392:
typically lie dormant since they have no way of receiving instructions. To mitigate this problem, a botnet can consist of several servers or channels. If one of the servers or channels becomes disabled, the botnet simply switches to another. It is still possible to detect and disrupt additional botnet servers or channels by sniffing IRC traffic. A botnet adversary can even potentially gain knowledge of the control scheme and imitate the bot herder by issuing commands correctly.
33:
161:
773:
hack into accounts. The idea is to overwhelm sites with tens of thousands of requests from different IPs all over the world, but with each bot only submitting a single request every 10 minutes or so, which can result in more than 5 million attempts per day. In these cases, many tools try to leverage volumetric detection, but automated bot attacks now have ways of circumventing triggers of volumetric detection.
4151:
205:
776:
One of the techniques for detecting these bot attacks is what's known as "signature-based systems" in which the software will attempt to detect patterns in the request packet. However, attacks are constantly evolving, so this may not be a viable option when patterns cannot be discerned from thousands
623:
are one of the most common uses for botnets, in which multiple systems submit as many requests as possible to a single
Internet computer or service, overloading it and preventing it from servicing legitimate requests. An example is an attack on a victim's server. The victim's server is bombarded with
695:
Botnets can be used for many electronic scams. These botnets can be used to distribute malware such as viruses to take control of a regular users computer/software By taking control of someone's personal computer they have unlimited access to their personal information, including passwords and login
657:
is often a consequence of malicious bot activity, according to CHEQ, Ad Fraud 2019, The
Economic Cost of Bad Actors on the Internet. Commercial purposes of bots include influencers using them to boost their supposed popularity, and online publishers using bots to increase the number of clicks an ad
638:
is software which sends information to its creators about a user's activities – typically passwords, credit card numbers and other information that can be sold on the black market. Compromised machines that are located within a corporate network can be worth more to the bot herder, as they can
391:
One problem with using IRC is that each bot client must know the IRC server, port, and channel to be of any use to the botnet. Anti-malware organizations can detect and shut down these servers and channels, effectively halting the botnet attack. If this happens, clients are still infected, but they
383:
IRC networks use simple, low bandwidth communication methods, making them widely used to host botnets. They tend to be relatively simple in construction and have been used with moderate success for coordinating DDoS attacks and spam campaigns while being able to continually switch channels to avoid
239:
until they identify another infected machine. The contacted bot replies with information such as its software version and list of known bots. If one of the bots' version is lower than the other, they will initiate a file transfer to update. This way, each bot grows its list of infected machines and
1635:
Researchers at the
University of California, Santa Barbara took control of a botnet that was six times smaller than expected. In some countries, it is common that users change their IP address a few times in one day. Estimating the size of the botnet by the number of IP addresses is often used by
772:
Detecting automated bot attacks is becoming more difficult each day as newer and more sophisticated generations of bots are getting launched by attackers. For example, an automated attack can deploy a large bot army and apply brute-force methods with highly accurate username and password lists to
719:
Computer security experts have succeeded in destroying or subverting malware command and control networks, by, among other means, seizing servers or getting them cut off from the
Internet, denying access to domains that were due to be used by malware to contact its C&C infrastructure, and, in
343:
Global law enforcement agencies, with the DOJ and FBI, dismantled the 911 S5 botnet, responsible for $ 5.9 billion in theft and various cybercrimes. Chinese national YunHe Wang, charged with operating the botnet, faces up to 65 years in prison. Authorities seized $ 60 million in assets, including
794:
The rise in vulnerable IoT devices has led to an increase in IoT-based botnet attacks. To address this, a novel network-based anomaly detection method for IoT called N-BaIoT was introduced. It captures network behavior snapshots and employs deep autoencoders to identify abnormal traffic from
798:
Additionally, comparing different ways of detecting botnets is really useful for researchers. It helps them see how well each method works compared to others. This kind of comparison is good because it lets researchers evaluate the methods fairly and find ways to make them better.
231:
Newer botnets fully operate over P2P networks. Rather than communicate with a centralized server, P2P bots perform as both a command distribution server and a client which receives commands. This avoids having any single point of failure, which is an issue for centralized botnets.
438:
Disadvantages of using this method are that it uses a considerable amount of bandwidth at large scale, and domains can be quickly seized by government agencies with little effort. If the domains controlling the botnets are not seized, they are also easy targets to compromise with
673:
Self-spreading functionality, to seek for pre-configured command-and-control (CNC) pushed instruction contains targeted devices or network, to aim for more infection, is also spotted in several botnets. Some of the botnets are utilizing this function to automate their
3042:
Taking Down
Botnets: Public and Private Efforts to Disrupt and Dismantle Cybercriminal Networks: Hearing before the Subcommittee on Crime and Terrorism of the Committee on the Judiciary, United States Senate, One Hundred Thirteenth Congress, Second Session, July 15,
777:
of requests. There is also the behavioral approach to thwarting bots, which ultimately tries to distinguish bots from humans. By identifying non-human behavior and recognizing known bot behavior, this process can be applied at the user, browser, and network levels.
195:
and join a channel pre-designated for C&C by the bot herder. The bot herder sends commands to the channel via the IRC server. Each client retrieves the commands and executes them. Clients send messages back to the IRC channel with the results of their actions.
551:
Newer bots can automatically scan their environment and propagate themselves using vulnerabilities and weak passwords. Generally, the more vulnerabilities a bot can scan and propagate through, the more valuable it becomes to a botnet controller community.
184:. Infected clients access a predetermined location and await incoming commands from the server. The bot herder sends commands to the server, which relays them to the clients. Clients execute the commands and report their results back to the bot herder.
567:
program, which may come from an email attachment. This malware will typically install modules that allow the computer to be commanded and controlled by the botnet's operator. After the software is downloaded, it will call home (send a reconnection
472:
towards an IRC server that harbors the bots. While these free DNS services do not themselves host attacks, they provide reference points (often hard-coded into the botnet executable). Removing such services can cripple an entire botnet.
795:
compromised IoT devices. The method was tested by infecting nine IoT devices with Mirai and BASHLITE botnets, showing its ability to accurately and promptly detect attacks originating from compromised IoT devices within a botnet.
2477:
268:. A bot herder creates an IRC channel for infected clients to join. Messages sent to the channel are broadcast to all channel members. The bot herder may set the channel's topic to command the botnet. For example, the message
3277:
The size of bot networks peaked in mid-2004, with many using more than 100,000 infected machines, according to Mark Sunner, chief technology officer at
MessageLabs.The average botnet size is now about 20,000 computers, he
720:
some cases, breaking into the C&C network itself. In response to this, C&C operators have resorted to using techniques such as overlaying their C&C networks on other existing benign infrastructure such as
683:
The botnet controller community constantly competes over who has the most bots, the highest overall bandwidth, and the most "high-quality" infected machines, like university, corporate, and even government machines.
2368:
3470:
2651:
2590:
543:
The botmaster may then use the bots to gather keystrokes or use form grabbing to steal online credentials and may rent out the botnet as DDoS and/or spam as a service or sell the credentials online for a
2560:
2308:
431:
services. This is one of the earliest types of C&C. A zombie computer accesses a specially-designed webpage or domain(s) which serves the list of controlling commands. The advantages of using
400:
Since most botnets using IRC networks and domains can be taken down with time, hackers have moved to P2P botnets with C&C to make the botnet more resilient and resistant to termination.
3440:
2987:
2469:
2185:
333:(DDoS). Most owners of zombie computers are unaware that their system is being used in this way. Because the owner tends to be unaware, these computers are metaphorically compared to
105:(malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based
2737:
3584:
2277:
572:) to the host computer. When the re-connection is made, depending on how it is written, a Trojan may then delete itself or may remain present to update and maintain the modules.
3744:
1845:
2695:
2335:
811:
during a lawsuit with notorious spammer Khan C. Smith in 2001. The botnet was constructed for the purpose of bulk spam, and accounted for nearly 25% of all spam at the time.
3946:
3834:
3808:
2244:
540:
instructs the infected PC to connect to a particular command-and-control (C&C) server. (This allows the botmaster to keep logs of how many bots are active and online.)
1698:
746:. Network-based approaches tend to use the techniques described above; shutting down C&C servers, null-routing DNS entries, or completely shutting down IRC servers.
3860:
639:
often gain access to confidential corporate information. Several targeted attacks on large corporations aimed to steal sensitive information, such as the Aurora botnet.
63:, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a
3522:
2507:
2358:
449:
can be used to make it difficult to track down the control servers, which may change from day to day. Control servers may also hop from DNS domain to DNS domain, with
3666:
3017:
3466:
2033:
1986:
2827:
2394:
363:
botnets use a simple C&C botnet protocol in which bots connect to the main command server to host the botnet. Bots are added to the botnet by using a scanning
4045:
2556:
700:. Phishing is the acquiring of login information to the "victim's" accounts with a link the "victim" clicks on that is sent through an email or text. A survey by
2647:
2583:
2300:
1755:
742:
was aimed at consumers, but most target enterprises and/or ISPs. Host-based techniques use heuristics to identify bot behavior that has bypassed conventional
670:
mining was used in some of the more recent botnets have which include bitcoin mining as a feature in order to generate profits for the operator of the botnet.
388:) standard is popular with botnets. The first known popular botnet controller script, "MaXiTE Bot" was using IRC XDCC protocol for private control commands.
3775:
208:
A peer-to-peer (P2P) network in which interconnected nodes ("peers") share resources among each other without the use of a centralized administrative system
99:
have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a
5104:
687:
While botnets are often named after the malware that created them, multiple botnets typically use the same malware but are operated by different entities.
352:
Botnet command and control (C&C) protocols have been implemented in a number of ways, from traditional IRC approaches to more sophisticated versions.
252:" or "bot master") controls the botnet remotely. This is known as the command-and-control (C&C). The program for the operation must communicate via a
3180:
3973:
2064:
529:
A hacker purchases or builds a Trojan and/or exploit kit and uses it to start infecting users' computers, whose payload is a malicious application—the
4589:
3383:
152:
to communicate. These P2P bot programs perform the same actions as the client–server model, but they do not require a central server to communicate.
148:(the controller of the botnet) to perform all control from a remote location, which obfuscates the traffic. Many recent botnets now rely on existing
3558:
2624:
285:
Some botnets implement custom versions of well-known protocols. The implementation differences can be used for detection of botnets. For example,
3444:
3153:
2446:
754:, that detects botnet activity within a network by analyzing network traffic and comparing it to patterns characteristic of malicious processes.
3207:
2979:
2878:
384:
being taken down. However, in some cases, merely blocking of certain keywords has proven effective in stopping IRC-based botnets. The RFC 1459 (
275:
from the bot herder alerts all infected clients belonging to #channel to begin a DDoS attack on the website www.victim.com. An example response
4956:
3636:
1661:
3696:
2734:
2177:
4566:
1812:
435:
or domains as C&C is that a large botnet can be effectively controlled and maintained with very simple code that can be readily updated.
3890:
3718:
3303:
2154:
632:
has said that these types of attacks causing outages on major websites will continue to occur regularly due the use of botnets as a service.
265:
56:
712:
The geographic dispersal of botnets means that each recruit must be individually identified/corralled/repaired and limits the benefits of
375:
server default logins. Once a login is found, the scanning server can infect it through SSH with malware, which pings the control server.
3580:
651:
occurs when the user's computer visits websites without the user's awareness to create false web traffic for personal or commercial gain.
140:
Botnet architecture has evolved over time in an effort to evade detection and disruption. Traditionally, bot programs are constructed as
4597:
2129:
340:
The process of stealing computing resources as a result of a system being joined to a "botnet" is sometimes referred to as "scrumping".
3748:
2796:
2417:
2267:
4038:
2011:
1837:
784:
software in order to convince the malware that a system is vulnerable. The malicious files are then analyzed using forensic software.
2713:
555:
Computers can be co-opted into a botnet when they execute malicious software. This can be accomplished by luring users into making a
5221:
4912:
4635:
4529:
3610:
3261:
1980:
1911:
1887:
3356:
3330:
2331:
3938:
4325:
3798:
2957:
172:
The first botnets on the
Internet used a client–server model to accomplish their tasks. Typically, these botnets operate through
3916:
3830:
2240:
2112:
Schiller, Craig A.; Binkley, Jim; Harley, David; Evron, Gadi; Bradley, Tony; Willems, Carsten; Cross, Michael (1 January 2007).
1870:
Schiller, Craig A.; Binkley, Jim; Harley, David; Evron, Gadi; Bradley, Tony; Willems, Carsten; Cross, Michael (1 January 2007).
664:
attacks use botnets to log in to many user accounts with stolen passwords, such as in the attack against
General Motors in 2022.
5109:
4579:
3500:
4006:– an all-volunteer security watchdog group that gathers, tracks, and reports on malware, botnet activity, and electronic fraud
3418:
1724:
1690:
5272:
4936:
3856:
3529:
3304:"Symantec.cloud | Email Security, Web Security, Endpoint Protection, Archiving, Continuity, Instant Messaging Security"
2499:
2086:
3670:
3009:
2935:
5175:
4392:
4031:
2390:
2218:
2029:
290:
2819:
5257:
4014:
3334:
758:
325:
and can be used to perform malicious tasks under remote direction. Botnets of zombie computers are often used to spread
4584:
4505:
4305:
2529:
450:
114:
5282:
5262:
5195:
4561:
4519:
4175:
2850:"Detecting and Dismantling Botnet Command and Control Infrastructure using Behavioral Profilers and Bot Informants"
1747:
1666:
791:, held a hearing on the threats posed by botnets and the public and private efforts to disrupt and dismantle them.
761:
are analyzing botnets' behavior by simultaneously running one million Linux kernels—a similar scale to a botnet—as
3997:
3771:
39:
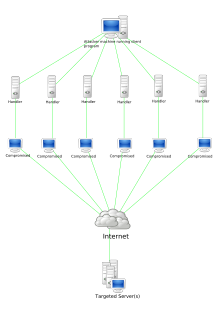
botnet diagram showing a DDoS attack. (Note this is also an example of a type of client–server model of a botnet.)
5063:
4422:
4140:
3047:
751:
310:
769:
to emulate a very large network, allowing them to watch how botnets work and experiment with ways to stop them.
4997:
4987:
4879:
4407:
4285:
4180:
620:
564:
440:
330:
322:
2758:
165:
141:
3176:
5073:
4495:
4447:
4110:
2673:
2056:
729:
725:
502:
408:
3969:
3387:
5287:
5124:
4951:
3554:
2907:
645:
are e-mail messages disguised as messages from people, but are either advertising, annoying, or malicious.
3039:
United States. Congress. Senate. Committee on the
Judiciary. Subcommittee on Crime and Terrorism (2018).
212:
In response to efforts to detect and decapitate IRC botnets, bot herders have begun deploying malware on
5277:
4905:
4673:
4628:
4536:
4270:
2616:
1779:
2018 26th
Euromicro International Conference on Parallel, Distributed and Network-based Processing (PDP)
733:
713:
407:
as a way to secure or lock down the botnet from others, most of the time when they use encryption it is
4009:
2442:
3115:
3069:
Meidan, Yair (2018). "N-BaIoT-Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders".
5231:
5226:
5185:
5114:
4972:
4874:
4556:
4468:
4417:
4362:
4230:
4203:
4185:
4150:
4083:
4054:
3632:
3203:
2867:
1792:
788:
781:
629:
585:
3692:
2912:
5180:
4340:
4115:
4073:
1671:
1500:
743:
661:
428:
385:
173:
121:
3441:"Pushdo Botnet — New DDOS attacks on major web sites — Harry Waldron — IT Security"
5165:
5002:
4982:
4864:
4524:
4452:
4357:
3882:
3722:
3307:
3253:
3096:
3078:
2146:
1818:
1782:
457:
364:
192:
92:
3607:"Calculating the Size of the Downadup Outbreak — F-Secure Weblog : News from the Lab"
2868:"DISCLOSURE: Detecting Botnet Command and Control Servers Through Large-Scale NetFlow Analysis"
5267:
5190:
5144:
5053:
4854:
4813:
4572:
4330:
4265:
4215:
4162:
4120:
4068:
3145:
2689:
2125:
1976:
1968:
1883:
1808:
1777:
Putman, C. G. J.; Abhishta; Nieuwenhuis, L. J. M. (March 2018). "Business Model of a Botnet".
1646:
604:
593:
556:
337:. A coordinated DDoS attack by multiple botnet machines also resembles a zombie horde attack.
225:
217:
96:
17:
5252:
5205:
5170:
4898:
4869:
4834:
4621:
4541:
4481:
4245:
4235:
4130:
3245:
3135:
3127:
3088:
2983:
2788:
2427:
2422:
2213:
2117:
1949:
1875:
1800:
1562:
787:
On 15 July 2014, the Subcommittee on Crime and Terrorism of the Committee on the Judiciary,
766:
762:
509:
306:
106:
72:
2008:
5200:
5139:
4748:
4738:
4683:
4432:
4412:
4135:
4125:
2906:. Proceedings of the 15th Annual Network and Distributed System Security Symposium. 2008.
2741:
2709:
2015:
1601:
1360:
1355:
1124:
1119:
560:
129:
32:
3230:
2557:"This Is What It Looks Like When A Click-Fraud Botnet Secretly Controls Your Web Browser"
1903:
547:
Depending on the quality and capability of the bots, the value is increased or decreased.
3606:
3360:
1796:
780:
The most capable method of using software to combat against a virus has been to utilize
5160:
5134:
4941:
4839:
4818:
4808:
4763:
4753:
4718:
4688:
4602:
4500:
4350:
4300:
4275:
4240:
4220:
4100:
4088:
3010:"Subcommittee on Crime and Terrorism | United States Senate Committee on the Judiciary"
2121:
1879:
1751:
1521:
1188:
1183:
1001:
960:
739:
569:
420:
318:
253:
220:
so that only someone with access to the private key can control the botnet, such as in
177:
3912:
1953:
624:
requests by the bots, attempting to connect to the server, therefore, overloading it.
5246:
5119:
5038:
4946:
4844:
4778:
4743:
4733:
4728:
4698:
4668:
4512:
4473:
4442:
4437:
4290:
4280:
4250:
1651:
1582:
1402:
1298:
1143:
1062:
1042:
980:
424:
297:'s SMTP server disables the entire pool of bots that rely upon the same SMTP server.
221:
3492:
3257:
3100:
2030:"Banks can't prevent cyber attacks like those hitting PNC, Key, U.S. Bank this week"
1822:
160:
5058:
4977:
4849:
4783:
4758:
4703:
4546:
4402:
4105:
3913:"Discovered: Botnet Costing Display Advertisers over Six Million Dollars per Month"
3410:
2272:
1720:
1423:
938:
881:
600:
372:
213:
149:
52:
36:
419:
Many large botnets tend to use domains rather than IRC in their construction (see
168:, where individual clients request services and resources from centralized servers
2849:
2178:"Hammertoss: Russian hackers target the cloud, Twitter, GitHub in malware spread"
2090:
704:
found that around two-thirds of electronic "espionage" cases come from phishing.
5129:
5048:
4708:
4486:
4320:
4295:
4260:
4095:
1481:
1382:
648:
642:
278:
271:
64:
27:
Collection of compromised internet-connected devices controlled by a third party
3131:
3092:
2927:
2208:
2009:
Inference and Analysis of Formal Models of Botnet Command and Control Protocols
1804:
5088:
5068:
5033:
4551:
4367:
4315:
4198:
4078:
607:
into China to create a large ephemeral botnet to attack large targets such as
581:
525:
This example illustrates how a botnet is created and used for malicious gain.
404:
368:
326:
249:
236:
125:
88:
3467:"New Zealand teenager accused of controlling botnet of 1.3 million computers"
3149:
2301:"Russian State Hackers Use Britney Spears Instagram Posts to Control Malware"
5078:
5028:
4803:
4693:
4427:
4382:
4377:
4225:
4193:
2904:
BotSniffer: Detecting Botnet Command and Control Channels in Network Traffic
1444:
1164:
808:
747:
494:
469:
446:
2533:
235:
In order to find other infected machines, P2P bots discreetly probe random
2470:"China deploys new weapon for online censorship in form of 'Great Cannon'"
814:
Around 2006, to thwart detection, some botnets were scaling back in size.
4773:
4723:
4678:
4387:
4345:
4208:
3803:
2363:
697:
654:
432:
84:
60:
48:
3249:
204:
5083:
4992:
4921:
4859:
4713:
4397:
4372:
4335:
4023:
1656:
1339:
701:
667:
635:
486:
313:
is a computer connected to the Internet that has been compromised by a
188:
181:
101:
3581:"New Massive Botnet Twice the Size of Storm — Security/Perimeter"
3140:
3040:
1940:
Heron, Simon (1 April 2007). "Botnet command and control techniques".
411:
and has presented challenges in both implementing it and breaking it.
75:". The term is usually used with a negative or malicious connotation.
5043:
5018:
4793:
4768:
4310:
4170:
1543:
1101:
919:
625:
608:
505:
490:
482:
461:
360:
334:
314:
294:
293:(SMTP) implementation for testing spam capability. Bringing down the
286:
3970:"Botnet size may be exaggerated, says Enisa | Security Threats"
3114:
García, S.; Grill, M.; Stiborek, J.; Zunino, A. (1 September 2014).
282:
by a bot client alerts the bot herder that it has begun the attack.
3719:"Infosecurity (UK) - BredoLab downed botnet linked with Spamit.com"
3083:
2766:
2359:"Cybercriminals are using the Tor network to control their botnets"
1838:"Novice cyberciminals offer commercial access to five mini botnets"
1787:
4798:
4788:
4663:
3939:"This tiny botnet is launching the most powerful DDoS attacks yet"
3357:"Storm Worm network shrinks to about one-tenth of its former size"
2648:"Got a botnet? Thinking of using it to mine Bitcoin? Don't bother"
1022:
658:
receives, allowing sites to earn more commission from advertisers.
589:
465:
159:
68:
31:
4890:
2820:"The Number of People Who Fall for Phishing Emails Is Staggering"
2958:"Researchers Boot Million Linux Kernels to Help Botnet Research"
2676:. BitcoinMining.com. Archived from the original on 19 April 2016
580:
In some cases, a botnet may be temporarily created by volunteer
498:
240:
updates itself by periodically communicating to all known bots.
4894:
4617:
4027:
4003:
732:
systems that are not dependent on any fixed servers, and using
4658:
4018:
3745:"Research: Small DIY botnets prevalent in enterprise networks"
2018:, 2010 ACM Conference on Computer and Communications Security.
721:
603:
allows the modification of legitimate web browsing traffic at
264:
IRC is a historically favored means of C&C because of its
110:
2332:"Walking through Win32/Jabberbot.A instant messaging C&C"
4149:
2500:"Here's why massive website outages will continue happening"
2268:"Reddit-powered botnet infected thousands of Macs worldwide"
1691:"Thingbots: The Future of Botnets in the Internet of Things"
3883:"EU police operation takes down malicious computer network"
3204:"EarthLink wins $ 25 million lawsuit against junk e-mailer"
2980:"Brute-Force Botnet Attacks Now Elude Volumetric Detection"
2617:"Credential-stuffing attack on GM exposes car owners' data"
453:
being used to create new DNS names for controller servers.
4613:
910:
Damon Briant, BOB.dc, Cotmonger, Hacktool.Spammer, Kraken
2960:. IT Security & Network Security News. 12 August 2009
256:
to the client on the victim's machine (zombie computer).
3231:"Hackers Strengthen Malicious Botnets by Shrinking Them"
1636:
researchers, possibly leading to inaccurate assessments.
144:
which communicate via existing servers. This allows the
4015:
Botnet Bust – "SpyEye Malware Mastermind Pleads Guilty"
3831:"Cómo detectar y borrar el rootkit TDL4 (TDSS/Alureon)"
807:
The first botnet was first acknowledged and exposed by
736:
to defeat attempts to break into or spoof the network.
128:
as commodities for a variety of purposes, including as
3799:"Spamhaus Declares Grum Botnet Dead, but Festi Surges"
3493:"Technology | Spam on rise after brief reprieve"
3116:"An empirical comparison of botnet detection methods"
3046:. Washington, DC: U.S. Government Publishing Office.
2241:"First Twitter-controlled Android botnet discovered"
2147:"When Bots Use Social Media for Command and Control"
2087:"One of world's biggest botnets taken down, US says"
5214:
5153:
5097:
5011:
4965:
4929:
4827:
4651:
4461:
4161:
4061:
2443:"Anonymous 101 Part Deux: Morals Triumph Over Lulz"
51:-connected devices, each of which runs one or more
3772:"Oleg Nikolaenko, Mega-D Botmaster to Stand Trial"
3359:. Tech.Blorge.Com. 21 October 2007. Archived from
2116:. Burlington, Virginia: Syngress. pp. 77–95.
1973:Handbook of Information and Communication Security
1874:. Burlington, Virginia: Syngress. pp. 29–75.
4010:EWeek.com – "Is the Botnet Battle Already Lost?"
3660:
3658:
3656:
3654:
2875:Annual Computer Security Applications Conference
2789:"What is phishing? - Definition from WhatIs.com"
2694:: CS1 maint: bot: original URL status unknown (
871:MaXiTE XDCC Bot, MaXiTE IRC TCL Script, MaxServ
3693:"Botnet sics zombie soldiers on gimpy websites"
3523:"Sality: Story of a Peer-to-Peer Viral Network"
2530:"Operation Aurora — The Command Structure"
3298:
3296:
3294:
3292:
3290:
3288:
3286:
1971:. In Stamp, Mark; Stavroulakis, Peter (eds.).
191:, infected clients connect to an infected IRC
4906:
4629:
4039:
3443:. Msmvps.com. 2 February 2010. Archived from
3331:"Researchers hijack control of Torpig botnet"
2584:"Social Media Bots and Deceptive Advertising"
750:is software, developed with support from the
367:, which runs on an external server and scans
8:
3998:The Honeynet Project & Research Alliance
280:PRIVMSG #channel I am DDoSing www.victim.com
3667:"Top botnets control 1M hijacked computers"
3633:"Waledac botnet 'decimated' by MS takedown"
1904:"Botnets: Definition, Types, How They Work"
1012:Pandex, Mutant (related to: Wigon, Pushdo)
4913:
4899:
4891:
4636:
4622:
4614:
4046:
4032:
4024:
3177:"Atlanta Business Chronicle, Staff Writer"
2007:C.Y. Cho, D. Babic, R. Shin, and D. Song.
816:
4590:Security information and event management
3528:. Symantec. 3 August 2011. Archived from
3139:
3082:
2911:
2330:Dorais-Joncas, Alexis (30 January 2013).
2028:Teresa Dixon Murray (28 September 2012).
1786:
563:, or by tricking the user into running a
501:open source instant message protocol and
2759:"Uses of botnets | The Honeynet Project"
696:information to accounts. This is called
203:
3555:"How FBI, police busted massive botnet"
2391:"Cisco ASA Botnet Traffic Filter Guide"
2209:"Hackers Use Twitter to Control Botnet"
1682:
87:-connected devices, such as computers,
4957:Timeline of computer viruses and worms
2687:
2654:from the original on 14 September 2017
1662:Timeline of computer viruses and worms
584:, such as with implementations of the
512:to communicate with a C&C server.
481:Calling back to popular sites such as
4567:Host-based intrusion detection system
4000:– "Know your Enemy: Tracking Botnets"
3267:from the original on 12 November 2013
3020:from the original on 11 December 2022
2990:from the original on 14 November 2017
2188:from the original on 18 February 2017
621:Distributed denial-of-service attacks
7:
3976:from the original on 23 October 2012
3469:. The H security. 30 November 2007.
3156:from the original on 9 December 2022
2716:from the original on 20 October 2012
2510:from the original on 10 October 2022
2449:from the original on 2 February 2013
1935:
1933:
1931:
1929:
1914:from the original on 10 January 2023
1865:
1863:
1471:LowSecurity, FreeMoney, Ring0.Tools
83:A botnet is a logical collection of
4598:Runtime application self-protection
3893:from the original on 7 October 2019
3833:. kasperskytienda.es. 3 July 2011.
3778:from the original on 7 January 2016
3244:(4). IEEE Computer Society: 17–19.
2357:Constantin, Lucian (25 July 2013).
2221:from the original on 7 October 2017
2157:from the original on 7 October 2017
1836:Danchev, Dancho (11 October 2013).
1727:from the original on 7 January 2023
1701:from the original on 7 January 2023
1510:Zbot, PRG, Wsnpoem, Gorhax, Kneber
248:A botnet's originator (known as a "
3859:. Networkworld.com. 22 July 2009.
3857:"America's 10 most wanted botnets"
3837:from the original on 14 March 2016
3639:from the original on 18 April 2011
3210:from the original on 23 March 2019
3202:Mary Jane Credeur (22 July 2002).
3183:from the original on 22 March 2019
2830:from the original on 24 March 2019
2799:from the original on 24 March 2019
2480:from the original on 17 April 2015
2468:Peterson, Andrea (10 April 2015).
2371:from the original on 3 August 2017
2280:from the original on 23 April 2017
2266:Gallagher, Sean (3 October 2014).
1175:DownUp, DownAndUp, DownAdUp, Kido
273:TOPIC #channel DDoS www.victim.com
25:
5222:Computer and network surveillance
4530:Security-focused operating system
3949:from the original on 31 July 2022
3863:from the original on 22 June 2024
3609:. F-secure.com. 16 January 2009.
3587:from the original on 11 June 2016
3561:from the original on 5 March 2010
3473:from the original on 8 March 2013
3421:from the original on 5 March 2016
3306:. Messagelabs.com. Archived from
3050:from the original on 22 June 2024
2938:from the original on 22 June 2024
2884:from the original on 4 March 2016
2735:Many-to-Many Botnet Relationships
2627:from the original on 31 July 2022
2596:from the original on 22 June 2024
2563:from the original on 23 July 2017
2555:Edwards, Jim (27 November 2013).
2416:Berinato, Scott (November 2006).
2067:from the original on 17 July 2017
2036:from the original on 25 July 2015
1989:from the original on 22 June 2024
1758:from the original on 12 July 2015
1748:"Bots &; Botnet: An Overview"
765:on a 4,480-node high-performance
59:(DDoS) attacks, steal data, send
55:. Botnets can be used to perform
4326:Insecure direct object reference
3919:from the original on 9 July 2017
3811:from the original on 1 July 2015
3770:Warner, Gary (2 December 2010).
3699:from the original on 11 May 2011
3613:from the original on 23 May 2016
3503:from the original on 22 May 2010
3409:Stewart, Joe (13 January 2009).
3386:. SC Magazine US. Archived from
3384:"The Rustock botnet spams again"
3333:. SC Magazine US. Archived from
2818:Aguilar, Mario (14 April 2015).
2441:Norton, Quinn (1 January 2012).
2397:from the original on 25 May 2017
2338:from the original on 2 June 2017
2311:from the original on 8 June 2017
2299:Cimpanu, Catalin (6 June 2017).
2247:from the original on 3 July 2017
2122:10.1016/B978-159749135-8/50005-6
1880:10.1016/B978-159749135-8/50004-4
1848:from the original on 1 July 2015
1329:Spam-DComServ, Covesmer, Xmiler
427:). They are usually hosted with
4580:Information security management
3797:Kirk, Jeremy (16 August 2012).
3774:. CyberCrime & Doing Time.
3669:. Computerworld. Archived from
3635:. The Register. 16 March 2010.
3411:"Spam Botnets to Watch in 2009"
2646:Nichols, Shaun (24 June 2014).
2207:Singel, Ryan (13 August 2009).
2055:Arntz, Pieter (30 March 2016).
1746:Ramneek, Puri (8 August 2003).
4937:Comparison of computer viruses
2928:"IRCHelp.org – Privacy on IRC"
2532:. Damballa.com. Archived from
1:
5176:Data loss prevention software
3968:Espiner, Tom (8 March 2011).
3721:. .canada.com. Archived from
3695:. The Register. 14 May 2008.
3665:Gregg Keizer (9 April 2008).
3583:. DarkReading. 7 April 2008.
3382:Chuck Miller (25 July 2008).
2710:"Trojan horse, and Virus FAQ"
2089:. 25 May 2024. Archived from
1954:10.1016/S1353-4858(07)70045-4
892:Beagle, Mitglieder, Lodeight
508:are popular ways of avoiding
344:luxury items and properties.
291:Simple Mail Transfer Protocol
289:features a slightly modified
216:networks. These bots may use
57:distributed denial-of-service
18:Command and control (malware)
3915:. Spider.io. 19 March 2013.
3229:Paulson, L.D. (April 2006).
1356:November 2010 (not complete)
759:Sandia National Laboratories
468:, and Afraid.org to point a
451:domain generation algorithms
4585:Information risk management
4506:Multi-factor authentication
4062:Related security categories
4004:The Shadowserver Foundation
3329:Chuck Miller (5 May 2009).
561:web browser vulnerabilities
115:Hypertext Transfer Protocol
5304:
5196:Intrusion detection system
4562:Intrusion detection system
4520:Computer security software
4176:Advanced persistent threat
3132:10.1016/j.cose.2014.05.011
3093:10.1109/MPRV.2018.03367731
1805:10.1109/PDP2018.2018.00077
1667:Advanced Persistent Threat
803:Historical list of botnets
5064:Privacy-invasive software
4147:
4141:Digital rights management
2057:"The Facts about Botnets"
2014:24 September 2016 at the
1288:Pokier, Slogger, Cryptic
949:Nuwar, Peacomm, Zhelatin
752:U.S. Army Research Office
460:hosting services such as
441:denial-of-service attacks
331:denial-of-service attacks
120:Botnets are increasingly
4286:Denial-of-service attack
4181:Arbitrary code execution
3120:Computers & Security
3071:IEEE Pervasive Computing
3014:www.judiciary.senate.gov
5074:Rogue security software
4496:Computer access control
4448:Rogue security software
4111:Electromagnetic warfare
3747:. ZDNet. Archived from
832:Spam capacity (bn/day)
730:peer-to-peer networking
409:public-key cryptography
164:A network based on the
5110:Classic Mac OS viruses
4952:List of computer worms
4542:Obfuscation (software)
4271:Browser Helper Objects
4155:
2877:. ACM. December 2012.
1969:"Peer-to-peer botnets"
1518:(Several: 2011, 2012)
829:Estimated no. of bots
456:Some botnets use free
266:communication protocol
209:
169:
40:
5273:Distributed computing
4537:Data-centric security
4418:Remote access trojans
4153:
3557:. theregister.co.uk.
3238:Computer; News Briefs
2854:vhosts.eecs.umich.edu
1695:Security Intelligence
734:public key encryption
601:Great Cannon of China
207:
163:
150:peer-to-peer networks
35:
5232:Operation: Bot Roast
4875:Operation: Bot Roast
4469:Application security
4363:Privilege escalation
4231:Cross-site scripting
4084:Cybersex trafficking
4055:Information security
3535:on 24 September 2015
3499:. 26 November 2008.
2986:. 19 December 2016.
2740:4 March 2016 at the
2418:"Attack of the Bots"
1781:. pp. 441–445.
1697:. 20 February 2016.
1505:3,600,000 (US only)
789:United States Senate
630:Shuman Ghosemajumder
586:Low Orbit Ion Cannon
403:Some have also used
95:(IoT) devices whose
5258:Command and control
5181:Defensive computing
5098:By operating system
4116:Information warfare
4074:Automotive security
3363:on 24 December 2007
3337:on 24 December 2007
3310:on 18 November 2020
3250:10.1109/MC.2006.136
3179:. bizjournals.com.
2982:. DARKReading from
2621:www.theregister.com
2506:. 24 October 2016.
2474:The Washington Post
1967:Wang, Ping (2010).
1797:2018arXiv180410848P
1672:Volunteer computing
1053:Cbeplay, Exchanger
744:anti-virus software
662:Credential stuffing
429:bulletproof hosting
348:Command and control
174:Internet Relay Chat
166:client–server model
156:Client–server model
5166:Antivirus software
5012:Malware for profit
4983:Man-in-the-browser
4930:Infectious malware
4865:Man-in-the-browser
4525:Antivirus software
4393:Social engineering
4358:Polymorphic engine
4311:Fraudulent dialers
4216:Hardware backdoors
4156:
2243:. 24 August 2016.
2176:Osborne, Charlie.
1308:Danmec, Hydraflux
971:RKRustok, Costrat
605:internet backbones
218:digital signatures
210:
170:
93:Internet of things
41:
5283:Security breaches
5263:Internet security
5240:
5239:
5191:Internet security
5145:HyperCard viruses
5054:Keystroke logging
5044:Fraudulent dialer
4988:Man-in-the-middle
4888:
4887:
4855:Internet security
4611:
4610:
4573:Anomaly detection
4478:Secure by default
4331:Keystroke loggers
4266:Drive-by download
4154:vectorial version
4121:Internet security
4069:Computer security
3673:on 13 August 2014
3447:on 16 August 2010
2305:Bleeping Computer
2061:Malwarebytes Labs
2032:. Cleveland.com.
1814:978-1-5386-4975-6
1647:Computer security
1632:
1631:
1091:Rlsloup, Pixoliz
929:Sinowal, Anserin
865:500-1000 servers
594:Project Chanology
557:drive-by download
260:Control protocols
226:ZeroAccess botnet
107:network protocols
16:(Redirected from
5295:
5206:Network security
5171:Browser security
4915:
4908:
4901:
4892:
4870:Network security
4835:Browser security
4638:
4631:
4624:
4615:
4482:Secure by design
4413:Hardware Trojans
4246:History sniffing
4236:Cross-site leaks
4131:Network security
4048:
4041:
4034:
4025:
3986:
3985:
3983:
3981:
3965:
3959:
3958:
3956:
3954:
3935:
3929:
3928:
3926:
3924:
3909:
3903:
3902:
3900:
3898:
3879:
3873:
3872:
3870:
3868:
3853:
3847:
3846:
3844:
3842:
3827:
3821:
3820:
3818:
3816:
3794:
3788:
3787:
3785:
3783:
3767:
3761:
3760:
3758:
3756:
3741:
3735:
3734:
3732:
3730:
3715:
3709:
3708:
3706:
3704:
3689:
3683:
3682:
3680:
3678:
3662:
3649:
3648:
3646:
3644:
3629:
3623:
3622:
3620:
3618:
3603:
3597:
3596:
3594:
3592:
3577:
3571:
3570:
3568:
3566:
3551:
3545:
3544:
3542:
3540:
3534:
3527:
3519:
3513:
3512:
3510:
3508:
3489:
3483:
3482:
3480:
3478:
3463:
3457:
3456:
3454:
3452:
3437:
3431:
3430:
3428:
3426:
3406:
3400:
3399:
3397:
3395:
3379:
3373:
3372:
3370:
3368:
3353:
3347:
3346:
3344:
3342:
3326:
3320:
3319:
3317:
3315:
3300:
3281:
3280:
3274:
3272:
3266:
3235:
3226:
3220:
3219:
3217:
3215:
3199:
3193:
3192:
3190:
3188:
3172:
3166:
3165:
3163:
3161:
3143:
3111:
3105:
3104:
3086:
3066:
3060:
3059:
3057:
3055:
3036:
3030:
3029:
3027:
3025:
3006:
3000:
2999:
2997:
2995:
2984:Information Week
2976:
2970:
2969:
2967:
2965:
2954:
2948:
2947:
2945:
2943:
2924:
2918:
2917:
2915:
2900:
2894:
2893:
2891:
2889:
2883:
2872:
2864:
2858:
2857:
2846:
2840:
2839:
2837:
2835:
2815:
2809:
2808:
2806:
2804:
2785:
2779:
2778:
2776:
2774:
2769:on 20 March 2019
2765:. Archived from
2763:www.honeynet.org
2755:
2749:
2732:
2726:
2725:
2723:
2721:
2706:
2700:
2699:
2693:
2685:
2683:
2681:
2674:"Bitcoin Mining"
2670:
2664:
2663:
2661:
2659:
2643:
2637:
2636:
2634:
2632:
2612:
2606:
2605:
2603:
2601:
2595:
2588:
2579:
2573:
2572:
2570:
2568:
2552:
2546:
2545:
2543:
2541:
2526:
2520:
2519:
2517:
2515:
2496:
2490:
2489:
2487:
2485:
2465:
2459:
2458:
2456:
2454:
2438:
2432:
2431:
2430:on 14 July 2014.
2426:. Archived from
2413:
2407:
2406:
2404:
2402:
2387:
2381:
2380:
2378:
2376:
2354:
2348:
2347:
2345:
2343:
2327:
2321:
2320:
2318:
2316:
2296:
2290:
2289:
2287:
2285:
2263:
2257:
2256:
2254:
2252:
2237:
2231:
2230:
2228:
2226:
2204:
2198:
2197:
2195:
2193:
2173:
2167:
2166:
2164:
2162:
2145:Zeltser, Lenny.
2142:
2136:
2135:
2109:
2103:
2102:
2100:
2098:
2083:
2077:
2076:
2074:
2072:
2052:
2046:
2045:
2043:
2041:
2025:
2019:
2005:
1999:
1998:
1996:
1994:
1964:
1958:
1957:
1942:Network Security
1937:
1924:
1923:
1921:
1919:
1900:
1894:
1893:
1867:
1858:
1857:
1855:
1853:
1833:
1827:
1826:
1790:
1774:
1768:
1767:
1765:
1763:
1743:
1737:
1736:
1734:
1732:
1717:
1711:
1710:
1708:
1706:
1687:
1537:2011 or earlier
1315:
1270:Loosky, Locksky
1252:Tofsee, Mondera
1199:Waled, Waledpak
1180:2008 (November)
1159:2008 (November)
1039:2008 (November)
823:Date dismantled
817:
767:computer cluster
763:virtual machines
510:egress filtering
307:computer science
281:
274:
21:
5303:
5302:
5298:
5297:
5296:
5294:
5293:
5292:
5243:
5242:
5241:
5236:
5215:Countermeasures
5210:
5201:Mobile security
5149:
5140:Palm OS viruses
5105:Android malware
5093:
5007:
5003:Zombie computer
4961:
4925:
4919:
4889:
4884:
4823:
4652:Notable botnets
4647:
4642:
4612:
4607:
4457:
4157:
4145:
4136:Copy protection
4126:Mobile security
4057:
4052:
3994:
3989:
3979:
3977:
3967:
3966:
3962:
3952:
3950:
3937:
3936:
3932:
3922:
3920:
3911:
3910:
3906:
3896:
3894:
3881:
3880:
3876:
3866:
3864:
3855:
3854:
3850:
3840:
3838:
3829:
3828:
3824:
3814:
3812:
3796:
3795:
3791:
3781:
3779:
3769:
3768:
3764:
3754:
3752:
3743:
3742:
3738:
3728:
3726:
3717:
3716:
3712:
3702:
3700:
3691:
3690:
3686:
3676:
3674:
3664:
3663:
3652:
3642:
3640:
3631:
3630:
3626:
3616:
3614:
3605:
3604:
3600:
3590:
3588:
3579:
3578:
3574:
3564:
3562:
3553:
3552:
3548:
3538:
3536:
3532:
3525:
3521:
3520:
3516:
3506:
3504:
3491:
3490:
3486:
3476:
3474:
3465:
3464:
3460:
3450:
3448:
3439:
3438:
3434:
3424:
3422:
3417:. SecureWorks.
3415:Secureworks.com
3408:
3407:
3403:
3393:
3391:
3390:on 4 April 2016
3381:
3380:
3376:
3366:
3364:
3355:
3354:
3350:
3340:
3338:
3328:
3327:
3323:
3313:
3311:
3302:
3301:
3284:
3270:
3268:
3264:
3233:
3228:
3227:
3223:
3213:
3211:
3201:
3200:
3196:
3186:
3184:
3175:Credeur, Mary.
3174:
3173:
3169:
3159:
3157:
3113:
3112:
3108:
3068:
3067:
3063:
3053:
3051:
3038:
3037:
3033:
3023:
3021:
3008:
3007:
3003:
2993:
2991:
2978:
2977:
2973:
2963:
2961:
2956:
2955:
2951:
2941:
2939:
2932:www.irchelp.org
2926:
2925:
2921:
2913:10.1.1.110.8092
2902:
2901:
2897:
2887:
2885:
2881:
2870:
2866:
2865:
2861:
2848:
2847:
2843:
2833:
2831:
2817:
2816:
2812:
2802:
2800:
2787:
2786:
2782:
2772:
2770:
2757:
2756:
2752:
2742:Wayback Machine
2733:
2729:
2719:
2717:
2708:
2707:
2703:
2686:
2679:
2677:
2672:
2671:
2667:
2657:
2655:
2645:
2644:
2640:
2630:
2628:
2614:
2613:
2609:
2599:
2597:
2593:
2586:
2581:
2580:
2576:
2566:
2564:
2554:
2553:
2549:
2539:
2537:
2536:on 11 June 2010
2528:
2527:
2523:
2513:
2511:
2498:
2497:
2493:
2483:
2481:
2467:
2466:
2462:
2452:
2450:
2440:
2439:
2435:
2415:
2414:
2410:
2400:
2398:
2389:
2388:
2384:
2374:
2372:
2356:
2355:
2351:
2341:
2339:
2329:
2328:
2324:
2314:
2312:
2298:
2297:
2293:
2283:
2281:
2265:
2264:
2260:
2250:
2248:
2239:
2238:
2234:
2224:
2222:
2206:
2205:
2201:
2191:
2189:
2175:
2174:
2170:
2160:
2158:
2144:
2143:
2139:
2132:
2131:978-159749135-8
2111:
2110:
2106:
2096:
2094:
2085:
2084:
2080:
2070:
2068:
2054:
2053:
2049:
2039:
2037:
2027:
2026:
2022:
2016:Wayback Machine
2006:
2002:
1992:
1990:
1983:
1966:
1965:
1961:
1939:
1938:
1927:
1917:
1915:
1902:
1901:
1897:
1890:
1869:
1868:
1861:
1851:
1849:
1835:
1834:
1830:
1815:
1776:
1775:
1771:
1761:
1759:
1745:
1744:
1740:
1730:
1728:
1719:
1718:
1714:
1704:
1702:
1689:
1688:
1684:
1680:
1643:
1457:2010 (January)
1313:
991:Buzus, Bachsoy
805:
757:Researchers at
710:
708:Countermeasures
693:
681:
617:
592:members during
578:
523:
518:
506:hidden services
479:
417:
398:
381:
371:for telnet and
358:
350:
311:zombie computer
303:
301:Zombie computer
276:
269:
262:
246:
244:Core components
202:
187:In the case of
158:
138:
130:booter/stresser
126:cyber criminals
81:
28:
23:
22:
15:
12:
11:
5:
5301:
5299:
5291:
5290:
5285:
5280:
5275:
5270:
5265:
5260:
5255:
5245:
5244:
5238:
5237:
5235:
5234:
5229:
5224:
5218:
5216:
5212:
5211:
5209:
5208:
5203:
5198:
5193:
5188:
5183:
5178:
5173:
5168:
5163:
5161:Anti-keylogger
5157:
5155:
5151:
5150:
5148:
5147:
5142:
5137:
5135:Mobile malware
5132:
5127:
5122:
5117:
5112:
5107:
5101:
5099:
5095:
5094:
5092:
5091:
5086:
5081:
5076:
5071:
5066:
5061:
5056:
5051:
5046:
5041:
5036:
5031:
5026:
5021:
5015:
5013:
5009:
5008:
5006:
5005:
5000:
4995:
4990:
4985:
4980:
4975:
4969:
4967:
4963:
4962:
4960:
4959:
4954:
4949:
4944:
4942:Computer virus
4939:
4933:
4931:
4927:
4926:
4920:
4918:
4917:
4910:
4903:
4895:
4886:
4885:
4883:
4882:
4877:
4872:
4867:
4862:
4857:
4852:
4847:
4842:
4840:Computer virus
4837:
4831:
4829:
4825:
4824:
4822:
4821:
4816:
4811:
4806:
4801:
4796:
4791:
4786:
4781:
4776:
4771:
4766:
4761:
4756:
4751:
4746:
4741:
4736:
4731:
4726:
4721:
4716:
4711:
4706:
4701:
4696:
4691:
4686:
4681:
4676:
4671:
4666:
4661:
4655:
4653:
4649:
4648:
4643:
4641:
4640:
4633:
4626:
4618:
4609:
4608:
4606:
4605:
4603:Site isolation
4600:
4595:
4594:
4593:
4587:
4577:
4576:
4575:
4570:
4559:
4554:
4549:
4544:
4539:
4534:
4533:
4532:
4527:
4517:
4516:
4515:
4510:
4509:
4508:
4501:Authentication
4493:
4492:
4491:
4490:
4489:
4479:
4476:
4465:
4463:
4459:
4458:
4456:
4455:
4450:
4445:
4440:
4435:
4430:
4425:
4420:
4415:
4410:
4405:
4400:
4395:
4390:
4385:
4380:
4375:
4370:
4365:
4360:
4355:
4354:
4353:
4343:
4338:
4333:
4328:
4323:
4318:
4313:
4308:
4303:
4301:Email spoofing
4298:
4293:
4288:
4283:
4278:
4273:
4268:
4263:
4258:
4253:
4248:
4243:
4241:DOM clobbering
4238:
4233:
4228:
4223:
4221:Code injection
4218:
4213:
4212:
4211:
4206:
4201:
4196:
4188:
4183:
4178:
4173:
4167:
4165:
4159:
4158:
4148:
4146:
4144:
4143:
4138:
4133:
4128:
4123:
4118:
4113:
4108:
4103:
4101:Cyberterrorism
4098:
4093:
4092:
4091:
4089:Computer fraud
4086:
4076:
4071:
4065:
4063:
4059:
4058:
4053:
4051:
4050:
4043:
4036:
4028:
4022:
4021:
4012:
4007:
4001:
3993:
3992:External links
3990:
3988:
3987:
3960:
3930:
3904:
3874:
3848:
3822:
3789:
3762:
3751:on 11 May 2011
3736:
3725:on 11 May 2011
3710:
3684:
3650:
3624:
3598:
3572:
3546:
3514:
3484:
3458:
3432:
3401:
3374:
3348:
3321:
3282:
3221:
3194:
3167:
3106:
3061:
3031:
3001:
2971:
2949:
2919:
2895:
2859:
2841:
2810:
2793:SearchSecurity
2780:
2750:
2748:, 8 June 2009.
2727:
2712:. DSLReports.
2701:
2665:
2638:
2607:
2574:
2547:
2521:
2491:
2460:
2433:
2408:
2382:
2349:
2322:
2291:
2258:
2232:
2199:
2168:
2137:
2130:
2104:
2093:on 30 May 2024
2078:
2047:
2020:
2000:
1981:
1959:
1925:
1895:
1888:
1859:
1828:
1813:
1769:
1752:SANS Institute
1738:
1712:
1681:
1679:
1676:
1675:
1674:
1669:
1664:
1659:
1654:
1649:
1642:
1639:
1638:
1637:
1630:
1629:
1627:
1625:
1622:
1619:
1617:
1613:
1612:
1609:
1607:
1604:
1599:
1597:
1596:2016 (August)
1593:
1592:
1590:
1588:
1585:
1580:
1578:
1574:
1573:
1570:
1568:
1565:
1560:
1558:
1557:2012 (Around)
1554:
1553:
1551:
1549:
1546:
1541:
1538:
1534:
1533:
1530:
1527:
1524:
1519:
1516:
1512:
1511:
1508:
1506:
1503:
1498:
1496:
1493:
1492:
1491:TDSS, Alureon
1489:
1487:
1484:
1479:
1477:
1476:2010 (around)
1473:
1472:
1469:
1466:
1463:
1460:
1458:
1454:
1453:
1451:
1449:
1447:
1442:
1440:
1436:
1435:
1432:
1429:
1426:
1421:
1419:
1418:2009 (August)
1415:
1414:
1411:
1408:
1405:
1400:
1398:
1395:
1394:
1391:
1388:
1385:
1380:
1377:
1376:2009 (Around)
1373:
1372:
1369:
1366:
1363:
1358:
1353:
1349:
1348:
1346:
1344:
1342:
1337:
1335:
1334:2008 (around)
1331:
1330:
1327:
1324:
1321:
1318:
1316:
1310:
1309:
1306:
1304:
1301:
1296:
1294:
1293:2008 (around)
1290:
1289:
1286:
1283:
1280:
1277:
1275:
1272:
1271:
1268:
1265:
1262:
1259:
1257:
1254:
1253:
1250:
1247:
1244:
1241:
1239:
1236:
1235:
1233:
1230:
1227:
1224:
1222:
1219:
1218:
1215:
1212:
1209:
1206:
1204:
1201:
1200:
1197:
1194:
1191:
1186:
1181:
1177:
1176:
1173:
1170:
1167:
1162:
1160:
1156:
1155:
1152:
1149:
1146:
1141:
1139:
1138:2008 (around)
1135:
1134:
1132:
1130:
1127:
1122:
1117:
1116:2008 (around)
1113:
1112:
1109:
1107:
1104:
1099:
1097:
1096:2008 (around)
1093:
1092:
1089:
1086:
1083:
1080:
1078:
1075:
1074:
1071:
1068:
1065:
1060:
1058:
1055:
1054:
1051:
1048:
1045:
1040:
1037:
1033:
1032:
1030:
1028:
1025:
1020:
1018:
1014:
1013:
1010:
1007:
1004:
999:
997:
996:2007 (around)
993:
992:
989:
986:
983:
978:
976:
973:
972:
969:
966:
963:
958:
955:
954:2006 (around)
951:
950:
947:
944:
941:
936:
934:
931:
930:
927:
925:
922:
917:
915:
912:
911:
908:
905:
902:
901:Marina Botnet
899:
897:
894:
893:
890:
887:
884:
879:
877:
873:
872:
869:
866:
863:
860:
858:
854:
853:
850:
847:
844:
841:
837:
836:
833:
830:
827:
824:
821:
804:
801:
740:Norton AntiBot
709:
706:
692:
689:
680:
677:
676:
675:
671:
665:
659:
652:
646:
640:
633:
616:
613:
577:
574:
549:
548:
545:
541:
534:
522:
519:
517:
514:
478:
475:
421:Rustock botnet
416:
413:
397:
394:
380:
377:
357:
354:
349:
346:
319:computer virus
302:
299:
261:
258:
254:covert channel
245:
242:
201:
198:
157:
154:
137:
134:
80:
77:
67:of the words "
47:is a group of
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
5300:
5289:
5288:Internet bots
5286:
5284:
5281:
5279:
5276:
5274:
5271:
5269:
5266:
5264:
5261:
5259:
5256:
5254:
5251:
5250:
5248:
5233:
5230:
5228:
5225:
5223:
5220:
5219:
5217:
5213:
5207:
5204:
5202:
5199:
5197:
5194:
5192:
5189:
5187:
5184:
5182:
5179:
5177:
5174:
5172:
5169:
5167:
5164:
5162:
5159:
5158:
5156:
5152:
5146:
5143:
5141:
5138:
5136:
5133:
5131:
5128:
5126:
5125:MacOS malware
5123:
5121:
5120:Linux malware
5118:
5116:
5113:
5111:
5108:
5106:
5103:
5102:
5100:
5096:
5090:
5087:
5085:
5082:
5080:
5077:
5075:
5072:
5070:
5067:
5065:
5062:
5060:
5057:
5055:
5052:
5050:
5047:
5045:
5042:
5040:
5039:Form grabbing
5037:
5035:
5032:
5030:
5027:
5025:
5022:
5020:
5017:
5016:
5014:
5010:
5004:
5001:
4999:
4996:
4994:
4991:
4989:
4986:
4984:
4981:
4979:
4976:
4974:
4971:
4970:
4968:
4964:
4958:
4955:
4953:
4950:
4948:
4947:Computer worm
4945:
4943:
4940:
4938:
4935:
4934:
4932:
4928:
4923:
4916:
4911:
4909:
4904:
4902:
4897:
4896:
4893:
4881:
4878:
4876:
4873:
4871:
4868:
4866:
4863:
4861:
4858:
4856:
4853:
4851:
4848:
4846:
4845:Computer worm
4843:
4841:
4838:
4836:
4833:
4832:
4830:
4828:Main articles
4826:
4820:
4817:
4815:
4812:
4810:
4807:
4805:
4802:
4800:
4797:
4795:
4792:
4790:
4787:
4785:
4782:
4780:
4777:
4775:
4772:
4770:
4767:
4765:
4762:
4760:
4757:
4755:
4752:
4750:
4747:
4745:
4742:
4740:
4737:
4735:
4732:
4730:
4727:
4725:
4722:
4720:
4717:
4715:
4712:
4710:
4707:
4705:
4702:
4700:
4697:
4695:
4692:
4690:
4687:
4685:
4682:
4680:
4677:
4675:
4672:
4670:
4667:
4665:
4662:
4660:
4657:
4656:
4654:
4650:
4646:
4639:
4634:
4632:
4627:
4625:
4620:
4619:
4616:
4604:
4601:
4599:
4596:
4591:
4588:
4586:
4583:
4582:
4581:
4578:
4574:
4571:
4568:
4565:
4564:
4563:
4560:
4558:
4555:
4553:
4550:
4548:
4545:
4543:
4540:
4538:
4535:
4531:
4528:
4526:
4523:
4522:
4521:
4518:
4514:
4513:Authorization
4511:
4507:
4504:
4503:
4502:
4499:
4498:
4497:
4494:
4488:
4485:
4484:
4483:
4480:
4477:
4475:
4474:Secure coding
4472:
4471:
4470:
4467:
4466:
4464:
4460:
4454:
4451:
4449:
4446:
4444:
4443:SQL injection
4441:
4439:
4436:
4434:
4431:
4429:
4426:
4424:
4423:Vulnerability
4421:
4419:
4416:
4414:
4411:
4409:
4408:Trojan horses
4406:
4404:
4403:Software bugs
4401:
4399:
4396:
4394:
4391:
4389:
4386:
4384:
4381:
4379:
4376:
4374:
4371:
4369:
4366:
4364:
4361:
4359:
4356:
4352:
4349:
4348:
4347:
4344:
4342:
4339:
4337:
4334:
4332:
4329:
4327:
4324:
4322:
4319:
4317:
4314:
4312:
4309:
4307:
4304:
4302:
4299:
4297:
4294:
4292:
4291:Eavesdropping
4289:
4287:
4284:
4282:
4281:Data scraping
4279:
4277:
4274:
4272:
4269:
4267:
4264:
4262:
4259:
4257:
4254:
4252:
4251:Cryptojacking
4249:
4247:
4244:
4242:
4239:
4237:
4234:
4232:
4229:
4227:
4224:
4222:
4219:
4217:
4214:
4210:
4207:
4205:
4202:
4200:
4197:
4195:
4192:
4191:
4189:
4187:
4184:
4182:
4179:
4177:
4174:
4172:
4169:
4168:
4166:
4164:
4160:
4152:
4142:
4139:
4137:
4134:
4132:
4129:
4127:
4124:
4122:
4119:
4117:
4114:
4112:
4109:
4107:
4104:
4102:
4099:
4097:
4094:
4090:
4087:
4085:
4082:
4081:
4080:
4077:
4075:
4072:
4070:
4067:
4066:
4064:
4060:
4056:
4049:
4044:
4042:
4037:
4035:
4030:
4029:
4026:
4020:
4016:
4013:
4011:
4008:
4005:
4002:
3999:
3996:
3995:
3991:
3975:
3972:. Zdnet.com.
3971:
3964:
3961:
3948:
3944:
3940:
3934:
3931:
3918:
3914:
3908:
3905:
3892:
3888:
3884:
3878:
3875:
3862:
3858:
3852:
3849:
3836:
3832:
3826:
3823:
3810:
3806:
3805:
3800:
3793:
3790:
3777:
3773:
3766:
3763:
3750:
3746:
3740:
3737:
3724:
3720:
3714:
3711:
3698:
3694:
3688:
3685:
3672:
3668:
3661:
3659:
3657:
3655:
3651:
3638:
3634:
3628:
3625:
3612:
3608:
3602:
3599:
3586:
3582:
3576:
3573:
3560:
3556:
3550:
3547:
3531:
3524:
3518:
3515:
3502:
3498:
3494:
3488:
3485:
3472:
3468:
3462:
3459:
3446:
3442:
3436:
3433:
3420:
3416:
3412:
3405:
3402:
3389:
3385:
3378:
3375:
3362:
3358:
3352:
3349:
3336:
3332:
3325:
3322:
3309:
3305:
3299:
3297:
3295:
3293:
3291:
3289:
3287:
3283:
3279:
3263:
3259:
3255:
3251:
3247:
3243:
3239:
3232:
3225:
3222:
3209:
3205:
3198:
3195:
3182:
3178:
3171:
3168:
3155:
3151:
3147:
3142:
3137:
3133:
3129:
3125:
3121:
3117:
3110:
3107:
3102:
3098:
3094:
3090:
3085:
3080:
3076:
3072:
3065:
3062:
3049:
3045:
3044:
3035:
3032:
3019:
3015:
3011:
3005:
3002:
2989:
2985:
2981:
2975:
2972:
2959:
2953:
2950:
2937:
2933:
2929:
2923:
2920:
2914:
2909:
2905:
2899:
2896:
2880:
2876:
2869:
2863:
2860:
2855:
2851:
2845:
2842:
2829:
2825:
2821:
2814:
2811:
2798:
2794:
2790:
2784:
2781:
2768:
2764:
2760:
2754:
2751:
2747:
2743:
2739:
2736:
2731:
2728:
2715:
2711:
2705:
2702:
2697:
2691:
2675:
2669:
2666:
2653:
2649:
2642:
2639:
2626:
2622:
2618:
2611:
2608:
2592:
2585:
2578:
2575:
2562:
2558:
2551:
2548:
2535:
2531:
2525:
2522:
2509:
2505:
2501:
2495:
2492:
2479:
2475:
2471:
2464:
2461:
2448:
2445:. Wired.com.
2444:
2437:
2434:
2429:
2425:
2424:
2419:
2412:
2409:
2396:
2392:
2386:
2383:
2370:
2366:
2365:
2360:
2353:
2350:
2337:
2333:
2326:
2323:
2310:
2306:
2302:
2295:
2292:
2279:
2275:
2274:
2269:
2262:
2259:
2246:
2242:
2236:
2233:
2220:
2216:
2215:
2210:
2203:
2200:
2187:
2183:
2179:
2172:
2169:
2156:
2152:
2148:
2141:
2138:
2133:
2127:
2123:
2119:
2115:
2108:
2105:
2092:
2088:
2082:
2079:
2066:
2062:
2058:
2051:
2048:
2035:
2031:
2024:
2021:
2017:
2013:
2010:
2004:
2001:
1988:
1984:
1982:9783642041174
1978:
1974:
1970:
1963:
1960:
1955:
1951:
1947:
1943:
1936:
1934:
1932:
1930:
1926:
1913:
1909:
1905:
1899:
1896:
1891:
1889:9781597491358
1885:
1881:
1877:
1873:
1866:
1864:
1860:
1847:
1843:
1839:
1832:
1829:
1824:
1820:
1816:
1810:
1806:
1802:
1798:
1794:
1789:
1784:
1780:
1773:
1770:
1757:
1753:
1749:
1742:
1739:
1726:
1722:
1716:
1713:
1700:
1696:
1692:
1686:
1683:
1677:
1673:
1670:
1668:
1665:
1663:
1660:
1658:
1655:
1653:
1652:Computer worm
1650:
1648:
1645:
1644:
1640:
1634:
1633:
1628:
1626:
1623:
1620:
1618:
1615:
1614:
1610:
1608:
1605:
1603:
1600:
1598:
1595:
1594:
1591:
1589:
1586:
1584:
1581:
1579:
1576:
1575:
1571:
1569:
1566:
1564:
1561:
1559:
1556:
1555:
1552:
1550:
1547:
1545:
1542:
1539:
1536:
1535:
1531:
1528:
1525:
1523:
1520:
1517:
1514:
1513:
1509:
1507:
1504:
1502:
1499:
1497:
1495:
1494:
1490:
1488:
1485:
1483:
1480:
1478:
1475:
1474:
1470:
1467:
1464:
1461:
1459:
1456:
1455:
1452:
1450:
1448:
1446:
1443:
1441:
1439:2010 (March)
1438:
1437:
1433:
1430:
1427:
1425:
1422:
1420:
1417:
1416:
1412:
1409:
1406:
1404:
1401:
1399:
1397:
1396:
1392:
1389:
1386:
1384:
1381:
1378:
1375:
1374:
1370:
1367:
1364:
1362:
1359:
1357:
1354:
1351:
1350:
1347:
1345:
1343:
1341:
1338:
1336:
1333:
1332:
1328:
1325:
1322:
1319:
1317:
1312:
1311:
1307:
1305:
1302:
1300:
1297:
1295:
1292:
1291:
1287:
1284:
1281:
1278:
1276:
1274:
1273:
1269:
1266:
1263:
1260:
1258:
1256:
1255:
1251:
1248:
1245:
1242:
1240:
1238:
1237:
1234:
1231:
1228:
1225:
1223:
1221:
1220:
1216:
1213:
1210:
1207:
1205:
1203:
1202:
1198:
1195:
1192:
1190:
1187:
1185:
1182:
1179:
1178:
1174:
1171:
1168:
1166:
1163:
1161:
1158:
1157:
1153:
1150:
1147:
1145:
1142:
1140:
1137:
1136:
1133:
1131:
1128:
1126:
1123:
1121:
1118:
1115:
1114:
1111:Sector, Kuku
1110:
1108:
1105:
1103:
1100:
1098:
1095:
1094:
1090:
1087:
1084:
1081:
1079:
1077:
1076:
1072:
1069:
1066:
1064:
1061:
1059:
1057:
1056:
1052:
1049:
1046:
1044:
1041:
1038:
1036:2007 (March)
1035:
1034:
1031:
1029:
1026:
1024:
1021:
1019:
1016:
1015:
1011:
1008:
1005:
1003:
1000:
998:
995:
994:
990:
987:
984:
982:
979:
977:
975:
974:
970:
967:
964:
962:
959:
957:2011 (March)
956:
953:
952:
948:
945:
942:
940:
937:
935:
933:
932:
928:
926:
923:
921:
918:
916:
914:
913:
909:
906:
903:
900:
898:
896:
895:
891:
888:
885:
883:
880:
878:
876:2004 (Early)
875:
874:
870:
867:
864:
861:
859:
856:
855:
851:
848:
845:
842:
839:
838:
834:
831:
828:
825:
822:
820:Date created
819:
818:
815:
812:
810:
802:
800:
796:
792:
790:
785:
783:
778:
774:
770:
768:
764:
760:
755:
753:
749:
745:
741:
737:
735:
731:
727:
723:
717:
715:
707:
705:
703:
699:
690:
688:
685:
678:
672:
669:
666:
663:
660:
656:
653:
650:
647:
644:
641:
637:
634:
631:
627:
622:
619:
618:
614:
612:
610:
606:
602:
597:
595:
591:
587:
583:
575:
573:
571:
566:
562:
559:, exploiting
558:
553:
546:
542:
539:
535:
532:
528:
527:
526:
520:
515:
513:
511:
507:
504:
500:
496:
492:
488:
484:
476:
474:
471:
467:
463:
459:
454:
452:
448:
447:Fast-flux DNS
444:
442:
436:
434:
430:
426:
425:Srizbi botnet
422:
414:
412:
410:
406:
401:
395:
393:
389:
387:
378:
376:
374:
370:
366:
362:
355:
353:
347:
345:
341:
338:
336:
332:
328:
324:
320:
316:
312:
308:
300:
298:
296:
292:
288:
283:
279:
272:
267:
259:
257:
255:
251:
243:
241:
238:
233:
229:
227:
223:
222:Gameover ZeuS
219:
215:
206:
199:
197:
194:
190:
185:
183:
179:
175:
167:
162:
155:
153:
151:
147:
143:
135:
133:
131:
127:
123:
118:
116:
112:
108:
104:
103:
98:
94:
90:
86:
78:
76:
74:
70:
66:
62:
58:
54:
50:
46:
38:
34:
30:
19:
5278:Cyberwarfare
5023:
4998:Trojan horse
4978:Clickjacking
4880:Trojan horse
4644:
4547:Data masking
4255:
4106:Cyberwarfare
3978:. Retrieved
3963:
3951:. Retrieved
3942:
3933:
3921:. Retrieved
3907:
3895:. Retrieved
3886:
3877:
3865:. Retrieved
3851:
3839:. Retrieved
3825:
3813:. Retrieved
3802:
3792:
3780:. Retrieved
3765:
3753:. Retrieved
3749:the original
3739:
3727:. Retrieved
3723:the original
3713:
3701:. Retrieved
3687:
3675:. Retrieved
3671:the original
3641:. Retrieved
3627:
3615:. Retrieved
3601:
3589:. Retrieved
3575:
3563:. Retrieved
3549:
3537:. Retrieved
3530:the original
3517:
3505:. Retrieved
3496:
3487:
3475:. Retrieved
3461:
3449:. Retrieved
3445:the original
3435:
3423:. Retrieved
3414:
3404:
3392:. Retrieved
3388:the original
3377:
3365:. Retrieved
3361:the original
3351:
3339:. Retrieved
3335:the original
3324:
3312:. Retrieved
3308:the original
3276:
3269:. Retrieved
3241:
3237:
3224:
3212:. Retrieved
3197:
3185:. Retrieved
3170:
3158:. Retrieved
3123:
3119:
3109:
3077:(3): 12–22.
3074:
3070:
3064:
3052:. Retrieved
3041:
3034:
3022:. Retrieved
3013:
3004:
2992:. Retrieved
2974:
2962:. Retrieved
2952:
2940:. Retrieved
2931:
2922:
2903:
2898:
2886:. Retrieved
2874:
2862:
2853:
2844:
2832:. Retrieved
2823:
2813:
2801:. Retrieved
2792:
2783:
2771:. Retrieved
2767:the original
2762:
2753:
2745:
2730:
2718:. Retrieved
2704:
2678:. Retrieved
2668:
2656:. Retrieved
2641:
2629:. Retrieved
2620:
2615:Burt, Jeff.
2610:
2598:. Retrieved
2577:
2565:. Retrieved
2550:
2538:. Retrieved
2534:the original
2524:
2512:. Retrieved
2503:
2494:
2482:. Retrieved
2473:
2463:
2451:. Retrieved
2436:
2428:the original
2421:
2411:
2399:. Retrieved
2385:
2373:. Retrieved
2362:
2352:
2340:. Retrieved
2325:
2313:. Retrieved
2304:
2294:
2282:. Retrieved
2273:Ars Technica
2271:
2261:
2249:. Retrieved
2235:
2223:. Retrieved
2212:
2202:
2190:. Retrieved
2181:
2171:
2159:. Retrieved
2150:
2140:
2113:
2107:
2095:. Retrieved
2091:the original
2081:
2069:. Retrieved
2060:
2050:
2038:. Retrieved
2023:
2003:
1991:. Retrieved
1975:. Springer.
1972:
1962:
1948:(4): 13–16.
1945:
1941:
1916:. Retrieved
1907:
1898:
1871:
1850:. Retrieved
1841:
1831:
1778:
1772:
1760:. Retrieved
1741:
1729:. Retrieved
1715:
1703:. Retrieved
1694:
1685:
1184:2010 (March)
1169:10,500,000+
813:
806:
797:
793:
786:
779:
775:
771:
756:
738:
718:
711:
694:
686:
682:
598:
579:
565:Trojan horse
554:
550:
537:
530:
524:
516:Construction
480:
455:
445:
437:
418:
402:
399:
390:
382:
359:
351:
342:
339:
323:trojan horse
304:
284:
263:
247:
237:IP addresses
234:
230:
214:peer-to-peer
211:
200:Peer-to-peer
186:
171:
145:
139:
136:Architecture
119:
100:
82:
44:
42:
37:Stacheldraht
29:
5130:Macro virus
5115:iOS malware
5089:Web threats
5049:Infostealer
4966:Concealment
4487:Misuse case
4321:Infostealer
4296:Email fraud
4261:Data breach
4096:Cybergeddon
3980:10 November
3867:10 November
3729:10 November
3477:12 November
3271:12 November
3214:10 December
3126:: 100–123.
3054:18 November
3024:11 December
2994:14 November
2942:21 November
2453:22 November
2151:zeltser.com
2040:2 September
1908:Crowdstrike
1762:12 November
1379:2012-07-19
1365:30,000,000
1352:2009 (May)
1226:Onewordsub
1129:12,000,000
846:999,999,999
674:infections.
649:Click fraud
643:E-mail spam
628:fraud czar
615:Common uses
588:as used by
582:hacktivists
521:Traditional
329:and launch
327:e-mail spam
189:IRC botnets
89:smartphones
65:portmanteau
5247:Categories
5154:Protection
5069:Ransomware
5034:Fleeceware
4814:ZeroAccess
4552:Encryption
4428:Web shells
4368:Ransomware
4316:Hacktivism
4079:Cybercrime
3782:6 December
3539:12 January
3341:7 November
3314:30 January
3160:8 December
3141:11336/6772
3084:1805.03409
1788:1804.10848
1678:References
1587:6,000,000
1548:3,000,000
1486:4,500,000
1106:1,000,000
1082:Xarvester
1027:1,300,000
1006:1,500,000
904:6,215,000
462:DynDns.org
405:encryption
250:bot herder
176:networks,
146:bot herder
132:services.
122:rented out
109:, such as
5079:Scareware
5029:Crimeware
4804:Vulcanbot
4694:Conficker
4383:Shellcode
4378:Scareware
4226:Crimeware
4186:Backdoors
3897:7 October
3150:0167-4048
2964:16 August
2908:CiteSeerX
2192:7 October
1563:Chameleon
1526:300,000+
1445:Vulcanbot
1434:Spamnost
1320:Spamthru
1165:Conficker
809:EarthLink
748:BotHunter
714:filtering
611:in 2015.
596:in 2010.
495:Instagram
470:subdomain
466:No-IP.com
433:web pages
369:IP ranges
5268:Spamming
5227:Honeypot
5186:Firewall
4973:Backdoor
4774:Slenfbot
4739:Mariposa
4724:Koobface
4684:Bredolab
4679:BASHLITE
4557:Firewall
4462:Defenses
4388:Spamming
4373:Rootkits
4346:Phishing
4306:Exploits
3974:Archived
3947:Archived
3923:21 March
3917:Archived
3891:Archived
3887:phys.org
3861:Archived
3835:Archived
3815:11 March
3809:Archived
3804:PC World
3776:Archived
3703:23 April
3697:Archived
3677:23 April
3643:23 April
3637:Archived
3617:24 April
3611:Archived
3585:Archived
3559:Archived
3507:24 April
3501:Archived
3497:BBC News
3471:Archived
3419:Archived
3262:Archived
3258:10312905
3208:Archived
3181:Archived
3154:Archived
3101:13677639
3048:Archived
3018:Archived
2988:Archived
2936:Archived
2879:Archived
2834:24 March
2828:Archived
2803:24 March
2797:Archived
2773:24 March
2746:Damballa
2738:Archived
2714:Archived
2690:cite web
2680:30 April
2652:Archived
2625:Archived
2591:Archived
2561:Archived
2508:Archived
2484:10 April
2478:Archived
2447:Archived
2395:Archived
2369:Archived
2364:PC World
2336:Archived
2309:Archived
2278:Archived
2245:Archived
2219:Archived
2186:Archived
2155:Archived
2065:Archived
2034:Archived
2012:Archived
1987:Archived
1918:18 April
1912:Archived
1846:Archived
1823:13756969
1756:Archived
1725:Archived
1721:"botnet"
1699:Archived
1641:See also
1606:380,000
1567:120,000
1540:2015-02
1465:11,000+
1428:250,000
1407:509,000
1387:560,000
1361:BredoLab
1261:Nucrypt
1208:Maazben
1154:Kracken
1148:495,000
1125:Mariposa
1120:2009-Dec
1067:260,000
1047:450,000
985:125,000
965:150,000
943:160,000
924:180,000
886:230,000
835:Aliases
782:honeypot
728:, using
698:phishing
691:Phishing
655:Ad fraud
599:China's
224:and the
182:websites
117:(HTTP).
97:security
85:Internet
79:Overview
49:Internet
5253:Botnets
5084:Spyware
4993:Rootkit
4922:Malware
4860:Malware
4809:Waledac
4764:Rustock
4754:Metulji
4719:Kelihos
4714:Gumblar
4689:Cutwail
4645:Botnets
4398:Spyware
4341:Payload
4336:Malware
4276:Viruses
4256:Botnets
4163:Threats
3953:31 July
3841:11 July
3755:30 July
3591:30 July
3565:3 March
3451:30 July
3425:9 March
3394:30 July
3367:30 July
3187:22 July
2888:16 June
2824:Gizmodo
2720:7 April
2631:31 July
2600:26 July
2540:30 July
2514:31 July
2114:Botnets
1993:28 July
1872:Botnets
1852:28 June
1842:Webroot
1793:Bibcode
1705:28 July
1657:Spambot
1621:Mantis
1522:Kelihos
1462:LowSec
1393:Tedroo
1371:Oficla
1340:Gumblar
1323:12,000
1303:15,000
1282:20,000
1264:20,000
1246:30,000
1229:40,000
1211:50,000
1193:80,000
1189:Waledac
1085:10,000
1002:Cutwail
961:Rustock
862:MaXiTE
702:Verizon
668:Bitcoin
636:Spyware
544:profit.
487:Twitter
415:Domains
335:zombies
178:domains
142:clients
102:malware
73:network
71:" and "
5059:Malbot
5024:Botnet
5019:Adware
4924:topics
4850:Malbot
4794:Torpig
4779:Srizbi
4769:Sality
4744:Mega-D
4734:Lethic
4729:Kraken
4699:Donbot
4669:Asprox
4592:(SIEM)
4569:(HIDS)
4453:Zombie
4190:Bombs
4171:Adware
3256:
3148:
3099:
2910:
2658:27 May
2567:27 May
2401:27 May
2375:27 May
2342:27 May
2315:8 June
2284:27 May
2251:27 May
2225:27 May
2161:27 May
2128:
2097:30 May
2071:27 May
1979:
1886:
1821:
1811:
1731:9 June
1583:Necurs
1544:Ramnit
1413:Ozdok
1403:Mega-D
1299:Asprox
1279:Wopla
1144:Kraken
1102:Sality
1063:Lethic
1043:Srizbi
981:Donbot
920:Torpig
849:100000
679:Market
626:Google
609:GitHub
576:Others
570:packet
497:, the
491:Reddit
483:GitHub
477:Others
365:script
361:Telnet
356:Telnet
315:hacker
295:Mega-D
287:Mega-D
193:server
45:botnet
4799:Virut
4789:TDL-4
4784:Storm
4759:Nitol
4749:Mirai
4704:Festi
4674:Bagle
4664:Akbot
4438:Worms
4433:Wiper
4351:Voice
4199:Logic
3943:ZDNet
3533:(PDF)
3526:(PDF)
3278:said.
3265:(PDF)
3254:S2CID
3234:(PDF)
3097:S2CID
3079:arXiv
2882:(PDF)
2871:(PDF)
2594:(PDF)
2587:(PDF)
2582:FTC.
2423:Wired
2214:Wired
2182:ZDNet
1819:S2CID
1783:arXiv
1624:5000
1616:2022
1611:None
1602:Mirai
1577:2014
1572:None
1532:Hlux
1515:2010
1431:2.25
1424:Festi
1390:39.9
1326:0.35
1249:0.24
1243:Gheg
1217:None
1088:0.15
1073:none
1023:Akbot
1017:2007
939:Storm
882:Bagle
857:2003
826:Name
590:4chan
180:, or
69:robot
4819:Zeus
4709:Grum
4204:Time
4194:Fork
3982:2011
3955:2022
3925:2013
3899:2019
3869:2011
3843:2011
3817:2016
3784:2010
3757:2010
3731:2011
3705:2011
3679:2011
3645:2011
3619:2010
3593:2010
3567:2010
3541:2012
3509:2010
3479:2011
3453:2010
3427:2016
3396:2010
3369:2010
3343:2011
3316:2014
3273:2013
3216:2018
3189:2002
3162:2023
3146:ISSN
3056:2018
3043:2014
3026:2022
2996:2017
2966:2024
2944:2020
2890:2017
2836:2019
2805:2019
2775:2019
2722:2011
2696:link
2682:2016
2660:2017
2633:2022
2602:2020
2569:2017
2542:2010
2516:2022
2486:2015
2455:2013
2403:2017
2377:2017
2344:2017
2317:2017
2286:2017
2253:2017
2227:2017
2194:2017
2163:2017
2126:ISBN
2099:2024
2073:2017
2042:2014
1995:2016
1977:ISBN
1946:2007
1920:2021
1884:ISBN
1854:2015
1809:ISBN
1764:2013
1733:2016
1707:2017
1501:Zeus
1482:TDL4
1468:0.5
1383:Grum
1368:3.6
1285:0.6
1232:1.8
1214:0.5
1196:1.5
988:0.8
889:5.7
840:1999
536:The
499:XMPP
423:and
309:, a
113:and
61:spam
53:bots
4659:3ve
4209:Zip
4019:FBI
3246:doi
3136:hdl
3128:doi
3089:doi
2504:Vox
2118:doi
1950:doi
1876:doi
1801:doi
1410:10
1172:10
1050:60
1009:74
968:30
907:92
852:!a
726:Tor
724:or
722:IRC
538:bot
531:bot
503:Tor
458:DNS
396:P2P
386:IRC
379:IRC
373:SSH
321:or
305:In
124:by
111:IRC
91:or
5249::
4017:,
3945:.
3941:.
3889:.
3885:.
3807:.
3801:.
3653:^
3495:.
3413:.
3285:^
3275:.
3260:.
3252:.
3242:39
3240:.
3236:.
3206:.
3152:.
3144:.
3134:.
3124:45
3122:.
3118:.
3095:.
3087:.
3075:17
3073:.
3016:.
3012:.
2934:.
2930:.
2873:.
2852:.
2826:.
2822:.
2795:.
2791:.
2761:.
2744:,
2692:}}
2688:{{
2650:.
2623:.
2619:.
2589:.
2559:.
2502:.
2476:.
2472:.
2420:.
2393:.
2367:.
2361:.
2334:.
2307:.
2303:.
2276:.
2270:.
2217:.
2211:.
2184:.
2180:.
2153:.
2149:.
2124:.
2063:.
2059:.
1985:.
1944:.
1928:^
1910:.
1906:.
1882:.
1862:^
1844:.
1840:.
1817:.
1807:.
1799:.
1791:.
1754:.
1750:.
1723:.
1693:.
1529:4
1267:5
1151:9
1070:2
946:3
868:0
843:!a
716:.
493:,
489:,
485:,
464:,
443:.
317:,
228:.
43:A
4914:e
4907:t
4900:v
4637:e
4630:t
4623:v
4047:e
4040:t
4033:v
3984:.
3957:.
3927:.
3901:.
3871:.
3845:.
3819:.
3786:.
3759:.
3733:.
3707:.
3681:.
3647:.
3621:.
3595:.
3569:.
3543:.
3511:.
3481:.
3455:.
3429:.
3398:.
3371:.
3345:.
3318:.
3248::
3218:.
3191:.
3164:.
3138::
3130::
3103:.
3091::
3081::
3058:.
3028:.
2998:.
2968:.
2946:.
2916:.
2892:.
2856:.
2838:.
2807:.
2777:.
2724:.
2698:)
2684:.
2662:.
2635:.
2604:.
2571:.
2544:.
2518:.
2488:.
2457:.
2405:.
2379:.
2346:.
2319:.
2288:.
2255:.
2229:.
2196:.
2165:.
2134:.
2120::
2101:.
2075:.
2044:.
1997:.
1956:.
1952::
1922:.
1892:.
1878::
1856:.
1825:.
1803::
1795::
1785::
1766:.
1735:.
1709:.
1314:0
533:.
277::
270::
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.