsoft Developer
1139:on November 3, 2018
704:learn.microsoft.com
686:learn.microsoft.com
467:Windows Server 2003
284:against port 80 of
1364:Operation Firewall
1055:. InternetNews.com
1027:"W32.Welchia.Worm"
806:"The Welchia Worm"
725:"W32.Blaster.Worm"
260:reverse engineered
244:Hopkins, Minnesota
49:W32.Blaster.Worm (
2014:
2013:
2010:
2009:
1492:associated events
1468:
1467:
1417:Project Chanology
1338:
1337:
1108:Microsoft Support
1001:Microsoft Support
811:. pp. 14, 17
580:Microsoft Support
477:System Shutdown:
286:windowsupdate.com
226:operating systems
203:
202:
175:Technical details
124:by the programmer
71:W32/Lovsan.worm (
2044:
1733:
1584:str0ke (milw0rm)
1453:Operation Aurora
1348:
1317:
1316:
1303:
1296:
1289:
1280:
1274:
1273:
1271:
1270:
1259:
1253:
1252:
1250:
1249:
1240:. Archived from
1226:
1220:
1219:
1217:
1216:
1211:. TrendMicro.com
1209:"Worm_MSBlast.A"
1205:
1199:
1198:
1196:
1195:
1179:
1173:
1172:
1170:
1169:
1154:
1148:
1147:
1145:
1144:
1129:
1123:
1122:
1120:
1119:
1100:
1094:
1093:
1091:
1090:
1075:
1064:
1063:
1061:
1060:
1048:
1042:
1041:
1039:
1038:
1023:
1012:
1011:
1009:
1008:
993:
987:
986:
984:
983:
971:
965:
964:
962:
961:
949:
943:
942:
940:
939:
924:
911:
910:
908:
907:
892:
886:
885:
883:
882:
867:
858:
857:
846:
840:
839:
837:
836:
826:
820:
819:
817:
816:
810:
801:
795:
794:
792:
791:
780:
774:
773:
771:
770:
764:
757:
749:
740:
739:
737:
736:
721:
708:
707:
696:
690:
689:
678:
672:
671:
669:
668:
657:
646:
645:
643:
642:
633:. Archived from
622:
616:
615:
613:
612:
597:
591:
590:
588:
587:
572:
561:
560:
558:
557:
542:
108:
19:
2052:
2051:
2047:
2046:
2045:
2043:
2042:
2041:
2027:Windows malware
2017:
2016:
2015:
2006:
1980:
1954:
1928:
1897:
1871:
1840:
1799:
1783:
1764:Anna Kournikova
1752:
1722:
1697:
1695:Vulnerabilities
1689:
1663:
1647:
1638:Dmitry Sklyarov
1618:Albert Gonzalez
1548:
1464:
1436:
1405:
1384:
1368:
1339:
1310:
1307:
1277:
1268:
1266:
1261:
1260:
1256:
1247:
1245:
1228:
1227:
1223:
1214:
1212:
1207:
1206:
1202:
1193:
1191:
1181:
1180:
1176:
1167:
1165:
1156:
1155:
1151:
1142:
1140:
1131:
1130:
1126:
1117:
1115:
1102:
1101:
1097:
1088:
1086:
1077:
1076:
1067:
1058:
1056:
1050:
1049:
1045:
1036:
1034:
1025:
1024:
1015:
1006:
1004:
995:
994:
990:
981:
979:
973:
972:
968:
959:
957:
951:
950:
946:
937:
935:
926:
925:
914:
905:
903:
894:
893:
889:
880:
878:
869:
868:
861:
848:
847:
843:
834:
832:
828:
827:
823:
814:
812:
808:
803:
802:
798:
789:
787:
782:
781:
777:
768:
766:
762:
755:
751:
750:
743:
734:
732:
731:on May 17, 2018
723:
722:
711:
706:. 1 March 2023.
698:
697:
693:
688:. 1 March 2023.
680:
679:
675:
666:
664:
659:
658:
649:
640:
638:
624:
623:
619:
610:
608:
599:
598:
594:
585:
583:
574:
573:
564:
555:
553:
544:
543:
539:
535:
508:
447:
339:
308:
267:buffer overflow
256:
208:(also known as
17:
12:
11:
5:
2050:
2048:
2040:
2039:
2034:
2029:
2019:
2018:
2012:
2011:
2008:
2007:
2005:
2004:
1999:
1994:
1988:
1986:
1982:
1981:
1979:
1978:
1973:
1968:
1962:
1960:
1956:
1955:
1953:
1952:
1950:Black Energy 1
1947:
1942:
1936:
1934:
1930:
1929:
1927:
1926:
1921:
1916:
1911:
1905:
1903:
1899:
1898:
1896:
1895:
1890:
1885:
1879:
1877:
1873:
1872:
1870:
1869:
1864:
1859:
1854:
1848:
1846:
1842:
1841:
1839:
1838:
1833:
1828:
1823:
1818:
1813:
1807:
1805:
1801:
1800:
1798:
1797:
1791:
1789:
1785:
1784:
1782:
1781:
1776:
1771:
1766:
1760:
1758:
1754:
1753:
1751:
1750:
1745:
1739:
1737:
1730:
1724:
1723:
1721:
1720:
1714:
1708:
1705:Shatter attack
1701:
1699:
1691:
1690:
1688:
1687:
1682:
1677:
1671:
1669:
1668:Hacking forums
1665:
1664:
1662:
1661:
1655:
1653:
1649:
1648:
1646:
1645:
1640:
1635:
1630:
1625:
1620:
1615:
1610:
1605:
1600:
1595:
1590:
1585:
1582:
1579:
1574:
1569:
1564:
1558:
1556:
1550:
1549:
1547:
1546:
1541:
1536:
1531:
1526:
1524:PLA Unit 61398
1521:
1516:
1511:
1506:
1501:
1496:
1495:
1494:
1484:
1478:
1476:
1470:
1469:
1466:
1465:
1463:
1462:
1456:
1450:
1448:Operation Troy
1444:
1442:
1438:
1437:
1435:
1434:
1429:
1424:
1419:
1413:
1411:
1407:
1406:
1404:
1403:
1398:
1392:
1390:
1386:
1385:
1383:
1382:
1376:
1374:
1370:
1369:
1367:
1366:
1361:
1354:
1352:
1345:
1341:
1340:
1336:
1335:
1329:
1324:
1315:
1312:
1311:
1308:
1306:
1305:
1298:
1291:
1283:
1276:
1275:
1263:"Blaster Worm"
1254:
1221:
1200:
1174:
1149:
1124:
1095:
1065:
1043:
1013:
988:
966:
944:
912:
887:
859:
856:on 2016-03-04.
841:
821:
796:
775:
741:
709:
691:
673:
647:
617:
592:
562:
536:
534:
531:
530:
529:
527:Zeus (malware)
524:
519:
514:
507:
504:
446:
443:
442:
441:
438:
435:
432:
429:
426:
423:
420:
417:
414:
411:
400:
397:
394:
391:
388:
385:
382:
379:
376:
373:
370:
367:
364:
361:
358:
355:
352:
338:
335:
255:
252:
201:
200:
195:
191:
190:
181:
177:
176:
172:
171:
168:
164:
163:
160:
156:
155:
152:
151:Isolation date
148:
147:
142:
138:
137:
134:
130:
129:
126:
125:
110:
109:
101:
100:
98:
97:
92:WORM_MSBLAST (
90:
87:
77:
76:
69:
55:
54:
47:
40:
37:
28:
27:Technical name
24:
23:
15:
13:
10:
9:
6:
4:
3:
2:
2049:
2038:
2035:
2033:
2030:
2028:
2025:
2024:
2022:
2003:
2000:
1998:
1995:
1993:
1990:
1989:
1987:
1983:
1977:
1974:
1972:
1969:
1967:
1964:
1963:
1961:
1957:
1951:
1948:
1946:
1943:
1941:
1938:
1937:
1935:
1931:
1925:
1922:
1920:
1917:
1915:
1912:
1910:
1907:
1906:
1904:
1900:
1894:
1891:
1889:
1886:
1884:
1881:
1880:
1878:
1874:
1868:
1865:
1863:
1860:
1858:
1855:
1853:
1850:
1849:
1847:
1843:
1837:
1834:
1832:
1829:
1827:
1824:
1822:
1819:
1817:
1814:
1812:
1809:
1808:
1806:
1802:
1796:
1793:
1792:
1790:
1786:
1780:
1777:
1775:
1772:
1770:
1767:
1765:
1762:
1761:
1759:
1755:
1749:
1746:
1744:
1741:
1740:
1738:
1734:
1731:
1729:
1725:
1718:
1715:
1712:
1709:
1706:
1703:
1702:
1700:
1696:
1692:
1686:
1683:
1681:
1678:
1676:
1673:
1672:
1670:
1666:
1660:
1657:
1656:
1654:
1650:
1644:
1641:
1639:
1636:
1634:
1631:
1629:
1626:
1624:
1621:
1619:
1616:
1614:
1611:
1609:
1606:
1604:
1601:
1599:
1596:
1594:
1591:
1589:
1586:
1583:
1580:
1578:
1575:
1573:
1570:
1568:
1565:
1563:
1560:
1559:
1557:
1555:
1551:
1545:
1542:
1540:
1539:World of Hell
1537:
1535:
1532:
1530:
1527:
1525:
1522:
1520:
1517:
1515:
1512:
1510:
1507:
1505:
1502:
1500:
1497:
1493:
1490:
1489:
1488:
1485:
1483:
1480:
1479:
1477:
1475:
1471:
1460:
1457:
1454:
1451:
1449:
1446:
1445:
1443:
1439:
1433:
1430:
1428:
1425:
1423:
1420:
1418:
1415:
1414:
1412:
1408:
1402:
1399:
1397:
1394:
1393:
1391:
1387:
1381:
1378:
1377:
1375:
1371:
1365:
1362:
1359:
1356:
1355:
1353:
1349:
1346:
1342:
1334: →
1333:
1330:
1328:
1325:
1323:
1320:←
1319:
1318:
1313:
1304:
1299:
1297:
1292:
1290:
1285:
1284:
1281:
1264:
1258:
1255:
1244:on 2014-11-10
1243:
1239:
1235:
1231:
1225:
1222:
1210:
1204:
1201:
1189:
1185:
1178:
1175:
1164:on 2014-07-14
1163:
1159:
1153:
1150:
1138:
1134:
1128:
1125:
1114:on 2014-08-06
1113:
1109:
1105:
1099:
1096:
1084:
1080:
1074:
1072:
1070:
1066:
1054:
1047:
1044:
1032:
1028:
1022:
1020:
1018:
1014:
1002:
998:
992:
989:
977:
970:
967:
955:
948:
945:
934:
930:
923:
921:
919:
917:
913:
902:on 2018-02-17
901:
897:
891:
888:
877:on 2014-07-15
876:
872:
866:
864:
860:
855:
851:
845:
842:
831:
825:
822:
807:
800:
797:
785:
779:
776:
765:on 2016-12-24
761:
754:
748:
746:
742:
730:
726:
720:
718:
716:
714:
710:
705:
701:
695:
692:
687:
683:
677:
674:
662:
656:
654:
652:
648:
637:on 2008-11-01
636:
632:
628:
621:
618:
606:
602:
596:
593:
581:
577:
571:
569:
567:
563:
552:on 2014-10-17
551:
547:
541:
538:
532:
528:
525:
523:
520:
518:
515:
513:
510:
509:
505:
503:
501:
497:
490:
487:
484:
481:
478:
474:
472:
468:
464:
460:
456:
452:
444:
439:
436:
433:
430:
427:
424:
421:
418:
415:
412:
409:
405:
401:
398:
395:
392:
389:
386:
383:
380:
377:
374:
371:
368:
365:
362:
359:
356:
353:
349:
345:
341:
340:
336:
333:
329:
327:
322:
320:
316:
310:
304:
300:
296:
293:
291:
287:
283:
278:
275:
272:
268:
263:
261:
253:
251:
249:
245:
240:
236:
234:
230:
227:
223:
222:computer worm
219:
215:
211:
207:
199:
196:
192:
189:
185:
182:
178:
173:
169:
165:
161:
157:
153:
149:
146:
143:
139:
135:
131:
127:
123:
119:
115:
111:
107:
102:
95:
91:
88:
85:
84:
83:
82:
74:
70:
67:
63:
62:
61:
60:
52:
48:
45:
42:W32/Blaster (
41:
38:
35:
34:
33:
29:
25:
20:
1893:Sony rootkit
1835:
1659:Bluehell IRC
1628:Dan Kaminsky
1623:Sven Jaschan
1267:. Retrieved
1265:. Techopedia
1257:
1246:. Retrieved
1242:the original
1233:
1224:
1213:. Retrieved
1203:
1192:. Retrieved
1187:
1177:
1166:. Retrieved
1162:the original
1152:
1141:. Retrieved
1137:the original
1127:
1116:. Retrieved
1112:the original
1107:
1098:
1087:. Retrieved
1085:. 2003-08-11
1057:. Retrieved
1046:
1035:. Retrieved
1031:the original
1005:. Retrieved
1000:
991:
980:. Retrieved
969:
958:. Retrieved
947:
936:. Retrieved
932:
904:. Retrieved
900:the original
890:
879:. Retrieved
875:the original
854:the original
844:
833:. Retrieved
824:
813:. Retrieved
799:
788:. Retrieved
778:
767:. Retrieved
760:the original
733:. Retrieved
729:the original
703:
694:
685:
676:
665:. Retrieved
639:. Retrieved
635:the original
620:
609:. Retrieved
607:. 2005-01-28
595:
584:. Retrieved
579:
554:. Retrieved
550:the original
540:
492:
488:
485:
482:
479:
476:
465:, including
451:Windows 2000
448:
445:Side effects
404:helpful worm
331:
323:
312:
306:
302:
298:
294:
279:
264:
257:
241:
237:
233:Windows 2000
217:
213:
209:
205:
204:
188:Windows 2000
80:
78:
58:
56:
31:
1811:SQL Slammer
1633:Samy Kamkar
1554:Individuals
1519:Level Seven
1482:Ac1db1tch3z
1461:(2008–2010)
1360:(2003–2006)
978:. InfoWorld
956:. InfoWorld
500:Sasser worm
94:Trend Micro
2021:Categories
1698:discovered
1685:darksun.ws
1680:unkn0wn.eu
1588:Lil Hacker
1534:ShadowCrew
1459:WebcamGate
1358:Titan Rain
1269:2018-11-03
1248:2018-11-03
1215:2018-11-03
1194:2018-11-03
1168:2018-11-03
1143:2018-11-03
1118:2018-11-03
1089:2018-11-03
1059:2018-11-03
1037:2018-11-03
1007:2018-11-03
982:2018-11-03
960:2018-11-03
938:2018-11-03
906:2018-11-03
881:2018-11-03
835:2018-11-03
815:2018-11-03
790:2018-11-03
769:2018-11-03
735:2018-11-03
667:2018-11-03
641:2018-11-03
631:vnunet.com
611:2021-02-17
586:2018-11-03
556:2018-11-03
533:References
463:Windows NT
455:Windows XP
319:co-founder
315:Bill Gates
229:Windows XP
194:Ports used
184:Windows XP
122:Bill Gates
1992:Conficker
1971:Agent.btz
1499:Avalanche
1487:Anonymous
1344:Incidents
933:InfoWorld
512:Conficker
486:Message:
282:SYN flood
118:Microsoft
1997:Koobface
1976:Mariposa
1924:Stration
1919:Clickbot
1883:PGPCoder
1831:Graybird
1769:Code Red
1743:ILOVEYOU
1717:sslstrip
1675:ryan1918
1652:Darknets
1643:Stakkato
1581:Digerati
1577:Dshocker
1544:Sandworm
1514:GhostNet
1327:Timeline
506:See also
337:Timeline
326:registry
220:) was a
180:Platform
120:founder
114:Hex dump
66:F-secure
64:Lovsan (
51:Symantec
2002:Waledac
1909:Rustock
1836:Blaster
1816:Welchia
1748:Pikachu
1728:Malware
1598:camZero
496:Welchia
408:Welchia
348:Welchia
218:MSBlast
214:Lovesan
206:Blaster
167:Authors
81:MSBLAST
32:Blaster
22:Blaster
1966:Asprox
1867:Mydoom
1862:Sasser
1857:NetSky
1795:Simile
1719:(2009)
1713:(2008)
1707:(2002)
1613:diabl0
1608:Cyxymu
1603:Coolio
1572:SilenZ
1474:Groups
1083:McAfee
351:used.)
317:, the
248:prison
210:Lovsan
159:Origin
73:McAfee
59:Lovsan
44:Sophos
1940:Storm
1852:Bagle
1826:Gruel
1821:Sobig
1774:Nimda
1562:AKill
1509:0x1fe
1332:2010s
1322:1990s
809:(PDF)
763:(PDF)
756:(PDF)
344:patch
216:, or
133:Alias
1985:2009
1959:2008
1945:ZeuS
1933:2007
1914:ZLOB
1902:2006
1888:Samy
1876:2005
1845:2004
1804:2003
1788:2002
1779:Klez
1757:2001
1736:2000
1593:BadB
1504:GNAA
1441:2009
1410:2008
1389:2007
1373:2005
1351:2004
469:and
271:DCOM
231:and
186:and
154:2004
145:Worm
141:Type
1529:RBN
459:RPC
453:or
274:RPC
79:As
57:As
30:As
2023::
1238:HP
1236:.
1232:.
1186:.
1106:.
1081:.
1068:^
1016:^
999:.
931:.
915:^
862:^
744:^
712:^
702:.
684:.
650:^
629:.
603:.
578:.
565:^
406:,
212:,
1302:e
1295:t
1288:v
1272:.
1251:.
1218:.
1197:.
1171:.
1146:.
1121:.
1092:.
1062:.
1040:.
1010:.
985:.
963:.
941:.
909:.
884:.
838:.
818:.
793:.
772:.
738:.
670:.
644:.
614:.
589:.
559:.
96:)
75:)
68:)
53:)
46:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.