834:
126:) – is the organizational and technical processes for first registering and authorizing access rights in the configuration phase, and then in the operation phase for identifying, authenticating and controlling individuals or groups of people to have access to applications, systems or networks based on previously authorized access rights. Identity management (IdM) is the task of controlling information about users on computers. Such information includes information that
335:(SP). When a user needs to access some service controlled by SP, they first authenticate against the IdP. Upon successful authentication, the IdP sends a secure "assertion" to the Service Provider. "SAML assertions, specified using a markup language intended for describing security assertions, can be used by a verifier to make a statement to a relying party about the identity of a claimant. SAML assertions may optionally be digitally signed."
225:
645:, otherwise known as identity and access management (IAM) is an identity security framework that works to authenticate and authorize user access to resources such as applications, data, systems, and cloud platforms. It seeks to ensure only the right people are being provisioned to the right tools, and for the right reasons. As our digital ecosystem continues to advance, so does the world of identity management.
379:: Roles are groups of operations and/or other roles. Users are granted roles often related to a particular job or job function. Roles are granted authorizations, effectively authorizing all users which have been granted the role. For example, a user administrator role might be authorized to reset a user's password, while a system administrator role might have the ability to assign a user to a specific server.
140:
304:
Organizations continue to add services for both internal users and by customers. Many such services require identity management to properly provide these services. Increasingly, identity management has been partitioned from application functions so that a single identity can serve many or even all of
295:
When organizations deploy an identity management process or system, their motivation is normally not primarily to manage a set of identities, but rather to grant appropriate access rights to those entities via their identities. In other words, access management is normally the motivation for identity
134:
to access and/or perform. It also includes the management of descriptive information about the user and how and by whom that information can be accessed and modified. In addition to users, managed entities typically include hardware and network resources and even applications. The diagram below shows
692:
me-identity: The 'me' (G. H. Mead) is the organised set of attitudes of others which one assumes. It is coconstituted by the 'I', the first person perspective, which incorporates the variety of third person perspectives it encounters and develops. Thus, the 'me' is continuously reconstituted in the
284:
User access enables users to assume a specific digital identity across applications, which enables access controls to be assigned and evaluated against this identity. The use of a single identity for a given user across multiple systems eases tasks for administrators and users. It simplifies access
1311:
Identity and access management (IAM) is the security discipline that enables the right individuals to access the right resources at the right times for the right reasons. IAM addresses the mission-critical need to ensure appropriate access to resources across increasingly heterogeneous technology
886:
systems operate to prove the online "identity" of a subject. Therefore, in IT terms, one can consider identity management as the management of information (as held in a directory) that represents items identified in real life (e.g. users, organizations, devices, services, etc.). The design of such
219:
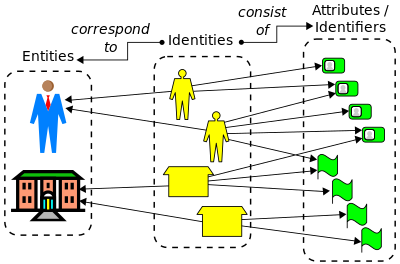
In general, an entity (real or virtual) can have multiple identities and each identity can encompass multiple attributes, some of which are unique within a given name space. The diagram below illustrates the conceptual relationship between identities and entities, as well as between identities and
326:
Identity federation comprises one or more systems that share user access and allow users to log in based on authenticating against one of the systems participating in the federation. This trust between several systems is often known as "Circle of Trust". In this setup, one system acts as the
291:
is crucial in this process, as it involves protecting the integrity and confidentiality of user credentials and preventing unauthorized access. Implementing robust authentication mechanisms, such as multi-factor authentication (MFA), regular security audits, and strict access controls, helps
894:
technology closely. In the environment of static web pages and static portals of the early 1990s, corporations investigated the delivery of informative web content such as the "white pages" of employees. Subsequently, as the information changed (due to employee turnover, provisioning and
373:: Managing authorization information that defines what operations an entity can perform in the context of a specific application. For example, one user might be authorized to enter a sales order, while a different user is authorized to approve the credit request for that order.
385:: Delegation allows local administrators or supervisors to perform system modifications without a global administrator or for one user to allow another to perform actions on their behalf. For example, a user could delegate the right to manage office-related information.
311:
Services often require access to extensive information about a user, including address books, preferences, entitlements and contact information. Since much of this information is subject to privacy and/or confidentiality requirements, controlling access to it is vital.
473:
SWIFT focuses on extending identity functions and federation to the network while addressing usability and privacy concerns and leverages identity technology as a key to integrate service and transport infrastructures for the benefit of users and the providers.
599:
Since 2016 Identity and Access
Management professionals have their own professional organization, IDPro. In 2018 the committee initiated the publication of An Annotated Bibliography, listing a number of important publications, books, presentations and videos.
238:(attribute values). These properties record information about the object, either for purposes external to the model or to operate the model, for example in classification and retrieval. A "pure identity" model is strictly not concerned with the external
56:), is a framework of policies and technologies to ensure that the right users (that are part of the ecosystem connected to or within an enterprise) have the appropriate access to technology resources. IdM systems fall under the overarching umbrellas of
215:
are unique, or that such identities bear a specific relationship to corresponding entities in the real world. Such an axiomatic model expresses "pure identity" in the sense that the model is not constrained by a specific application context.
261:
such as managing access or entitlement, but which are simply stored, maintained and retrieved, without special treatment by the model. The absence of external semantics within the model qualifies it as a "pure identity" model.
688:
Ipse-identity: The ipse-identity perspective is the first-person perspective on what constitutes oneself as a continuous being (idem) in the course of time, while experiencing multiplicity and difference in the here and
359:
In addition to creation, deletion, modification of user identity data either assisted or self-service, identity management controls ancillary entity data for use by applications, such as contact information or location.
592:(IGA). Commercial software tools exist to help automate and simplify such organizational-level identity management functions. How effectively and appropriately such tools are used falls within scope of broader
583:
In each organization there is normally a role or department that is responsible for managing the schema of digital identities of their staff and their own objects, which are represented by object identities or
64:. Identity and access management systems not only identify, authenticate, and control access for individuals who will be utilizing IT resources but also the hardware and applications employees need to access.
648:"Identity management" and "access and identity management" (or AIM) are terms that are used interchangeably under the title of identity management while identity management itself falls under the umbrella of
253:
which the model may use internally to verify some aspect of the identity in satisfaction of an external purpose. To the extent that the model expresses such semantics internally, it is not a pure model.
546:), such as the elaboration of a framework for identity management, including the definition of identity-related terms. The published standards and current work items includes the following:
867:
In general, electronic IdM can be said to cover the management of any form of digital identities. The focus on identity management goes back to the development of directories, such as
308:
For internal use identity management is evolving to control access to all digital assets, including devices, network equipment, servers, portals, content, applications and/or products.
67:
IdM addresses the need to ensure appropriate access to resources across increasingly heterogeneous technology environments and to meet increasingly rigorous compliance requirements.
740:
Authorization and non-repudiation: Authorization of documents or transaction with e-ID and most often with digital signature based on e-ID. Generates non-repudiation and receipts.
367:: Verification that an entity is who/what it claims to be using a password, biometrics such as a fingerprint, or distinctive behavior such as a gesture pattern on a touchscreen.
2536:
685:
Idem-identity: A third-person (i.e., objectified) attribution of sameness. Such an objectified perspective can not only be taken towards others but also towards oneself.
166:
guidelines on protecting PII. It can be interpreted as the codification of identity names and attributes of a physical instance in a way that facilitates processing.
188:
The service function: A system that delivers personalized, role-based, online, on-demand, multimedia (content), presence-based services to users and their devices.
2373:
2052:
Paintsil, Ebenezer; Fritsch, Lothar (2013), "Executable Model-Based Risk
Analysis Method for Identity Management Systems: Using Hierarchical Colored Petri Nets",
535:
749:
Identity-management systems, products, applications, and platforms are commercial
Identity-management solutions implemented for enterprises and organizations.
470:
PrimeLife develops concepts and technologies to help individuals to protect autonomy and retain control over personal information, irrespective of activities.
426:
services make heavy use of identity management. Helping users decide how to manage access to their personal information has become an issue of broad concern.
882:
standard defined certificates carried identity attributes as two directory names: the certificate subject and the certificate issuer. X.509 certificates and
2125:
Røssvoll, Till
Halbach; Fritsch, Lothar (2013). "Trustworthy and Inclusive Identity Management for Applications in Social Media". In Kurosu, Masaaki (ed.).
265:
Identity management can thus be defined as a set of operations on a given identity model, or more generally, as a set of capabilities with reference to it.
593:
895:
de-provisioning), the ability to perform self-service and help-desk updates more efficiently morphed into what became known as
Identity Management today.
875:
serves to hold named objects that represent real-life "identified" entities, such as countries, organizations, applications, subscribers or devices. The
91:, the roles, and sometimes the permissions that identity grants, the protection of that identity, and the technologies supporting that protection (e.g.,
666:
Identity governance to ensure that user access is being granted according to appropriate access policies for onboarding and role/responsibility changes
542:, SC27 IT Security techniques WG5 Identity Access Management and Privacy techniques) is conducting some standardization work for identity management (
135:
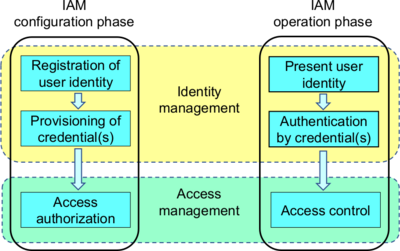
the relationship between the configuration and operation phases of IAM, as well as the distinction between identity management and access management.
80:, products, applications and platforms manage identifying and ancillary data about entities that include individuals, computer-related hardware, and
467:
The PICOS Project investigates and develops a state-of-the-art platform for providing trust, privacy and identity management in mobile communities.
2551:
2190:
697:
In
Bertino's and Takahashi's textbook, three categories of identity are defined that are to a degree overlapping with the FIDIS identity concepts:
1385:
1148:
2586:
2488:
2394:
2212:
2144:
2069:
1995:
588:(OID). The organizational policies and processes and procedures related to the oversight of identity management are sometimes referred to as
1842:
245:
The most common departure from "pure identity" in practice occurs with properties intended to assure some aspect of identity, for example a
2556:
2561:
2331:
2285:
389:
1421:
2351:
1573:"Avoiding Unintended Flows of Personally Identifiable Information : Enterprise Identity Management and Online Social Networks"
673:
These technologies can be combined using identity governance, which provides the foundation for automated workflows and processes.
437:
happens when thieves gain access to identity information – such as the personal details needed to get access to a bank account.
2591:
445:
Research related to the management of identity covers disciplines such as technology, social sciences, humanities and the law.
1087:
968:
382:
1736:
2531:
1133:
2268:
Gross, Ralph; Acquisti, Alessandro; Heinz, J. H. (2005). "Information revelation and privacy in online social networks".
1913:
285:
monitoring and verification and allows the organizations to minimize excessive privileges granted to one user. Ensuring
2581:
2377:
2270:
Workshop On
Privacy In The Electronic Society; Proceedings of the 2005 ACM workshop on Privacy in the electronic society
669:
Privileged access management to control and monitor access to highly privileged accounts, applications and system assets
292:
safeguard user identities and sensitive data. User access can be tracked from initiation to termination of user access.
2332:"Young People and Emerging Digital Services. An Exploratory Survey on Motivations, Perceptions and Acceptance of Risks"
1499:
Networks, Institute of
Medicine (US) Committee on Regional Health Data; Donaldson, Molla S.; Lohr, Kathleen N. (1994).
1163:
936:
461:
273:
77:
1474:
1346:
178:
The pure identity function: Creation, management and deletion of identities without regard to access or entitlements;
1888:
1404:
1324:
1257:"ACROSS: A generic framework for attribute-based access control with distributed policies for virtual organizations"
681:
Identity is conceptualized in three different modes, according to an analysis:from the FIDIS Network of
Excellence:
1178:
1158:
1128:
843:
636:
158:
is an entity's online presence, encompassing personal identifying information (PII) and ancillary information. See
1964:
1661:
1193:
962:
915:
883:
449:
376:
269:
2191:
http://www.fidis.net/fileadmin/fidis/deliverables/fidis-WP7-del7.14a-idem_meets_ipse_conceptual_explorations.pdf
663:
Access management/Single sign-on to verify users' identities before they can access the network and applications
276:
among multiple identity models. The process of reconciling accounts may also be referred to as De-provisioning.
224:
931:
926:
423:
328:
174:
In the real-world context of engineering online systems, identity management can involve five basic functions:
2160:
1938:
656:
1198:
1143:
139:
2433:"Identification practices in government: citizen surveillance and the quest for public service improvement"
1758:
1373:
Fred Carter, OECD Workshop on
Digital Identity Management, Trondheim, Norway, 9 May 2007 (PPT presentation)
1298:
1230:
74:) and "identity and access management" are used interchangeably in the area of identity access management.
1780:
1528:
1078:
789:
392:
96:
519:
Less specialized journals publish on the topic and for instance have special issues on Identity such as:
512:
1656:
1255:
Silva, Edelberto Franco; Muchaluat-Saade, Débora Christina; Fernandes, Natalia Castro (1 January 2018).
1168:
344:
235:
208:
2546:
1517:
1382:
716:
Identity management systems are concerned with the creation, the administration and the deployment of:
2552:
Identity management and information sharing in ISO 18876 Industrial automation systems and integration
464:
of the European Union from 2007 to 2013, several new projects related to Identity Management started.
1256:
793:
553:
ISO/IEC 24760-2 A Framework for Identity Management – Part 2: Reference architecture and requirements
258:
92:
81:
1533:
616:, or to a set of technologies that can be used for enterprise or cross-network identity management.
1188:
1153:
921:
185:
and its associated data used by a customer to log on to a service or services (a traditional view);
1864:
1446:
482:
Ongoing projects include Future of Identity in the Information Society (FIDIS), GUIDE, and PRIME.
2291:
2129:. Lecture Notes in Computer Science. Vol. 8006. Springer Berlin Heidelberg. pp. 68–77.
2001:
1123:
1038:
995:
903:
613:
321:
192:
2566:
2484:
2390:
2347:
2281:
2218:
2208:
2140:
2107:
2065:
1991:
1800:
1792:
1572:
1546:
1276:
1138:
1118:
1016:
761:
627:
585:
490:
413:
246:
57:
17:
2511:
2467:
2444:
2417:
2357:
2339:
2316:
2273:
2130:
2097:
2057:
2032:
1983:
1538:
1268:
1072:
1001:
990:
948:
777:
773:
757:
753:
332:
231:
155:
88:
1408:
1389:
1006:
Identity repository (directory services for the administration of user account attributes)
211:
can be constructed from a small set of axioms, for example that all identities in a given
61:
395:
is a prominent means used to exchange identity information between two identity domains.
850:
Please help update this article to reflect recent events or newly available information.
1203:
1108:
1103:
953:
785:
781:
769:
652:
and information privacy and privacy risk as well as usability and e-inclusion studies.
434:
396:
364:
250:
145:
127:
2406:"Nine principles for assessing whether privacy is protected in a surveillance society"
550:
ISO/IEC 24760-1 A framework for identity management – Part 1: Terminology and concepts
257:
Contrast this situation with properties that might be externally used for purposes of
2575:
2005:
1392:, Recommendations of the National Institute of Standards and Technology, January 2009
1208:
1113:
539:
370:
268:
In practice, identity management often expands to express how model content is to be
149:
131:
2250:
1383:
Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
2500:"Holistic Privacy-Preserving Identity Management System for the Internet of Things"
2295:
1028:
Next-generation systems – Composite Adaptive Directory Services (CADS) and CADS SDP
287:
2479:
Williamson, Graham; Yip, David; Sharni, Ilan; Spaulding, Kent (1 September 2009).
1370:
723:
Credentials: Data providing evidence for claims about identities or parts thereof.
1542:
1475:"What is identity management (ID management) ? – Definition from WhatIs.com"
1347:"What is identity management (ID management) ? – Definition from WhatIs.com"
1272:
130:
the identity of a user, and information that describes data and actions they are
2378:"Information Technology—Security Techniques—A Framework for Identity Management"
2135:
2061:
1744:
1500:
801:
765:
649:
619:
The following terms are used in relationship with "identity-management system":
2471:
1828:
2449:
2432:
2422:
2405:
2321:
2304:
2102:
2085:
1987:
1022:
419:
182:
2562:
Stop Remembering Password and Switch to Identity Management: Business Insider
2222:
2111:
1914:"What is identity management (ID management)? Definition from SearchSecurity"
1796:
1550:
1280:
1041:
of user access rights on web applications across otherwise untrusted networks
2277:
2084:
Fritsch, Lothar; Fuglerud, Kristin Skeide; Solheim, Ivar (1 December 2010).
872:
239:
212:
2516:
2499:
2498:
Bernal Bernabe, Jorge; Hernandez-Ramos, Jose L.; Skarmeta, Antonio (2017).
1831:, PostgreSQL: Introduction and Concepts, in Bruce Momjian, 21 November 1999
1586:
351:. Both of these languages also provide Single Sign on (SSO) capabilities.
296:
management and the two sets of processes are consequently closely related.
1808:
1804:
556:
ISO/IEC DIS 24760-3 A Framework for Identity Management – Part 3: Practice
505:
498:
343:
The most popular reference implementations of the SAML specifications are
1401:
1057:
1009:
891:
809:
805:
752:
Technologies, services, and terms related to identity management include
737:
Authentication: Is this the real user? Systems needs to provide evidence!
412:
concerns. Absent proper protections, the data may be used to implement a
100:
2387:
Oracle Identity Management: Governance, Risk and Compliance Architecture
2187:
D7.14a: Where idem-identity meets ipse-identity: Conceptual explorations
1312:
environments, and to meet increasingly rigorous compliance requirements.
409:
408:
Putting personal information onto computer networks necessarily raises
198:
Audit function: Monitor bottlenecks, malfunctions and suspect behavior.
2557:
50 Data Principles for Loosely-Coupled Identity Management: SlideShare
2037:
2020:
1843:"The 17 Best Identity Governance and Administration Platforms of 2018"
1737:"Creating a European Identity Management Architecture for eGovernment"
887:
systems requires explicit information and identity engineering tasks.
2547:
Secure Widespread Identities for Federated Telecommunications (SWIFT)
1183:
1067:
1045:
797:
1231:"What Is Identity and Access Management (IAM)? Webopedia Definition"
2343:
1173:
1062:
981:
906:
which fall under the category of identity management may include:
879:
876:
868:
813:
734:
Identification: Who is the user – used on logon or database lookup
448:
Decentralized identity management is identity management based on
1781:"Special Issue: Special section on: Digital identity management"
1766:
1694:"PrimeLife – Privacy and Identity Management in Europe for Life"
985:
890:
The evolution of identity management follows the progression of
817:
163:
159:
31:
2305:"A roadmap for research on identity in the information society"
1299:"Gartner IT Glossary > Identity and Access Management (IAM)"
2205:
Identity Management : concepts, technologies, and systems
1411:, The Center For Democracy & Technology, 14 September 2007
1081:– Identity standards targeted towards educational environments
827:
493:
that publish articles related to identity management include:
2532:
General Public Tutorial about Privacy and Identity Management
1722:
1516:
Burr, William E.; Dodson, Donna F.; Polk, W. Timothy (2006).
348:
27:
Technical and Policy systems to give users appropriate access
1707:
1978:
Rannenberg, Kai; Royer, Denis; Deuker, André, eds. (2009).
1693:
2185:
Hildebrandt, M., Koops, E. J., & de Vries, K. (2008).
2236:
726:
Attributes: Data describing characteristics of a subject.
1889:"What Is Identity Management and Access Control? | Okta"
1422:"What is IAM? Identity and access management explained"
693:
face of changing third person perspectives on the self.
148:
is the enforcement of access rights defined as part of
1075:– A consortium promoting federated identity management
234:, a given identity object consists of a finite set of
195:
to authenticate a user without knowing their password.
2127:
Human-Computer Interaction. Users and Contexts of Use
1723:"Home: Future of IDentity in the Information Society"
1371:
Functional requirements for privacy enhancing systems
2237:"FREE Verification App for 4.2 Billion Online Users"
2021:"The Clean Privacy Ecosystem of the Future Internet"
1759:"PRIME – Privacy and Identity Management for Europe"
704:"Our-Identity": What others and I define as identity
30:"IdAM" redirects here. For Tamil/Sanskrit word, see
1965:"Identity management as a component of IT Security"
1791:(3). Bradford: MCB University Press. 19 June 2009.
707:"Their-Identity": What others define as my identity
574:
ISO/IEC 29134 Privacy Impact Assessment Methodology
565:
ISO/IEC CD 29003 Identity Proofing and Verification
2431:Taylor, John A.; Lips, Miriam; Organ, Joe (2009).
1982:. Berlin, Heidelberg: Springer Berlin Heidelberg.
1619:
181:The user access (log-on) function: For example: a
1980:The Future of Identity in the Information Society
1643:
846:may be compromised due to out-of-date information
730:The purposes of identity management systems are:
2054:Trust, Privacy, and Security in Digital Business
230:In most theoretical and all practical models of
1607:
562:ISO/IEC 29146 A framework for access management
2207:. Takahashi, Kenji. Boston, MA: Artech House.
2056:, Springer Berlin Heidelberg, pp. 48–61,
712:Purposes for using identity management systems
720:Identifiers: Data used to identify a subject.
559:ISO/IEC 29115 Entity Authentication Assurance
191:Identity Federation: A system that relies on
8:
1502:Confidentiality and Privacy of Personal Data
87:IdM covers issues such as how users gain an
998:(Formally Microsoft Azure Active Directory)
594:governance, risk management, and compliance
2330:Lusoli, Wainer; Miltgen, Caroline (2009).
2515:
2448:
2421:
2320:
2303:Halperin, Ruth; Backhouse, James (2008).
2161:"What Is Identity and Access Management?"
2134:
2101:
2036:
1532:
1402:PII (Personally Identifiable Information)
2458:Taylor, John A. (2008). "Zero Privacy".
1587:"Working Groups | Identity Commons"
701:"Me-Identity": What I define as identity
2338:(EUR 23765 EN) (published March 2009).
2086:"Towards inclusive identity management"
1221:
1631:
1149:Identity threat detection and response
590:Identity Governance and Administration
1469:
1467:
1325:"identity management (ID management)"
7:
2336:JRC Scientific and Technical Reports
1292:
1290:
657:Identity and Access Management (IAM)
462:Seventh Research Framework Programme
2437:Identity in the Information Society
2410:Identity in the Information Society
2380:. ISO/IEC WD 24760 (Working draft).
2309:Identity in the Information Society
2090:Identity in the Information Society
1765:. 28 September 2006. Archived from
543:
506:Identity in the Information Society
1657:"Decentralized Identifiers (DIDs)"
1261:Future Generation Computer Systems
754:Microsoft Windows active directory
571:ISO/IEC 29101 Privacy Architecture
331:(IdP) and other system(s) acts as
25:
1044:Directory-enabled networking and
499:Ethics and Information Technology
70:The terms "identity management" (
1939:"History of Identity Management"
1620:Gross, Acquisti & Heinz 2005
1505:. National Academies Press (US).
1327:. SearchSecurity. 1 October 2013
1229:Stroud, Forrest (22 June 2015).
832:
223:
138:
1012:replication and synchronization
568:ISO/IEC 29100 Privacy framework
2251:"Identity management security"
2019:Fritsch, Lothar (March 2013).
1088:Central Authentication Service
969:Attribute based access control
824:Electronic identity management
655:There are three components of
305:an organization's activities.
120:identity and access management
46:identity and access management
18:Identity and Access Management
1:
2481:Identity Management: A Primer
1644:Halperin & Backhouse 2008
1608:Taylor, Lips & Organ 2009
1134:Identity verification service
633:Entitlement-management system
2587:Computer security procedures
2537:Identity Management Overview
1841:Canner, Ben (24 July 2018).
1763:Portal for the PRIME Project
1543:10.6028/NIST.SP.800-63v1.0.2
1273:10.1016/j.future.2017.07.049
959:Web single sign-on (Web SSO)
677:Modes of identity management
2136:10.1007/978-3-642-39265-8_8
2062:10.1007/978-3-642-40343-9_5
1865:"An Annotated Bibliography"
1164:Multi-factor authentication
937:Self-service password reset
78:Identity-management systems
2608:
2504:Mobile Information Systems
2472:10.1109/MSPEC.2008.4547499
2404:Pounder, C. N. M. (2008).
2315:(1) (published 2009): 71.
1179:Online identity management
1159:Mobile identity management
1129:Identity driven networking
1015:Directory virtualization (
991:Microsoft Active Directory
610:identity-management system
513:Surveillance & Society
319:
29:
2450:10.1007/s12394-009-0007-5
2423:10.1007/s12394-008-0002-2
2389:. Auerbach Publications.
2322:10.1007/s12394-008-0004-0
2103:10.1007/s12394-010-0075-6
1988:10.1007/978-3-642-01820-6
1785:Online Information Review
1662:World Wide Web Consortium
1194:Role-based access control
963:Role-based access control
916:User account provisioning
579:Organization implications
524:Online Information Review
450:decentralized identifiers
399:is another such protocol.
2203:Bertino, Elisa. (2010).
2167:. SailPoint Technologies
1945:. SailPoint Technologies
1525:NIST Special Publication
932:Password synchronization
927:Delegated administration
910:Management of identities
637:User provisioning system
623:Access-governance system
424:online social networking
2278:10.1145/1102199.1102214
1199:Self-sovereign identity
1144:Identity-based security
1025:scale directory systems
790:security token services
538:(and more specifically
2592:Management cybernetics
2385:Pohlman, M.B. (2008).
1741:istrg.som.surrey.ac.uk
1518:"Information Security"
1388:13 August 2009 at the
1079:Shibboleth (Internet2)
339:Popular SAML Languages
2416:(published 2009): 1.
2193:, accessed 2019-12-09
1571:Labitzke, Sebastian.
1407:28 April 2009 at the
1169:Mutual authentication
242:of these properties.
82:software applications
2517:10.1155/2017/6384186
745:Commercial solutions
414:surveillance society
288:user access security
259:information security
150:access authorization
97:digital certificates
2582:Identity management
1829:Object Id's (OID'S)
1769:on 10 October 2007.
1451:console.bluemix.net
1189:Password management
1154:Information privacy
1084:Global Trust Center
922:Workflow automation
918:and de-provisioning
643:Identity management
355:System capabilities
316:Identity federation
207:A general model of
112:Identity management
38:Identity management
2272:. pp. 71–80.
1845:. Solutions Review
1124:Federated identity
996:Microsoft Entra ID
976:Directory services
774:digital identities
762:identity providers
614:information system
604:Management systems
586:object identifiers
322:Federated identity
220:their attributes.
193:federated identity
2510:(6384186): 1–20.
2490:978-1-58347-093-0
2396:978-1-4200-7247-1
2214:978-1-60807-039-8
2189:. Brussel: FIDIS.
2146:978-3-642-39265-8
2071:978-3-642-40342-2
2038:10.3390/fi5010034
1997:978-3-540-88480-4
1721:FIDISCoord (DR).
1139:Identity provider
1119:Directory service
1017:Virtual directory
865:
864:
778:password managers
758:service providers
628:access management
491:Academic journals
456:European research
388:Interchange: The
329:Identity Provider
247:digital signature
93:network protocols
44:), also known as
16:(Redirected from
2599:
2521:
2519:
2494:
2475:
2454:
2452:
2427:
2425:
2400:
2381:
2369:
2367:
2365:
2360:on 16 March 2017
2356:. Archived from
2326:
2324:
2299:
2255:
2254:
2247:
2241:
2240:
2233:
2227:
2226:
2200:
2194:
2183:
2177:
2176:
2174:
2172:
2157:
2151:
2150:
2138:
2122:
2116:
2115:
2105:
2081:
2075:
2074:
2049:
2043:
2042:
2040:
2016:
2010:
2009:
1975:
1969:
1968:
1961:
1955:
1954:
1952:
1950:
1935:
1929:
1928:
1926:
1924:
1910:
1904:
1903:
1901:
1899:
1885:
1879:
1878:
1876:
1874:
1869:
1861:
1855:
1854:
1852:
1850:
1838:
1832:
1826:
1820:
1819:
1817:
1815:
1777:
1771:
1770:
1755:
1749:
1748:
1743:. Archived from
1733:
1727:
1726:
1718:
1712:
1711:
1704:
1698:
1697:
1690:
1684:
1681:
1675:
1674:
1672:
1670:
1653:
1647:
1641:
1635:
1629:
1623:
1617:
1611:
1605:
1599:
1598:
1596:
1594:
1583:
1577:
1576:
1568:
1562:
1561:
1559:
1557:
1536:
1522:
1513:
1507:
1506:
1496:
1490:
1489:
1487:
1485:
1471:
1462:
1461:
1459:
1457:
1447:"IBM Cloud Docs"
1443:
1437:
1436:
1434:
1432:
1418:
1412:
1399:
1393:
1380:
1374:
1368:
1362:
1361:
1359:
1357:
1343:
1337:
1336:
1334:
1332:
1321:
1315:
1314:
1308:
1306:
1294:
1285:
1284:
1252:
1246:
1245:
1243:
1241:
1226:
1073:Liberty Alliance
1033:Other categories
1002:NetIQ eDirectory
949:Password manager
860:
857:
851:
844:factual accuracy
836:
835:
828:
478:Ongoing projects
333:Service Provider
232:digital identity
227:
156:Digital identity
142:
21:
2607:
2606:
2602:
2601:
2600:
2598:
2597:
2596:
2572:
2571:
2541:Computer Weekly
2528:
2497:
2491:
2478:
2457:
2430:
2403:
2397:
2384:
2372:
2363:
2361:
2354:
2329:
2302:
2288:
2267:
2264:
2259:
2258:
2249:
2248:
2244:
2235:
2234:
2230:
2215:
2202:
2201:
2197:
2184:
2180:
2170:
2168:
2159:
2158:
2154:
2147:
2124:
2123:
2119:
2083:
2082:
2078:
2072:
2051:
2050:
2046:
2025:Future Internet
2018:
2017:
2013:
1998:
1977:
1976:
1972:
1963:
1962:
1958:
1948:
1946:
1937:
1936:
1932:
1922:
1920:
1912:
1911:
1907:
1897:
1895:
1887:
1886:
1882:
1872:
1870:
1867:
1863:
1862:
1858:
1848:
1846:
1840:
1839:
1835:
1827:
1823:
1813:
1811:
1779:
1778:
1774:
1757:
1756:
1752:
1735:
1734:
1730:
1720:
1719:
1715:
1708:"ist-swift.org"
1706:
1705:
1701:
1692:
1691:
1687:
1682:
1678:
1668:
1666:
1655:
1654:
1650:
1642:
1638:
1630:
1626:
1618:
1614:
1606:
1602:
1592:
1590:
1589:. Idcommons.org
1585:
1584:
1580:
1570:
1569:
1565:
1555:
1553:
1534:10.1.1.153.2795
1520:
1515:
1514:
1510:
1498:
1497:
1493:
1483:
1481:
1473:
1472:
1465:
1455:
1453:
1445:
1444:
1440:
1430:
1428:
1420:
1419:
1415:
1409:Wayback Machine
1400:
1396:
1390:Wayback Machine
1381:
1377:
1369:
1365:
1355:
1353:
1345:
1344:
1340:
1330:
1328:
1323:
1322:
1318:
1304:
1302:
1297:
1295:
1288:
1254:
1253:
1249:
1239:
1237:
1228:
1227:
1223:
1218:
1213:
1099:
1054:
901:
861:
855:
852:
849:
841:This article's
837:
833:
826:
786:security tokens
747:
714:
679:
606:
581:
533:
531:Standardization
488:
480:
458:
443:
432:
406:
357:
349:Simple-SAML.php
341:
324:
318:
302:
282:
205:
172:
109:
62:data management
35:
28:
23:
22:
15:
12:
11:
5:
2605:
2603:
2595:
2594:
2589:
2584:
2574:
2573:
2570:
2569:
2567:NIST SP 800-63
2564:
2559:
2554:
2549:
2544:
2534:
2527:
2526:External links
2524:
2523:
2522:
2495:
2489:
2476:
2455:
2428:
2401:
2395:
2382:
2370:
2352:
2327:
2300:
2287:978-1595932280
2286:
2263:
2260:
2257:
2256:
2242:
2228:
2213:
2195:
2178:
2152:
2145:
2117:
2096:(3): 515–538.
2076:
2070:
2044:
2011:
1996:
1970:
1956:
1930:
1905:
1880:
1856:
1833:
1821:
1772:
1750:
1747:on 8 May 2009.
1728:
1713:
1699:
1685:
1676:
1648:
1636:
1624:
1612:
1600:
1578:
1563:
1508:
1491:
1479:SearchSecurity
1463:
1438:
1413:
1394:
1375:
1363:
1351:SearchSecurity
1338:
1316:
1286:
1247:
1220:
1219:
1217:
1214:
1212:
1211:
1206:
1204:Single sign-on
1201:
1196:
1191:
1186:
1181:
1176:
1171:
1166:
1161:
1156:
1151:
1146:
1141:
1136:
1131:
1126:
1121:
1116:
1111:
1109:Authentication
1106:
1104:Access control
1100:
1098:
1095:
1094:
1093:
1092:NIST SP 800-63
1090:
1085:
1082:
1076:
1070:
1065:
1060:
1053:
1050:
1049:
1048:
1042:
1030:
1029:
1026:
1020:
1013:
1007:
1004:
999:
993:
988:
973:
972:
966:
960:
957:
954:Single sign-on
951:
943:Access control
940:
939:
934:
929:
924:
919:
900:
897:
863:
862:
840:
838:
831:
825:
822:
782:single sign-on
770:access control
746:
743:
742:
741:
738:
735:
728:
727:
724:
721:
713:
710:
709:
708:
705:
702:
695:
694:
690:
686:
678:
675:
671:
670:
667:
664:
640:
639:
634:
631:
624:
605:
602:
580:
577:
576:
575:
572:
569:
566:
563:
560:
557:
554:
551:
532:
529:
528:
527:
517:
516:
509:
502:
487:
484:
479:
476:
457:
454:
442:
439:
435:Identity theft
431:
430:Identity theft
428:
405:
402:
401:
400:
397:OpenID Connect
386:
380:
374:
368:
365:Authentication
356:
353:
340:
337:
320:Main article:
317:
314:
301:
298:
281:
278:
251:software token
204:
201:
200:
199:
196:
189:
186:
179:
171:
168:
146:Access control
108:
105:
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
2604:
2593:
2590:
2588:
2585:
2583:
2580:
2579:
2577:
2568:
2565:
2563:
2560:
2558:
2555:
2553:
2550:
2548:
2545:
2542:
2538:
2535:
2533:
2530:
2529:
2525:
2518:
2513:
2509:
2505:
2501:
2496:
2492:
2486:
2482:
2477:
2473:
2469:
2465:
2461:
2460:IEEE Spectrum
2456:
2451:
2446:
2442:
2438:
2434:
2429:
2424:
2419:
2415:
2411:
2407:
2402:
2398:
2392:
2388:
2383:
2379:
2375:
2371:
2359:
2355:
2353:9789279113307
2349:
2345:
2344:10.2791/68925
2341:
2337:
2333:
2328:
2323:
2318:
2314:
2310:
2306:
2301:
2297:
2293:
2289:
2283:
2279:
2275:
2271:
2266:
2265:
2261:
2252:
2246:
2243:
2238:
2232:
2229:
2224:
2220:
2216:
2210:
2206:
2199:
2196:
2192:
2188:
2182:
2179:
2166:
2165:sailpoint.com
2162:
2156:
2153:
2148:
2142:
2137:
2132:
2128:
2121:
2118:
2113:
2109:
2104:
2099:
2095:
2091:
2087:
2080:
2077:
2073:
2067:
2063:
2059:
2055:
2048:
2045:
2039:
2034:
2030:
2026:
2022:
2015:
2012:
2007:
2003:
1999:
1993:
1989:
1985:
1981:
1974:
1971:
1966:
1960:
1957:
1944:
1943:sailpoint.com
1940:
1934:
1931:
1919:
1915:
1909:
1906:
1894:
1890:
1884:
1881:
1866:
1860:
1857:
1844:
1837:
1834:
1830:
1825:
1822:
1810:
1806:
1802:
1798:
1794:
1790:
1786:
1782:
1776:
1773:
1768:
1764:
1760:
1754:
1751:
1746:
1742:
1738:
1732:
1729:
1724:
1717:
1714:
1709:
1703:
1700:
1695:
1689:
1686:
1680:
1677:
1665:. 8 June 2020
1664:
1663:
1658:
1652:
1649:
1645:
1640:
1637:
1633:
1628:
1625:
1621:
1616:
1613:
1609:
1604:
1601:
1588:
1582:
1579:
1574:
1567:
1564:
1552:
1548:
1544:
1540:
1535:
1530:
1526:
1519:
1512:
1509:
1504:
1503:
1495:
1492:
1480:
1476:
1470:
1468:
1464:
1452:
1448:
1442:
1439:
1427:
1423:
1417:
1414:
1410:
1406:
1403:
1398:
1395:
1391:
1387:
1384:
1379:
1376:
1372:
1367:
1364:
1352:
1348:
1342:
1339:
1326:
1320:
1317:
1313:
1300:
1293:
1291:
1287:
1282:
1278:
1274:
1270:
1266:
1262:
1258:
1251:
1248:
1236:
1235:webopedia.com
1232:
1225:
1222:
1215:
1210:
1209:User modeling
1207:
1205:
1202:
1200:
1197:
1195:
1192:
1190:
1187:
1185:
1182:
1180:
1177:
1175:
1172:
1170:
1167:
1165:
1162:
1160:
1157:
1155:
1152:
1150:
1147:
1145:
1142:
1140:
1137:
1135:
1132:
1130:
1127:
1125:
1122:
1120:
1117:
1115:
1114:Authorization
1112:
1110:
1107:
1105:
1102:
1101:
1096:
1091:
1089:
1086:
1083:
1080:
1077:
1074:
1071:
1069:
1066:
1064:
1061:
1059:
1056:
1055:
1051:
1047:
1043:
1040:
1037:
1036:
1035:
1034:
1027:
1024:
1021:
1018:
1014:
1011:
1008:
1005:
1003:
1000:
997:
994:
992:
989:
987:
983:
980:
979:
978:
977:
970:
967:
964:
961:
958:
955:
952:
950:
947:
946:
945:
944:
938:
935:
933:
930:
928:
925:
923:
920:
917:
914:
913:
912:
911:
907:
905:
898:
896:
893:
888:
885:
881:
878:
874:
870:
859:
847:
845:
839:
830:
829:
823:
821:
819:
815:
811:
807:
803:
799:
795:
791:
787:
783:
779:
775:
771:
767:
763:
759:
755:
750:
744:
739:
736:
733:
732:
731:
725:
722:
719:
718:
717:
711:
706:
703:
700:
699:
698:
691:
687:
684:
683:
682:
676:
674:
668:
665:
662:
661:
660:
658:
653:
651:
646:
644:
638:
635:
632:
629:
626:Identity and
625:
622:
621:
620:
617:
615:
612:refers to an
611:
603:
601:
597:
595:
591:
587:
578:
573:
570:
567:
564:
561:
558:
555:
552:
549:
548:
547:
545:
541:
540:ISO/IEC JTC 1
537:
530:
525:
522:
521:
520:
515:
514:
510:
508:
507:
503:
501:
500:
496:
495:
494:
492:
485:
483:
477:
475:
471:
468:
465:
463:
455:
453:
451:
446:
440:
438:
436:
429:
427:
425:
421:
417:
415:
411:
403:
398:
394:
391:
387:
384:
381:
378:
375:
372:
371:Authorization
369:
366:
363:
362:
361:
354:
352:
350:
346:
338:
336:
334:
330:
323:
315:
313:
309:
306:
299:
297:
293:
290:
289:
279:
277:
275:
271:
266:
263:
260:
255:
252:
248:
243:
241:
237:
233:
228:
226:
221:
217:
214:
210:
203:Pure identity
202:
197:
194:
190:
187:
184:
180:
177:
176:
175:
169:
167:
165:
161:
157:
153:
151:
147:
143:
141:
136:
133:
129:
128:authenticates
125:
121:
117:
116:ID management
113:
106:
104:
102:
98:
94:
90:
85:
83:
79:
75:
73:
68:
65:
63:
59:
55:
51:
47:
43:
39:
33:
19:
2540:
2507:
2503:
2483:. MC Press.
2480:
2463:
2459:
2440:
2436:
2413:
2409:
2386:
2362:. Retrieved
2358:the original
2335:
2312:
2308:
2269:
2245:
2231:
2204:
2198:
2186:
2181:
2169:. Retrieved
2164:
2155:
2126:
2120:
2093:
2089:
2079:
2053:
2047:
2031:(1): 34–45.
2028:
2024:
2014:
1979:
1973:
1959:
1947:. Retrieved
1942:
1933:
1921:. Retrieved
1917:
1908:
1896:. Retrieved
1892:
1883:
1871:. Retrieved
1859:
1847:. Retrieved
1836:
1824:
1812:. Retrieved
1788:
1784:
1775:
1767:the original
1762:
1753:
1745:the original
1740:
1731:
1716:
1702:
1688:
1679:
1667:. Retrieved
1660:
1651:
1639:
1627:
1615:
1603:
1591:. Retrieved
1581:
1566:
1554:. Retrieved
1524:
1511:
1501:
1494:
1482:. Retrieved
1478:
1454:. Retrieved
1450:
1441:
1429:. Retrieved
1425:
1416:
1397:
1378:
1366:
1354:. Retrieved
1350:
1341:
1329:. Retrieved
1319:
1310:
1303:. Retrieved
1264:
1260:
1250:
1238:. Retrieved
1234:
1224:
1032:
1031:
975:
974:
942:
941:
909:
908:
902:
889:
866:
856:January 2012
853:
842:
766:Web services
751:
748:
729:
715:
696:
680:
672:
654:
647:
642:
641:
618:
609:
607:
598:
589:
582:
534:
523:
518:
511:
504:
497:
489:
486:Publications
481:
472:
469:
466:
459:
447:
444:
433:
418:
407:
358:
342:
325:
310:
307:
303:
294:
286:
283:
267:
264:
256:
244:
229:
222:
218:
206:
173:
154:
144:
137:
123:
119:
115:
111:
110:
86:
76:
71:
69:
66:
53:
49:
45:
41:
37:
36:
1898:22 November
1873:6 September
1849:17 December
1632:Taylor 2008
1356:20 December
1305:2 September
1240:27 February
802:WS-Security
650:IT security
460:Within the
280:User access
270:provisioned
107:Definitions
58:IT security
2576:Categories
1814:29 January
1593:12 January
1556:10 October
1484:3 December
1456:3 December
1426:CSO Online
1216:References
1046:802.1X EAP
1039:Federation
1023:e-Business
871:, where a
420:Social web
383:Delegation
345:Shibboleth
274:reconciled
236:properties
183:smart card
132:authorized
2466:(7): 20.
2223:700220032
2112:1876-0678
2006:153140099
1809:676858452
1805:807197565
1797:1468-4527
1551:655513066
1529:CiteSeerX
1301:. Gartner
1296:Compare:
1281:0167-739X
1052:Standards
904:Solutions
899:Solutions
873:namespace
794:workflows
596:regimes.
240:semantics
213:namespace
103:, etc.).
101:passwords
2376:(2009).
2374:ISO, IEC
2364:17 March
1923:16 April
1918:Security
1893:okta.com
1431:24 April
1405:Archived
1386:Archived
1267:: 1–17.
1097:See also
1058:SAML 2.0
1010:Metadata
892:Internet
810:SAML 2.0
806:WS-Trust
544:ISO 2009
452:(DIDs).
441:Research
393:protocol
300:Services
209:identity
170:Function
89:identity
2443:: 135.
2296:9923609
2262:Sources
1669:22 June
1331:2 March
792:(STS),
410:privacy
404:Privacy
118:) – or
2487:
2393:
2350:
2294:
2284:
2221:
2211:
2171:12 May
2143:
2110:
2068:
2004:
1994:
1949:12 May
1803:
1795:
1549:
1531:
1279:
1184:OpenID
1068:OpenID
971:(ABAC)
965:(RBAC)
816:, and
798:OpenID
630:system
2292:S2CID
2002:S2CID
1868:(PDF)
1683:PICOS
1521:(PDF)
1174:OAuth
1063:OAuth
982:x.500
956:(SSO)
880:ITU-T
877:X.509
869:X.500
814:OAuth
377:Roles
2508:2017
2485:ISBN
2391:ISBN
2366:2009
2348:ISBN
2282:ISBN
2219:OCLC
2209:ISBN
2173:2021
2141:ISBN
2108:ISSN
2066:ISBN
1992:ISBN
1951:2021
1925:2023
1900:2020
1875:2019
1851:2019
1816:2021
1801:OCLC
1793:ISSN
1671:2020
1595:2013
1558:2015
1547:OCLC
1486:2018
1458:2018
1433:2024
1358:2019
1333:2017
1307:2016
1277:ISSN
1242:2019
986:LDAP
984:and
818:RBAC
689:now.
422:and
390:SAML
347:and
272:and
164:NIST
162:and
160:OECD
60:and
54:IdAM
32:Idam
2512:doi
2468:doi
2445:doi
2418:doi
2340:doi
2317:doi
2274:doi
2131:doi
2098:doi
2058:doi
2033:doi
1984:doi
1539:doi
1269:doi
884:PKI
608:An
536:ISO
249:or
124:IAM
72:IdM
52:or
50:IAM
42:IdM
2578::
2506:.
2502:.
2464:45
2462:.
2439:.
2435:.
2412:.
2408:.
2346:.
2334:.
2311:.
2307:.
2290:.
2280:.
2217:.
2163:.
2139:.
2106:.
2092:.
2088:.
2064:,
2027:.
2023:.
2000:.
1990:.
1941:.
1916:.
1891:.
1807:,
1799:.
1789:33
1787:.
1783:.
1761:.
1739:.
1673:.
1659:.
1545:.
1537:.
1527:.
1523:.
1477:.
1466:^
1449:.
1424:.
1349:.
1309:.
1289:^
1275:.
1265:78
1263:.
1259:.
1233:.
820:.
812:,
808:,
804:,
800:,
796:,
788:,
784:,
780:,
776:,
772:,
768:,
764:,
760:,
756:,
659::
416:.
152:.
99:,
95:,
84:.
2543:)
2539:(
2520:.
2514::
2493:.
2474:.
2470::
2453:.
2447::
2441:1
2426:.
2420::
2414:1
2399:.
2368:.
2342::
2325:.
2319::
2313:1
2298:.
2276::
2253:.
2239:.
2225:.
2175:.
2149:.
2133::
2114:.
2100::
2094:3
2060::
2041:.
2035::
2029:5
2008:.
1986::
1967:.
1953:.
1927:.
1902:.
1877:.
1853:.
1818:.
1725:.
1710:.
1696:.
1646:.
1634:.
1622:.
1610:.
1597:.
1575:.
1560:.
1541::
1488:.
1460:.
1435:.
1360:.
1335:.
1283:.
1271::
1244:.
1019:)
858:)
854:(
848:.
526:.
122:(
114:(
48:(
40:(
34:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.