24:
181:
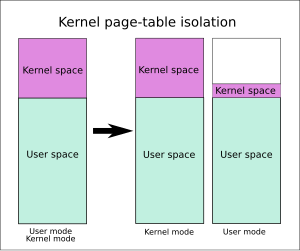
KPTI fixes these leaks by separating user-space and kernel-space page tables entirely. One set of page tables includes both kernel-space and user-space addresses same as before, but it is only used when the system is running in kernel mode. The second set of page tables for use in user mode contains
109:(KASLR), which makes it more difficult to exploit other kernel vulnerabilities, which relies on kernel address mappings remaining hidden from user space. Despite prohibiting access to these kernel mappings, it turns out that there are several
116:
KAISER addressed these problems in KASLR by eliminating some sources of address leakage. Whereas KASLR merely prevents address mappings from leaking, KAISER also prevents the data from leaking, thereby covering the
Meltdown case.
27:
One set of page table for use in kernel mode includes both kernel-space and user-space. The second set of page table for use in user mode contains a copy of user-space and a minimal set of kernel-space handling system calls and
200:
The overhead was measured to be 0.28% according to KAISER's original authors; a Linux developer measured it to be roughly 5% for most workloads and up to 30% in some cases, even with the PCID optimization; for database engine
173:
x86 processors are not currently known to be affected by
Meltdown and don't need KPTI to mitigate them. However, AMD processors are still susceptible to KASLR bypass when KPTI is disabled.
102:), a technique conceived in 2016 and published in June 2017 back when Meltdown was not known yet. KAISER makes it harder to defeat KASLR, a 2014 mitigation for a much less severe issue.
1030:
826:
527:
498:
232:
KPTI can partially be disabled with the "nopti" kernel boot option. Also provisions were created to disable KPTI if newer processors fix the information leaks.
182:
a copy of user-space and a minimal set of kernel-space mappings that provides the information needed to enter or exit system calls, interrupts and exceptions.
120:
KPTI is based on KAISER. Without KPTI enabled, whenever executing user-space code (applications), Linux would also keep its entire kernel memory mapped in
106:
67:
297:
800:
315:
759:
708:
668:
607:
550:
149:
52:
87:
167:
KPTI (conceptually based on KAISER) prevents
Meltdown by preventing most protected locations from being mapped to user space.
1015:
884:
968:
214:
160:. It was a far more severe vulnerability than the KASLR bypass that KAISER originally intended to fix: It was found that
190:
930:
226:
206:
909:
571:
380:
Gruss, Daniel; Lipp, Moritz; Schwarz, Michael; Fellner, Richard; Maurice, Clémentine; Mangard, Stefan (2017-06-24).
186:
1025:
1020:
624:
253:
643:
949:
164:
of kernel memory could also be leaked, not just the locations of memory mappings, as previously thought.
113:
in modern processors that can leak the location of this memory, making it possible to work around KASLR.
17:
193:(TLB) flush can be avoided, but even then it comes at a significant performance cost, particularly in
480:
827:"Kernel panic! What are Meltdown and Spectre, the bugs affecting nearly every computer and device?"
528:"Kernel panic! What are Meltdown and Spectre, the bugs affecting nearly every computer and device?"
110:
863:
765:
714:
461:
423:
153:
442:
755:
736:
704:
664:
603:
79:
23:
597:
747:
696:
654:
910:"Initial Benchmarks Of The Performance Impact Resulting From Linux's x86 Security Changes"
400:
349:
274:
844:
499:"Apple has already partially implemented fix in macOS for 'KPTI' Intel CPU security flaw"
684:
Gruss, Daniel; Maurice, Clémentine; Fogh, Anders; Lipp, Moritz; Mangard, Stefan (2016).
546:
157:
133:
1009:
995:
769:
693:
Proceedings of the 2016 ACM SIGSAC Conference on
Computer and Communications Security
651:
Proceedings of the 2016 ACM SIGSAC Conference on
Computer and Communications Security
124:, although protected from access. The advantage is that when the application makes a
718:
868:
476:
48:
864:"Kernel-memory-leaking Intel processor design flaw forces Linux, Windows redesign"
209:
processor was 7–17% (or 16–23% without PCID), while a full benchmark lost 13–19% (
210:
125:
889:
202:
121:
71:
950:"VM Performance Showing Mixed Impact With Linux 4.15 KPTI Patches – Phoronix"
74:
and kernel space memory. KPTI was merged into Linux kernel version 4.15, and
700:
659:
137:
129:
885:"heads up: Fix for intel hardware bug will lead to performance regressions"
783:
914:
218:
75:
1000:
801:"Spectre, Meltdown: Critical CPU Security Flaws Explained – ExtremeTech"
316:"Spectre, Meltdown: Critical CPU Security Flaws Explained – ExtremeTech"
751:
484:
194:
931:"Linux Gaming Performance Doesn't Appear Affected By The x86 PTI Work"
685:
572:"Linux kernel 3.14, Section 1.7. Kernel address space randomization"
381:
644:"Breaking Kernel Address Space Layout Randomization with Intel TSX"
404:
353:
278:
222:
100:
Kernel
Address Isolation to have Side-channels Efficiently Removed
83:
56:
22:
737:"Practical Timing Side Channel Attacks against Kernel Space ASLR"
254:"Further Analyzing The Intel CPU "x86 PTI Issue" On More Systems"
547:"#FunFact: We submitted #KAISER to #bhusa17 and got it rejected"
996:
17. Page Table
Isolation (PTI) - The Linux Kernel documentation
298:"OS Makers Preparing Patches for Secret Intel CPU Security Bug"
848:
225:
slowed by 6–7%. Linux kernel compilation slowed down by 5% on
170:
63:
60:
599:
Architectural and
Operating System Support for Virtual Memory
903:
901:
132:
is received, kernel page tables are always present, so most
86:
released similar updates. KPTI does not address the related
66:) and improves kernel hardening against attempts to bypass
596:
Bhattacharjee, Abhishek; Lustig, Daniel (2017-09-29).
247:
245:
695:. CCS '16. New York, NY, USA: ACM. pp. 368–379.
653:. CCS '16. New York, NY, USA: ACM. pp. 380–392.
477:"Windows 17035 Kernel ASLR/VA Isolation In Practice"
279:"The current state of kernel page-table isolation"
642:Jang, Yeongjin; Lee, Sangho; Kim, Taesoo (2016).
98:The KPTI patches were based on KAISER (short for
602:. Morgan & Claypool Publishers. p. 56.
389:. Engineering Secure Software and Systems 2017.
78:to Linux kernels 4.14.11, 4.9.75, and 4.4.110.
969:"Linux KPTI performance hit on real workloads"
625:"KPTI Intel Chip Flaw Exposes Security Risks"
152:vulnerability was published, known to affect
8:
862:Leyden, John; Williams, Chris (2018-01-02).
735:Hund, R.; Willems, C.; Holz, T. (May 2013).
140:, page-table swapping, etc) can be avoided.
744:2013 IEEE Symposium on Security and Privacy
354:"KAISER: hiding the kernel from user space"
16:"KPTI" redirects here. For other uses, see
205:the impact on read-only tests on an Intel
658:
107:kernel address space layout randomization
68:kernel address space layout randomization
892:development mailing list (pgsql-hackers)
1031:Transient execution CPU vulnerabilities
241:
197:-heavy and interrupt-heavy workloads.
70:(KASLR). It works by better isolating
845:"An Update on AMD Processor Security"
521:
519:
269:
267:
217:). Many benchmarks have been done by
7:
967:Velvindron, Loganaden (2018-01-04).
730:
728:
405:"Kernel page-table isolation merged"
375:
373:
371:
369:
367:
344:
342:
340:
338:
336:
623:Kerner, Sean Michael (2018-01-03).
460:Kroah-Hartman, Greg (2018-01-05).
441:Kroah-Hartman, Greg (2018-01-05).
422:Kroah-Hartman, Greg (2018-01-02).
105:In 2014, the Linux kernel adopted
14:
948:Larabel, Michael (2018-01-03).
929:Larabel, Michael (2018-01-02).
908:Larabel, Michael (2018-01-02).
686:"Prefetch Side-Channel Attacks"
553:from the original on 2018-01-08
296:Cimpanu, Catalin (2018-01-03).
252:Larabel, Michael (2018-01-03).
185:On processors that support the
144:Meltdown vulnerability and KPTI
53:Meltdown security vulnerability
825:Coldewey, Devin (2018-01-04).
526:Coldewey, Devin (2018-01-04).
383:KASLR is Dead: Long Live KASLR
1:
883:Freund, Andres (2018-01-02).
545:Gruss, Daniel (2018-01-03).
191:translation lookaside buffer
187:process-context identifiers
51:feature that mitigates the
33:Kernel page-table isolation
1047:
15:
462:"Linux 4.4.110 Changelog"
424:"Linux 4.14.11 Changelog"
1001:KPTI documentation patch
475:@aionescu (2017-11-14).
443:"Linux 4.9.75 Changelog"
701:10.1145/2976749.2978356
660:10.1145/2976749.2978321
128:into the kernel or an
29:
1016:Linux kernel features
148:In January 2018, the
26:
18:KPTI (disambiguation)
973:Loganaden Velvindron
746:. pp. 191–205.
560:– via Twitter.
136:-related overheads (
111:side-channel attacks
94:Background on KAISER
43:, previously called
752:10.1109/sp.2013.23
55:(affecting mainly
30:
761:978-0-7695-4977-4
710:978-1-4503-4139-4
670:978-1-4503-4139-4
609:978-1-62705-933-6
576:kernelnewbies.org
302:Bleeping Computer
134:context switching
1038:
1026:X86 architecture
983:
982:
980:
979:
964:
958:
957:
945:
939:
938:
926:
920:
919:
905:
896:
895:
880:
874:
873:
859:
853:
852:
841:
835:
834:
822:
816:
815:
813:
812:
797:
791:
790:
788:
780:
774:
773:
741:
732:
723:
722:
690:
681:
675:
674:
662:
648:
639:
633:
632:
620:
614:
613:
593:
587:
586:
584:
583:
568:
562:
561:
559:
558:
542:
536:
535:
523:
514:
513:
511:
510:
505:. 3 January 2018
495:
489:
488:
472:
466:
465:
457:
451:
450:
438:
432:
431:
419:
413:
412:
401:Corbet, Jonathan
397:
391:
390:
388:
377:
362:
361:
350:Corbet, Jonathan
346:
331:
330:
328:
327:
312:
306:
305:
293:
287:
286:
275:Corbet, Jonathan
271:
262:
261:
249:
154:Intel's x86 CPUs
1046:
1045:
1041:
1040:
1039:
1037:
1036:
1035:
1006:
1005:
992:
987:
986:
977:
975:
966:
965:
961:
947:
946:
942:
928:
927:
923:
907:
906:
899:
882:
881:
877:
861:
860:
856:
843:
842:
838:
824:
823:
819:
810:
808:
799:
798:
794:
786:
782:
781:
777:
762:
739:
734:
733:
726:
711:
688:
683:
682:
678:
671:
646:
641:
640:
636:
622:
621:
617:
610:
595:
594:
590:
581:
579:
570:
569:
565:
556:
554:
544:
543:
539:
525:
524:
517:
508:
506:
497:
496:
492:
474:
473:
469:
459:
458:
454:
440:
439:
435:
421:
420:
416:
399:
398:
394:
386:
379:
378:
365:
348:
347:
334:
325:
323:
314:
313:
309:
295:
294:
290:
273:
272:
265:
251:
250:
243:
238:
179:
146:
96:
90:vulnerability.
21:
12:
11:
5:
1044:
1042:
1034:
1033:
1028:
1023:
1021:Virtual memory
1018:
1008:
1007:
1004:
1003:
998:
991:
990:External links
988:
985:
984:
959:
940:
921:
897:
875:
854:
836:
817:
792:
775:
760:
724:
709:
676:
669:
634:
615:
608:
588:
563:
537:
515:
490:
483:) – via
467:
452:
433:
414:
403:(2017-12-20).
392:
363:
352:(2017-11-15).
332:
307:
288:
277:(2017-12-20).
263:
240:
239:
237:
234:
178:
177:Implementation
175:
158:ARM Cortex-A75
145:
142:
95:
92:
13:
10:
9:
6:
4:
3:
2:
1043:
1032:
1029:
1027:
1024:
1022:
1019:
1017:
1014:
1013:
1011:
1002:
999:
997:
994:
993:
989:
974:
970:
963:
960:
955:
951:
944:
941:
936:
932:
925:
922:
917:
916:
911:
904:
902:
898:
893:
891:
886:
879:
876:
871:
870:
865:
858:
855:
851:. 2018-01-04.
850:
846:
840:
837:
832:
828:
821:
818:
806:
802:
796:
793:
785:
779:
776:
771:
767:
763:
757:
753:
749:
745:
738:
731:
729:
725:
720:
716:
712:
706:
702:
698:
694:
687:
680:
677:
672:
666:
661:
656:
652:
645:
638:
635:
630:
626:
619:
616:
611:
605:
601:
600:
592:
589:
577:
573:
567:
564:
552:
548:
541:
538:
533:
529:
522:
520:
516:
504:
500:
494:
491:
486:
482:
478:
471:
468:
463:
456:
453:
448:
444:
437:
434:
429:
425:
418:
415:
410:
406:
402:
396:
393:
385:
384:
376:
374:
372:
370:
368:
364:
359:
355:
351:
345:
343:
341:
339:
337:
333:
321:
317:
311:
308:
303:
299:
292:
289:
284:
280:
276:
270:
268:
264:
259:
255:
248:
246:
242:
235:
233:
230:
228:
224:
220:
216:
212:
208:
204:
198:
196:
192:
188:
183:
176:
174:
172:
168:
165:
163:
159:
155:
151:
143:
141:
139:
135:
131:
127:
123:
118:
114:
112:
108:
103:
101:
93:
91:
89:
85:
81:
77:
73:
69:
65:
62:
58:
54:
50:
46:
42:
38:
34:
25:
19:
976:. Retrieved
972:
962:
953:
943:
934:
924:
913:
888:
878:
869:The Register
867:
857:
839:
830:
820:
809:. Retrieved
807:. 2018-01-04
804:
795:
778:
743:
692:
679:
650:
637:
628:
618:
598:
591:
580:. Retrieved
578:. 2014-03-30
575:
566:
555:. Retrieved
540:
531:
507:. Retrieved
503:AppleInsider
502:
493:
470:
455:
446:
436:
427:
417:
408:
395:
382:
357:
324:. Retrieved
322:. 2018-01-04
319:
310:
301:
291:
282:
257:
231:
199:
184:
180:
169:
166:
161:
147:
119:
115:
104:
99:
97:
49:Linux kernel
44:
40:
36:
32:
31:
805:ExtremeTech
320:ExtremeTech
215:Broadwell-E
211:Coffee Lake
126:system call
122:page tables
28:interrupts.
1010:Categories
978:2018-01-05
890:PostgreSQL
831:TechCrunch
811:2018-01-05
784:"Meltdown"
582:2014-04-02
557:2018-01-08
532:TechCrunch
509:2018-01-03
447:kernel.org
428:kernel.org
326:2018-01-05
236:References
203:PostgreSQL
189:(PCID), a
76:backported
72:user space
770:215754624
138:TLB flush
130:interrupt
954:Phoronix
935:Phoronix
915:Phoronix
719:15973158
551:Archived
258:Phoronix
219:Phoronix
162:contents
150:Meltdown
485:Twitter
409:LWN.net
358:LWN.net
283:LWN.net
227:Haswell
207:Skylake
195:syscall
88:Spectre
80:Windows
47:) is a
768:
758:
717:
707:
667:
606:
45:KAISER
787:(PDF)
766:S2CID
740:(PDF)
715:S2CID
689:(PDF)
647:(PDF)
629:eWEEK
481:Tweet
387:(PDF)
223:Redis
84:macOS
57:Intel
756:ISBN
705:ISBN
665:ISBN
604:ISBN
213:vs.
156:and
82:and
64:CPUs
37:KPTI
849:AMD
748:doi
697:doi
655:doi
171:AMD
61:x86
59:'s
41:PTI
39:or
1012::
971:.
952:.
933:.
912:.
900:^
887:.
866:.
847:.
829:.
803:.
764:.
754:.
742:.
727:^
713:.
703:.
691:.
663:.
649:.
627:.
574:.
549:.
530:.
518:^
501:.
445:.
426:.
407:.
366:^
356:.
335:^
318:.
300:.
281:.
266:^
256:.
244:^
229:.
221:,
981:.
956:.
937:.
918:.
894:.
872:.
833:.
814:.
789:.
772:.
750::
721:.
699::
673:.
657::
631:.
612:.
585:.
534:.
512:.
487:.
479:(
464:.
449:.
430:.
411:.
360:.
329:.
304:.
285:.
260:.
35:(
20:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.