492:, and their solutions must be agreed upon by all nodes and reach consensus. The solutions are then used to validate transactions, add blocks and generate new bitcoins. Miners are rewarded for solving these puzzles and successfully adding new blocks. However, the Bitcoin-style mining process is very energy intensive because the proof of work shaped like a lottery mechanism. The underlying computational work has no other use but to provide security to the network that provides open access and has to work in adversarial conditions. Miners have to use a lot of energy to add a new block containing a transaction to the blockchain. The energy used in this competition is what fundamentally gives bitcoin its level of security and resistance to attacks. Also, miners have to invest computer hardwares that need large spaces as fixed cost.
4603:
4627:
241:
4615:
221:
417:
4573:
3474:
2396:
3498:
3486:
2406:
215:
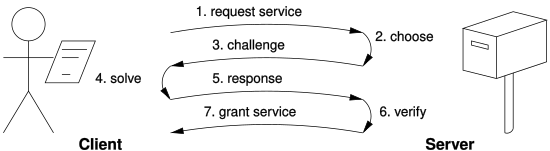
protocols assume a direct interactive link between the requester (client) and the provider (server). The provider chooses a challenge, say an item in a set with a property, the requester finds the relevant response in the set, which is sent back and checked by the provider. As the challenge is chosen
445:
Each block that is added to the blockchain, starting with the block containing a given transaction, is called a confirmation of that transaction. Ideally, merchants and services that receive payment in the cryptocurrency should wait for at least one confirmation to be distributed over the network,
195:
Whether PoW systems can actually solve a particular denial-of-service issue such as the spam problem is subject to debate; the system must make sending spam emails obtrusively unproductive for the spammer, but should also not prevent legitimate users from sending their messages. In other words, a
469:
Some PoWs claim to be ASIC-resistant, i.e. to limit the efficiency gain that an ASIC can have over commodity hardware, like a GPU, to be well under an order of magnitude. ASIC resistance has the advantage of keeping mining economically feasible on commodity hardware, but also contributes to the
151:
was designed as an anti-spam mechanism that required email senders to perform a small computational task, effectively proving that they expended resources (in the form of CPU time) before sending an email. This task was trivial for legitimate users but would impose a significant cost on spammers
403:
PoW. But in
Bitcoin, double-spend protection is provided by a decentralized P2P protocol for tracking transfers of coins, rather than the hardware trusted computing function used by RPoW. Bitcoin has better trustworthiness because it is protected by computation. Bitcoins are "mined" using the
446:
before assuming that the payment was done. The more confirmations that the merchant waits for, the more difficult it is for an attacker to successfully reverse the transaction in a blockchain—unless the attacker controls more than half the total network power, in which case it is called a
293:
computations that allow participants who know a secret, typically a private key, to generate cheap PoWs. The rationale is that mailing-list holders may generate stamps for every recipient without incurring a high cost. Whether such a feature is desirable depends on the usage scenario.
231:
protocols do not assume such a link: as a result, the problem must be self-imposed before a solution is sought by the requester, and the provider must check both the problem choice and the found solution. Most such schemes are unbounded probabilistic iterative procedures such as
196:
genuine user should not encounter any difficulties when sending an email, but an email spammer would have to expend a considerable amount of computing power to send out many emails at once. Proof-of-work systems are being used by other, more complex cryptographic systems such as
284:
if the client must perform few computations, but must collect some tokens from remote servers before querying the final service provider. In this sense, the work is not actually performed by the requester, but it incurs delays anyway because of the latency to get the required
130:
was carried out or that a computational puzzle was "solved", but deterring manipulation of data by establishing large energy and hardware-control requirements to be able to do so. Proof-of-work systems have been criticized by environmentalists for their energy consumption.
155:
Hashcash's system was based on the concept of finding a hash value that met certain criteria, a task that required computational effort and thus served as a "proof of work." The idea was that by making it computationally expensive to send large volumes of email,
216:
on the spot by the provider, its difficulty can be adapted to its current load. The work on the requester side may be bounded if the challenge-response protocol has a known solution (chosen by the provider), or is known to exist within a bounded search space.
466:(ASICs) for PoW. This trend toward mining pools and specialized ASICs has made mining some cryptocurrencies economically infeasible for most players without access to the latest ASICs, nearby sources of inexpensive energy, or other special advantages.
518:
in to continue mining without the use of renewable energy but they will not be allowed to expand or renew permits with the state, no new mining companies that do not completely use renewable energy will not also not be allowed to begin mining.
428:
cryptocurrency. Studies have estimated the total energy consumption of cryptocurrency mining. The PoW mechanism requires a vast amount of computing resources, which consume a significant amount of electricity. 2018 estimates from the
378:
based on "proof of useful work" (PoUW). Rather than miners consuming energy in solving complex, but essentially useless, puzzles to validate transactions, Ofelimos achieves consensus while simultaneously providing a decentralized
935:
87:
in a permissionless decentralized network, in which miners compete to append blocks and mine new currency, each miner experiencing a success probability proportional to the computational effort expended. PoW and PoS
1827:
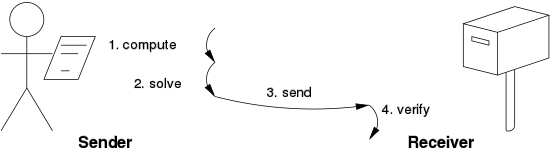
107:– the computation – must be moderately hard (yet feasible) on the prover or requester side but easy to check for the verifier or service provider. This idea is also known as a CPU cost function,
52:) that a certain amount of a specific computational effort has been expended. Verifiers can subsequently confirm this expenditure with minimal effort on their part. The concept was invented by
1898:
Describes a complete money system (including generation, storage, assay, and transfer) based on proof of work functions and the machine architecture problem raised by the use of these functions.
383:. The protocol is built around Doubly Parallel Local Search (DPLS), a local search algorithm that is used as the PoUW component. The paper gives an example that implements a variant of
68:
on a network by requiring some work from a service requester, usually meaning processing time by a computer. The term "proof of work" was first coined and formalized in a 1999 paper by
921:
831:
4553:
4383:
255:(with the same mean). A generic technique for reducing variance is to use multiple independent sub-challenges, as the average of multiple samples will have a lower variance.
1857:
139:
The concept of Proof of Work (PoW) has its roots in early research on combating spam and preventing denial-of-service attacks. One of the earliest implementations of PoW was
404:
Hashcash proof-of-work function by individual miners and verified by the decentralized nodes in the P2P bitcoin network. The difficulty is periodically adjusted to keep the
1603:
278:
where the computation speed is bound by main memory accesses (either latency or bandwidth), the performance of which is expected to be less sensitive to hardware evolution.
371:
1018:
1270:
1819:
4236:
4156:
3544:
1960:
3573:
2442:
2158:
1448:
1514:
496:
3434:
1668:
2117:
463:
870:
189:
including the colon and any amount of whitespace following it up to the digit '1') begins with 52 binary zeros, that is 13 hexadecimal zeros:
3414:
1400:
1246:
1186:
1110:
730:
1646:
818:
4607:
4100:
899:
3933:
470:
corresponding risk that an attacker can briefly rent access to a large amount of unspecialized commodity processing power to launch a
163:
One popular system, used in
Hashcash, uses partial hash inversions to prove that computation was done, as a goodwill token to send an
4229:
3424:
1930:
248:
1849:
998:
765:
736:
1965:
1595:
1312:
794:
335:
3537:
2825:
2011:
1738:
483:
247:
Known-solution protocols tend to have slightly lower variance than unbounded probabilistic protocols because the variance of a
73:
4432:
4141:
3626:
3578:
2435:
2269:
3928:
3404:
2830:
2112:
1331:
4593:
4222:
4146:
2876:
2535:
2286:
573:
375:
84:
4657:
4548:
4503:
4316:
3915:
3557:
3553:
2480:
2249:
359:
4427:
3530:
3318:
2950:
1417:
Juels, Ari; Brainard, John (1999). "Client puzzles: A cryptographic defense against connection depletion attacks".
1192:
313:
4652:
4543:
4172:
3811:
3490:
3478:
3444:
3419:
3399:
3074:
3064:
2871:
2428:
2264:
2102:
1902:
380:
322:
Partial hash inversion This paper formalizes the idea of a proof of work and introduces "the dependent idea of a
1850:"New York governor signs first-of-its-kind law cracking down on bitcoin mining — here's everything that's in it"
1692:
399:
network went online. Bitcoin is a proof-of-work digital currency that, like Finney's RPoW, is also based on the
4533:
4523:
4378:
4151:
3987:
3686:
3681:
3502:
3449:
3369:
3089:
61:
1138:
1481:
4528:
4518:
4321:
4281:
4274:
4264:
4259:
4074:
3894:
3127:
3003:
2983:
2598:
1437:
430:
323:
1627:
1503:
4269:
4182:
3568:
3384:
3230:
3117:
2955:
2940:
2925:
2851:
2792:
2751:
2470:
2363:
1224:
108:
4647:
4576:
4422:
4368:
4197:
3847:
3801:
3691:
3649:
3634:
3616:
3439:
3394:
3054:
3024:
2960:
2772:
2746:
2737:
2490:
2485:
2475:
2259:
2193:
2148:
2107:
1991:
1923:
1664:
1050:
568:
434:
240:
127:
76:
in 2004 through the idea of "reusable proof of work" using the 160-bit secure hash algorithm 1 (SHA-1).
2988:
374:
conference Crypto 2022 researchers presented a paper describing
Ofelimos, a blockchain protocol with a
4614:
1289:
1219:
Abliz, Mehmud; Znati, Taieb (December 2009). "A Guided Tour Puzzle for Denial of
Service Prevention".
4538:
4462:
3867:
3771:
3721:
3696:
3059:
2978:
2945:
2930:
2856:
1986:
1955:
252:
1547:
1229:
1021:, a specific comparison that shows how different classes of devices have different processing power.
862:
220:
4301:
4192:
4069:
4018:
3957:
3776:
3736:
3716:
3240:
2993:
2920:
2409:
2071:
1366:
926:
826:
553:
416:
4631:
4407:
4391:
4338:
4126:
4110:
4059:
3644:
3044:
2998:
2544:
2515:
2495:
2316:
2254:
2061:
1950:
1800:
1730:
1643:
1264:
1252:
1084:
643:
543:
1572:
1474:"An (almost) constant-effort solution-verification proof-of-work protocol based on Merkle trees"
1384:
1375:
167:. For instance, the following header represents about 2 hash computations to send a message to
4467:
4457:
4328:
4003:
3301:
2777:
2505:
2500:
2208:
2163:
1880:
1792:
1396:
1242:
1182:
1106:
726:
635:
306:
116:
65:
4402:
4090:
4044:
3806:
3459:
3409:
3389:
3245:
3225:
3195:
2915:
2910:
2891:
2648:
2399:
2322:
2066:
2026:
2021:
1916:
1782:
1772:
1722:
1388:
1234:
1174:
1096:
891:
716:
673:
625:
511:
507:
69:
4619:
4105:
4054:
4049:
3837:
3429:
3379:
3190:
2338:
2294:
2133:
2041:
1893:
1884:
1696:
1650:
1631:
1063:
1034:
994:
4477:
4397:
4358:
4306:
4291:
4095:
3823:
3255:
3185:
3135:
3039:
2811:
2782:
2554:
2549:
2520:
2451:
2376:
2353:
2143:
2001:
1981:
931:
757:
708:
563:
558:
538:
500:
269:
97:
89:
786:
4641:
4558:
4513:
4472:
4452:
4348:
4311:
4286:
4064:
3766:
3308:
2086:
2046:
2031:
1804:
1734:
1433:
1370:
1080:
1038:
700:
647:
548:
57:
41:
1710:
1256:
510:
enacted a two-year moratorium on cryptocurrency mining that does not completely use
111:, computational puzzle, or CPU pricing function. Another common feature is built-in
4508:
4353:
4343:
4333:
4296:
4245:
2706:
2593:
2381:
2229:
2224:
2168:
2076:
847:
the two best-known – and in the context of cryptocurrencies also most commonly used
425:
93:
38:
1777:
1760:
995:"Proof of Work can work - Fifth Workshop on the Economics of Information Security"
1101:
1095:. Lecture Notes in Computer Science. Vol. 2729. Springer. pp. 426–444.
678:
665:
612:
Lachtar, Nada; Elkhail, Abdulrahman Abu; Bacha, Anys; Malik, Hafiz (2020-07-01).
471:
447:
4487:
4177:
4023:
3952:
3948:
3857:
3454:
3343:
3215:
3079:
2371:
2153:
2056:
1178:
715:. Lecture Notes in Computer Science. Vol. 740. Springer. pp. 139–147.
592:
515:
459:
424:
Since the creation of
Bitcoin, proof-of-work has been the predominant design of
353:
176:
169:
1342:
1173:. Lecture Notes in Computer Science. Vol. 8976. Springer. pp. 49–62.
4447:
4417:
4412:
4373:
3374:
3265:
3210:
3097:
3049:
2970:
2672:
2667:
2465:
2138:
2036:
2006:
978:
Laurie, Ben; Clayton, Richard (May 2004). "Proof-of-work proves not to work".
958:
533:
405:
115:-structures that reward allocating computational capacity to the network with
1796:
1392:
721:
639:
630:
613:
499:
Erik Thedéen called on the EU to ban the proof of work model in favor of the
17:
4437:
3852:
3205:
3107:
3034:
2935:
2787:
2051:
1996:
1088:
704:
144:
123:
112:
53:
3639:
1726:
1238:
4482:
4442:
4131:
4028:
4013:
4008:
3998:
3962:
3882:
3796:
3676:
3200:
3180:
3160:
3150:
3145:
3069:
3029:
3008:
2866:
2846:
2840:
2820:
2797:
2767:
2697:
2687:
2682:
2642:
2633:
2618:
2613:
2608:
2510:
2348:
2343:
2081:
1890:
1709:
Savva
Shanaev; Arina Shuraeva; Mikhail Vasenin; Maksim Kuznetsov (2019).
400:
233:
157:
148:
1787:
1311:
Gabber, Eran; Jakobsson, Markus; Matias, Yossi; Mayer, Alain J. (1998).
3967:
3923:
3701:
3348:
3313:
3270:
3165:
3140:
3112:
2881:
2623:
2588:
2333:
2016:
1939:
1690:
tevador/RandomX: Proof of work algorithm based on random code execution
1163:
528:
489:
396:
384:
197:
80:
4363:
4136:
3877:
3872:
3842:
3832:
3791:
3786:
3781:
3761:
3756:
3731:
3726:
3711:
3671:
3323:
3250:
3170:
3155:
3102:
2901:
2835:
2727:
2677:
2658:
2178:
1689:
164:
2420:
1820:"Ban proof of work crypto mining to save energy, EU regulator says"
1759:
Ciaian, Pavel; Kancs, d’Artis; Rajcaniova, Miroslava (2021-10-21).
1711:"Cryptocurrency Value and 51% Attacks: Evidence from Event Studies"
670:
Secure
Information Networks: Communications and Multimedia Security
514:
as a power source for two years. Existing mining companies will be
3862:
3751:
3706:
3654:
3611:
3606:
3600:
3353:
3291:
3275:
3235:
3220:
3175:
2886:
2711:
2579:
2328:
2183:
1473:
1332:"Defending against denial-of-service attacks with puzzle auctions"
1130:
458:
Within the
Bitcoin community there are groups working together in
415:
258:
There are also fixed-cost functions such as the time-lock puzzle.
182:
922:"Analysis | Bye-Bye, Miners! How Ethereum's Big Change Will Work"
261:
Moreover, the underlying functions used by these schemes may be:
3977:
3972:
3943:
3938:
3902:
2603:
2525:
1624:
1131:"Exponential memory-bound functions for proof of work protocols"
614:"A Cross-Stack Approach Towards Defending Against Cryptojacking"
4218:
3526:
2424:
1912:
103:
A key feature of proof-of-work schemes is their asymmetry: the
3746:
3741:
3594:
3296:
3260:
2861:
1383:. Lecture Notes in Computer Science. Vol. 1318. pp.
863:"Proof of Work Explained in Simple Terms - The Chain Bulletin"
272:, as well as from high-end server to low-end portable devices.
181:
It is verified with a single computation by checking that the
1438:"New client puzzle outsourcing techniques for DoS resistance"
27:
System that regulates the formation of blocks on a blockchain
1164:"Cuckoo Cycle: A Memory Bound Graph-Theoretic Proof-of-Work"
239:
219:
72:
and Ari Juels. The concept was adapted to digital tokens by
1445:
11th ACM Conference on
Computer and Communications Security
1908:
268:
where the computation runs at the speed of the processor,
1568:
1540:"Cambridge Bitcoin Electricity Consumption Index (CBECI)"
1539:
1285:
1091:(2003). "On Memory-Bound Functions for Fighting Spam".
4384:
Cryptographically secure pseudorandom number generator
980:
Workshop on the
Economics of Information Security 2004
387:, a local search algorithm to solve Boolean problems.
4591:
1504:"Combinatorial Optimization via Proof-of-Useful-Work"
1221:
2009 Annual Computer Security Applications Conference
3514:
1301:
A popular PoW system. First announced in March 1997.
1037:; Burrows, Mike; Manasse, Mark; Wobber, Ted (2005).
4496:
4252:
4165:
4119:
4083:
4037:
3986:
3914:
3891:
3820:
3664:
3625:
3587:
3362:
3336:
3284:
3126:
3088:
3017:
2969:
2900:
2810:
2760:
2736:
2720:
2696:
2657:
2632:
2578:
2568:
2534:
2458:
2362:
2305:
2278:
2242:
2217:
2201:
2192:
2126:
2095:
1974:
1374:
208:There are two classes of proof-of-work protocols.
1569:"Cambridge Bitcoin Electricity Consumption Index"
488:Miners compete to solve crypto challenges on the
302:Here is a list of known proof-of-work functions:
959:"Hashcash - A Denial of Service Counter-Measure"
892:"The Only Crypto Story You Need, by Matt Levine"
709:"Pricing via Processing or Combatting Junk Mail"
1432:Waters, Brent; Juels, Ari; Halderman, John A.;
1313:"Curbing junk e-mail via secure classification"
1075:
1073:
813:
811:
589:On most Unix systems this can be verified with
433:equate Bitcoin's energy consumption to that of
1376:"Auditable metering with lightweight security"
1029:
1027:
973:
971:
319:Ong–Schnorr–Shamir signature broken by Pollard
4230:
3538:
2436:
1924:
1761:"The economic dependency of bitcoin security"
1594:Michael J. Casey; Paul Vigna (16 June 2014).
1330:Wang, Xiao-Feng; Reiter, Michael (May 2003).
326:", a "re-usable proof-of-work" (RPoW) system.
8:
1571:. Cambridge Center For Alternative Finance.
787:"What Is Proof of Work (PoW) in Blockchain?"
695:
693:
691:
689:
666:"Proofs of Work and Bread Pudding Protocols"
659:
657:
200:, which uses a system similar to Hashcash.
4237:
4223:
4215:
3545:
3531:
3523:
3519:
3515:
3497:
3281:
2575:
2443:
2429:
2421:
2198:
1931:
1917:
1909:
1905:for Simplified Payment Verification (SPV).
1339:IEEE Symposium on Security and Privacy '03
1269:: CS1 maint: location missing publisher (
1214:
1212:
1157:
1155:
1124:
1122:
420:Bitcoin electricity consumption as of 2021
1786:
1776:
1228:
1100:
1039:"Moderately hard, memory-bound functions"
720:
677:
629:
497:European Securities and Markets Authority
192:0000000000000756af69e2ffbdb930261873cd71
1596:"Short-Term Fixes To Avert "51% Attack""
1171:Financial Cryptography and Data Security
1019:How powerful was the Apollo 11 computer?
464:application-specific integrated circuits
185:hash of the stamp (omit the header name
4598:
2118:List of people in blockchain technology
1848:Sigalos, MacKenzie (23 November 2022).
993:Liu, Debin; Camp, L. Jean (June 2006).
672:. Kluwer Academic Publishers: 258–272.
604:
79:Proof of work was later popularized by
1715:The Journal of Alternative Investments
1575:from the original on 29 September 2020
1262:
1059:
1048:
664:Jakobsson, Markus; Juels, Ari (1999).
503:model due its lower energy emissions.
3415:Decentralized autonomous organization
1520:from the original on 9 September 2022
100:they are the most common mechanisms.
7:
3485:
2405:
1665:"The State of Cryptocurrency Mining"
1625:Overview of the Bitcoin mining pools
1093:Advances in Cryptology - CRYPTO 2003
938:from the original on 2 December 2021
857:
855:
1606:from the original on 15 August 2020
713:Advances in Cryptology — CRYPTO' 92
143:, created by British cryptographer
1671:from the original on 10 March 2020
1223:. Honolulu, HI. pp. 279–288.
920:Kharif, Olga (November 30, 2021).
618:IEEE Computer Architecture Letters
594::::9B760005E92F0DAE | openssl sha1
495:In January 2022 Vice-Chair of the
152:attempting to send bulk messages.
25:
3425:Distributed ledger technology law
1887: (archived December 22, 2007)
1478:Cryptology ePrint Archive, Report
1135:Cryptology ePrint Archive, Report
837:from the original on 27 June 2023
819:"Cryptocurrencies and blockchain"
64:and other service abuses such as
4625:
4613:
4601:
4572:
4571:
3496:
3484:
3473:
3472:
2404:
2395:
2394:
1903:Merkle Proof Standardised Format
758:"RPOW - Reusable Proofs of Work"
289:Finally, some PoW systems offer
251:is lower than the variance of a
1860:from the original on 2022-12-03
1830:from the original on 2022-04-19
1741:from the original on 2021-02-06
1550:from the original on 2020-03-02
1484:from the original on 2016-08-26
1454:from the original on 2021-04-21
1292:from the original on 2017-09-29
1198:from the original on 2017-07-05
1141:from the original on 2018-04-09
1001:from the original on 2017-08-20
902:from the original on 2023-04-07
873:from the original on 2023-04-01
797:from the original on 2024-01-17
768:from the original on 2023-06-19
739:from the original on 2017-11-26
484:Environmental impact of bitcoin
298:List of proof-of-work functions
119:in the form of cryptocurrency.
4433:Information-theoretic security
4142:NIST hash function competition
2270:2020 Twitter account hijacking
506:In November 2022 the state of
1:
4608:Free and open-source software
2113:List of bitcoin organizations
1778:10.1080/00036846.2021.1931003
1663:Vorick, David (13 May 2018).
122:The purpose of proof-of-work
4147:Password Hashing Competition
3558:message authentication codes
3554:Cryptographic hash functions
2287:The Rise and Rise of Bitcoin
1407:Updated version May 4, 1998.
1102:10.1007/978-3-540-45146-4_25
679:10.1007/978-0-387-35568-9_18
574:Consensus (computer science)
270:which greatly varies in time
126:is not proving that certain
92:) remain the two best known
4549:Message authentication code
4504:Cryptographic hash function
4317:Cryptographic hash function
4101:Merkle–Damgård construction
2481:Cryptographic hash function
2250:Bitcoin scalability problem
1818:Bateman, Tom (2022-01-19).
1511:IACR conference Crypto 2022
1179:10.1007/978-3-662-48051-9_4
381:optimization problem solver
366:Proof of useful work (PoUW)
360:Guided tour puzzle protocol
94:Sybil deterrence mechanisms
4674:
4428:Harvest now, decrypt later
957:Back, Adam (August 2002).
481:
474:against a cryptocurrency.
391:Bitcoin-type proof of work
307:Integer square root modulo
60:in 1993 as a way to deter
4567:
4544:Post-quantum cryptography
4214:
3564:
3522:
3518:
3468:
3445:Initial exchange offering
3420:Decentralized application
3400:Cryptocurrency in Nigeria
2390:
2265:2018 Bitcoin bomb threats
2260:2018 cryptocurrency crash
2103:List of bitcoin companies
1946:
62:denial-of-service attacks
4534:Quantum key distribution
4524:Authenticated encryption
4379:Random number generation
3895:key derivation functions
3450:List of cryptocurrencies
3337:Crypto service companies
3128:Cryptocurrency exchanges
1393:10.1007/3-540-63594-7_75
722:10.1007/3-540-48071-4_10
631:10.1109/LCA.2020.3017457
249:rectangular distribution
175:X-Hashcash: 1:52:380119:
48:) proves to others (the
44:in which one party (the
4529:Public-key cryptography
4519:Symmetric-key algorithm
4322:Key derivation function
4282:Cryptographic primitive
4275:Authentication protocol
4265:Outline of cryptography
4260:History of cryptography
4173:Hash-based cryptography
4075:Length extension attack
1602:. Wall Street Journal.
1472:Coelho, Fabien (2007).
1129:Coelho, Fabien (2005).
431:University of Cambridge
4270:Cryptographic protocol
4183:Message authentication
3385:Complementary currency
2486:Decentralized exchange
2471:Cryptocurrency tumbler
2364:Bitcoin in El Salvador
1727:10.3905/jai.2019.1.081
1381:Financial Cryptography
1317:Financial Cryptography
1058:Cite journal requires
478:Environmental concerns
454:ASICs and mining pools
421:
408:around a target time.
324:bread pudding protocol
244:
224:
4423:End-to-end encryption
4369:Cryptojacking malware
3440:Initial coin offering
3395:Cryptocurrency bubble
2921:Basic Attention Token
2491:Decentralized finance
2476:Cryptocurrency wallet
2149:Cryptocurrency wallet
2108:List of bitcoin forks
1966:Environmental effects
1644:What is an ASIC miner
1239:10.1109/ACSAC.2009.33
762:nakamotoinstitute.org
569:Proof of elapsed time
419:
243:
229:Solution–verification
223:
172:on January 19, 2038:
4539:Quantum cryptography
4463:Trusted timestamping
3435:Environmental impact
3405:Cryptocurrency scams
1987:Andreas Antonopoulos
1653:on digitaltrends.com
1367:Franklin, Matthew K.
1162:Tromp, John (2015).
591:echo -n 1:52:380119:
441:History modification
253:Poisson distribution
178::::9B760005E92F0DAE
96:. In the context of
83:as a foundation for
4302:Cryptographic nonce
4070:Side-channel attack
3090:Inactive currencies
927:The Washington Post
827:European Parliament
554:Proof of personhood
376:consensus mechanism
160:would be reduced.
4658:Energy consumption
4408:Subliminal channel
4392:Pseudorandom noise
4339:Key (cryptography)
4127:CAESAR Competition
4111:HAIFA construction
4060:Brute-force attack
2545:Proof of authority
2516:Non-fungible token
2496:Distributed ledger
2317:Bitcoin Foundation
2255:History of bitcoin
2062:Cameron Winklevoss
1695:2021-09-01 at the
1649:2018-05-22 at the
1634:on blockchain.info
1630:2020-04-21 at the
544:Proof of authority
490:Bitcoin blockchain
462:. Some miners use
422:
412:Energy consumption
245:
225:
213:Challenge–response
4589:
4588:
4585:
4584:
4468:Key-based routing
4458:Trapdoor function
4329:Digital signature
4210:
4209:
4206:
4205:
4004:ChaCha20-Poly1305
3821:Password hashing/
3512:
3511:
3332:
3331:
2989:First Digital USD
2806:
2805:
2506:Lightning Network
2418:
2417:
2310:
2238:
2237:
2209:Bitcoin Unlimited
2164:Lightning Network
1771:(49): 5738–5755.
1765:Applied Economics
1502:Fitzi, Matthias.
1434:Felten, Edward W.
1402:978-3-540-63594-9
1248:978-1-4244-5327-6
1188:978-3-662-48050-2
1112:978-3-540-40674-7
867:chainbulletin.com
732:978-3-540-57340-1
16:(Redirected from
4665:
4653:Cryptocurrencies
4630:
4629:
4628:
4618:
4617:
4606:
4605:
4604:
4597:
4575:
4574:
4403:Insecure channel
4239:
4232:
4225:
4216:
4091:Avalanche effect
4045:Collision attack
3588:Common functions
3547:
3540:
3533:
3524:
3520:
3516:
3500:
3499:
3488:
3487:
3476:
3475:
3460:Virtual currency
3410:Digital currency
3390:Crypto-anarchism
3282:
3035:HBAR (Hashgraph)
3018:Other currencies
2649:Ethereum Classic
2576:
2452:Cryptocurrencies
2445:
2438:
2431:
2422:
2408:
2407:
2398:
2397:
2323:Bitcoin Magazine
2308:
2199:
2067:Tyler Winklevoss
2027:Satoshi Nakamoto
1933:
1926:
1919:
1910:
1869:
1868:
1866:
1865:
1845:
1839:
1838:
1836:
1835:
1815:
1809:
1808:
1790:
1780:
1756:
1750:
1749:
1747:
1746:
1706:
1700:
1687:
1681:
1680:
1678:
1676:
1660:
1654:
1641:
1635:
1622:
1616:
1615:
1613:
1611:
1591:
1585:
1584:
1582:
1580:
1565:
1559:
1558:
1556:
1555:
1536:
1530:
1529:
1527:
1525:
1519:
1508:
1499:
1493:
1492:
1490:
1489:
1469:
1463:
1462:
1460:
1459:
1453:
1442:
1429:
1423:
1422:
1414:
1408:
1406:
1378:
1363:
1357:
1356:
1354:
1353:
1347:
1341:. Archived from
1336:
1327:
1321:
1320:
1308:
1302:
1300:
1298:
1297:
1281:
1275:
1274:
1268:
1260:
1232:
1216:
1207:
1206:
1204:
1203:
1197:
1168:
1159:
1150:
1149:
1147:
1146:
1126:
1117:
1116:
1104:
1085:Goldberg, Andrew
1077:
1068:
1067:
1061:
1056:
1054:
1046:
1031:
1022:
1016:
1010:
1009:
1007:
1006:
990:
984:
983:
975:
966:
965:
963:
954:
948:
947:
945:
943:
917:
911:
910:
908:
907:
888:
882:
881:
879:
878:
859:
850:
849:
844:
842:
836:
823:
815:
806:
805:
803:
802:
783:
777:
776:
774:
773:
754:
748:
747:
745:
744:
724:
697:
684:
683:
681:
661:
652:
651:
633:
609:
595:
588:
512:renewable energy
188:
171:
98:cryptocurrencies
70:Markus Jakobsson
21:
4673:
4672:
4668:
4667:
4666:
4664:
4663:
4662:
4638:
4637:
4636:
4626:
4624:
4612:
4602:
4600:
4592:
4590:
4581:
4563:
4492:
4248:
4243:
4202:
4161:
4120:Standardization
4115:
4106:Sponge function
4079:
4055:Birthday attack
4050:Preimage attack
4033:
3989:
3982:
3910:
3893:
3892:General purpose
3887:
3822:
3816:
3665:Other functions
3660:
3627:SHA-3 finalists
3621:
3583:
3560:
3551:
3513:
3508:
3464:
3430:Double-spending
3380:Blockchain game
3358:
3328:
3280:
3122:
3084:
3013:
2965:
2896:
2802:
2756:
2732:
2716:
2692:
2653:
2628:
2564:
2530:
2454:
2449:
2419:
2414:
2386:
2358:
2339:Canaan Creative
2309:(not exchanges)
2307:
2301:
2274:
2234:
2213:
2188:
2134:Bitcoin network
2122:
2091:
2042:Vitalik Buterin
1992:Brian Armstrong
1970:
1942:
1937:
1885:Wayback Machine
1881:Finney's system
1877:
1872:
1863:
1861:
1847:
1846:
1842:
1833:
1831:
1817:
1816:
1812:
1758:
1757:
1753:
1744:
1742:
1708:
1707:
1703:
1697:Wayback Machine
1688:
1684:
1674:
1672:
1662:
1661:
1657:
1651:Wayback Machine
1642:
1638:
1632:Wayback Machine
1623:
1619:
1609:
1607:
1593:
1592:
1588:
1578:
1576:
1567:
1566:
1562:
1553:
1551:
1538:
1537:
1533:
1523:
1521:
1517:
1506:
1501:
1500:
1496:
1487:
1485:
1471:
1470:
1466:
1457:
1455:
1451:
1440:
1431:
1430:
1426:
1416:
1415:
1411:
1403:
1365:
1364:
1360:
1351:
1349:
1345:
1334:
1329:
1328:
1324:
1310:
1309:
1305:
1295:
1293:
1283:
1282:
1278:
1261:
1249:
1230:10.1.1.597.6304
1218:
1217:
1210:
1201:
1199:
1195:
1189:
1166:
1161:
1160:
1153:
1144:
1142:
1128:
1127:
1120:
1113:
1079:
1078:
1071:
1057:
1047:
1033:
1032:
1025:
1017:
1013:
1004:
1002:
992:
991:
987:
977:
976:
969:
961:
956:
955:
951:
941:
939:
919:
918:
914:
905:
903:
890:
889:
885:
876:
874:
861:
860:
853:
840:
838:
834:
821:
817:
816:
809:
800:
798:
785:
784:
780:
771:
769:
756:
755:
751:
742:
740:
733:
699:
698:
687:
663:
662:
655:
611:
610:
606:
602:
590:
585:
582:
525:
486:
480:
456:
443:
414:
393:
368:
300:
206:
193:
186:
179:
168:
137:
37:) is a form of
28:
23:
22:
15:
12:
11:
5:
4671:
4669:
4661:
4660:
4655:
4650:
4640:
4639:
4635:
4634:
4622:
4610:
4587:
4586:
4583:
4582:
4580:
4579:
4568:
4565:
4564:
4562:
4561:
4556:
4554:Random numbers
4551:
4546:
4541:
4536:
4531:
4526:
4521:
4516:
4511:
4506:
4500:
4498:
4494:
4493:
4491:
4490:
4485:
4480:
4478:Garlic routing
4475:
4470:
4465:
4460:
4455:
4450:
4445:
4440:
4435:
4430:
4425:
4420:
4415:
4410:
4405:
4400:
4398:Secure channel
4395:
4389:
4388:
4387:
4376:
4371:
4366:
4361:
4359:Key stretching
4356:
4351:
4346:
4341:
4336:
4331:
4326:
4325:
4324:
4319:
4309:
4307:Cryptovirology
4304:
4299:
4294:
4292:Cryptocurrency
4289:
4284:
4279:
4278:
4277:
4267:
4262:
4256:
4254:
4250:
4249:
4244:
4242:
4241:
4234:
4227:
4219:
4212:
4211:
4208:
4207:
4204:
4203:
4201:
4200:
4195:
4190:
4185:
4180:
4175:
4169:
4167:
4163:
4162:
4160:
4159:
4154:
4149:
4144:
4139:
4134:
4129:
4123:
4121:
4117:
4116:
4114:
4113:
4108:
4103:
4098:
4096:Hash collision
4093:
4087:
4085:
4081:
4080:
4078:
4077:
4072:
4067:
4062:
4057:
4052:
4047:
4041:
4039:
4035:
4034:
4032:
4031:
4026:
4021:
4016:
4011:
4006:
4001:
3995:
3993:
3984:
3983:
3981:
3980:
3975:
3970:
3965:
3960:
3955:
3946:
3941:
3936:
3931:
3926:
3920:
3918:
3912:
3911:
3909:
3908:
3905:
3899:
3897:
3889:
3888:
3886:
3885:
3880:
3875:
3870:
3865:
3860:
3855:
3850:
3845:
3840:
3835:
3829:
3827:
3824:key stretching
3818:
3817:
3815:
3814:
3809:
3804:
3799:
3794:
3789:
3784:
3779:
3774:
3769:
3764:
3759:
3754:
3749:
3744:
3739:
3734:
3729:
3724:
3719:
3714:
3709:
3704:
3699:
3694:
3689:
3684:
3679:
3674:
3668:
3666:
3662:
3661:
3659:
3658:
3652:
3647:
3642:
3637:
3631:
3629:
3623:
3622:
3620:
3619:
3614:
3609:
3604:
3598:
3591:
3589:
3585:
3584:
3582:
3581:
3576:
3571:
3565:
3562:
3561:
3552:
3550:
3549:
3542:
3535:
3527:
3510:
3509:
3507:
3506:
3494:
3482:
3469:
3466:
3465:
3463:
3462:
3457:
3452:
3447:
3442:
3437:
3432:
3427:
3422:
3417:
3412:
3407:
3402:
3397:
3392:
3387:
3382:
3377:
3372:
3366:
3364:
3363:Related topics
3360:
3359:
3357:
3356:
3351:
3346:
3340:
3338:
3334:
3333:
3330:
3329:
3327:
3326:
3321:
3316:
3311:
3306:
3305:
3304:
3294:
3288:
3286:
3279:
3278:
3273:
3268:
3263:
3258:
3253:
3248:
3243:
3238:
3233:
3228:
3223:
3218:
3213:
3208:
3203:
3198:
3193:
3188:
3183:
3178:
3173:
3168:
3163:
3158:
3153:
3148:
3143:
3138:
3132:
3130:
3124:
3123:
3121:
3120:
3115:
3110:
3105:
3100:
3094:
3092:
3086:
3085:
3083:
3082:
3077:
3072:
3067:
3062:
3057:
3052:
3047:
3042:
3037:
3032:
3027:
3021:
3019:
3015:
3014:
3012:
3011:
3006:
3001:
2996:
2991:
2986:
2981:
2975:
2973:
2967:
2966:
2964:
2963:
2958:
2953:
2948:
2943:
2938:
2933:
2928:
2923:
2918:
2913:
2907:
2905:
2898:
2897:
2895:
2894:
2889:
2884:
2879:
2874:
2869:
2864:
2859:
2854:
2849:
2844:
2838:
2833:
2828:
2823:
2817:
2815:
2812:Proof of stake
2808:
2807:
2804:
2803:
2801:
2800:
2795:
2790:
2785:
2783:Nervos Network
2780:
2775:
2770:
2764:
2762:
2758:
2757:
2755:
2754:
2749:
2743:
2741:
2734:
2733:
2731:
2730:
2724:
2722:
2718:
2717:
2715:
2714:
2709:
2703:
2701:
2694:
2693:
2691:
2690:
2685:
2680:
2675:
2670:
2664:
2662:
2655:
2654:
2652:
2651:
2646:
2639:
2637:
2630:
2629:
2627:
2626:
2621:
2616:
2611:
2606:
2601:
2596:
2591:
2585:
2583:
2573:
2566:
2565:
2563:
2562:
2557:
2555:Proof of stake
2552:
2550:Proof of space
2547:
2541:
2539:
2532:
2531:
2529:
2528:
2523:
2521:Smart contract
2518:
2513:
2508:
2503:
2498:
2493:
2488:
2483:
2478:
2473:
2468:
2462:
2460:
2456:
2455:
2450:
2448:
2447:
2440:
2433:
2425:
2416:
2415:
2413:
2412:
2402:
2391:
2388:
2387:
2385:
2384:
2379:
2374:
2368:
2366:
2360:
2359:
2357:
2356:
2351:
2346:
2341:
2336:
2331:
2326:
2319:
2313:
2311:
2306:Legal entities
2303:
2302:
2300:
2299:
2291:
2282:
2280:
2276:
2275:
2273:
2272:
2267:
2262:
2257:
2252:
2246:
2244:
2240:
2239:
2236:
2235:
2233:
2232:
2227:
2221:
2219:
2215:
2214:
2212:
2211:
2205:
2203:
2196:
2190:
2189:
2187:
2186:
2181:
2176:
2171:
2166:
2161:
2156:
2151:
2146:
2144:Cryptocurrency
2141:
2136:
2130:
2128:
2124:
2123:
2121:
2120:
2115:
2110:
2105:
2099:
2097:
2093:
2092:
2090:
2089:
2084:
2079:
2074:
2069:
2064:
2059:
2054:
2049:
2044:
2039:
2034:
2029:
2024:
2019:
2014:
2009:
2004:
2002:Wences Casares
1999:
1994:
1989:
1984:
1982:Gavin Andresen
1978:
1976:
1972:
1971:
1969:
1968:
1963:
1958:
1953:
1947:
1944:
1943:
1938:
1936:
1935:
1928:
1921:
1913:
1907:
1906:
1900:
1888:
1876:
1875:External links
1873:
1871:
1870:
1840:
1810:
1751:
1701:
1682:
1655:
1636:
1617:
1586:
1560:
1531:
1494:
1464:
1424:
1409:
1401:
1371:Malkhi, Dahlia
1358:
1322:
1303:
1276:
1247:
1208:
1187:
1151:
1118:
1111:
1081:Dwork, Cynthia
1069:
1060:|journal=
1023:
1011:
985:
967:
949:
932:Bloomberg News
912:
883:
851:
807:
778:
749:
731:
701:Dwork, Cynthia
685:
653:
624:(2): 126–129.
603:
601:
598:
597:
596:
581:
578:
577:
576:
571:
566:
564:Proof of stake
561:
559:Proof of space
556:
551:
546:
541:
539:Cryptocurrency
536:
531:
524:
521:
501:proof of stake
479:
476:
455:
452:
442:
439:
413:
410:
392:
389:
367:
364:
363:
362:
357:
351:
348:
345:
342:
339:
336:Diffie-Hellman
333:
330:
329:Hash sequences
327:
320:
317:
310:
299:
296:
287:
286:
279:
273:
238:
237:
218:
217:
205:
202:
191:
174:
136:
133:
90:proof of stake
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
4670:
4659:
4656:
4654:
4651:
4649:
4646:
4645:
4643:
4633:
4623:
4621:
4616:
4611:
4609:
4599:
4595:
4578:
4570:
4569:
4566:
4560:
4559:Steganography
4557:
4555:
4552:
4550:
4547:
4545:
4542:
4540:
4537:
4535:
4532:
4530:
4527:
4525:
4522:
4520:
4517:
4515:
4514:Stream cipher
4512:
4510:
4507:
4505:
4502:
4501:
4499:
4495:
4489:
4486:
4484:
4481:
4479:
4476:
4474:
4473:Onion routing
4471:
4469:
4466:
4464:
4461:
4459:
4456:
4454:
4453:Shared secret
4451:
4449:
4446:
4444:
4441:
4439:
4436:
4434:
4431:
4429:
4426:
4424:
4421:
4419:
4416:
4414:
4411:
4409:
4406:
4404:
4401:
4399:
4396:
4393:
4390:
4385:
4382:
4381:
4380:
4377:
4375:
4372:
4370:
4367:
4365:
4362:
4360:
4357:
4355:
4352:
4350:
4349:Key generator
4347:
4345:
4342:
4340:
4337:
4335:
4332:
4330:
4327:
4323:
4320:
4318:
4315:
4314:
4313:
4312:Hash function
4310:
4308:
4305:
4303:
4300:
4298:
4295:
4293:
4290:
4288:
4287:Cryptanalysis
4285:
4283:
4280:
4276:
4273:
4272:
4271:
4268:
4266:
4263:
4261:
4258:
4257:
4255:
4251:
4247:
4240:
4235:
4233:
4228:
4226:
4221:
4220:
4217:
4213:
4199:
4196:
4194:
4191:
4189:
4188:Proof of work
4186:
4184:
4181:
4179:
4176:
4174:
4171:
4170:
4168:
4164:
4158:
4155:
4153:
4150:
4148:
4145:
4143:
4140:
4138:
4135:
4133:
4130:
4128:
4125:
4124:
4122:
4118:
4112:
4109:
4107:
4104:
4102:
4099:
4097:
4094:
4092:
4089:
4088:
4086:
4082:
4076:
4073:
4071:
4068:
4066:
4065:Rainbow table
4063:
4061:
4058:
4056:
4053:
4051:
4048:
4046:
4043:
4042:
4040:
4036:
4030:
4027:
4025:
4022:
4020:
4017:
4015:
4012:
4010:
4007:
4005:
4002:
4000:
3997:
3996:
3994:
3991:
3988:Authenticated
3985:
3979:
3976:
3974:
3971:
3969:
3966:
3964:
3961:
3959:
3956:
3954:
3950:
3947:
3945:
3942:
3940:
3937:
3935:
3932:
3930:
3927:
3925:
3922:
3921:
3919:
3917:
3916:MAC functions
3913:
3906:
3904:
3901:
3900:
3898:
3896:
3890:
3884:
3881:
3879:
3876:
3874:
3871:
3869:
3866:
3864:
3861:
3859:
3856:
3854:
3851:
3849:
3846:
3844:
3841:
3839:
3836:
3834:
3831:
3830:
3828:
3825:
3819:
3813:
3810:
3808:
3805:
3803:
3800:
3798:
3795:
3793:
3790:
3788:
3785:
3783:
3780:
3778:
3775:
3773:
3770:
3768:
3765:
3763:
3760:
3758:
3755:
3753:
3750:
3748:
3745:
3743:
3740:
3738:
3735:
3733:
3730:
3728:
3725:
3723:
3720:
3718:
3715:
3713:
3710:
3708:
3705:
3703:
3700:
3698:
3695:
3693:
3690:
3688:
3685:
3683:
3680:
3678:
3675:
3673:
3670:
3669:
3667:
3663:
3656:
3653:
3651:
3648:
3646:
3643:
3641:
3638:
3636:
3633:
3632:
3630:
3628:
3624:
3618:
3615:
3613:
3610:
3608:
3605:
3603:(compromised)
3602:
3599:
3597:(compromised)
3596:
3593:
3592:
3590:
3586:
3580:
3579:Known attacks
3577:
3575:
3572:
3570:
3567:
3566:
3563:
3559:
3555:
3548:
3543:
3541:
3536:
3534:
3529:
3528:
3525:
3521:
3517:
3505:
3504:
3495:
3493:
3492:
3483:
3481:
3480:
3471:
3470:
3467:
3461:
3458:
3456:
3453:
3451:
3448:
3446:
3443:
3441:
3438:
3436:
3433:
3431:
3428:
3426:
3423:
3421:
3418:
3416:
3413:
3411:
3408:
3406:
3403:
3401:
3398:
3396:
3393:
3391:
3388:
3386:
3383:
3381:
3378:
3376:
3373:
3371:
3368:
3367:
3365:
3361:
3355:
3352:
3350:
3347:
3345:
3342:
3341:
3339:
3335:
3325:
3322:
3320:
3317:
3315:
3312:
3310:
3309:LocalBitcoins
3307:
3303:
3300:
3299:
3298:
3295:
3293:
3290:
3289:
3287:
3283:
3277:
3274:
3272:
3269:
3267:
3264:
3262:
3259:
3257:
3254:
3252:
3249:
3247:
3244:
3242:
3241:ItBit (Paxos)
3239:
3237:
3234:
3232:
3229:
3227:
3224:
3222:
3219:
3217:
3214:
3212:
3209:
3207:
3204:
3202:
3199:
3197:
3194:
3192:
3189:
3187:
3184:
3182:
3179:
3177:
3174:
3172:
3169:
3167:
3164:
3162:
3159:
3157:
3154:
3152:
3149:
3147:
3144:
3142:
3139:
3137:
3134:
3133:
3131:
3129:
3125:
3119:
3116:
3114:
3111:
3109:
3106:
3104:
3101:
3099:
3096:
3095:
3093:
3091:
3087:
3081:
3078:
3076:
3073:
3071:
3068:
3066:
3063:
3061:
3058:
3056:
3053:
3051:
3048:
3046:
3043:
3041:
3038:
3036:
3033:
3031:
3028:
3026:
3023:
3022:
3020:
3016:
3010:
3007:
3005:
3002:
3000:
2997:
2995:
2992:
2990:
2987:
2985:
2982:
2980:
2977:
2976:
2974:
2972:
2968:
2962:
2959:
2957:
2954:
2952:
2949:
2947:
2944:
2942:
2939:
2937:
2934:
2932:
2929:
2927:
2924:
2922:
2919:
2917:
2914:
2912:
2909:
2908:
2906:
2903:
2899:
2893:
2890:
2888:
2885:
2883:
2880:
2878:
2875:
2873:
2870:
2868:
2865:
2863:
2860:
2858:
2855:
2853:
2850:
2848:
2845:
2842:
2839:
2837:
2834:
2832:
2829:
2827:
2824:
2822:
2819:
2818:
2816:
2813:
2809:
2799:
2796:
2794:
2791:
2789:
2786:
2784:
2781:
2779:
2776:
2774:
2771:
2769:
2766:
2765:
2763:
2759:
2753:
2750:
2748:
2745:
2744:
2742:
2739:
2735:
2729:
2726:
2725:
2723:
2721:RandomX-based
2719:
2713:
2710:
2708:
2705:
2704:
2702:
2699:
2695:
2689:
2686:
2684:
2681:
2679:
2676:
2674:
2671:
2669:
2666:
2665:
2663:
2660:
2656:
2650:
2647:
2644:
2641:
2640:
2638:
2635:
2631:
2625:
2622:
2620:
2617:
2615:
2612:
2610:
2607:
2605:
2602:
2600:
2597:
2595:
2592:
2590:
2587:
2586:
2584:
2581:
2577:
2574:
2571:
2570:Proof of work
2567:
2561:
2560:Proof of work
2558:
2556:
2553:
2551:
2548:
2546:
2543:
2542:
2540:
2537:
2533:
2527:
2524:
2522:
2519:
2517:
2514:
2512:
2509:
2507:
2504:
2502:
2499:
2497:
2494:
2492:
2489:
2487:
2484:
2482:
2479:
2477:
2474:
2472:
2469:
2467:
2464:
2463:
2461:
2457:
2453:
2446:
2441:
2439:
2434:
2432:
2427:
2426:
2423:
2411:
2403:
2401:
2393:
2392:
2389:
2383:
2380:
2378:
2377:Bitcoin Beach
2375:
2373:
2370:
2369:
2367:
2365:
2361:
2355:
2352:
2350:
2347:
2345:
2342:
2340:
2337:
2335:
2332:
2330:
2327:
2325:
2324:
2320:
2318:
2315:
2314:
2312:
2304:
2297:
2296:
2292:
2289:
2288:
2284:
2283:
2281:
2277:
2271:
2268:
2266:
2263:
2261:
2258:
2256:
2253:
2251:
2248:
2247:
2245:
2241:
2231:
2228:
2226:
2223:
2222:
2220:
2216:
2210:
2207:
2206:
2204:
2200:
2197:
2195:
2191:
2185:
2182:
2180:
2177:
2175:
2174:Proof of work
2172:
2170:
2167:
2165:
2162:
2160:
2157:
2155:
2152:
2150:
2147:
2145:
2142:
2140:
2137:
2135:
2132:
2131:
2129:
2125:
2119:
2116:
2114:
2111:
2109:
2106:
2104:
2101:
2100:
2098:
2094:
2088:
2087:Erik Voorhees
2085:
2083:
2080:
2078:
2075:
2073:
2070:
2068:
2065:
2063:
2060:
2058:
2055:
2053:
2050:
2048:
2047:Ross Ulbricht
2045:
2043:
2040:
2038:
2035:
2033:
2032:Charlie Shrem
2030:
2028:
2025:
2023:
2022:Mark Karpelès
2020:
2018:
2015:
2013:
2010:
2008:
2005:
2003:
2000:
1998:
1995:
1993:
1990:
1988:
1985:
1983:
1980:
1979:
1977:
1973:
1967:
1964:
1962:
1959:
1957:
1954:
1952:
1949:
1948:
1945:
1941:
1934:
1929:
1927:
1922:
1920:
1915:
1914:
1911:
1904:
1901:
1899:
1895:
1892:
1889:
1886:
1882:
1879:
1878:
1874:
1859:
1855:
1851:
1844:
1841:
1829:
1825:
1821:
1814:
1811:
1806:
1802:
1798:
1794:
1789:
1784:
1779:
1774:
1770:
1766:
1762:
1755:
1752:
1740:
1736:
1732:
1728:
1724:
1720:
1716:
1712:
1705:
1702:
1698:
1694:
1691:
1686:
1683:
1670:
1666:
1659:
1656:
1652:
1648:
1645:
1640:
1637:
1633:
1629:
1626:
1621:
1618:
1605:
1601:
1597:
1590:
1587:
1574:
1570:
1564:
1561:
1549:
1545:
1544:www.cbeci.org
1541:
1535:
1532:
1516:
1512:
1505:
1498:
1495:
1483:
1479:
1475:
1468:
1465:
1450:
1446:
1439:
1435:
1428:
1425:
1420:
1413:
1410:
1404:
1398:
1394:
1390:
1386:
1382:
1377:
1372:
1368:
1362:
1359:
1348:on 2016-03-03
1344:
1340:
1333:
1326:
1323:
1318:
1314:
1307:
1304:
1291:
1287:
1280:
1277:
1272:
1266:
1258:
1254:
1250:
1244:
1240:
1236:
1231:
1226:
1222:
1215:
1213:
1209:
1194:
1190:
1184:
1180:
1176:
1172:
1165:
1158:
1156:
1152:
1140:
1136:
1132:
1125:
1123:
1119:
1114:
1108:
1103:
1098:
1094:
1090:
1086:
1082:
1076:
1074:
1070:
1065:
1052:
1045:(2): 299–327.
1044:
1040:
1036:
1035:Abadi, Martín
1030:
1028:
1024:
1020:
1015:
1012:
1000:
996:
989:
986:
981:
974:
972:
968:
960:
953:
950:
937:
933:
929:
928:
923:
916:
913:
901:
897:
896:Bloomberg.com
893:
887:
884:
872:
868:
864:
858:
856:
852:
848:
833:
830:. July 2018.
829:
828:
820:
814:
812:
808:
796:
792:
788:
782:
779:
767:
763:
759:
753:
750:
738:
734:
728:
723:
718:
714:
710:
706:
702:
696:
694:
692:
690:
686:
680:
675:
671:
667:
660:
658:
654:
649:
645:
641:
637:
632:
627:
623:
619:
615:
608:
605:
599:
593:
587:
584:
583:
579:
575:
572:
570:
567:
565:
562:
560:
557:
555:
552:
550:
549:Proof of burn
547:
545:
542:
540:
537:
535:
532:
530:
527:
526:
522:
520:
517:
516:grandfathered
513:
509:
504:
502:
498:
493:
491:
485:
477:
475:
473:
467:
465:
461:
453:
451:
449:
440:
438:
436:
432:
427:
418:
411:
409:
407:
402:
398:
395:In 2009, the
390:
388:
386:
382:
377:
373:
365:
361:
358:
355:
352:
349:
346:
343:
340:
338:–based puzzle
337:
334:
331:
328:
325:
321:
318:
315:
311:
309:a large prime
308:
305:
304:
303:
297:
295:
292:
283:
282:Network-bound
280:
277:
274:
271:
267:
264:
263:
262:
259:
256:
254:
250:
242:
235:
230:
227:
226:
222:
214:
211:
210:
209:
203:
201:
199:
190:
184:
177:
173:
170:
166:
161:
159:
153:
150:
146:
142:
134:
132:
129:
125:
120:
118:
114:
110:
109:client puzzle
106:
101:
99:
95:
91:
86:
82:
77:
75:
71:
67:
63:
59:
58:Cynthia Dwork
55:
51:
47:
43:
40:
39:cryptographic
36:
32:
31:Proof of work
19:
18:Proof-of-work
4648:Cryptography
4509:Block cipher
4354:Key schedule
4344:Key exchange
4334:Kleptography
4297:Cryptosystem
4246:Cryptography
4187:
3501:
3489:
3477:
3354:Initiative Q
2707:Bitcoin Gold
2599:Counterparty
2594:Bitcoin Cash
2569:
2559:
2382:Bitcoin City
2321:
2293:
2285:
2230:Bitcoin Gold
2225:Bitcoin Cash
2173:
2127:Technologies
2077:Dave Kleiman
2072:Craig Wright
1961:Legal status
1897:
1862:. Retrieved
1853:
1843:
1832:. Retrieved
1823:
1813:
1788:10419/251105
1768:
1764:
1754:
1743:. Retrieved
1721:(3): 65–77.
1718:
1714:
1704:
1685:
1673:. Retrieved
1658:
1639:
1620:
1608:. Retrieved
1599:
1589:
1579:30 September
1577:. Retrieved
1563:
1552:. Retrieved
1543:
1534:
1522:. Retrieved
1510:
1497:
1486:. Retrieved
1477:
1467:
1456:. Retrieved
1444:
1427:
1418:
1412:
1380:
1361:
1350:. Retrieved
1343:the original
1338:
1325:
1316:
1306:
1294:. Retrieved
1284:Back, Adam.
1279:
1220:
1200:. Retrieved
1170:
1143:. Retrieved
1134:
1092:
1051:cite journal
1042:
1014:
1003:. Retrieved
988:
979:
952:
940:. Retrieved
925:
915:
904:. Retrieved
895:
886:
875:. Retrieved
866:
846:
839:. Retrieved
825:
799:. Retrieved
791:Investopedia
790:
781:
770:. Retrieved
761:
752:
741:. Retrieved
712:
669:
621:
617:
607:
586:
505:
494:
487:
468:
460:mining pools
457:
444:
426:Peer-to-peer
423:
394:
369:
350:Cuckoo Cycle
301:
290:
288:
281:
276:Memory-bound
275:
265:
260:
257:
246:
228:
212:
207:
194:
180:
162:
154:
140:
138:
121:
104:
102:
78:
49:
45:
34:
30:
29:
4632:Numismatics
4497:Mathematics
4488:Mix network
4178:Merkle tree
4166:Utilization
4152:NSA Suite B
3455:Token money
3344:Hyperledger
3216:EDX Markets
3080:WhopperCoin
2971:Stablecoins
2372:Bitcoin Law
2298:(2015 film)
2290:(2014 film)
2154:Bitcoin ATM
2057:Cody Wilson
1524:9 September
435:Switzerland
354:Merkle tree
314:Fiat–Shamir
187:X-Hashcash:
4642:Categories
4448:Ciphertext
4418:Decryption
4413:Encryption
4374:Ransomware
3990:encryption
3767:RadioGatún
3574:Comparison
3375:BitLicense
3319:QuadrigaCX
3302:bankruptcy
3266:ShapeShift
3211:Crypto.com
3098:BitConnect
3050:MobileCoin
2814:currencies
2673:Bitconnect
2668:Auroracoin
2572:currencies
2538:mechanisms
2466:Blockchain
2459:Technology
2139:Blockchain
2037:Nick Szabo
2012:Hal Finney
2007:Tim Draper
1864:2022-12-04
1834:2022-01-22
1745:2020-10-28
1675:28 October
1600:Money Beat
1554:2020-02-20
1488:2007-11-25
1458:2019-08-06
1352:2013-04-15
1296:2005-03-02
1286:"HashCash"
1202:2015-09-30
1145:2007-11-04
1089:Naor, Moni
1005:2015-12-29
942:13 January
906:2023-04-01
877:2023-04-01
841:29 October
801:2024-01-17
772:2024-01-17
743:2012-09-10
705:Naor, Moni
600:References
534:Bitmessage
482:See also:
472:51% attack
448:51% attack
406:block time
316:signatures
135:Background
124:algorithms
74:Hal Finney
4438:Plaintext
3907:KDF1/KDF2
3826:functions
3812:Whirlpool
3206:Coincheck
3108:KodakCoin
2951:Shiba Inu
2936:KodakCoin
2926:Chainlink
2852:Injective
2826:Avalanche
2788:Primecoin
2536:Consensus
2052:Roger Ver
1997:Adam Back
1956:Economics
1805:231942439
1797:0003-6846
1735:211422987
1699:on Github
1265:cite book
1225:CiteSeerX
648:222070383
640:1556-6056
266:CPU-bound
147:in 1997.
145:Adam Back
113:incentive
85:consensus
54:Moni Naor
50:verifiers
4620:Internet
4577:Category
4483:Kademlia
4443:Codetext
4386:(CSPRNG)
4132:CRYPTREC
3963:Poly1305
3883:yescrypt
3797:Streebog
3677:CubeHash
3657:(winner)
3479:Category
3201:Coinbase
3181:Bitstamp
3161:Bitpanda
3151:bitFlyer
3146:Bitfinex
3070:SafeMoon
3030:Filecoin
3009:USD Coin
2872:Polkadot
2867:Peercoin
2847:Gridcoin
2841:Ethereum
2821:Algorand
2798:Vertcoin
2768:AmbaCoin
2698:Equihash
2688:Litecoin
2683:Dogecoin
2643:Ethereum
2619:Peercoin
2614:Namecoin
2609:MazaCoin
2511:MetaMask
2400:Category
2349:GHash.io
2344:CoinDesk
2295:Deep Web
2218:Currency
2082:Jihan Wu
1894:Bit gold
1891:bit gold
1858:Archived
1828:Archived
1824:euronews
1739:Archived
1693:Archived
1669:Archived
1647:Archived
1628:Archived
1604:Archived
1573:Archived
1548:Archived
1515:Archived
1482:Archived
1449:Archived
1436:(2004).
1373:(1997).
1290:Archived
1257:14434713
1193:Archived
1139:Archived
999:Archived
936:Archived
900:Archived
871:Archived
832:Archived
795:Archived
766:Archived
737:Archived
707:(1993).
523:See also
508:New York
401:Hashcash
347:Hokkaido
341:Moderate
291:shortcut
234:Hashcash
204:Variants
158:spamming
149:Hashcash
141:Hashcash
4594:Portals
4253:General
4038:Attacks
3968:SipHash
3924:CBC-MAC
3858:LM hash
3838:Balloon
3702:HAS-160
3491:Commons
3370:Airdrop
3349:IQ.Wiki
3314:Mt. Gox
3285:Defunct
3271:Uniswap
3231:Genesis
3166:Bithumb
3141:Binance
3113:OneCoin
3075:Stellar
2956:The DAO
2946:Polygon
2916:Aventus
2831:Cardano
2624:Titcoin
2589:Bitcoin
2580:SHA-256
2410:Commons
2334:Bitmain
2243:History
2017:Wei Dai
1951:History
1940:Bitcoin
1883:at the
1610:30 June
1419:NDSS 99
1385:151–160
529:Bitcoin
397:Bitcoin
385:WalkSAT
370:At the
332:Puzzles
312:Weaken
285:tokens.
198:bitcoin
81:Bitcoin
4364:Keygen
4198:Pepper
4137:NESSIE
4084:Design
3878:scrypt
3873:PBKDF2
3848:Catena
3843:bcrypt
3833:Argon2
3792:Snefru
3787:Shabal
3782:SWIFFT
3762:RIPEMD
3757:N-hash
3732:MASH-2
3727:MASH-1
3712:Kupyna
3672:BLAKE3
3655:Keccak
3640:Grøstl
3617:BLAKE2
3324:Thodex
3251:Kucoin
3246:Kraken
3226:Gemini
3196:Circle
3171:BitMEX
3156:Bitkub
3103:Coinye
3065:Ripple
3040:Helium
3004:Tether
2904:tokens
2902:ERC-20
2877:Solana
2836:EOS.IO
2740:-based
2728:Monero
2700:-based
2678:Coinye
2661:-based
2659:Scrypt
2636:-based
2634:Ethash
2582:-based
2279:Movies
2202:Client
2179:SegWit
1975:People
1803:
1795:
1733:
1399:
1255:
1245:
1227:
1185:
1109:
729:
646:
638:
356:–based
344:Mbound
165:e-mail
46:prover
4394:(PRN)
3992:modes
3868:Makwa
3863:Lyra2
3853:crypt
3802:Tiger
3752:MDC-2
3707:HAVAL
3692:Fugue
3650:Skein
3635:BLAKE
3612:SHA-3
3607:SHA-2
3601:SHA-1
3292:BTC-e
3276:Upbit
3236:Huobi
3221:eToro
3176:Bitso
3118:Petro
2999:Terra
2941:Minds
2911:Augur
2887:Tezos
2882:Steem
2843:(2.0)
2793:Verge
2761:Other
2752:Petro
2712:Zcash
2645:(1.0)
2329:BitGo
2194:Forks
2184:SHA-2
2159:ECDSA
2096:Lists
1801:S2CID
1731:S2CID
1518:(PDF)
1507:(PDF)
1452:(PDF)
1441:(PDF)
1346:(PDF)
1335:(PDF)
1253:S2CID
1196:(PDF)
1167:(PDF)
962:(PDF)
835:(PDF)
822:(PDF)
644:S2CID
580:Notes
183:SHA-1
117:value
42:proof
4193:Salt
4157:CNSA
4024:IAPM
3978:VMAC
3973:UMAC
3958:PMAC
3953:CMAC
3949:OMAC
3944:NMAC
3939:HMAC
3934:GMAC
3903:HKDF
3772:SIMD
3722:Lane
3697:GOST
3682:ECOH
3569:List
3556:and
3503:List
3256:Kuna
3186:BTCC
3136:Abra
3055:Nano
3045:Luna
3025:Chia
2984:Diem
2961:TRON
2778:IOTA
2773:Firo
2747:Dash
2604:LBRY
2526:Web3
2501:Fork
2354:Nuri
1854:CNBC
1793:ISSN
1677:2020
1612:2014
1581:2020
1526:2022
1397:ISBN
1271:link
1243:ISBN
1183:ISBN
1107:ISBN
1064:help
944:2022
843:2020
727:ISBN
636:ISSN
372:IACR
128:work
105:work
66:spam
56:and
4029:OCB
4019:GCM
4014:EAX
4009:CWC
3999:CCM
3929:DAA
3807:VSH
3777:SM3
3747:MD6
3742:MD4
3737:MD2
3717:LSH
3687:FSB
3595:MD5
3297:FTX
3261:OKX
3191:BUX
3060:NEO
2994:Pax
2979:Dai
2931:Kin
2892:TON
2862:Nxt
2857:Kin
2738:X11
2169:P2P
1783:hdl
1773:doi
1723:doi
1389:doi
1235:doi
1175:doi
1097:doi
717:doi
674:doi
626:doi
35:PoW
4644::
3645:JH
1896:.
1856:.
1852:.
1826:.
1822:.
1799:.
1791:.
1781:.
1769:53
1767:.
1763:.
1737:.
1729:.
1719:22
1717:.
1713:.
1667:.
1598:.
1546:.
1542:.
1513:.
1509:.
1480:.
1476:.
1447:.
1443:.
1395:.
1387:.
1379:.
1369:;
1337:.
1315:.
1288:.
1267:}}
1263:{{
1251:.
1241:.
1233:.
1211:^
1191:.
1181:.
1169:.
1154:^
1137:.
1133:.
1121:^
1105:.
1087:;
1083:;
1072:^
1055::
1053:}}
1049:{{
1041:.
1026:^
997:.
970:^
934:.
930:.
924:.
898:.
894:.
869:.
865:.
854:^
845:.
824:.
810:^
793:.
789:.
764:.
760:.
735:.
725:.
711:.
703:;
688:^
668:.
656:^
642:.
634:.
622:19
620:.
616:.
450:.
437:.
4596::
4238:e
4231:t
4224:v
3951:/
3546:e
3539:t
3532:v
2444:e
2437:t
2430:v
1932:e
1925:t
1918:v
1867:.
1837:.
1807:.
1785::
1775::
1748:.
1725::
1679:.
1614:.
1583:.
1557:.
1528:.
1491:.
1461:.
1421:.
1405:.
1391::
1355:.
1319:.
1299:.
1273:)
1259:.
1237::
1205:.
1177::
1148:.
1115:.
1099::
1066:)
1062:(
1043:5
1008:.
982:.
964:.
946:.
909:.
880:.
804:.
775:.
746:.
719::
682:.
676::
650:.
628::
236:.
88:(
33:(
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.