25:
337:
613:: the object that is passed from the source to the Command/Action object, to the Target object to the code that does the work. Each button click or shortcut key results in a new command/event object. Some implementations add more information to the command/event object as it is being passed from one object (e.g.
631:: the actual code that does the copying, pasting, moving, etc. In some implementations the handler code is part of the command/action object. In other implementations the code is part of the Receiver/Target Object, and in yet other implementations the handler code is kept separate from the other objects.
515:
may refer to a single (move up) command that should be executed twice, or it may refer to two commands, each of which happens to do the same thing (move up). If the former command is added twice to an undo stack, both items on the stack refer to the same command instance. This may be appropriate when
387:
If all user actions are represented by command objects, a program can record a sequence of actions simply by keeping a list of the command objects as they are executed. It can then "play back" the same actions by executing the same command objects again in sequence. If the program embeds a scripting
171:
Using command objects makes it easier to construct general components that need to delegate, sequence or execute method calls at a time of their choosing without the need to know the class of the method or the method parameters. Using an invoker object allows bookkeeping about command executions to
478:
Often a wizard presents several pages of configuration for a single action that happens only when the user clicks the "Finish" button on the last page. In these cases, a natural way to separate user interface code from application code is to implement the wizard using a command object. The command
584:
object), which knows about shortcut keys, button images, command text, etc. related to the command. A source or invoker object calls the
Command or Action object's execute or performAction method. The Command/Action object notifies the appropriate source/invoker objects when the availability of a
637:: an object that puts command/event objects on an undo stack or redo stack, or that holds on to command/event objects until other objects are ready to act on them, or that routes the command/event objects to the appropriate receiver/target object or handler code.
649:(WPF), introduces routed commands, which combine the command pattern with event processing. As a result, the command object no longer contains a reference to the target object nor a reference to the application code. Instead, invoking the command object's
528:. On the other hand, if the latter commands are added to an undo stack, the stack refers to two separate objects. This may be appropriate when each object on the stack must contain information that allows the command to be undone. For example, to undo a
451:
method that adds a work item to an internal queue of tasks waiting to be done. It maintains a pool of threads that execute commands from the queue. The items in the queue are command objects. Typically these objects implement a common interface such as
410:
If all user actions in a program are implemented as command objects, the program can keep a stack of the most recently executed commands. When the user wants to undo a command, the program simply pops the most recent command object and executes its
167:
decides which receiver objects it assigns to the command objects, and which commands it assigns to the invoker. The client decides which commands to execute at which points. To execute a command, it passes the command object to the invoker object.
1346:
The first published mention of using a
Command class to implement interactive systems seems to be a 1985 article by Henry Lieberman. The first published description of a (multiple-level) undo-redo mechanism, using a Command class with
230:
This enables one to configure a class with a command object that is used to perform a request. The class is no longer coupled to a particular request and has no knowledge (is independent) of how the request is carried out.
400:
Using languages such as Java where code can be streamed/slurped from one location to another via URLClassloaders and
Codebases the commands can enable new behavior to be delivered to remote locations (EJB Command, Master
470:). For example, if two database tables that refer to each other must be updated, and the second update fails, the transaction can be rolled back, so that the first table does not now contain an invalid reference.
617:) to another (e.g. document section). Other implementations put command/event objects in other event objects (like a box inside a bigger box) as they move along the line, to avoid naming conflicts. (See also
172:
be conveniently performed, as well as implementing different modes for commands, which are managed by the invoker object, without the need for the client to be aware of the existence of bookkeeping or modes.
465:
Similar to undo, a database engine or software installer may keep a list of operations that have been or will be performed. Should one of them fail, all others can be reversed or discarded (usually called
479:
object is created when the wizard is first displayed. Each wizard page stores its GUI changes in the command object, so the object is populated as the user progresses. "Finish" simply triggers a call to
215:
Implementing (hard-wiring) a request directly into a class is inflexible because it couples the class to a particular request at compile-time, which makes it impossible to specify a request at run-time.
135:
and invokes a method of the receiver. Values for parameters of the receiver method are stored in the command. The receiver object to execute these methods is also stored in the command object by
427:
Where the commands are written as tasks to a shared resource and executed by many threads in parallel (possibly on remote machines; this variant is often referred to as the Master/Worker pattern)
108:
all information needed to perform an action or trigger an event at a later time. This information includes the method name, the object that owns the method and values for the method parameters.
155:
object knows how to execute a command, and optionally does bookkeeping about the command execution. The invoker does not know anything about a concrete command, it knows only about the command
201:
that describe how to solve recurring design problems to design flexible and reusable object-oriented software, that is, objects that are easier to implement, change, test, and reuse.
456:
that allows the thread pool to execute the command even though the thread pool class itself was written without any knowledge of the specific tasks for which it would be used.
54:
439:
method, the program can easily estimate the total duration. It can show a progress bar that meaningfully reflects how close the program is to completing all the tasks.
374:
may have an associated icon, keyboard shortcut, tooltip text, and so on. A toolbar button or menu item component may be completely initialized using only the
248:
1546:
559:
method has been invoked, but that does not necessarily mean that the application code has run. That occurs only after some further event processing.
421:
It is possible to send whole command objects across the network to be executed on the other machines, for example player actions in computer games.
585:
command/action has changed. This allows buttons and menu items to become inactive (grayed out) when a command/action cannot be executed/performed.
1519:
1360:
492:
The terminology used to describe command pattern implementations is not consistent and can therefore be confusing. This is the result of
2071:
607:
action. On the other hand, if the code is defined by the command object itself, the target object will be a different object entirely.
2179:
2096:
1397:
101:
76:
1869:
591:: the object that is about to be copied, pasted, moved, etc. The receiver object owns the method that is called by the command's
2044:
1668:
618:
552:
537:
184:
1852:
1762:
1320:
1892:
208:
Coupling the invoker of a request to a particular request should be avoided. That is, hard-wired requests should be avoided.
1862:
1857:
1539:
366:
1413:
37:
2137:
1975:
187:. Specifically, the invoker object is a higher-order function of which the command object is a first-class argument.
90:
536:
command must be undone. Note that using a separate object for each invocation of a command is also an example of the
47:
41:
33:
1752:
1300:
1960:
1955:
1782:
1070:// knows how to perform the operations associated with carrying out a request. Any class may serve as a Receiver.
298:
256:
58:
2000:
1965:
1932:
1582:
1532:
381:
1797:
1902:
1874:
1812:
1777:
1713:
1555:
1335:
1330:
517:
1879:
1807:
1757:
1592:
247:
2158:
2061:
1907:
1887:
1832:
180:
226:
A class delegates a request to a command object instead of implementing a particular request directly.
1970:
1927:
1922:
1912:
1822:
459:
435:
Suppose a program has a sequence of commands that it executes in order. If each command object has a
176:
2010:
1995:
1990:
1847:
1732:
1678:
595:
method. The receiver is typically also the target object. For example, if the receiver object is a
2132:
2111:
2020:
1917:
1767:
1660:
1612:
1574:
532:
command, the object may contain a copy of the deleted text so that it can be re-inserted, if the
136:
105:
98:
1802:
1645:
1635:
1630:
1602:
1597:
1393:
1389:
1382:
473:
361:
2101:
1842:
1787:
1708:
1698:
1688:
1683:
1475:
661:
object that identifies the target and the application code, which is executed at that point.
301:
2091:
2037:
2015:
1792:
1747:
1718:
1693:
1620:
1587:
1563:
1310:
197:
574:: the button, toolbar button, or menu item clicked, the shortcut key pressed by the user.
646:
2076:
1937:
1640:
1625:
1493:
1356:
1325:
547:
is also ambiguous. It may refer to running the code identified by the command object's
2173:
1897:
1742:
1703:
1650:
1315:
1305:
500:, and implementations that may obscure the original pattern by going well beyond it.
395:
259:
211:
It should be possible to configure an object (that invokes a request) with a request.
2153:
2116:
2005:
1980:
1772:
430:
370:
is a command object. In addition to the ability to perform the desired command, an
354:
2106:
2081:
2066:
1985:
1817:
1295:
672:
This C++14 implementation is based on the pre C++98 implementation in the book.
442:
1466:
Lieberman, Henry (1985). "There's more to menu systems than meets the screen".
1442:
1421:
336:
986:// implements execute by invoking the corresponding operation(s) on Receiver.
2086:
493:
1524:
1479:
565:
497:
175:
The central ideas of this design pattern closely mirror the semantics of
657:
that during the event's tunneling or bubbling may encounter a so-called
251:
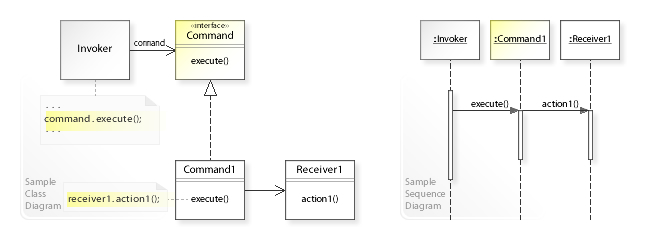
A sample UML class and sequence diagram for the
Command design pattern.
159:. Invoker object(s), command objects and receiver objects are held by a
1355:
methods, and a history list, appears to be the first (1988) edition of
516:
a command can always be undone the same way (e.g. move down). Both the
358:
1514:
635:
Command
Manager, Undo Manager, Scheduler, Queue, Dispatcher, Invoker
1414:"The Command design pattern - Problem, Solution, and Applicability"
219:
Using the command design pattern describes the following solution:
642:
Implementations that go well beyond the original command pattern.
335:
246:
1380:
Erich Gamma; Richard Helm; Ralph
Johnson; John Vlissides (1994).
555:
a command is considered to have been executed when the command's
447:
A typical, general-purpose thread pool class might have a public
195:
The command design pattern is one of the twenty-three well-known
405:
392:
method, and user actions can then be easily recorded as scripts.
1528:
1520:
Java Tip 68: Learn how to implement the
Command pattern in Java
1384:
Design
Patterns: Elements of Reusable Object-Oriented Software
18:
836:// defines a binding between a Receiver object and an action.
603:, then one would expect that the cursor is the target of the
223:
Define separate (command) objects that encapsulate a request.
204:
Using the command design pattern can solve these problems:
1443:"The Command design pattern - Structure and Collaboration"
111:
Four terms always associated with the command pattern are
266:
class doesn't implement a request directly. Instead,
704:// declares an interface for executing an operation.
611:
Command Object, routed event arguments, event object
578:
Command Object, Routed
Command Object, Action Object
2146:
2125:
2054:
2029:
1946:
1831:
1731:
1659:
1611:
1573:
1562:
234:See also the UML class and sequence diagram below.
1381:
290:interface by performing an action on a receiver (
282:independent of how the request is performed. The
46:but its sources remain unclear because it lacks
1540:
580:: a singleton object (e.g. there is only one
8:
388:engine, each command object can implement a
1127:// The smart pointers prevent memory leaks.
1570:
1547:
1533:
1525:
77:Learn how and when to remove this message
483:. This way, the command class will work.
1372:
1498:Object-Oriented Software Construction
1361:Object-oriented Software Construction
304:shows the run-time interactions: The
7:
524:use this interpretation of the term
328:object, which performs the request.
340:UML diagram of the command pattern
14:
551:method. However, in Microsoft's
274:interface to perform a request (
185:functional programming languages
23:
2045:Enterprise Integration Patterns
653:command results in a so-called
647:Windows Presentation Foundation
619:chain of responsibility pattern
553:Windows Presentation Foundation
538:chain of responsibility pattern
1500:(1st ed.). Prentice-Hall.
1468:ACM SIGGRAPH Computer Graphics
243:UML class and sequence diagram
104:in which an object is used to
1:
143:then does the work when the
2138:Portland Pattern Repository
1388:. Addison Wesley. pp.
511:is ambiguous. For example,
91:object-oriented programming
2196:
627:ExecutedRoutedEventHandler
350:GUI buttons and menu items
599:and the method is called
521:
16:Behavioral design pattern
2180:Software design patterns
1763:Event-based asynchronous
1556:Software design patterns
1275:
674:
32:This article includes a
1669:Chain of responsibility
1331:Software design pattern
589:Receiver, Target Object
572:Client, Source, Invoker
61:more precise citations.
1808:Scheduled-task pattern
1758:Double-checked locking
1273:The program output is
437:getEstimatedDuration()
341:
252:
181:higher-order functions
2159:Architectural pattern
2062:Christopher Alexander
1480:10.1145/325165.325235
1336:GoF – Design Patterns
1321:Model–view–controller
1097:"MyClass::action
655:Executed Routed Event
339:
286:class implements the
250:
177:first-class functions
1971:Dependency injection
1928:Inversion of control
1923:Data transfer object
1823:Thread-local storage
1976:Intercepting filter
424:Parallel processing
292:receiver1.action1()
278:), which makes the
198:GoF design patterns
131:object knows about
2133:The Hillside Group
1918:Data access object
1768:Guarded suspension
1753:Binding properties
806:// ConcreteCommand
629:, method, function
522:Java example below
454:java.lang.Runnable
342:
253:
34:list of references
2167:
2166:
1961:Business delegate
1893:Publish–subscribe
1727:
1726:
332:UML class diagram
276:command.execute()
87:
86:
79:
2187:
1966:Composite entity
1843:Front controller
1583:Abstract factory
1571:
1549:
1542:
1535:
1526:
1502:
1501:
1490:
1484:
1483:
1463:
1457:
1456:
1454:
1453:
1439:
1433:
1432:
1430:
1429:
1420:. Archived from
1410:
1404:
1403:
1387:
1377:
1363:, section 12.2.
1285:
1282:
1279:
1269:
1266:
1263:
1260:
1257:
1254:
1251:
1248:
1245:
1242:
1239:
1236:
1233:
1230:
1227:
1224:
1221:
1218:
1215:
1212:
1209:
1206:
1203:
1200:
1197:
1194:
1191:
1188:
1185:
1182:
1179:
1176:
1173:
1170:
1167:
1164:
1161:
1158:
1155:
1152:
1149:
1146:
1143:
1140:
1137:
1134:
1131:
1128:
1125:
1122:
1119:
1116:
1113:
1110:
1107:
1104:
1101:
1098:
1095:
1092:
1089:
1086:
1083:
1080:
1077:
1074:
1071:
1068:
1065:
1062:
1059:
1056:
1053:
1050:
1047:
1044:
1041:
1038:
1035:
1032:
1029:
1026:
1023:
1020:
1017:
1014:
1011:
1008:
1005:
1002:
999:
996:
993:
990:
987:
984:
981:
978:
975:
972:
969:
966:
963:
960:
957:
954:
951:
948:
945:
944:// rule of three
942:
939:
936:
933:
930:
927:
924:
921:
918:
915:
912:
909:
906:
903:
900:
897:
894:
891:
888:
885:
882:
879:
876:
873:
870:
867:
864:
861:
858:
855:
852:
849:
846:
843:
840:
837:
834:
831:
828:
825:
822:
819:
816:
813:
810:
807:
804:
801:
798:
795:
792:
789:
786:
783:
780:
777:
774:
771:
768:
765:
762:
759:
756:
753:
750:
747:
744:
741:
738:
735:
732:
729:
726:
723:
720:
717:
714:
711:
708:
705:
702:
699:
696:
693:
690:
687:
684:
681:
680:<iostream>
678:
628:
616:
606:
602:
583:
534:delete selection
530:delete selection
513:move up, move up
482:
455:
450:
438:
414:
391:
377:
373:
369:
364:programming, an
327:
323:
319:
315:
311:
307:
302:sequence diagram
293:
289:
285:
281:
277:
273:
269:
265:
146:
82:
75:
71:
68:
62:
57:this article by
48:inline citations
27:
26:
19:
2195:
2194:
2190:
2189:
2188:
2186:
2185:
2184:
2170:
2169:
2168:
2163:
2142:
2121:
2112:Douglas Schmidt
2092:Ward Cunningham
2050:
2038:Design Patterns
2025:
2016:Method chaining
1948:
1942:
1903:Service locator
1834:
1827:
1798:Read–write lock
1734:
1723:
1714:Template method
1655:
1607:
1565:
1558:
1553:
1515:Command Pattern
1511:
1506:
1505:
1494:Meyer, Bertrand
1492:
1491:
1487:
1465:
1464:
1460:
1451:
1449:
1441:
1440:
1436:
1427:
1425:
1412:
1411:
1407:
1400:
1379:
1378:
1374:
1369:
1344:
1311:Function object
1292:
1287:
1286:
1283:
1280:
1277:
1271:
1270:
1267:
1264:
1261:
1258:
1255:
1252:
1249:
1246:
1243:
1240:
1237:
1234:
1231:
1228:
1225:
1222:
1219:
1216:
1213:
1210:
1207:
1204:
1201:
1198:
1195:
1192:
1189:
1186:
1183:
1180:
1177:
1174:
1171:
1168:
1165:
1162:
1159:
1156:
1153:
1150:
1147:
1144:
1141:
1138:
1135:
1132:
1129:
1126:
1123:
1120:
1117:
1114:
1111:
1108:
1105:
1102:
1099:
1096:
1093:
1090:
1087:
1084:
1081:
1078:
1075:
1072:
1069:
1066:
1063:
1060:
1057:
1054:
1051:
1048:
1045:
1042:
1039:
1036:
1033:
1030:
1027:
1024:
1021:
1018:
1015:
1012:
1009:
1006:
1003:
1000:
997:
994:
991:
988:
985:
982:
979:
976:
973:
970:
967:
964:
961:
958:
955:
952:
949:
946:
943:
940:
937:
934:
931:
928:
925:
922:
919:
916:
913:
910:
907:
904:
901:
898:
895:
892:
889:
886:
883:
880:
877:
874:
871:
868:
865:
862:
859:
856:
853:
850:
847:
844:
841:
838:
835:
832:
829:
826:
823:
820:
817:
814:
811:
808:
805:
802:
799:
796:
793:
790:
787:
784:
781:
778:
775:
772:
769:
766:
763:
760:
757:
754:
751:
748:
745:
742:
739:
736:
733:
730:
727:
724:
721:
718:
715:
712:
709:
706:
703:
700:
697:
694:
691:
688:
685:
682:
679:
676:
670:
626:
614:
604:
600:
581:
490:
480:
453:
448:
436:
412:
389:
375:
371:
365:
347:
334:
325:
321:
317:
313:
309:
305:
291:
287:
283:
279:
275:
271:
267:
263:
245:
240:
193:
144:
95:command pattern
83:
72:
66:
63:
52:
38:related reading
28:
24:
17:
12:
11:
5:
2193:
2191:
2183:
2182:
2172:
2171:
2165:
2164:
2162:
2161:
2156:
2150:
2148:
2144:
2143:
2141:
2140:
2135:
2129:
2127:
2123:
2122:
2120:
2119:
2114:
2109:
2104:
2099:
2094:
2089:
2084:
2079:
2077:John Vlissides
2074:
2069:
2064:
2058:
2056:
2052:
2051:
2049:
2048:
2041:
2033:
2031:
2027:
2026:
2024:
2023:
2018:
2013:
2008:
2003:
1998:
1993:
1988:
1983:
1978:
1973:
1968:
1963:
1958:
1952:
1950:
1944:
1943:
1941:
1940:
1935:
1930:
1925:
1920:
1915:
1910:
1905:
1900:
1895:
1890:
1885:
1877:
1872:
1867:
1866:
1865:
1860:
1850:
1845:
1839:
1837:
1829:
1828:
1826:
1825:
1820:
1815:
1810:
1805:
1800:
1795:
1790:
1785:
1780:
1775:
1770:
1765:
1760:
1755:
1750:
1745:
1739:
1737:
1729:
1728:
1725:
1724:
1722:
1721:
1716:
1711:
1706:
1701:
1696:
1691:
1686:
1681:
1676:
1671:
1665:
1663:
1657:
1656:
1654:
1653:
1648:
1643:
1638:
1633:
1628:
1623:
1617:
1615:
1609:
1608:
1606:
1605:
1600:
1595:
1593:Factory method
1590:
1585:
1579:
1577:
1568:
1560:
1559:
1554:
1552:
1551:
1544:
1537:
1529:
1523:
1522:
1517:
1510:
1509:External links
1507:
1504:
1503:
1485:
1474:(3): 181–189.
1458:
1434:
1405:
1398:
1371:
1370:
1368:
1365:
1357:Bertrand Meyer
1343:
1340:
1339:
1338:
1333:
1328:
1326:Priority queue
1323:
1318:
1313:
1308:
1303:
1298:
1291:
1288:
1276:
686:<memory>
675:
669:
666:
665:
664:
663:
662:
640:
639:
638:
632:
622:
608:
586:
575:
562:
561:
560:
541:
489:
486:
485:
484:
476:
471:
463:
457:
445:
440:
433:
428:
425:
422:
419:
416:
408:
402:
398:
393:
385:
379:
351:
346:
343:
333:
330:
270:refers to the
244:
241:
239:
236:
228:
227:
224:
213:
212:
209:
192:
189:
151:is called. An
102:design pattern
85:
84:
42:external links
31:
29:
22:
15:
13:
10:
9:
6:
4:
3:
2:
2192:
2181:
2178:
2177:
2175:
2160:
2157:
2155:
2152:
2151:
2149:
2145:
2139:
2136:
2134:
2131:
2130:
2128:
2124:
2118:
2115:
2113:
2110:
2108:
2105:
2103:
2102:Robert Martin
2100:
2098:
2097:Martin Fowler
2095:
2093:
2090:
2088:
2085:
2083:
2080:
2078:
2075:
2073:
2072:Ralph Johnson
2070:
2068:
2065:
2063:
2060:
2059:
2057:
2053:
2047:
2046:
2042:
2040:
2039:
2035:
2034:
2032:
2028:
2022:
2019:
2017:
2014:
2012:
2009:
2007:
2004:
2002:
1999:
1997:
1994:
1992:
1989:
1987:
1984:
1982:
1979:
1977:
1974:
1972:
1969:
1967:
1964:
1962:
1959:
1957:
1954:
1953:
1951:
1945:
1939:
1936:
1934:
1931:
1929:
1926:
1924:
1921:
1919:
1916:
1914:
1911:
1909:
1908:Active record
1906:
1904:
1901:
1899:
1898:Naked objects
1896:
1894:
1891:
1889:
1888:Specification
1886:
1884:
1882:
1878:
1876:
1873:
1871:
1868:
1864:
1861:
1859:
1856:
1855:
1854:
1851:
1849:
1846:
1844:
1841:
1840:
1838:
1836:
1833:Architectural
1830:
1824:
1821:
1819:
1816:
1814:
1811:
1809:
1806:
1804:
1801:
1799:
1796:
1794:
1791:
1789:
1786:
1784:
1781:
1779:
1776:
1774:
1771:
1769:
1766:
1764:
1761:
1759:
1756:
1754:
1751:
1749:
1746:
1744:
1743:Active object
1741:
1740:
1738:
1736:
1730:
1720:
1717:
1715:
1712:
1710:
1707:
1705:
1702:
1700:
1697:
1695:
1692:
1690:
1687:
1685:
1682:
1680:
1677:
1675:
1672:
1670:
1667:
1666:
1664:
1662:
1658:
1652:
1649:
1647:
1644:
1642:
1639:
1637:
1634:
1632:
1629:
1627:
1624:
1622:
1619:
1618:
1616:
1614:
1610:
1604:
1601:
1599:
1596:
1594:
1591:
1589:
1586:
1584:
1581:
1580:
1578:
1576:
1572:
1569:
1567:
1561:
1557:
1550:
1545:
1543:
1538:
1536:
1531:
1530:
1527:
1521:
1518:
1516:
1513:
1512:
1508:
1499:
1495:
1489:
1486:
1481:
1477:
1473:
1469:
1462:
1459:
1448:
1447:w3sDesign.com
1444:
1438:
1435:
1424:on 2020-09-23
1423:
1419:
1418:w3sDesign.com
1415:
1409:
1406:
1401:
1399:0-201-63361-2
1395:
1391:
1386:
1385:
1376:
1373:
1366:
1364:
1362:
1358:
1354:
1350:
1341:
1337:
1334:
1332:
1329:
1327:
1324:
1322:
1319:
1317:
1316:Job scheduler
1314:
1312:
1309:
1307:
1306:Command queue
1304:
1302:
1299:
1297:
1294:
1293:
1289:
1274:
1214:SimpleCommand
968:SimpleCommand
950:SimpleCommand
926:SimpleCommand
917:SimpleCommand
839:SimpleCommand
791:SimpleCommand
673:
667:
660:
656:
652:
648:
644:
643:
641:
636:
633:
630:
623:
620:
612:
609:
598:
594:
590:
587:
579:
576:
573:
570:
569:
567:
564:Synonyms and
563:
558:
554:
550:
546:
542:
539:
535:
531:
527:
523:
519:
514:
510:
506:
505:
503:
502:
501:
499:
496:, the use of
495:
487:
477:
475:
472:
469:
464:
461:
460:Transactional
458:
446:
444:
441:
434:
432:
431:Progress bars
429:
426:
423:
420:
417:
409:
407:
403:
399:
397:
394:
386:
383:
380:
368:
363:
360:
356:
352:
349:
348:
344:
338:
331:
329:
308:object calls
303:
300:
295:
261:
260:class diagram
258:
255:In the above
249:
242:
237:
235:
232:
225:
222:
221:
220:
217:
210:
207:
206:
205:
202:
200:
199:
190:
188:
186:
182:
178:
173:
169:
166:
162:
158:
154:
150:
142:
138:
134:
130:
126:
122:
118:
114:
109:
107:
103:
100:
96:
92:
81:
78:
70:
67:December 2012
60:
56:
50:
49:
43:
39:
35:
30:
21:
20:
2154:Anti-pattern
2117:Linda Rising
2043:
2036:
1981:Lazy loading
1913:Identity map
1880:
1673:
1564:Gang of Four
1497:
1488:
1471:
1467:
1461:
1450:. Retrieved
1446:
1437:
1426:. Retrieved
1422:the original
1417:
1408:
1383:
1375:
1352:
1348:
1345:
1272:
671:
658:
654:
650:
645:Microsoft's
634:
624:
610:
596:
592:
588:
577:
571:
556:
548:
544:
533:
529:
525:
518:Gang of Four
512:
508:
491:
467:
443:Thread pools
404:Multi-level
296:
254:
233:
229:
218:
214:
203:
196:
194:
174:
170:
164:
163:object. The
160:
156:
152:
148:
140:
132:
128:
124:
120:
116:
112:
110:
94:
88:
73:
64:
53:Please help
45:
2126:Communities
2107:Jim Coplien
2082:Grady Booch
2067:Erich Gamma
2011:Type tunnel
1996:Object pool
1991:Null object
1986:Mock object
1848:Interceptor
1818:Thread pool
1733:Concurrency
1679:Interpreter
1296:Batch queue
1208:make_unique
1160:make_shared
1061:// Receiver
615:CopyCommand
582:CopyCommand
504:Ambiguity.
488:Terminology
396:Mobile code
137:aggregation
106:encapsulate
59:introducing
2021:Delegation
1956:Blackboard
1661:Behavioral
1613:Structural
1575:Creational
1452:2017-08-12
1428:2017-08-12
1367:References
1184:unique_ptr
1136:shared_ptr
851:shared_ptr
418:Networking
390:toScript()
147:method in
99:behavioral
2087:Kent Beck
1813:Semaphore
1803:Scheduler
1646:Flyweight
1636:Decorator
1631:Composite
1603:Singleton
1598:Prototype
887:receiver_
863:receiver_
749:protected
625:Handler,
543:The term
507:The term
494:ambiguity
481:execute()
449:addTask()
384:recording
326:Receiver1
322:action1()
310:execute()
238:Structure
157:interface
145:execute()
2174:Category
2147:See also
1949:patterns
1835:patterns
1788:Proactor
1735:patterns
1709:Strategy
1699:Observer
1689:Mediator
1684:Iterator
1566:patterns
1496:(1988).
1359:'s book
1290:See also
1232:receiver
1148:receiver
1094:<<
1034:receiver
1028:Receiver
1007:receiver
956:operator
881:receiver
857:Receiver
824:Receiver
782:Receiver
779:typename
773:template
683:#include
677:#include
566:homonyms
520:and the
498:synonyms
468:rollback
462:behavior
401:Worker).
318:Command1
316:object.
314:Command1
284:Command1
191:Overview
141:receiver
133:receiver
117:receiver
2001:Servant
1933:Model 2
1793:Reactor
1783:Monitor
1748:Balking
1719:Visitor
1694:Memento
1674:Command
1621:Adapter
1588:Builder
1349:execute
1342:History
1301:Closure
1278:MyClass
1262:execute
1256:command
1241:MyClass
1220:MyClass
1196:command
1190:Command
1166:MyClass
1142:MyClass
1055:MyClass
1022:private
995:execute
989:virtual
905:action_
872:action_
815:typedef
800:Command
764:default
755:Command
743:default
734:Command
728:virtual
713:execute
707:virtual
692:Command
668:Example
659:binding
651:execute
593:execute
557:execute
549:execute
545:execute
526:command
509:command
474:Wizards
415:method.
378:object.
359:Borland
306:Invoker
288:Command
280:Invoker
272:Command
268:Invoker
264:Invoker
153:invoker
149:command
129:command
121:invoker
113:command
55:improve
2055:People
1938:Broker
1641:Facade
1626:Bridge
1396:
1284:action
1253:// ...
1247:action
1175:// ...
1103:"
1076:action
1064:public
1043:action
1040:Action
1013:action
1010:->*
980:delete
938:delete
899:action
869:Action
830:Action
809:public
797:public
698:public
605:moveUp
601:moveUp
597:cursor
413:undo()
376:Action
372:Action
367:Action
362:Delphi
320:calls
262:, the
165:client
161:client
139:. The
125:client
93:, the
2030:Books
1947:Other
1883:-tier
1704:State
1651:Proxy
1390:233ff
1259:->
1238:&
1052:class
971:&
965:const
953:&
947:const
929:&
923:const
788:class
689:class
382:Macro
355:Swing
324:on a
312:on a
97:is a
40:, or
2006:Twin
1863:MVVM
1778:Lock
1773:Join
1394:ISBN
1353:undo
1351:and
1226:>
1223:>
1217:<
1211:<
1193:>
1187:<
1169:>
1163:<
1145:>
1139:<
1118:main
1091:cout
1073:void
1016:)();
992:void
896:()),
860:>
854:<
833:)();
818:void
785:>
776:<
710:void
406:undo
357:and
345:Uses
297:The
179:and
127:. A
123:and
1875:ECS
1870:ADR
1858:MVP
1853:MVC
1476:doi
1265:();
1202:std
1178:std
1172:();
1154:std
1130:std
1115:int
1085:std
893:get
845:std
827:::*
353:In
299:UML
294:).
257:UML
183:in
89:In
2176::
1472:19
1470:.
1445:.
1416:.
1392:.
1281:::
1250:);
1244:::
1205:::
1181:::
1157:::
1133:::
1121:()
1112:};
1100:\n
1088:::
1079:()
1049:};
998:()
848:::
770:};
758:()
737:()
716:()
621:.)
568:.
119:,
115:,
44:,
36:,
1881:n
1548:e
1541:t
1534:v
1482:.
1478::
1455:.
1431:.
1402:.
1268:}
1235:,
1229:(
1199:=
1151:=
1124:{
1109:}
1106:;
1082:{
1067::
1058:{
1046:;
1037:;
1031:*
1025::
1019:}
1004:(
1001:{
983:;
977:=
974:)
962:(
959:=
941:;
935:=
932:)
920:(
914:}
911:{
908:)
902:(
890:.
884:(
878::
875:)
866:,
842:(
821:(
812::
803:{
794::
767:;
761:=
752::
746:;
740:=
731:~
725:;
722:0
719:=
701::
695:{
540:.
80:)
74:(
69:)
65:(
51:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.