2320:
255:
security, the S-boxes can be kept secret. In the original standard where GOST was specified, no S-boxes were given, but they were to be supplied somehow. This led to speculation that organizations the government wished to spy on were given weak S-boxes. One GOST chip manufacturer reported that he generated S-boxes himself using a
685:
Until 2011 researchers unanimously agreed that GOST could or should be very secure, which was summarised in 2010 in these words: despite considerable cryptanalytic efforts spent in the past 20 years, GOST is still not broken". Unhappily, it was recently discovered that GOST can be broken and is a
506:
Until 2011 researchers unanimously agreed that GOST could or should be very secure, which was summarised in 2010 in these words: despite considerable cryptanalytic efforts spent in the past 20 years, GOST is still not broken". Unhappily, it was recently discovered that GOST can be broken and is a
254:
The S-boxes accept a four-bit input and produce a four-bit output. The S-box substitution in the round function consists of eight 4 × 4 S-boxes. The S-boxes are implementation-dependent, thus parties that want to secure their communications using GOST must be using the same S-boxes. For extra
452:
In
December 2012, Courtois, Gawinecki, and Song improved attacks on GOST by computing only 2 GOST rounds. Isobe had already published a single key attack on the full GOST cipher, which Dinur, Dunkelman, and Shamir improved upon, reaching 2 time complexity for 2 data and 2 memory, and 2 time
433:
The latest cryptanalysis of GOST shows that it is secure in a theoretical sense. In practice, the data and memory complexity of the best published attacks has reached the level of practical, while the time complexity of even the best attack is still 2 when 2 data is available.
250:
The subkeys are chosen in a pre-specified order. The key schedule is very simple: break the 256-bit key into eight 32-bit subkeys, and each subkey is used four times in the algorithm; the first 24 rounds use the key words in order, the last 8 rounds use them in reverse order.
38:
573:
456:
Since the attacks reduce the expected strength from 2 (key length) to around 2, the cipher can be considered broken. However, this attack is not feasible in practice, as the number of tests to be performed 2 is out of reach.
444:
In 2011 several authors discovered more significant flaws in GOST, being able to attack the full 32-round GOST with arbitrary keys for the first time. It has even been called "a deeply flawed cipher" by
155:
In 2011 several authors discovered more significant flaws in GOST, being able to attack the full 32-round GOST with arbitrary keys for the first time. It has even been called "a deeply flawed cipher" by
449:. Initial attacks were able to reduce time complexity from 2 to 2 at the cost of huge memory requirements, and soon they were improved up to 2 time complexity (at the cost of 2 memory and 2 data).
247:
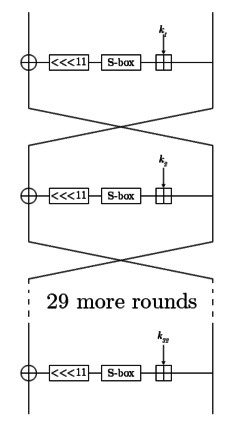
2, put the result through a layer of S-boxes, and rotate that result left by 11 bits. The result of that is the output of the round function. In the adjacent diagram, one line represents 32 bits.
236:(16!)) bits of secret information, so the effective key size can be increased to 610 bits; however, a chosen-key attack can recover the contents of the S-boxes in approximately 2 encryptions.
2300:
2130:
751:
725:
703:
680:
501:
460:
Note that for any block cipher with block size of n bits, the maximum amount of plaintext that can be encrypted before rekeying must take place is 2 blocks, due to the
1983:
1918:
999:
553:
Fleischmann, Ewan; Gorski, Michael; Hühne, Jan-Hendrik; Lucks, Stefan (2009). "Key
Recovery Attack on Full GOST Block Cipher with Zero Time and Memory".
185:
with a block size of 64 bits. The original standard, published in 1989, did not give the cipher any name, but the most recent revision of the standard,
1745:
1101:
200:
Developed in the 1970s, the standard had been marked "Top Secret" and then downgraded to "Secret" in 1990. Shortly after the dissolution of the
1735:
1229:
842:
807:
622:
1636:
1898:
1872:
1740:
859:"Draft of ISO/IEC JTC 1/SC 27 Standing Document No. 12 (SD12) on the Assessment of Cryptographic Techniques and Key Lengths, 4th edition"
1713:
1976:
1882:
992:
1761:
578:
We show that a simple "black box" chosen-key attack against GOST can recover secret S-boxes with approximately 2^32 encryptions
522:
2179:
1939:
2353:
256:
1969:
1029:
2295:
2250:
2063:
1825:
985:
2174:
1842:
1752:
1730:
1043:
858:
2290:
1847:
1703:
1656:
1131:
221:
117:
2358:
2280:
2270:
2125:
1913:
1795:
1670:
1039:
209:
959:
An open source implementation of PKCS#11 software device with
Russian GOST cryptography standards capabilities
2363:
2275:
2265:
2068:
2028:
2021:
2011:
2006:
1852:
1641:
1012:
204:, it was declassified and it was released to the public in 1994. GOST 28147 was a Soviet alternative to the
2348:
2016:
1944:
1820:
1815:
1767:
263:
1616:
2323:
2169:
2115:
1934:
1757:
1194:
948:
584:
612:
2285:
2209:
1837:
1720:
1646:
1329:
1309:
190:
137:
81:
2048:
1800:
1777:
905:
437:
Since 2007, several attacks have been developed against reduced-round GOST implementations and/or
2154:
2138:
2085:
1785:
1693:
1405:
1334:
1304:
1249:
953:
244:
2214:
2204:
2075:
1505:
1204:
1164:
1159:
1126:
1086:
1034:
838:
803:
618:
639:
2149:
1877:
1772:
1651:
1510:
1390:
1359:
1053:
922:
828:
795:
461:
446:
157:
193:
is based on this cipher. The new standard also specifies a new 128-bit block cipher called
1724:
1708:
1697:
1631:
1590:
1555:
1485:
1465:
1339:
1219:
1214:
1169:
766:
597:
240:
130:
2224:
2144:
2105:
2053:
2038:
1862:
1810:
1621:
1606:
1545:
1540:
1425:
1174:
2342:
2305:
2260:
2219:
2199:
2095:
2058:
2033:
1857:
1805:
1684:
1666:
1455:
1430:
1420:
1244:
1234:
1081:
205:
179:
148:
657:
529:
2255:
2100:
2090:
2080:
2043:
1992:
1790:
1611:
1575:
1440:
1319:
1274:
1106:
1058:
1008:
182:
823:
Dinur, Itai; Dunkelman, Orr; Shamir, Adi (2012). "Improved
Attacks on Full GOST".
799:
2234:
1400:
1395:
1279:
833:
673:"Security Evaluation of GOST 28147-89 In View Of International Standardisation"
494:"Security Evaluation of GOST 28147-89 In View Of International Standardisation"
2194:
2164:
2159:
2120:
1832:
1550:
1490:
1374:
1369:
1314:
1184:
1047:
225:
194:
85:
927:
790:
Isobe, Takanori (2011). "A Single-Key Attack on the Full GOST Block Cipher".
17:
2184:
1565:
1560:
1450:
1364:
1259:
1239:
914:
2229:
2189:
1903:
1867:
1661:
1324:
1199:
1179:
1091:
949:
Description, texts of the standard, online GOST encrypt and decrypt tools
438:
189:(RFC 7801, RFC 8891), specifies that it may be referred to as Magma. The
107:
963:
37:
1570:
1520:
1480:
1470:
1415:
1410:
1254:
1063:
794:. Lecture Notes in Computer Science. Vol. 6733. pp. 290–305.
740:
614:
Applied cryptography : protocols, algorithms, and source code in C
966:— open-source implementation of Russian GOST cryptography for OpenSSL.
718:
2110:
1908:
1530:
1525:
1460:
1445:
1435:
1380:
1354:
1349:
1344:
1224:
1209:
918:
896:
887:
243:
of 32 rounds. Its round function is very simple: add a 32-bit subkey
827:. Lecture Notes in Computer Science. Vol. 7549. pp. 9–28.
958:
895:
Popov, Vladimir; Leontiev, Serguei; Kurepkin, Igor (January 2006).
888:"RFC 5830: GOST 28147-89 encryption, decryption and MAC algorithms"
878:
464:, and none of the aforementioned attacks require less than 2 data.
1626:
1585:
1535:
1515:
1500:
1289:
1269:
1189:
1154:
699:
672:
493:
349:, adds the missing S-box specification and defines it as follows.
229:
897:"RFC 4357: Additional Cryptographic Algorithms for Use with GOST"
767:"CONTRADICTION IMMUNITY AND GUESS-THEN-DETERMINE ATTACKS ON GOST"
1475:
1384:
1299:
1294:
1284:
1264:
1136:
1121:
473:
201:
95:
58:
1965:
981:
765:
Nicolas T. Courtois; Jerzy A. Gawinecki; Guangyan Song (2012).
1580:
1495:
1116:
1111:
62:
36:
741:"Algebraic Complexity Reduction and Cryptanalysis of GOST"
574:"A chosen key attack against the secret S-boxes of GOST"
178:(RFC 5830), is a Soviet and Russian government standard
2131:
Cryptographically secure pseudorandom number generator
969:
2243:
1999:
1927:
1891:
1680:
1599:
1145:
1072:
1020:
345:However, the most recent revision of the standard,
146:
136:
126:
116:
106:
101:
91:
77:
69:
54:
49:
638:Eli Biham; Orr Dunkelman; Nathan Keller (2007).
212:. Thus, the two are very similar in structure.
719:"An Improved Differential Attack on Full GOST"
232:can be secret, and they contain about 354 (log
1977:
993:
904:Alex Biryukov & David Wagner (May 2000).
27:Soviet/Russian national standard block cipher
8:
698:Nicolas T. Courtois; Michał Miształ (2011).
30:
1984:
1970:
1962:
1000:
986:
978:
974:
970:
658:"Reflection Cryptanalysis of Some Ciphers"
926:
913:. Advances in Cryptology, Proceedings of
832:
517:
515:
881:. Rudolf Nickolaev, WebCrypto GOST team.
351:
268:
617:(2. ed., ed.). New York : Wiley.
484:
593:
582:
29:
964:https://github.com/gost-engine/engine
921:: Springer-Verlag. pp. 589–606.
739:Courtois, Nicolas T. (Jun 13, 2011).
7:
700:"Differential Cryptanalysis of GOST"
671:Courtois, Nicolas T. (9 May 2011).
492:Courtois, Nicolas T. (9 May 2011).
523:"GOST R 34.12-2015 (Russian only)"
264:Central Bank of Russian Federation
25:
2319:
2318:
572:Saarinen, Markku-Juhani (1998).
422:1 7 E D 0 5 8 3 4 F A 6 9 C B 2
414:8 E 2 5 6 9 1 C F 4 B 0 D A 3 7
406:5 D F 6 9 2 C A B 7 8 1 4 3 E 0
398:7 F 5 A 8 1 6 D 0 9 3 E B 4 2 C
390:C 8 2 1 D 4 F 6 7 0 A 5 3 E 9 B
382:B 3 5 8 2 F A D E 1 7 4 C 9 6 0
374:6 8 2 3 9 A 5 C 1 E 4 7 B D 0 F
366:C 4 6 2 A 5 B 9 E 8 D 7 0 3 F 1
339:1 F D 0 5 7 A 4 9 2 3 E 6 B 8 C
331:D B 4 1 3 F 5 9 0 A E 7 6 8 2 C
323:4 B A 0 7 2 1 D 3 6 8 5 9 C F E
315:6 C 7 1 5 F D 8 4 A 9 E 0 3 B 2
307:7 D A 1 0 8 9 F E 4 6 C B 2 5 3
299:5 8 1 D A 3 4 2 E F C 7 6 0 9 B
291:E B 4 C 6 D F A 2 3 8 1 0 7 5 9
283:4 A 9 2 D 8 0 E 6 B 1 C 7 F 5 3
886:Dolmatov, Vasily (March 2010).
2180:Information-theoretic security
1:
266:used the following S-boxes:
257:pseudorandom number generator
800:10.1007/978-3-642-21702-9_17
717:Nicolas T. Courtois (2012).
2296:Message authentication code
2251:Cryptographic hash function
2064:Cryptographic hash function
834:10.1007/978-3-642-34047-5_2
174:), defined in the standard
2380:
2175:Harvest now, decrypt later
2314:
2291:Post-quantum cryptography
1961:
1883:Time/memory/data tradeoff
977:
973:
748:Cryptology ePrint Archive
677:Cryptology ePrint Archive
498:Cryptology ePrint Archive
154:
73:1994-05-23 (declassified)
35:
2281:Quantum key distribution
2271:Authenticated encryption
2126:Random number generation
1671:Whitening transformation
928:10.1007/3-540-45539-6_41
879:"WebCrypto GOST Library"
825:Fast Software Encryption
792:Fast Software Encryption
640:"Improved Slide Attacks"
611:Schneier, Bruce (1996).
555:Published as ISO/IEC JTC
358:GOST R 34.12-2015 S-box
2276:Public-key cryptography
2266:Symmetric-key algorithm
2069:Key derivation function
2029:Cryptographic primitive
2022:Authentication protocol
2012:Outline of cryptography
2007:History of cryptography
1642:Confusion and diffusion
453:complexity for 2 data.
2017:Cryptographic protocol
907:Advanced Slide Attacks
592:Cite journal requires
41:
2170:End-to-end encryption
2116:Cryptojacking malware
1935:Initialization vector
954:SCAN's entry for GOST
429:Cryptanalysis of GOST
40:
31:GOST 28147-89 (Magma)
2354:Broken block ciphers
2286:Quantum cryptography
2210:Trusted timestamping
1714:3-subset MITM attack
1330:Intel Cascade Cipher
1310:Hasty Pudding cipher
686:deeply flawed cipher
507:deeply flawed cipher
208:standard algorithm,
2049:Cryptographic nonce
1753:Differential-linear
656:Orhun Kara (2008).
32:
2155:Subliminal channel
2139:Pseudorandom noise
2086:Key (cryptography)
1826:Differential-fault
1044:internal mechanics
220:GOST has a 64-bit
191:GOST hash function
82:GOST hash function
42:
2336:
2335:
2332:
2331:
2215:Key-based routing
2205:Trapdoor function
2076:Digital signature
1957:
1956:
1953:
1952:
1940:Mode of operation
1617:Lai–Massey scheme
844:978-3-642-34046-8
809:978-3-642-21701-2
624:978-0-471-11709-4
426:
425:
347:GOST R 34.12-2015
343:
342:
262:For example, the
228:of 256 bits. Its
187:GOST R 34.12-2015
168:GOST block cipher
164:
163:
16:(Redirected from
2371:
2322:
2321:
2150:Insecure channel
1986:
1979:
1972:
1963:
1811:Power-monitoring
1652:Avalanche effect
1360:Khufu and Khafre
1013:security summary
1002:
995:
988:
979:
975:
971:
938:
936:
935:
930:
912:
900:
891:
882:
866:
865:
863:
855:
849:
848:
836:
820:
814:
813:
787:
781:
780:
778:
777:
771:
762:
756:
755:
745:
736:
730:
729:
723:
714:
708:
707:
695:
689:
688:
668:
662:
661:
653:
647:
646:
644:
635:
629:
628:
608:
602:
601:
595:
590:
588:
580:
569:
563:
562:
550:
544:
543:
541:
540:
534:
528:. Archived from
527:
519:
510:
509:
489:
462:birthday paradox
447:Nicolas Courtois
352:
269:
158:Nicolas Courtois
65:, 8th Department
33:
21:
2379:
2378:
2374:
2373:
2372:
2370:
2369:
2368:
2359:Feistel ciphers
2339:
2338:
2337:
2328:
2310:
2239:
1995:
1990:
1949:
1923:
1892:Standardization
1887:
1816:Electromagnetic
1768:Integral/Square
1725:Piling-up lemma
1709:Biclique attack
1698:EFF DES cracker
1682:
1676:
1607:Feistel network
1595:
1220:CIPHERUNICORN-E
1215:CIPHERUNICORN-A
1147:
1141:
1074:
1068:
1022:
1016:
1006:
945:
933:
931:
910:
903:
894:
885:
877:
874:
872:Further reading
869:
861:
857:
856:
852:
845:
822:
821:
817:
810:
789:
788:
784:
775:
773:
769:
764:
763:
759:
743:
738:
737:
733:
721:
716:
715:
711:
697:
696:
692:
670:
669:
665:
655:
654:
650:
642:
637:
636:
632:
625:
610:
609:
605:
591:
581:
571:
570:
566:
552:
551:
547:
538:
536:
532:
525:
521:
520:
513:
491:
490:
486:
482:
470:
431:
241:Feistel network
235:
218:
131:Feistel network
70:First published
45:
44:Diagram of GOST
28:
23:
22:
15:
12:
11:
5:
2377:
2375:
2367:
2366:
2364:GOST standards
2361:
2356:
2351:
2341:
2340:
2334:
2333:
2330:
2329:
2327:
2326:
2315:
2312:
2311:
2309:
2308:
2303:
2301:Random numbers
2298:
2293:
2288:
2283:
2278:
2273:
2268:
2263:
2258:
2253:
2247:
2245:
2241:
2240:
2238:
2237:
2232:
2227:
2225:Garlic routing
2222:
2217:
2212:
2207:
2202:
2197:
2192:
2187:
2182:
2177:
2172:
2167:
2162:
2157:
2152:
2147:
2145:Secure channel
2142:
2136:
2135:
2134:
2123:
2118:
2113:
2108:
2106:Key stretching
2103:
2098:
2093:
2088:
2083:
2078:
2073:
2072:
2071:
2066:
2056:
2054:Cryptovirology
2051:
2046:
2041:
2039:Cryptocurrency
2036:
2031:
2026:
2025:
2024:
2014:
2009:
2003:
2001:
1997:
1996:
1991:
1989:
1988:
1981:
1974:
1966:
1959:
1958:
1955:
1954:
1951:
1950:
1948:
1947:
1942:
1937:
1931:
1929:
1925:
1924:
1922:
1921:
1916:
1911:
1906:
1901:
1895:
1893:
1889:
1888:
1886:
1885:
1880:
1875:
1870:
1865:
1860:
1855:
1850:
1845:
1840:
1835:
1830:
1829:
1828:
1823:
1818:
1813:
1808:
1798:
1793:
1788:
1783:
1775:
1770:
1765:
1758:Distinguishing
1755:
1750:
1749:
1748:
1743:
1738:
1728:
1718:
1717:
1716:
1711:
1701:
1690:
1688:
1678:
1677:
1675:
1674:
1664:
1659:
1654:
1649:
1644:
1639:
1634:
1629:
1624:
1622:Product cipher
1619:
1614:
1609:
1603:
1601:
1597:
1596:
1594:
1593:
1588:
1583:
1578:
1573:
1568:
1563:
1558:
1553:
1548:
1543:
1538:
1533:
1528:
1523:
1518:
1513:
1508:
1503:
1498:
1493:
1488:
1483:
1478:
1473:
1468:
1463:
1458:
1453:
1448:
1443:
1438:
1433:
1428:
1423:
1418:
1413:
1408:
1403:
1398:
1393:
1388:
1377:
1372:
1367:
1362:
1357:
1352:
1347:
1342:
1337:
1332:
1327:
1322:
1317:
1312:
1307:
1302:
1297:
1292:
1287:
1282:
1277:
1272:
1267:
1262:
1257:
1252:
1250:Cryptomeria/C2
1247:
1242:
1237:
1232:
1227:
1222:
1217:
1212:
1207:
1202:
1197:
1192:
1187:
1182:
1177:
1172:
1167:
1162:
1157:
1151:
1149:
1143:
1142:
1140:
1139:
1134:
1129:
1124:
1119:
1114:
1109:
1104:
1099:
1094:
1089:
1084:
1078:
1076:
1070:
1069:
1067:
1066:
1061:
1056:
1051:
1037:
1032:
1026:
1024:
1018:
1017:
1007:
1005:
1004:
997:
990:
982:
968:
967:
961:
956:
951:
944:
943:External links
941:
940:
939:
901:
892:
883:
873:
870:
868:
867:
850:
843:
815:
808:
782:
757:
731:
709:
690:
663:
648:
630:
623:
603:
594:|journal=
564:
545:
511:
483:
481:
478:
477:
476:
474:GOST standards
469:
466:
430:
427:
424:
423:
420:
416:
415:
412:
408:
407:
404:
400:
399:
396:
392:
391:
388:
384:
383:
380:
376:
375:
372:
368:
367:
364:
360:
359:
356:
341:
340:
337:
333:
332:
329:
325:
324:
321:
317:
316:
313:
309:
308:
305:
301:
300:
297:
293:
292:
289:
285:
284:
281:
277:
276:
273:
233:
217:
214:
162:
161:
152:
151:
144:
143:
140:
134:
133:
128:
124:
123:
120:
114:
113:
110:
104:
103:
99:
98:
93:
89:
88:
79:
75:
74:
71:
67:
66:
56:
52:
51:
47:
46:
43:
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
2376:
2365:
2362:
2360:
2357:
2355:
2352:
2350:
2349:Block ciphers
2347:
2346:
2344:
2325:
2317:
2316:
2313:
2307:
2306:Steganography
2304:
2302:
2299:
2297:
2294:
2292:
2289:
2287:
2284:
2282:
2279:
2277:
2274:
2272:
2269:
2267:
2264:
2262:
2261:Stream cipher
2259:
2257:
2254:
2252:
2249:
2248:
2246:
2242:
2236:
2233:
2231:
2228:
2226:
2223:
2221:
2220:Onion routing
2218:
2216:
2213:
2211:
2208:
2206:
2203:
2201:
2200:Shared secret
2198:
2196:
2193:
2191:
2188:
2186:
2183:
2181:
2178:
2176:
2173:
2171:
2168:
2166:
2163:
2161:
2158:
2156:
2153:
2151:
2148:
2146:
2143:
2140:
2137:
2132:
2129:
2128:
2127:
2124:
2122:
2119:
2117:
2114:
2112:
2109:
2107:
2104:
2102:
2099:
2097:
2096:Key generator
2094:
2092:
2089:
2087:
2084:
2082:
2079:
2077:
2074:
2070:
2067:
2065:
2062:
2061:
2060:
2059:Hash function
2057:
2055:
2052:
2050:
2047:
2045:
2042:
2040:
2037:
2035:
2034:Cryptanalysis
2032:
2030:
2027:
2023:
2020:
2019:
2018:
2015:
2013:
2010:
2008:
2005:
2004:
2002:
1998:
1994:
1987:
1982:
1980:
1975:
1973:
1968:
1967:
1964:
1960:
1946:
1943:
1941:
1938:
1936:
1933:
1932:
1930:
1926:
1920:
1917:
1915:
1912:
1910:
1907:
1905:
1902:
1900:
1897:
1896:
1894:
1890:
1884:
1881:
1879:
1876:
1874:
1871:
1869:
1866:
1864:
1861:
1859:
1856:
1854:
1851:
1849:
1846:
1844:
1841:
1839:
1838:Interpolation
1836:
1834:
1831:
1827:
1824:
1822:
1819:
1817:
1814:
1812:
1809:
1807:
1804:
1803:
1802:
1799:
1797:
1794:
1792:
1789:
1787:
1784:
1782:
1781:
1776:
1774:
1771:
1769:
1766:
1763:
1759:
1756:
1754:
1751:
1747:
1744:
1742:
1739:
1737:
1734:
1733:
1732:
1729:
1726:
1722:
1719:
1715:
1712:
1710:
1707:
1706:
1705:
1702:
1699:
1695:
1692:
1691:
1689:
1686:
1685:cryptanalysis
1679:
1672:
1668:
1667:Key whitening
1665:
1663:
1660:
1658:
1655:
1653:
1650:
1648:
1645:
1643:
1640:
1638:
1635:
1633:
1630:
1628:
1625:
1623:
1620:
1618:
1615:
1613:
1610:
1608:
1605:
1604:
1602:
1598:
1592:
1589:
1587:
1584:
1582:
1579:
1577:
1574:
1572:
1569:
1567:
1564:
1562:
1559:
1557:
1554:
1552:
1549:
1547:
1544:
1542:
1539:
1537:
1534:
1532:
1529:
1527:
1524:
1522:
1519:
1517:
1514:
1512:
1509:
1507:
1504:
1502:
1499:
1497:
1494:
1492:
1489:
1487:
1484:
1482:
1479:
1477:
1474:
1472:
1469:
1467:
1464:
1462:
1459:
1457:
1456:New Data Seal
1454:
1452:
1449:
1447:
1444:
1442:
1439:
1437:
1434:
1432:
1429:
1427:
1424:
1422:
1419:
1417:
1414:
1412:
1409:
1407:
1404:
1402:
1399:
1397:
1394:
1392:
1389:
1386:
1382:
1378:
1376:
1373:
1371:
1368:
1366:
1363:
1361:
1358:
1356:
1353:
1351:
1348:
1346:
1343:
1341:
1338:
1336:
1333:
1331:
1328:
1326:
1323:
1321:
1318:
1316:
1313:
1311:
1308:
1306:
1303:
1301:
1298:
1296:
1293:
1291:
1288:
1286:
1283:
1281:
1278:
1276:
1273:
1271:
1268:
1266:
1263:
1261:
1258:
1256:
1253:
1251:
1248:
1246:
1243:
1241:
1238:
1236:
1233:
1231:
1228:
1226:
1223:
1221:
1218:
1216:
1213:
1211:
1208:
1206:
1203:
1201:
1198:
1196:
1195:BEAR and LION
1193:
1191:
1188:
1186:
1183:
1181:
1178:
1176:
1173:
1171:
1168:
1166:
1163:
1161:
1158:
1156:
1153:
1152:
1150:
1144:
1138:
1135:
1133:
1130:
1128:
1125:
1123:
1120:
1118:
1115:
1113:
1110:
1108:
1105:
1103:
1100:
1098:
1095:
1093:
1090:
1088:
1085:
1083:
1080:
1079:
1077:
1071:
1065:
1062:
1060:
1057:
1055:
1052:
1049:
1045:
1041:
1038:
1036:
1033:
1031:
1028:
1027:
1025:
1019:
1014:
1010:
1009:Block ciphers
1003:
998:
996:
991:
989:
984:
983:
980:
976:
972:
965:
962:
960:
957:
955:
952:
950:
947:
946:
942:
929:
924:
920:
916:
909:
908:
902:
898:
893:
889:
884:
880:
876:
875:
871:
860:
854:
851:
846:
840:
835:
830:
826:
819:
816:
811:
805:
801:
797:
793:
786:
783:
768:
761:
758:
753:
749:
742:
735:
732:
727:
720:
713:
710:
705:
701:
694:
691:
687:
682:
678:
674:
667:
664:
659:
652:
649:
641:
634:
631:
626:
620:
616:
615:
607:
604:
599:
586:
579:
575:
568:
565:
560:
556:
549:
546:
535:on 2015-09-24
531:
524:
518:
516:
512:
508:
503:
499:
495:
488:
485:
479:
475:
472:
471:
467:
465:
463:
458:
454:
450:
448:
442:
440:
435:
428:
421:
418:
417:
413:
410:
409:
405:
402:
401:
397:
394:
393:
389:
386:
385:
381:
378:
377:
373:
370:
369:
365:
362:
361:
357:
354:
353:
350:
348:
338:
335:
334:
330:
327:
326:
322:
319:
318:
314:
311:
310:
306:
303:
302:
298:
295:
294:
290:
287:
286:
282:
279:
278:
274:
271:
270:
267:
265:
260:
258:
252:
248:
246:
242:
237:
231:
227:
223:
216:The algorithm
215:
213:
211:
207:
206:United States
203:
198:
196:
192:
188:
184:
181:
180:symmetric key
177:
176:GOST 28147-89
173:
169:
159:
153:
150:
149:cryptanalysis
145:
141:
139:
135:
132:
129:
125:
121:
119:
115:
111:
109:
105:
102:Cipher detail
100:
97:
96:GOST standard
94:
92:Certification
90:
87:
83:
80:
76:
72:
68:
64:
60:
57:
53:
48:
39:
34:
19:
18:GOST 28147-89
2256:Block cipher
2101:Key schedule
2091:Key exchange
2081:Kleptography
2044:Cryptosystem
1993:Cryptography
1843:Partitioning
1801:Side-channel
1779:
1746:Higher-order
1731:Differential
1612:Key schedule
1096:
932:. Retrieved
906:
853:
824:
818:
791:
785:
774:. Retrieved
760:
747:
734:
712:
693:
684:
676:
666:
651:
633:
613:
606:
585:cite journal
577:
567:
558:
554:
548:
537:. Retrieved
530:the original
505:
497:
487:
459:
455:
451:
443:
436:
432:
346:
344:
261:
253:
249:
238:
219:
199:
186:
183:block cipher
175:
171:
167:
165:
147:Best public
2244:Mathematics
2235:Mix network
1928:Utilization
1914:NSA Suite B
1899:AES process
1848:Rubber-hose
1786:Related-key
1694:Brute-force
1073:Less common
118:Block sizes
2343:Categories
2195:Ciphertext
2165:Decryption
2160:Encryption
2121:Ransomware
1878:Chi-square
1796:Rotational
1736:Impossible
1657:Block size
1551:Spectr-H64
1375:Ladder-DES
1370:Kuznyechik
1315:Hierocrypt
1185:BassOmatic
1148:algorithms
1075:algorithms
1048:Triple DES
1023:algorithms
934:2007-09-03
776:2014-08-25
539:2015-08-28
480:References
239:GOST is a
226:key length
222:block size
195:Kuznyechik
86:Kuznyechik
78:Successors
2185:Plaintext
1853:Black-bag
1773:Boomerang
1762:Known-key
1741:Truncated
1566:Threefish
1561:SXAL/MBAL
1451:MultiSwap
1406:MacGuffin
1365:KN-Cipher
1305:Grand Cru
1260:CS-Cipher
1240:COCONUT98
915:EUROCRYPT
772:. Versita
439:weak keys
127:Structure
108:Key sizes
55:Designers
2324:Category
2230:Kademlia
2190:Codetext
2133:(CSPRNG)
1904:CRYPTREC
1868:Weak key
1821:Acoustic
1662:Key size
1506:Red Pike
1325:IDEA NXT
1205:Chiasmus
1200:CAST-256
1180:BaseKing
1165:Akelarre
1160:Adiantum
1127:Skipjack
1092:CAST-128
1087:Camellia
1035:Blowfish
468:See also
112:256 bits
2000:General
1945:Padding
1863:Rebound
1571:Treyfer
1521:SAVILLE
1481:PRESENT
1471:NOEKEON
1416:MAGENTA
1411:Madryga
1391:Lucifer
1255:CRYPTON
1064:Twofish
1054:Serpent
899:. IETF.
890:. IETF.
864:. 2016.
230:S-boxes
122:64 bits
50:General
2111:Keygen
1909:NESSIE
1858:Davies
1806:Timing
1721:Linear
1681:Attack
1600:Design
1591:Zodiac
1556:Square
1531:SHACAL
1526:SC2000
1486:Prince
1466:Nimbus
1461:NewDES
1446:MULTI2
1436:MISTY1
1379:LOKI (
1355:KHAZAD
1350:KeeLoq
1345:KASUMI
1340:Kalyna
1225:CLEFIA
1210:CIKS-1
1170:Anubis
1021:Common
919:Bruges
917:2000.
841:
806:
621:
275:S-box
245:modulo
224:and a
138:Rounds
2141:(PRN)
1791:Slide
1647:Round
1632:P-box
1627:S-box
1586:XXTEA
1546:Speck
1541:Simon
1536:SHARK
1516:SAFER
1501:REDOC
1426:Mercy
1385:89/91
1335:Iraqi
1300:G-DES
1290:FEA-M
1270:DES-X
1235:Cobra
1190:BATON
1175:Ascon
1155:3-Way
1146:Other
911:(PDF)
862:(PDF)
770:(PDF)
744:(PDF)
722:(PDF)
643:(PDF)
533:(PDF)
526:(PDF)
172:Magma
1919:CNSA
1778:Mod
1704:MITM
1476:NUSH
1431:MESH
1421:MARS
1295:FROG
1285:FEAL
1265:DEAL
1245:Crab
1230:CMEA
1137:XTEA
1122:SEED
1102:IDEA
1097:GOST
1082:ARIA
839:ISBN
804:ISBN
752:IACR
726:IACR
704:IACR
681:IACR
619:ISBN
598:help
502:IACR
202:USSR
166:The
59:USSR
1873:Tau
1833:XSL
1637:SPN
1581:xmx
1576:UES
1511:S-1
1496:RC2
1441:MMB
1320:ICE
1275:DFC
1132:TEA
1117:RC6
1112:RC5
1107:LEA
1059:SM4
1040:DES
1030:AES
923:doi
829:doi
796:doi
210:DES
197:.
63:KGB
2345::
1401:M8
1396:M6
1383:,
1381:97
1280:E2
1046:,
837:.
802:.
750:.
746:.
724:.
702:.
683:.
679:.
675:.
589::
587:}}
583:{{
576:.
557:.
514:^
504:.
500:.
496:.
441:.
419:8
411:7
403:6
395:5
387:4
379:3
371:2
363:1
355:#
336:8
328:7
320:6
312:5
304:4
296:3
288:2
280:1
272:#
259:.
142:32
84:,
61:,
1985:e
1978:t
1971:v
1780:n
1764:)
1760:(
1727:)
1723:(
1700:)
1696:(
1687:)
1683:(
1673:)
1669:(
1491:Q
1387:)
1050:)
1042:(
1015:)
1011:(
1001:e
994:t
987:v
937:.
925::
847:.
831::
812:.
798::
779:.
754:.
728:.
706:.
660:.
645:.
627:.
600:)
596:(
561:.
559:1
542:.
234:2
170:(
160:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.