679:
706:) as part of the authentication process. Because only Windows can detect this key combination, requiring this additional security measure would prevent spoofed dialogs from behaving the same way as a legitimate dialog. For example, a spoofed dialog might not ask the user to press Ctrl+Alt+Del, and the user could realize that the dialog was fake. Or, when the user did press Ctrl+Alt+Del, the user would be brought to the screen Ctrl+Alt+Del normally brings them to instead of a UAC confirmation dialog. Thus the user could tell whether the dialog was an attempt to trick them into providing their password to a piece of malicious software.
807:, when logged in as a standard user, the user must enter an administrator's name and password each time they need to grant an application elevated privileges; but when logged in as a member of the Administrators group, they (by default) simply confirm or deny, instead of re-entering their password each time (though that is an option). While the default approach is simpler, it is also less secure, since if the user physically walks away from the computer without locking it, another person could walk up and have administrator privileges over the system.
291:
941:
827:
545:
256:
120:
78:(and its descendants), CP/M-80, and all Mac operating systems prior to Mac OS X, had only one category of user who was allowed to do anything. With separate execution contexts it is possible for multiple users to store private files, for multiple users to use a computer at the same time, to protect the system against malicious users, and to protect the system against malicious programs. The first multi-user secure system was
195:
438:
481:
229:
987:, which contains a list of users and the privileged applications and actions that those users are permitted to use. The grammar of the sudoers file is intended to be flexible enough to cover many different scenarios, such as placing restrictions on command-line parameters. For example, a user can be granted access to change anybody's password except for the root account, as follows:
380:
24:
409:
1010:. When an application is started, the manifest is looked at for information about what security requirements the application has. For example, this XML fragment will indicate that the application will require administrator access, but will not require unfettered access to other parts of the user desktop outside the application:
882:
programs that run in that tty (for sudo) or all programs not running in a terminal (for gksudo and kdesu) prefixed by either of those commands before the timeout receive administrator privileges. Security-conscious users may remove the temporary administrator privileges upon completing the tasks requiring them by using the
318:
1058:
UAC also makes a distinction between elevation requests from a signed executable and an unsigned executable; and if the former, whether or not the publisher is 'Windows Vista'. The color, icon, and wording of the prompts are different in each case: for example, attempting to convey a greater sense
674:
dialogs that look like legitimate security confirmation requests. If the user were to input credentials into a fake dialog, thinking the dialog was legitimate, the malicious software would then know the user's password. If the Secure
Desktop or similar feature were disabled, the malicious software
656:
to record the administrator's password; or, in the case of UAC if running as an administrator, spoofing a mouse click on the "Allow" button. For this reason, voice recognition is also prohibited from interacting with the dialog. Note that since gksu password prompt runs without special privileges,
598:
run in the terminal, where they are vulnerable to spoofed input. Of course, if the user was not running a multitasking environment (i.e. a single user in the shell only), this would not be a problem. Terminal windows are usually rendered as ordinary windows to the user, therefore on an intelligent
918:
However, there are varying levels of authentication, known as Rights. The right that is requested can be shown by expanding the triangle next to "details", underneath the password. Normally, applications use system.privilege.admin, but another may be used, such as a lower right for security, or a
975:
In the case of user interfaces such as the
Control Panel in Microsoft Windows, and the Preferences panels in Mac OS X, the exact privilege requirements are hard-coded into the system so that the user is presented with an authorization dialog at an appropriate time (for example, before displaying
875:
do not ask the user to re-enter their password every time it is called to elevate a program. Rather, the user is asked for their password once at the start. If the user has not used their administrative privileges for a certain period of time (sudo's default is 5 minutes), the user is once again
971:
In order for an operating system to know when to prompt the user for authorization, an application or action needs to identify itself as requiring elevated privileges. While it is technically possible for the user to be prompted at the exact moment that an operation requiring such privileges is
881:
sudo's approach is a trade-off between security and usability. On one hand, a user only has to enter their password once to perform a series of administrator tasks, rather than having to enter their password for each task. But at the same time, the surface area for attack is larger because all
761:
use a simpler approach. With these programs, the user is pre-configured to be granted access to specific administrative tasks, but must explicitly authorize applications to run with those privileges. The user enters their own password instead of that of the superuser or some another
1053:. Heuristic scanning is also used, primarily for backwards compatibility. One example of this is looking at the executable's file name; if it contains the word "Setup", it is assumed that the executable is an installer, and a UAC prompt is displayed before the application starts.
972:
executed, it is often not ideal to ask for privileges partway through completing a task. If the user were unable to provide proper credentials, the work done before requiring administrator privileges would have to be undone because the task could not be seen through to the end.
179:, also introduced with Windows 2000. This service provides the capability to allow applications running as a separate user to interact with the logged-in user's desktop. This is necessary to support drag-and-drop, clipboard sharing, and other interactive login features.
906:
does not save passwords. If the user is a standard user, they must enter a username and a password. If the user is an administrator, the current user's name is already filled in, and only needs to enter their password. The name can still be modified to run as another
1068:
ask for specific privileges when prompting for authentication, and PolicyKit performs those actions on behalf of the application. Before authenticating, users are able to see which application requested the action and which action was
912:
The application only requires authentication once, and is requested at the time the application needs the privilege. Once "elevated", the application does not need to authenticate again until the application has been Quit and
717:
might look different from an authentication dialog for a system without one. Applications do not have access to the configuration of PolicyKit, so they have no way of knowing which dialog will appear and thus how to spoof
645:, preventing malicious applications from simulating clicking the "Allow" button or otherwise interfering with the confirmation dialog. In this mode, the user's desktop appears dimmed and cannot be interacted with.
772:
combine these two ideas into one. With these programs, administrators explicitly authorize programs to run with higher privileges. Non-administrators are prompted for an administrator username and password.
605:
Commonly, the desktop system locks or secures all common means of input, before requesting passwords or other authentication, so that they cannot be intercepted, manipulated, or simulated:
272:. su (substitute user) allows users to switch the terminal to a different account by entering the username and password of that account. If no user name is given, the operating system's
919:
higher right if higher access is needed. If the right the application has is not suitable for a task, the application may need to authenticate again to increase the privilege level.
245:
In contrast to earlier systems, applications using PolicyKit never run with privileges above those of the current user. Instead, they indirectly make requests of the PolicyKit
38:
599:
client or desktop system used as a client, the user must take responsibility for preventing other malware on their desktop from manipulating, simulating, or capturing input.
1606:
631:- by default "locks" the keyboard, mouse, and window focus, preventing anything but the actual user from inputting the password or otherwise interfering with the
976:
information that only administrators should see). Different operating systems offer distinct methods for applications to identify their security requirements:
652:
If either gksudo's "lock" feature or UAC's Secure
Desktop were compromised or disabled, malicious applications could gain administrator privileges by using
1510:
1208:
898:
not within a terminal instance (e.g. through the Alt + F2 "Run
Application" dialogue box, unticking "Run in terminal") will have the desired effect.
998:
uses a combination of heuristic scanning and "application manifests" to determine if an application requires administrator privileges. Manifest (
1646:
207:
dialog, which prompts the user to input their password in order to perform administrator tasks. This is essentially a graphical front-end of
678:
1482:
713:
uses different dialogs, depending on the configuration of the system. For example, the authentication dialog for a system equipped with a
743:
require the user to know the password to at least two accounts: the regular-use account, and an account with higher privileges such as
1641:
1129:
1158:
1651:
1393:
580:
A major security consideration is the ability of malicious applications to simulate keystrokes or mouse clicks, thus tricking or
1614:
311:, but it allows certain users to run programs with root privileges without spawning a root shell or requiring root's password.
1097:
1091:
353:
comes up automatically when a supported application needs to perform an action requiring root privileges. A replacement, "
338:
1381:
1085:
625:
server to capture all keyboard and mouse input. Other desktop environments using PolicyKit may use their own mechanisms.
172:
119:
1238:
241:
A privilege authorization feature, designed to be independent of the desktop environment in use and already adopted by
66:
from gaining sufficient privileges to compromise the computer system. Operating systems lacking such features, such as
1373:
1318:
813:
requires the user to re-enter his or her password or provide some other means of authentication (e.g. fingerprint).
246:
1461:
886:
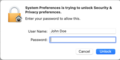
command when from each tty or pts in which sudo was used (in the case of pts's, closing the terminal emulator is
703:
508:
504:
632:
168:
194:
1514:
1216:
290:
1183:
228:
1079:
682:
129:
778:
can be configured to adopt any of these approaches. In practice, the distribution will choose one.
255:
1581:
1137:
1050:
714:
699:
686:
281:
63:
151:
prompts the user for authorization when an application tries to perform an administrator task.
653:
437:
277:
144:
71:
59:
480:
1557:"Developer Best Practices and Guidelines for Applications in a Least Privileged Environment"
1418:
1447:
1377:
671:
622:
581:
176:
1556:
379:
37:
Please expand the article to include this information. Further details may exist on the
1343:
391:
1397:
1347:
940:
826:
544:
1635:
1478:
140:
983:
centralizes all privilege authorization information in a single configuration file,
408:
164:
98:
in the late 80s and early 90s that multi-tasking security contexts were brought to
91:
276:
account (known as "root") is used, thus providing a fast method to obtain a login
1049:
Manifest files can also be compiled into the application executable itself as an
685:
requesting the secure attention sequence on
Windows 11, asking the user to press
317:
1536:
1109:
apply policy regarding when, how and to whom these passwords may be disclosed.
1006:
files with the same name as the application and a suffix of ".manifest", e.g.
95:
75:
876:
restricted to standard user privileges until they enter their password again.
584:
the security feature into granting malicious applications higher privileges.
1490:
1426:
1242:
1133:
999:
744:
728:
358:
273:
262:
235:
1367:
23:
1322:
1269:
951: with: Information for the Mac "Authenticate" dialog. You can help by
837: with: Information for the Mac "Authenticate" dialog. You can help by
555: with: Information for the Mac "Authenticate" dialog. You can help by
1448:"gksu: locking mouse/keyboard not enough to protect against keylogging"
670:
Another security consideration is the ability of malicious software to
526:
500:
428:
79:
861:
prompts for authorization each time it is called to elevate a program.
1582:"Understanding and Configuring User Account Control in Windows Vista"
658:
657:
malicious applications can still do keystroke logging using e.g. the
1303:
589:
Using a terminal based client (standalone or within a desktop/GUI):
727:
Another consideration that has gone into these implementations is
677:
618:
370:
242:
200:
157:
519:
297:
269:
209:
83:
603:
Using a GUI/desktop tightly integrated to the operating system:
1289:
1106:
store password values in a secure, highly available vault; and
1003:
935:
894:. There is no gksudo option to do the same; however, running
821:
539:
399:
335:
332:
175:
as a different user. Runas makes use of the "Secondary Login"
99:
87:
67:
17:
694:
Though it is not the default behavior for usability reasons,
991:
pete ALL = /usr/bin/passwd *, !/usr/bin/passwd root
788:
In order to grant an application administrative privileges,
474:. The idea of the project is to remain simple and bug free.
307:
is a highly configurable Unix command line tool similar to
503:
based operating systems. It has been developed mainly for
163:
A command-line tool and context-menu verb introduced with
82:, which began development in the 1960s; it wasn't until
952:
838:
556:
927:
can be configured to adopt either of these approaches.
661:
tool. (ptrace was restricted in later kernel versions)
1103:
i.e., periodically scramble privileged passwords; and
1100:, similar concept to privileged identity management:
1059:
of warning if the executable is unsigned than if not.
1419:"User Account Control Prompts on the Secure Desktop"
689:
first to enter credentials, to avoid login spoofing.
675:could use that password to gain higher privileges.
890:sufficient). The equivalent command for kdesu is
1094:, the methodology of managing privileged accounts
932:Identifying when administrative rights are needed
800:prompt administrators to re-enter their password.
1263:
1261:
1259:
1002:) files, first introduced with Windows XP, are
698:may be configured to require the user to press
284:command returns the user to their own account.
280:with full privileges to the system. Issuing an
249:, which is the only program that runs as root.
8:
1473:
1471:
1394:"gksu - a Gtk+ su frontend Linux Man Page"
1184:""RunAs" basic (and intermediate) topics"
62:employ security features to help prevent
1121:
470:tupid", and is a graphical version of
124:User Account Control prompt dialog box
7:
35:about the Mac "Authenticate" dialog.
1483:"Security Features vs. Convenience"
1213:PolicyKit Language Reference Manual
14:
1163:Windows XP Product Documentation
1028:"requireAdministrator"
939:
825:
576:Falsified/intercepted user input
543:
479:
436:
407:
378:
369:, is being developed as part of
316:
289:
254:
227:
193:
118:
22:
1130:"User Account Control Overview"
167:that allows running a program,
106:Introduction to implementations
1304:"gksu PolicyKit on Gnome wiki"
1098:Privileged password management
1092:Privileged Identity Management
735:Separate administrator account
431:, starting with Kubuntu 7.10.
1:
1647:Security software comparisons
1317:Bellevue Linux (2004-11-20).
491:A graphical front-end to the
1348:"GutsyGibbon/Tribe5/Kubuntu"
1136:. 2006-10-02. Archived from
1086:Principle of least privilege
1082:, a type of security exploit
1040:</requestedPrivileges>
419:A Qt graphical front-end to
1613:. Microsoft. Archived from
1088:, a security design pattern
1022:<requestedExecutionLevel
1019:<requestedPrivileges>
666:Fake authentication dialogs
394:graphical front-end to the
1668:
495:command that has replaced
1642:Operating system security
1239:"A Brief History of Sudo"
704:secure attention sequence
641:- by default runs in the
117:
74:implementations prior to
1607:"Accessible UAC Prompts"
1190:. MSDN Blogs. 2004-06-23
1013:
723:Usability considerations
268:A command line tool for
1652:Computer access control
1487:Windows Vista Team Blog
536:Security considerations
525:sudo replacement since
1513:. 2007. Archived from
1511:"Authentication Agent"
1215:. 2007. Archived from
1188:Aaron Margosis' WebLog
690:
33:is missing information
681:
303:Created around 1980,
58:A number of computer
1319:"The KDE su Command"
1270:"Sudo in a Nutshell"
1080:Privilege escalation
1008:Notepad.exe.manifest
996:User Account Control
783:Simplicity of dialog
169:control panel applet
130:User Account Control
1462:"ptrace Protection"
1064:Applications using
633:confirmation dialog
529:5.8 (October 2015)
147:operating systems,
102:consumer machines.
1611:Windows Vista Blog
1376:2011-07-25 at the
1366:You can read more
818:Saving credentials
715:fingerprint reader
691:
423:that has replaced
220:Unix and Unix-like
64:malicious software
1209:"About PolicyKit"
1051:embedded resource
1043:</security>
1034:"false"
969:
968:
855:
854:
654:keystroke logging
573:
572:
533:
532:
217:
216:
183:
182:
145:Microsoft Windows
125:
111:Microsoft Windows
60:operating systems
56:
55:
1659:
1626:
1625:
1623:
1622:
1603:
1597:
1596:
1594:
1593:
1578:
1572:
1571:
1569:
1568:
1553:
1547:
1546:
1544:
1543:
1537:"Sudoers Manual"
1535:Miller, Todd C.
1532:
1526:
1525:
1523:
1522:
1507:
1501:
1500:
1498:
1497:
1475:
1466:
1465:
1458:
1452:
1451:
1444:
1438:
1437:
1435:
1434:
1415:
1409:
1408:
1406:
1405:
1396:. Archived from
1390:
1384:
1380:and download it
1364:
1358:
1357:
1355:
1354:
1340:
1334:
1333:
1331:
1330:
1321:. Archived from
1314:
1308:
1307:
1300:
1294:
1293:
1290:"GKSu home page"
1286:
1280:
1279:
1277:
1276:
1268:Miller, Todd C.
1265:
1254:
1253:
1251:
1250:
1241:. Archived from
1237:Miller, Todd C.
1234:
1228:
1227:
1225:
1224:
1205:
1199:
1198:
1196:
1195:
1180:
1174:
1173:
1171:
1170:
1155:
1149:
1148:
1146:
1145:
1126:
1044:
1041:
1038:
1035:
1032:
1029:
1026:
1023:
1020:
1017:
1016:<security>
1009:
986:
964:
961:
943:
936:
897:
893:
885:
850:
847:
829:
822:
568:
565:
547:
540:
483:
440:
411:
382:
320:
293:
258:
236:PolicyKit/pkexec
231:
224:
223:
212:
197:
190:
189:
123:
122:
115:
114:
51:
48:
42:
26:
18:
1667:
1666:
1662:
1661:
1660:
1658:
1657:
1656:
1632:
1631:
1630:
1629:
1620:
1618:
1605:
1604:
1600:
1591:
1589:
1580:
1579:
1575:
1566:
1564:
1555:
1554:
1550:
1541:
1539:
1534:
1533:
1529:
1520:
1518:
1509:
1508:
1504:
1495:
1493:
1477:
1476:
1469:
1460:
1459:
1455:
1446:
1445:
1441:
1432:
1430:
1417:
1416:
1412:
1403:
1401:
1392:
1391:
1387:
1378:Wayback Machine
1365:
1361:
1352:
1350:
1342:
1341:
1337:
1328:
1326:
1316:
1315:
1311:
1302:
1301:
1297:
1288:
1287:
1283:
1274:
1272:
1267:
1266:
1257:
1248:
1246:
1236:
1235:
1231:
1222:
1220:
1207:
1206:
1202:
1193:
1191:
1182:
1181:
1177:
1168:
1166:
1157:
1156:
1152:
1143:
1141:
1128:
1127:
1123:
1118:
1076:
1046:
1045:
1042:
1039:
1036:
1033:
1030:
1027:
1024:
1021:
1018:
1015:
1007:
992:
984:
965:
959:
956:
949:needs expansion
934:
895:
891:
883:
851:
845:
842:
835:needs expansion
820:
785:
737:
725:
687:Ctrl+Alt+Delete
668:
578:
569:
563:
560:
553:needs expansion
538:
524:
490:
447:
418:
389:
331:
302:
267:
240:
208:
177:Windows service
162:
138:
108:
52:
46:
43:
36:
27:
12:
11:
5:
1665:
1663:
1655:
1654:
1649:
1644:
1634:
1633:
1628:
1627:
1598:
1573:
1548:
1527:
1502:
1481:(2007-01-23).
1467:
1453:
1439:
1410:
1385:
1359:
1346:(2007-08-25).
1344:Canonical Ltd.
1335:
1309:
1295:
1281:
1255:
1229:
1200:
1175:
1150:
1120:
1119:
1117:
1114:
1113:
1112:
1111:
1110:
1107:
1104:
1095:
1089:
1083:
1075:
1072:
1071:
1070:
1061:
1060:
1055:
1054:
1014:
1012:
1011:
990:
989:
988:
967:
966:
946:
944:
933:
930:
929:
928:
921:
920:
915:
914:
909:
908:
900:
899:
878:
877:
862:
853:
852:
832:
830:
819:
816:
815:
814:
808:
801:
784:
781:
780:
779:
773:
763:
748:
736:
733:
724:
721:
720:
719:
707:
702:(known as the
667:
664:
663:
662:
650:
649:
648:
647:
646:
643:Secure Desktop
636:
626:
621:- directs the
607:
606:
600:
577:
574:
571:
570:
550:
548:
537:
534:
531:
530:
516:
513:
512:
484:
476:
475:
441:
433:
432:
412:
404:
403:
383:
375:
374:
357:", which uses
355:gksu PolicyKit
321:
313:
312:
294:
286:
285:
259:
251:
250:
232:
222:
221:
215:
214:
198:
188:
187:
181:
180:
153:
152:
139:Included with
126:
113:
112:
107:
104:
54:
53:
47:September 2021
30:
28:
21:
13:
10:
9:
6:
4:
3:
2:
1664:
1653:
1650:
1648:
1645:
1643:
1640:
1639:
1637:
1617:on 2008-01-27
1616:
1612:
1608:
1602:
1599:
1587:
1583:
1577:
1574:
1562:
1558:
1552:
1549:
1538:
1531:
1528:
1517:on 2012-02-18
1516:
1512:
1506:
1503:
1492:
1488:
1484:
1480:
1474:
1472:
1468:
1463:
1457:
1454:
1449:
1443:
1440:
1428:
1424:
1420:
1414:
1411:
1400:on 2011-07-15
1399:
1395:
1389:
1386:
1383:
1379:
1375:
1372:
1371:
1363:
1360:
1349:
1345:
1339:
1336:
1325:on 2007-02-02
1324:
1320:
1313:
1310:
1305:
1299:
1296:
1291:
1285:
1282:
1271:
1264:
1262:
1260:
1256:
1245:on 2007-02-22
1244:
1240:
1233:
1230:
1219:on 2012-02-18
1218:
1214:
1210:
1204:
1201:
1189:
1185:
1179:
1176:
1164:
1160:
1154:
1151:
1140:on 2011-08-22
1139:
1135:
1131:
1125:
1122:
1115:
1108:
1105:
1102:
1101:
1099:
1096:
1093:
1090:
1087:
1084:
1081:
1078:
1077:
1073:
1067:
1063:
1062:
1057:
1056:
1052:
1048:
1047:
1005:
1001:
997:
994:
993:
982:
979:
978:
977:
973:
963:
960:December 2009
954:
950:
947:This section
945:
942:
938:
937:
931:
926:
923:
922:
917:
916:
911:
910:
905:
902:
901:
889:
880:
879:
874:
870:
866:
863:
860:
857:
856:
849:
846:December 2009
840:
836:
833:This section
831:
828:
824:
823:
817:
812:
809:
806:
802:
799:
795:
791:
787:
786:
782:
777:
774:
771:
767:
764:
760:
756:
752:
749:
746:
742:
739:
738:
734:
732:
730:
722:
716:
712:
708:
705:
701:
697:
693:
692:
688:
684:
680:
676:
673:
665:
660:
655:
651:
644:
640:
639:UAC (Windows)
637:
634:
630:
627:
624:
620:
616:
613:
612:
611:
610:
609:
608:
604:
601:
597:
593:
590:
587:
586:
585:
583:
575:
567:
564:December 2009
558:
554:
551:This section
549:
546:
542:
541:
535:
528:
522:
521:
517:
515:
514:
510:
506:
502:
498:
494:
488:
485:
482:
478:
477:
473:
469:
465:
462:
458:
454:
450:
445:
442:
439:
435:
434:
430:
426:
422:
416:
413:
410:
406:
405:
401:
397:
393:
387:
384:
381:
377:
376:
372:
368:
364:
360:
356:
352:
348:
344:
340:
337:
334:
329:
325:
322:
319:
315:
314:
310:
306:
300:
299:
295:
292:
288:
287:
283:
279:
275:
271:
265:
264:
260:
257:
253:
252:
248:
244:
238:
237:
233:
230:
226:
225:
219:
218:
211:
206:
203:includes the
202:
199:
196:
192:
191:
185:
184:
178:
174:
170:
166:
160:
159:
155:
154:
150:
146:
142:
141:Windows Vista
136:
132:
131:
127:
121:
116:
110:
109:
105:
103:
101:
97:
93:
89:
85:
81:
77:
73:
69:
65:
61:
50:
40:
34:
31:This article
29:
25:
20:
19:
16:
1619:. Retrieved
1615:the original
1610:
1601:
1590:. Retrieved
1585:
1576:
1565:. Retrieved
1560:
1551:
1540:. Retrieved
1530:
1519:. Retrieved
1515:the original
1505:
1494:. Retrieved
1486:
1479:Allchin, Jim
1456:
1442:
1431:. Retrieved
1429:. 2006-05-03
1422:
1413:
1402:. Retrieved
1398:the original
1388:
1369:
1362:
1351:. Retrieved
1338:
1327:. Retrieved
1323:the original
1312:
1298:
1284:
1273:. Retrieved
1247:. Retrieved
1243:the original
1232:
1221:. Retrieved
1217:the original
1212:
1203:
1192:. Retrieved
1187:
1178:
1167:. Retrieved
1162:
1153:
1142:. Retrieved
1138:the original
1124:
1065:
995:
985:/etc/sudoers
980:
974:
970:
957:
953:adding to it
948:
924:
904:Authenticate
903:
887:
872:
868:
864:
858:
843:
839:adding to it
834:
810:
804:
798:Authenticate
797:
793:
789:
775:
770:Authenticate
769:
765:
758:
754:
750:
740:
726:
710:
700:Ctrl+Alt+Del
695:
669:
642:
638:
628:
614:
602:
595:
591:
588:
579:
561:
557:adding to it
552:
518:
496:
492:
486:
471:
467:
463:
460:
456:
452:
451:stands for "
448:
443:
424:
420:
414:
398:command for
395:
385:
366:
362:
361:rather than
354:
350:
346:
342:
327:
323:
308:
304:
296:
261:
234:
205:Authenticate
204:
165:Windows 2000
156:
148:
134:
128:
57:
44:
32:
15:
1588:. Microsoft
1563:. Microsoft
1165:. Microsoft
913:relaunched.
173:MMC snap-in
1636:Categories
1621:2008-02-13
1592:2007-03-15
1567:2007-03-15
1542:2007-03-12
1521:2017-11-15
1496:2007-03-12
1433:2007-03-04
1404:2007-08-14
1353:2007-09-18
1329:2007-03-12
1275:2007-07-01
1249:2007-03-12
1223:2017-11-03
1194:2007-03-13
1169:2007-03-13
1144:2007-03-12
1116:References
1069:requested.
709:In GNOME,
143:and later
76:Windows NT
1491:Microsoft
1427:Microsoft
1382:from Koji
1134:Microsoft
1066:PolicyKit
1031:uiAccess=
1000:.manifest
925:PolicyKit
811:PolicyKit
776:PolicyKit
729:usability
711:PolicyKit
615:PolicyKit
359:PolicyKit
336:Graphical
274:superuser
213:command.
39:talk page
1374:Archived
1074:See also
892:kdesu -s
762:account.
582:spoofing
339:frontend
1586:TechNet
1423:UACBlog
1159:"Runas"
896:sudo -k
884:sudo -k
527:OpenBSD
501:Red Hat
466:imple,
429:Kubuntu
415:kdesudo
171:, or a
80:Multics
72:Windows
1368:about
1025:level=
871:, and
869:gksudo
796:, and
794:gksudo
759:gksudo
659:strace
629:gksudo
509:Fedora
449:ktsuss
444:ktsuss
328:GKsudo
247:daemon
94:, and
1370:beesu
1037:/>
907:user.
873:kdesu
803:With
755:kdesu
672:spoof
619:GNOME
487:beesu
425:kdesu
386:kdesu
371:GNOME
278:shell
243:GNOME
201:macOS
186:macOS
158:Runas
92:Linux
1561:MSDN
981:sudo
865:sudo
790:sudo
768:and
757:and
751:sudo
745:root
596:sudo
594:and
520:doas
507:and
505:RHEL
497:gksu
455:eep
421:sudo
367:sudo
351:GKsu
347:sudo
345:and
333:GTK+
326:and
324:GKSu
305:sudo
298:sudo
282:exit
270:Unix
210:sudo
84:UNIX
1004:XML
955:.
888:not
859:UAC
841:.
805:UAC
766:UAC
718:it.
696:UAC
683:UAC
559:.
499:in
459:he
427:in
400:KDE
341:to
149:UAC
135:UAC
100:x86
88:BSD
68:DOS
1638::
1609:.
1584:.
1559:.
1489:.
1485:.
1470:^
1425:.
1421:.
1258:^
1211:.
1186:.
1161:.
1132:.
867:,
792:,
753:,
741:su
731:.
592:su
511:.
493:su
472:su
461:su
402:.
396:su
392:Qt
390:A
373:.
363:su
349:.
343:su
309:su
263:su
137:):
96:NT
90:,
86:,
70:,
1624:.
1595:.
1570:.
1545:.
1524:.
1499:.
1464:.
1450:.
1436:.
1407:.
1356:.
1332:.
1306:.
1292:.
1278:.
1252:.
1226:.
1197:.
1172:.
1147:.
962:)
958:(
848:)
844:(
747:.
635:.
623:X
617:(
566:)
562:(
523::
489::
468:s
464:s
457:t
453:k
446::
417::
388::
365:/
330::
301::
266::
239::
161::
133:(
49:)
45:(
41:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.