253:
301:
289:
186:
163:
146:
134:
118:
106:
94:
760:.) Reading from and writing to the circular buffer may then be carried out with greater efficiency by means of direct memory access; those accesses which fall beyond the end of the first virtual-memory region will automatically wrap around to the beginning of the underlying buffer. When the read offset is advanced into the second virtual-memory region, both offsets—read and write—are decremented by the length of the underlying buffer.
80:
31:
307:
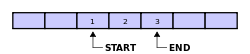
In the beginning the indexes end and start are set to 0. The circular buffer write operation writes an element to the end index position and the end index is incremented to the next buffer position. The circular buffer read operation reads an element from the start index position and the start index
792:(bipartite buffer) is very similar to a circular buffer, except it always returns contiguous blocks which can be variable length. This offers nearly all the efficiency advantages of a circular buffer while maintaining the ability for the buffer to be used in APIs that only accept contiguous blocks.
311:
The start and end indexes alone are not enough to distinguish between buffer full or empty state while also utilizing all buffer slots, but can be if the buffer only has a maximum in-use size of Length - 1. In this case, the buffer is empty if the start and end indexes are equal and full when the
221:
that has fixed maximum size. Should a maximum size be adopted for a queue, then a circular buffer is a completely ideal implementation; all queue operations are constant time. However, expanding a circular buffer requires shifting memory, which is comparatively costly. For arbitrarily expanding
197:
The useful property of a circular buffer is that it does not need to have its elements shuffled around when one is consumed. (If a non-circular buffer were used then it would be necessary to shift all elements when one is consumed.) In other words, the circular buffer is well-suited as a
312:
in-use size is Length - 1. Another solution is to have another integer count that is incremented at a write operation and decremented at a read operation. Then checking for emptiness means testing count equals 0 and checking for fullness means testing count equals Length.
34:
A ring showing, conceptually, a circular buffer. This visually shows that the buffer has no real end and it can loop around the buffer. However, since memory is never physically created as a ring, a linear representation is generally used as is done
241:
family of lossless data compression algorithms operates on the assumption that strings seen more recently in a data stream are more likely to occur soon in the stream. Implementations store the most recent data in a circular buffer.
315:
The following source code is a C implementation together with a minimal test. Function put() puts an item in the buffer, function get() gets an item from the buffer. Both functions take care about the capacity of the buffer :
152:
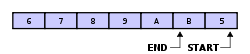
A property of the circular buffer is that when it is full and a subsequent write is performed, then it starts overwriting the oldest data. In the current example, two more elements — A & B — are added and they
83:
A 24-byte keyboard circular buffer. When the write pointer is about to reach the read pointer—because the microprocessor is not responding—the buffer stops recording keystrokes. On some computers a beep would be
795:
Fixed-sized compressed circular buffers use an alternative indexing strategy based on elementary number theory to maintain a fixed-sized compressed representation of the entire data sequence.
997:
941:
1468:
1089:
966:
1144:
771:
Some implementations of the circular buffer use fixed-length elements that are bigger than 8-bit bytes—16-bit integers for audio buffers, 53-byte
128:) logic. In the example, 1 & 2 were the first to enter the circular buffer, they are the first to be removed, leaving 3 inside of the buffer.
1093:
881:
Wireless
Algorithms, Systems, and Applications: 16th International Conference, WASA 2021, Nanjing, China, June 25–27, 2021, Proceedings, Part II
920:
1438:
889:
252:
1377:
989:
229:
In some situations, overwriting circular buffer can be used, e.g. in multimedia. If the buffer is used as the bounded buffer in the
1084:
199:
173:. Whether or not data is overwritten is up to the semantics of the buffer routines or the application using the circular buffer.
100:
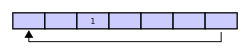
Assume that 1 is written in the center of a circular buffer (the exact starting location is not important in a circular buffer):
1167:
779:, so software reading and writing these values can be faster than software that handles non-contiguous and non-aligned values.
1113:
124:
If two elements are removed, the two oldest values inside of the circular buffer would be removed. Circular buffers use FIFO (
1172:
263:
230:
1018:
180:
3 & 4 (or rather now A & B) but 5 & 6 because 5 & 6 are now the oldest elements, yielding the buffer with:
1137:
233:
then it is probably desired for the producer (e.g., an audio generator) to overwrite old data if the consumer (e.g., the
1251:
1234:
1072:
169:
Alternatively, the routines that manage the buffer could prevent overwriting the data and return an error or raise an
112:
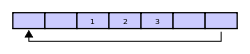
Then assume that two more elements are added to the circular buffer — 2 & 3 — which get put after 1:
1450:
1217:
1212:
772:
1207:
64:
1502:
1246:
1241:
1200:
1130:
300:
288:
1481:
1458:
958:
88:
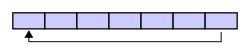
A circular buffer first starts out empty and has a set length. In the diagram below is a 7-element buffer:
1463:
1263:
218:
1389:
1344:
1306:
1100:
1080:
1329:
912:
785:
can be considered a very specialized circular buffer with exactly two large fixed-length elements.
1372:
1357:
1222:
1182:
1047:
295:
This image shows a full buffer with four elements (numbers 1 through 4) having been overwritten:
170:
1291:
1190:
885:
879:
1314:
1039:
782:
757:
207:
40:
756:. (Naturally, the underlying buffer‘s length must then equal some multiple of the system’s
185:
162:
145:
133:
117:
105:
79:
1507:
1334:
1117:
815:
Operating
Systems: Three Easy Pieces [Chapter: Condition Variables, figure 30.13]
93:
1426:
1404:
1229:
1153:
813:
776:
753:
60:
1496:
1399:
1296:
1281:
884:. Lecture Notes in Computer Science. Springer International Publishing. p. 117.
768:
Perhaps the most common version of the circular buffer uses 8-bit bytes as elements.
1051:
67:
as if it were connected end-to-end. This structure lends itself easily to buffering
1110:
990:"mikeash.com: Friday Q&A 2012-02-17: Ring Buffers and Mirrored Memory: Part II"
856:
1068:
1394:
1319:
223:
68:
1382:
1286:
1030:
Gunther, John C. (March 2014). "Algorithm 938: Compressing circular buffers".
833:
234:
30:
1324:
1271:
954:
775:
cells for telecom buffers, etc. Each item is contiguous and has the correct
17:
1421:
1367:
1195:
176:
Finally, if two elements are now removed then what would be returned is
1416:
1362:
1411:
1352:
1105:
1043:
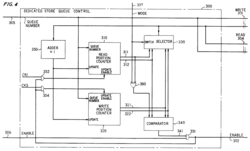
857:"US patent 3979733 Digital data communications system packet switch"
256:
Circular buffer implementation in hardware, US patent 3979733, fig4
206:) buffer while a standard, non-circular buffer is well suited as a
1122:
1433:
749:
238:
71:. There were early circular buffer implementations in hardware.
1126:
217:
Circular buffering makes a good implementation strategy for a
812:
Arpaci-Dusseau, Remzi H.; Arpaci-Dusseau, Andrea C. (2014),
357:// note: only (N - 1) elements can be stored at a given time
283:
This image shows a partially full buffer with Length = 7:
140:
If the buffer has 7 elements, then it is completely full:
764:
Fixed-length-element and contiguous-block circular buffer
748:
A circular-buffer implementation may be optimized by
1449:
1343:
1305:
1262:
1181:
1160:
1019:"The Bip Buffer - The Circular Buffer with a Twist"
752:the underlying buffer to two contiguous regions of
27:
A circular shaped buffer shown while obtaining data
913:"Implementing Circular/Ring Buffer in Embedded C"
834:"Impulswiederholer - Telephone Exchange (video)"
237:) is unable to momentarily keep up. Also, the
1138:
262:A circular buffer can be implemented using a
8:
308:is incremented to the next buffer position.
1145:
1131:
1123:
1032:ACM Transactions on Mathematical Software
911:Chandrasekaran, Siddharth (2014-05-16).
251:
78:
29:
804:
923:from the original on 11 February 2017
7:
963:Open Data Structures (in pseudocode)
1081:Templated Circular Buffer Container
969:from the original on 31 August 2015
878:Liu, Z.; Wu, F.; Das, S.K. (2021).
226:approach may be preferred instead.
959:"ArrayQueue: An Array-Based Queue"
25:
832:Hartl, Johann (17 October 2011).
447:// buffer is full, avoid overflow
299:
287:
184:
161:
144:
132:
116:
104:
92:
1000:from the original on 2019-01-11
63:that uses a single, fixed-size
279:read from buffer index (start)
1:
1469:Directed acyclic word graph
1235:Double-ended priority queue
1073:Portland Pattern Repository
276:write to buffer index (end)
1524:
1090:Synchronized Bounded Queue
855:Fraser, Alexander Gibson.
345:// size of circular buffer
1477:
246:Circular buffer mechanics
231:producer–consumer problem
1201:Retrieval Data Structure
1085:circular_buffer/base.hpp
318:
273:buffer capacity (length)
1482:List of data structures
1459:Binary decision diagram
988:Mike Ash (2012-02-17).
645:// test circular buffer
1464:Directed acyclic graph
1094:sync_bounded_queue.hpp
821:, Arpaci-Dusseau Books
270:buffer start in memory
257:
85:
36:
919:. EmbedJournal Team.
255:
82:
33:
1330:Unrolled linked list
1017:Simon Cooke (2003),
266:and three integers:
1378:Self-balancing tree
1111:Circular queue in C
783:Ping-pong buffering
204:first in, first out
126:first in, first out
1358:Binary search tree
1223:Double-ended queue
1116:2018-10-29 at the
1101:CB in Linux kernel
859:. US States Patent
561:// buffer is empty
258:
212:last in, first out
86:
37:
1490:
1489:
1292:Hashed array tree
1191:Associative array
891:978-3-030-86130-8
16:(Redirected from
1515:
1315:Association list
1147:
1140:
1133:
1124:
1056:
1055:
1027:
1021:
1015:
1009:
1008:
1006:
1005:
985:
979:
978:
976:
974:
951:
945:
942:Circular buffers
939:
933:
932:
930:
928:
908:
902:
901:
899:
898:
875:
869:
868:
866:
864:
852:
846:
845:
843:
841:
829:
823:
822:
820:
809:
739:
736:
733:
730:
727:
724:
721:
718:
715:
712:
709:
706:
703:
700:
697:
694:
691:
688:
685:
682:
679:
676:
673:
670:
667:
664:
661:
658:
655:
652:
649:
646:
643:
640:
637:
634:
631:
628:
625:
622:
619:
616:
613:
610:
607:
604:
601:
598:
595:
592:
589:
586:
583:
580:
577:
574:
571:
568:
565:
562:
559:
556:
553:
550:
547:
544:
541:
538:
535:
532:
529:
526:
523:
520:
517:
514:
511:
508:
505:
502:
499:
496:
493:
490:
487:
484:
481:
478:
475:
472:
469:
466:
463:
460:
457:
454:
451:
448:
445:
442:
439:
436:
433:
430:
427:
424:
421:
418:
415:
412:
409:
406:
403:
400:
397:
394:
391:
388:
385:
382:
379:
376:
373:
370:
367:
364:
361:
358:
355:
352:
349:
346:
343:
340:
337:
334:
331:
328:
325:
322:
303:
291:
188:
165:
148:
136:
120:
108:
96:
41:computer science
21:
1523:
1522:
1518:
1517:
1516:
1514:
1513:
1512:
1503:Computer memory
1493:
1492:
1491:
1486:
1473:
1445:
1339:
1335:XOR linked list
1301:
1277:Circular buffer
1258:
1177:
1156:
1154:Data structures
1151:
1118:Wayback Machine
1065:
1060:
1059:
1044:10.1145/2559995
1029:
1028:
1024:
1016:
1012:
1003:
1001:
987:
986:
982:
972:
970:
953:
952:
948:
940:
936:
926:
924:
910:
909:
905:
896:
894:
892:
877:
876:
872:
862:
860:
854:
853:
849:
839:
837:
831:
830:
826:
818:
811:
810:
806:
801:
766:
746:
741:
740:
737:
734:
731:
728:
725:
722:
719:
716:
713:
710:
707:
704:
701:
698:
695:
692:
689:
686:
683:
680:
677:
674:
671:
668:
665:
662:
659:
656:
653:
650:
647:
644:
641:
638:
635:
632:
629:
626:
623:
620:
617:
614:
611:
608:
605:
602:
599:
596:
593:
590:
587:
584:
581:
578:
575:
572:
569:
566:
563:
560:
557:
554:
551:
548:
545:
542:
539:
536:
533:
530:
527:
524:
521:
518:
515:
512:
509:
506:
503:
500:
497:
494:
491:
488:
485:
482:
479:
476:
473:
470:
467:
464:
461:
458:
455:
452:
449:
446:
443:
440:
437:
434:
431:
428:
425:
422:
419:
416:
413:
410:
407:
404:
401:
398:
395:
392:
389:
386:
383:
380:
377:
374:
371:
368:
365:
362:
359:
356:
353:
350:
347:
344:
341:
338:
335:
332:
329:
326:
324:<stdio.h>
323:
320:
248:
195:
157:the 3 & 4:
77:
45:circular buffer
28:
23:
22:
15:
12:
11:
5:
1521:
1519:
1511:
1510:
1505:
1495:
1494:
1488:
1487:
1485:
1484:
1478:
1475:
1474:
1472:
1471:
1466:
1461:
1455:
1453:
1447:
1446:
1444:
1443:
1442:
1441:
1431:
1430:
1429:
1427:Hilbert R-tree
1424:
1419:
1409:
1408:
1407:
1405:Fibonacci heap
1402:
1397:
1387:
1386:
1385:
1380:
1375:
1373:Red–black tree
1370:
1365:
1355:
1349:
1347:
1341:
1340:
1338:
1337:
1332:
1327:
1322:
1317:
1311:
1309:
1303:
1302:
1300:
1299:
1294:
1289:
1284:
1279:
1274:
1268:
1266:
1260:
1259:
1257:
1256:
1255:
1254:
1249:
1239:
1238:
1237:
1230:Priority queue
1227:
1226:
1225:
1215:
1210:
1205:
1204:
1203:
1198:
1187:
1185:
1179:
1178:
1176:
1175:
1170:
1164:
1162:
1158:
1157:
1152:
1150:
1149:
1142:
1135:
1127:
1121:
1120:
1108:
1103:
1098:
1097:
1096:
1087:
1075:
1069:CircularBuffer
1064:
1063:External links
1061:
1058:
1057:
1022:
1010:
980:
946:
934:
903:
890:
870:
847:
824:
803:
802:
800:
797:
777:data alignment
765:
762:
754:virtual memory
745:
742:
319:
305:
304:
293:
292:
281:
280:
277:
274:
271:
260:
259:
247:
244:
194:
191:
190:
189:
167:
166:
150:
149:
138:
137:
122:
121:
110:
109:
98:
97:
76:
73:
61:data structure
49:circular queue
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
1520:
1509:
1506:
1504:
1501:
1500:
1498:
1483:
1480:
1479:
1476:
1470:
1467:
1465:
1462:
1460:
1457:
1456:
1454:
1452:
1448:
1440:
1437:
1436:
1435:
1432:
1428:
1425:
1423:
1420:
1418:
1415:
1414:
1413:
1410:
1406:
1403:
1401:
1400:Binomial heap
1398:
1396:
1393:
1392:
1391:
1388:
1384:
1381:
1379:
1376:
1374:
1371:
1369:
1366:
1364:
1361:
1360:
1359:
1356:
1354:
1351:
1350:
1348:
1346:
1342:
1336:
1333:
1331:
1328:
1326:
1323:
1321:
1318:
1316:
1313:
1312:
1310:
1308:
1304:
1298:
1297:Sparse matrix
1295:
1293:
1290:
1288:
1285:
1283:
1282:Dynamic array
1280:
1278:
1275:
1273:
1270:
1269:
1267:
1265:
1261:
1253:
1250:
1248:
1245:
1244:
1243:
1240:
1236:
1233:
1232:
1231:
1228:
1224:
1221:
1220:
1219:
1216:
1214:
1211:
1209:
1206:
1202:
1199:
1197:
1194:
1193:
1192:
1189:
1188:
1186:
1184:
1180:
1174:
1171:
1169:
1166:
1165:
1163:
1159:
1155:
1148:
1143:
1141:
1136:
1134:
1129:
1128:
1125:
1119:
1115:
1112:
1109:
1107:
1104:
1102:
1099:
1095:
1091:
1088:
1086:
1082:
1079:
1078:
1076:
1074:
1070:
1067:
1066:
1062:
1053:
1049:
1045:
1041:
1037:
1033:
1026:
1023:
1020:
1014:
1011:
999:
995:
991:
984:
981:
968:
964:
960:
956:
950:
947:
943:
938:
935:
922:
918:
917:Embed Journal
914:
907:
904:
893:
887:
883:
882:
874:
871:
858:
851:
848:
835:
828:
825:
817:
816:
808:
805:
798:
796:
793:
791:
786:
784:
780:
778:
774:
769:
763:
761:
759:
755:
751:
743:
711:"read %d
317:
313:
309:
302:
298:
297:
296:
290:
286:
285:
284:
278:
275:
272:
269:
268:
267:
265:
254:
250:
249:
245:
243:
240:
236:
232:
227:
225:
220:
215:
213:
209:
205:
201:
192:
187:
183:
182:
181:
179:
174:
172:
164:
160:
159:
158:
156:
147:
143:
142:
141:
135:
131:
130:
129:
127:
119:
115:
114:
113:
107:
103:
102:
101:
95:
91:
90:
89:
81:
74:
72:
70:
66:
62:
58:
54:
53:cyclic buffer
50:
46:
42:
32:
19:
1276:
1252:Disjoint-set
1035:
1031:
1025:
1013:
1002:. Retrieved
993:
983:
971:. Retrieved
962:
949:
937:
925:. Retrieved
916:
906:
895:. Retrieved
880:
873:
861:. Retrieved
850:
838:. Retrieved
827:
814:
807:
794:
789:
787:
781:
770:
767:
747:
744:Optimization
314:
310:
306:
294:
282:
261:
228:
216:
211:
203:
196:
177:
175:
168:
154:
151:
139:
125:
123:
111:
99:
87:
69:data streams
56:
52:
48:
44:
38:
18:Circular log
1395:Binary heap
1320:Linked list
1038:(2): 1–12.
994:mikeash.com
863:15 December
840:15 December
224:linked list
57:ring buffer
1497:Categories
1383:Splay tree
1287:Hash table
1168:Collection
1004:2019-01-10
973:7 November
955:Morin, Pat
944:kernel.org
897:2023-09-04
799:References
790:bip buffer
235:sound card
222:queues, a
214:) buffer.
1439:Hash tree
1325:Skip list
1272:Bit array
1173:Container
1106:CB in DSP
927:14 August
836:. Youtube
758:page size
552:writeIndx
483:writeIndx
474:writeIndx
417:writeIndx
363:writeIndx
171:exception
155:overwrite
1368:AVL tree
1247:Multiset
1196:Multimap
1183:Abstract
1114:Archived
1052:14682572
998:Archived
967:Archived
921:Archived
600:readIndx
591:readIndx
546:readIndx
438:readIndx
378:readIndx
321:#include
75:Overview
1422:R+ tree
1417:R* tree
1363:AA tree
1077:Boost:
1071:at the
750:mapping
264:pointer
84:played.
1508:Arrays
1451:Graphs
1412:R-tree
1353:B-tree
1307:Linked
1264:Arrays
1050:
888:
729:return
717:"
705:printf
621:return
585:buffer
564:return
504:return
462:buffer
450:return
351:buffer
65:buffer
35:below.
1345:Trees
1218:Queue
1213:Stack
1161:Types
1048:S2CID
819:(PDF)
723:value
699:value
696:&
684:while
675:value
663:while
651:value
579:value
531:value
219:queue
59:is a
1434:Trie
1390:Heap
1208:List
975:2015
929:2017
886:ISBN
865:2021
842:2021
788:The
657:1001
636:main
468:item
402:item
327:enum
239:LZ77
208:LIFO
200:FIFO
193:Uses
43:, a
1242:Set
1092::
1040:doi
773:ATM
690:get
681:));
669:put
648:int
633:int
525:int
519:get
516:int
399:int
393:put
390:int
375:int
360:int
348:int
178:not
55:or
39:In
1499::
1083::
1046:.
1036:40
1034:.
996:.
992:.
965:.
961:.
957:.
915:.
726:);
714:\n
702:))
678:++
639:()
549:==
540:if
435:==
414:((
411:if
342:};
339:10
51:,
47:,
1146:e
1139:t
1132:v
1054:.
1042::
1007:.
977:.
931:.
900:.
867:.
844:.
738:}
735:;
732:0
720:,
708:(
693:(
687:(
672:(
666:(
660:;
654:=
642:{
630:}
627:;
624:1
618:;
615:N
612:%
609:)
606:1
603:+
597:(
594:=
588:;
582:=
576:*
573:}
570:;
567:0
558:{
555:)
543:(
537:{
534:)
528:*
522:(
513:}
510:;
507:1
501:;
498:N
495:%
492:)
489:1
486:+
480:(
477:=
471:;
465:=
459:}
456:;
453:0
444:{
441:)
432:N
429:%
426:)
423:1
420:+
408:{
405:)
396:(
387:;
384:0
381:=
372:;
369:0
366:=
354:;
336:=
333:N
330:{
210:(
202:(
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.