1991:'s implementation modified Bernstein's published algorithm by changing the 64-bit nonce and 64-bit block counter to a 96-bit nonce and 32-bit block counter. The name was not changed when the algorithm was modified, as it is cryptographically insignificant (both form what a cryptographer would recognize as a 128-bit nonce), but the interface change could be a source of confusion for developers. Because of the reduced block counter, the maximum message length that can be safely encrypted by the IETF's variant is 2 blocks of 64 bytes (256
1025:
27:
4061:
1830:
cipher. Use the key and the first 128 bits of the nonce (in input words 12 through 15) to form a ChaCha input block, then perform the block operation (omitting the final addition). Output words 0–3 and 12–15 (those words corresponding to non-key words of the input) then form the key used for ordinary
954:
if Salsa20 is secure, but is more suitable for applications where longer nonces are desired. XSalsa20 feeds the key and the first 128 bits of the nonce into one block of Salsa20 (without the final addition, which may either be omitted, or subtracted after a standard Salsa20 block), and uses 256 bits
941:
Salsa20 performs 20 rounds of mixing on its input. However, reduced-round variants Salsa20/8 and Salsa20/12 using 8 and 12 rounds respectively have also been introduced. These variants were introduced to complement the original Salsa20, not to replace it, and perform better in the eSTREAM benchmarks
1224:
The ChaCha quarter round has the same number of adds, xors, and bit rotates as the Salsa20 quarter-round, but the fact that two of the rotates are multiples of 8 allows for a small optimization on some architectures including x86. Additionally, the input formatting has been rearranged to support an
967:
project, receiving the highest weighted voting score of any
Profile 1 algorithm at the end of Phase 2. Salsa20 had previously been selected as a Phase 2 Focus design for Profile 1 (software) and as a Phase 2 design for Profile 2 (hardware) by the eSTREAM project, but was not advanced to Phase 3 for
1220:
Notice that this version updates each word twice, while Salsa20's quarter round updates each word only once. In addition, the ChaCha quarter-round diffuses changes more quickly. On average, after changing 1 input bit the Salsa20 quarter-round will change 8 output bits while ChaCha will change 12.5
998:
In 2008, Aumasson, Fischer, Khazaei, Meier, and
Rechberger reported a cryptanalytic attack against Salsa20/7 with a time complexity of 2, and they reported an attack against Salsa20/8 with an estimated time complexity of 2. This attack makes use of the new concept of probabilistic neutral key bits
1132:
family of ciphers, which aim to increase the diffusion per round while achieving the same or slightly better performance. The
Aumasson et al. paper also attacks ChaCha, achieving one round fewer (for 256-bit ChaCha6 with complexity 2, ChaCha7 with complexity 2, and 128-bit ChaCha6 within 2) but
200:, and a 64-bit counter to a 512-bit block of the key stream (a Salsa version with a 128-bit key also exists). This gives Salsa20 and ChaCha the unusual advantage that the user can efficiently seek to any position in the key stream in constant time. Salsa20 offers speeds of around 4–14
1296:// Odd round QR(0, 4, 8, 12) // column 1 QR(1, 5, 9, 13) // column 2 QR(2, 6, 10, 14) // column 3 QR(3, 7, 11, 15) // column 4 // Even round QR(0, 5, 10, 15) // diagonal 1 (main diagonal) QR(1, 6, 11, 12) // diagonal 2 QR(2, 7, 8, 13) // diagonal 3 QR(3, 4, 9, 14) // diagonal 4
1229:
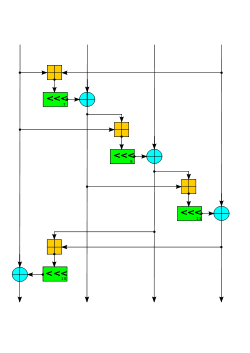
implementation optimization discovered for Salsa20. Rather than alternating rounds down columns and across rows, they are performed down columns and along diagonals. Like Salsa20, ChaCha arranges the sixteen 32-bit words in a 4×4 matrix. If we index the matrix elements from 0 to 15
406:// Odd round QR( 0, 4, 8, 12) // column 1 QR( 5, 9, 13, 1) // column 2 QR(10, 14, 2, 6) // column 3 QR(15, 3, 7, 11) // column 4 // Even round QR( 0, 1, 2, 3) // row 1 QR( 5, 6, 7, 4) // row 2 QR(10, 11, 8, 9) // row 3 QR(15, 12, 13, 14) // row 4
2139:
Since the majority of the work consists of performing the repeated rounds, the number of rounds is inversely proportional to the performance. That is, halving the number of rounds roughly doubles the performance. Reduced-round variants are thus appreciably
955:
of the output as the key for standard Salsa20 using the last 64 bits of the nonce and the stream position. Specifically, the 256 bits of output used are those corresponding to the non-secret portions of the input: indexes 0, 5, 10, 15, 6, 7, 8 and 9.
930:. In other words, applying the reverse operations would produce the original 4×4 matrix, including the key. Adding the mixed array to the original makes it impossible to recover the input. (This same technique is widely used in hash functions from
3169:
Pfau, Johannes; Reuter, Maximilian; Harbaum, Tanja; Hofmann, Klaus; Becker, Jurgen (September 2019). "A Hardware
Perspective on the ChaCha Ciphers: Scalable Chacha8/12/20 Implementations Ranging from 476 Slices to Bitrates of 175 Gbit/s".
994:
announced a cryptanalysis of Salsa20 which breaks 8 out of 20 rounds to recover the 256-bit secret key in 2 operations, using 2 keystream pairs. However, this attack does not seem to be competitive with the brute force attack.
982:
In 2005, Paul
Crowley reported an attack on Salsa20/5 with an estimated time complexity of 2 and won Bernstein's US$ 1000 prize for "most interesting Salsa20 cryptanalysis". This attack and all subsequent attacks are based on
173:
European Union cryptographic validation process by
Bernstein. ChaCha is a modification of Salsa20 published in 2008. It uses a new round function that increases diffusion and increases performance on some architectures.
4094:
987:. In 2006, Fischer, Meier, Berbain, Biasse, and Robshaw reported an attack on Salsa20/6 with estimated time complexity of 2, and a related-key attack on Salsa20/7 with estimated time complexity of 2.
403:
to each of the four columns in the 4×4 matrix, and even-numbered rounds apply it to each of the four rows. Two consecutive rounds (column-round and row-round) together are called a double-round:
1843:, yielding a 2.5× speedup. A compromise ChaCha12 (based on the eSTREAM recommendation of a 12-round Salsa) also sees some use. The eSTREAM benchmarking suite includes ChaCha8 and ChaCha12.
1136:
Like Salsa20, ChaCha's initial state includes a 128-bit constant, a 256-bit key, a 64-bit counter, and a 64-bit nonce (in the original version; as described later, a version of ChaCha from
4041:
3871:
926:
In the last line, the mixed array is added, word by word, to the original array to obtain its 64-byte key stream block. This is important because the mixing rounds on their own are
1818:, and its faster successors BLAKE2 and BLAKE3. It also defines a variant using sixteen 64-bit words (1024 bits of state), with correspondingly adjusted rotation constants.
1009:. (Specifically, it has no differential characteristic with higher probability than 2, so differential cryptanalysis would be more difficult than 128-bit key exhaustion.)
4104:
3724:
3342:
1002:
In 2012, the attack by
Aumasson et al. was improved by Shi et al. against Salsa20/7 (128-bit key) to a time complexity of 2 and Salsa20/8 (256-bit key) to 2.
971:
The eSTREAM committee recommends the use of Salsa20/12, the 12-round variant, for "combining very good performance with a comfortable margin of security."
3587:
3060:
3248:
Changes from regular ChaCha. The nonce: block sequence number split was changed from 64:64 to 96:32 The ChaCha20 state is initialized as follows:
1217:
a += b; d ^= a; d <<<= 16; c += d; b ^= c; b <<<= 12; a += b; d ^= a; d <<<= 8; c += d; b ^= c; b <<<= 7;
3006:
2462:
Progress in
Cryptology - INDOCRYPT 2006: 7th International Conference on Cryptology in India, Kolkata, India, December 11-13, 2006, Proceeding
3189:
2829:
2542:
2487:
984:
979:
As of 2015, there are no published attacks on Salsa20/12 or the full Salsa20/20; the best attack known breaks 8 of the 12 or 20 rounds.
385:
The constant words spell "expand 32-byte k" in ASCII (i.e. the 4 words are "expa", "nd 3", "2-by", and "te k"). This is an example of a
1937:
subroutine of the kernel. Starting from version 4.8, the Linux kernel uses the ChaCha20 algorithm to generate data for the nonblocking
3134:
3717:
3649:
3335:
1839:
Aumasson argues in 2020 that 8 rounds of ChaCha (ChaCha8) probably provides enough resistance to future cryptanalysis for the same
968:
Profile 2 because eSTREAM felt that it was probably not a good candidate for extremely resource-constrained hardware environments.
1144:
is slightly different), arranged as a 4×4 matrix of 32-bit words. But ChaCha re-arranges some of the words in the initial state:
2601:
2525:
Zhenqing Shi; Bin Zhang; Dengguo Feng; Wenling Wu (2012). "Improved Key
Recovery Attacks on Reduced-Round Salsa20 and ChaCha".
3920:
3644:
3634:
1815:
2854:
2619:
two of these constants are multiples of 8; this allows for a 1 instruction rotation in Core2 and later Intel CPUs using the
1867:
999:
for probabilistic detection of a truncated differential. The attack can be adapted to break Salsa20/7 with a 128-bit key.
2728:
3710:
3328:
1949:
396:
b ^= (a + d) <<< 7; c ^= (b + a) <<< 9; d ^= (c + b) <<< 13; a ^= (d + c) <<< 18;
148:
2008 cryptanalysis breaks 8 out of 20 rounds to recover the 256-bit secret key in 2 operations, using 2 keystream pairs.
4099:
4036:
3991:
3804:
386:
228:
2 ⊞, and constant-distance rotation operations <<< on an internal state of sixteen 32-bit words. Using only
3915:
3618:
3477:
1006:
4031:
1226:
1964:-based CPUs. Specialized hardware accelerators for ChaCha20 are also less complex compared to AES accelerators.
4021:
4011:
3866:
3613:
3091:
1871:
1863:
1826:
Although not announced by
Bernstein, the security proof of XSalsa20 extends straightforwardly to an analogous
4089:
4016:
4006:
3809:
3769:
3762:
3752:
3747:
1893:
Shortly after Google's adoption for TLS, both the ChaCha20 and Poly1305 algorithms were also used for a new
3757:
2465:
1956:
for x86 processors). As a result, ChaCha20 is sometimes preferred over AES in certain use cases involving
1024:
236:
in software implementations. The internal state is made of sixteen 32-bit words arranged as a 4×4 matrix.
4064:
3910:
3856:
3685:
3659:
3512:
2207:
Jean-Philippe Aumasson; Simon Fischer; Shahram Khazaei; Willi Meier; Christian Rechberger (2008-03-14).
2070:
1811:
178:
208:
processors, and reasonable hardware performance. It is not patented, and Bernstein has written several
4026:
3950:
3680:
2875:
1105:
118:
2693:"rand_chacha: consider ChaCha12 (or possibly ChaCha8) over ChaCha20 · Issue #932 · rust-random/rand"
2470:
1210:
The constant is the same as Salsa20 ("expand 32-byte k"). ChaCha replaces the Salsa20 quarter-round
3789:
3608:
3014:
2236:
1953:
1043:
197:
166:
45:
3234:
2943:
Legacy arc4random(3) API from OpenBSD reimplemented using the ChaCha20 PRF, with per-thread state.
1005:
In 2013, Mouha and Preneel published a proof that 15 rounds of Salsa20 was 128-bit secure against
950:
In 2008, Bernstein proposed a variant of Salsa20 with 192-bit nonces called XSalsa20. XSalsa20 is
3895:
3879:
3826:
3675:
225:
3955:
3945:
3816:
3185:
2804:
2538:
2483:
2119:
1875:
2779:
2503:
Yukiyasu Tsunoo; Teruo Saito; Hiroyasu Kubo; Tomoyasu Suzaki; Hiroki Nakashima (2007-01-02).
3890:
3457:
3307:
3177:
2530:
2475:
2097:
2086:
2078:
1996:
1980:
1961:
1137:
1299:
ChaCha20 uses 10 iterations of the double round. An implementation in C/C++ appears below.
3577:
3572:
3547:
3421:
3087:
2710:
1119:
951:
201:
132:
2651:
2504:
1952:(AES) algorithm on systems where the CPU does not feature AES acceleration (such as the
3965:
3885:
3846:
3794:
3779:
3639:
3492:
3447:
3140:
2113:
1840:
3181:
3171:
3061:"Merge tag 'random_for_linus' of git.kernel.org/pub/scm/linux/kernel/git/tytso/random"
2887:
Replace the RC4 algorithm for generating in-kernel secure random numbers with Chacha20
2560:"Towards Finding Optimal Differential Characteristics for ARX: Application to Salsa20"
4083:
4046:
4001:
3960:
3940:
3836:
3799:
3774:
3592:
3552:
3532:
3522:
3487:
3351:
3308:
Implementation and Didactical Visualization of the ChaCha Cipher Family in CrypTool 2
2652:"XChaCha: eXtended-nonce ChaCha and AEAD_XChaCha20_Poly1305 (Expired Internet-Draft)"
1957:
1930:
233:
209:
162:
141:
2900:
2607:
2406:
2164:
26:
3996:
3841:
3831:
3821:
3784:
3733:
2457:
2423:
2392:
2373:
1967:
ChaCha20-Poly1305 (IETF version; see below) is the exclusive algorithm used by the
229:
221:
186:
182:
3292:
2349:
169:. Salsa20, the original cipher, was designed in 2005, then later submitted to the
3155:
2955:
2928:
2692:
2534:
963:
Salsa20/12 has been selected as a Phase 3 design for Profile 1 (software) by the
3975:
3527:
3385:
3302:
2754:
2101:
2090:
2082:
2000:
1984:
1895:
1141:
2985:
2322:
2294:
1995:). For applications where this is not enough, such as file or disk encryption,
3935:
3905:
3900:
3861:
3654:
2240:
2104:. RFC 8439 merges in some errata and adds additional security considerations.
1902:. Subsequently, this made it possible for OpenSSH to avoid any dependency on
3925:
3567:
3497:
3431:
2636:
2442:
1968:
3970:
3930:
3380:
3095:
2833:
1992:
1855:
1079:
193:
92:
2670:
3400:
2559:
2529:. Lecture Notes in Computer Science. Vol. 7839. pp. 337–351.
2479:
2377:
2208:
1918:
1914:
1903:
1899:
964:
190:
170:
79:
3205:
2279:
2186:
1831:
ChaCha (with the last 64 bits of nonce and 64 bits of block counter).
3851:
3517:
3482:
3452:
3416:
1942:
1934:
1922:
1887:
1851:
1029:
The ChaCha quarter-round function. Four parallel copies make a round.
307:), two words of nonce (essentially additional stream position bits) (
3276:
2830:"OpenSSH Has a New Cipher — Chacha20-poly1305 — from D.J. Bernstein"
2464:. Lecture Notes in Computer Science. Vol. 4329. pp. 2–16.
31:
The Salsa quarter-round function. Four parallel copies make a round.
3286:
3036:
1948:
ChaCha20 usually offers better performance than the more prevalent
942:
than Salsa20, though with a correspondingly lower security margin.
3562:
3116:
2460:(2006). "Non-randomness in eSTREAM Candidates Salsa20 and TSC-4".
2074:
1304:#define ROTL(a,b) (((a) << (b)) | ((a) >> (32 - (b))))
935:
420:#define ROTL(a,b) (((a) << (b)) | ((a) >> (32 - (b))))
3582:
3557:
3507:
3502:
3370:
3365:
3271:
2456:
Simon Fischer; Willi Meier; Côme Berbain; Jean-François Biasse;
2443:"Truncated differential cryptanalysis of five rounds of Salsa20"
2265:
1988:
1883:
1879:
1859:
3706:
3324:
3297:
2586:
1979:
An implementation reference for ChaCha20 has been published in
185:(ARX) operations — 32-bit addition, bitwise addition (XOR) and
3542:
3537:
3390:
3280:
1926:
931:
393:
that takes a four-word input and produces a four-word output:
205:
3173:
2019 32nd IEEE International System-on-Chip Conference (SOCC)
3117:"Secure Randomness in Go 1.22 - The Go Programming Language"
3075:
random: replace non-blocking pool with a Chacha20-based CRNG
2729:"Do the ChaCha: better mobile performance with cryptography"
2828:
Murenin, Constantine A. (2013-12-11). Unknown Lamer (ed.).
2809:
Super User's BSD Cross Reference: PROTOCOL.chacha20poly1305
2122:– an AEAD scheme combining ChaCha20 with the Poly1305 MAC
2003:
proposes using the original algorithm with 64-bit nonce.
1874:
construction combining both algorithms, which is called
4095:
Cryptographically secure pseudorandom number generators
2853:
Murenin, Constantine A. (2014-04-30). Soulskill (ed.).
1133:
claims that the attack fails to break 128-bit ChaCha7.
3872:
Cryptographically secure pseudorandom number generator
2407:"eSTREAM: Short Report on the End of the Second Phase"
3135:"What's the appeal of using ChaCha20 instead of AES?"
389:. The core operation in Salsa20 is the quarter-round
3312:
2637:"ChaCha20 and Poly1305 for IETF Protocols: RFC 7539"
2085:. Standardization of its use in TLS is published in
1938:
299:
The initial state is made up of eight words of key (
212:
implementations optimized for common architectures.
3984:
3740:
3668:
3627:
3601:
3470:
3440:
3409:
3399:
3358:
1114:
1104:
1096:
1088:
1078:
1073:
1065:
1057:
1049:
1039:
1034:
139:
127:
117:
109:
101:
91:
86:
75:
67:
59:
51:
41:
36:
2603:Faster ChaCha implementations for Intel processors
2567:International Association for Cryptologic Research
2216:International Association for Cryptologic Research
2915:ChaCha based random number generator for OpenBSD.
1128:In 2008, Bernstein published the closely related
2527:Information Security and Cryptology – ICISC 2012
2323:"Extending the Salsa20 nonce (original version)"
1941:device. ChaCha8 is used for the default PRNG in
220:Internally, the cipher uses bitwise addition ⊕ (
3092:"/dev/random Seeing Improvements For Linux 4.8"
2960:Super User's BSD Cross Reference: subr_csprng.c
2927:riastradh (Taylor Campbell), ed. (2016-03-25).
2295:"Extending the Salsa20 nonce (updated in 2011)"
2266:"Snuffle 2005: the Salsa20 encryption function"
2116:– an add-rotate-xor cipher developed by the NSA
2933:Super User's BSD Cross Reference: arc4random.c
2905:Super User's BSD Cross Reference: arc4random.c
2899:guenther (Philip Guenther), ed. (2015-09-13).
2580:
2578:
2576:
3718:
3336:
3272:Snuffle 2005: the Salsa20 encryption function
2687:
2685:
2158:
2156:
1854:had selected ChaCha20 along with Bernstein's
8:
3156:"AES-NI SSL Performance Study @ Calomel.org"
2855:"OpenSSH No Longer Has To Depend On OpenSSL"
1878:. ChaCha20 and Poly1305 are now used in the
1017:
19:
3725:
3711:
3703:
3406:
3343:
3329:
3321:
3317:
3313:
3235:"ChaCha20 and Poly1305 for IETF protocols"
2753:Thomson, Martin; Turner, Sean (May 2021).
1862:, which was intended as a replacement for
409:An implementation in C/C++ appears below.
2505:"Differential Cryptanalysis of Salsa20/8"
2469:
1925:operating systems, instead of the broken
3229:
3227:
2424:"Salsa20/12, The eSTREAM portfolio page"
2231:
2229:
2227:
2225:
2005:
1232:
1146:
317:
238:
4105:Public-domain software with source code
2202:
2200:
2198:
2196:
2152:
2132:
1427:// 10 loops × 2 rounds/loop = 20 rounds
543:// 10 loops × 2 rounds/loop = 20 rounds
2650:Arciszewski, Scott (10 January 2020).
2165:"The Salsa20 family of stream ciphers"
1971:VPN system, as of protocol version 1.
1870:. In the process, they proposed a new
1307:#define QR(a, b, c, d) ( \
1016:
18:
2587:"The ChaCha family of stream ciphers"
2374:"The eSTREAM Project: End of Phase 2"
2007:Initial state of ChaCha20 (RFC 7539)
189:operations. The core function maps a
7:
985:truncated differential cryptanalysis
3375:
3298:The ChaCha family of stream ciphers
2096:In 2018, RFC 7539 was obsoleted by
2585:Daniel J. Bernstein (2008-04-25).
2558:Nicky Mouha; Bart Preneel (2013).
2264:Daniel J. Bernstein (2013-05-16).
2187:"Salsa 20 speed; Salsa20 software"
2185:Daniel J. Bernstein (2013-05-16).
2163:Daniel J. Bernstein (2007-12-24).
1316:a += b, d ^= a, d = ROTL(d, 8), \
1313:c += d, b ^= c, b = ROTL(b, 12), \
1310:a += b, d ^= a, d = ROTL(d, 16), \
1293:then a double round in ChaCha is:
14:
3182:10.1109/SOCC46988.2019.1570548289
2393:"eSTREAM PHASE 3: End of Phase 1"
303:), two words of stream position (
4060:
4059:
2778:Bishop, Mike (2 February 2021).
2669:Aumasson, Jean-Philippe (2020).
1319:c += d, b ^= c, b = ROTL(b, 7))
1023:
357:
352:
25:
2986:"ChaCha Usage & Deployment"
2805:"ssh/PROTOCOL.chacha20poly1305"
2635:Y. Nir; A. Langley (May 2015).
1945:. Rust's CSPRNG uses ChaCha12.
1858:message authentication code in
3921:Information-theoretic security
3303:Salsa20 Usage & Deployment
3115:Cox, Russ; Valsorda, Filippo.
2678:. Real World Crypto Symposium.
2209:"New Features of Latin Dances"
1909:ChaCha20 is also used for the
1816:NIST hash function competition
1:
2803:Miller, Damien (2016-05-03).
1906:, via a compile-time option.
1643:// diagonal 1 (main diagonal)
3635:block ciphers in stream mode
3293:The eSTREAM Project: Salsa20
3013:. 2014-11-16. Archived from
2600:Neves, Samuel (2009-10-07),
2535:10.1007/978-3-642-37682-5_24
2242:ChaCha, a variant of Salsa20
1950:Advanced Encryption Standard
959:eSTREAM selection of Salsa20
177:Both ciphers are built on a
4037:Message authentication code
3992:Cryptographic hash function
3805:Cryptographic hash function
3206:"Protocol and Cryptography"
2441:Paul Crowley (2006-02-09).
1913:random number generator in
1810:ChaCha is the basis of the
946:XSalsa20 with 192-bit nonce
387:nothing-up-my-sleeve number
4121:
3916:Harvest now, decrypt later
3619:alternating step generator
1007:differential cryptanalysis
423:#define QR(a, b, c, d)( \
399:Odd-numbered rounds apply
232:avoids the possibility of
4055:
4032:Post-quantum cryptography
3702:
3320:
3316:
2901:"libc/crypt/arc4random.c"
2391:Hongjun Wu (2007-03-30).
2280:"Salsa20: Software speed"
2077:has been standardized in
1882:protocol, which replaces
1022:
319:Initial state of Salsa20
311:), and four fixed words (
230:add-rotate-xor operations
147:
24:
4022:Quantum key distribution
4012:Authenticated encryption
3867:Random number generation
3614:self-shrinking generator
3287:Salsa20/8 and Salsa20/12
3065:Linux kernel source tree
3037:"Replacing /dev/urandom"
1872:authenticated encryption
1301:
1148:Initial state of ChaCha
975:Cryptanalysis of Salsa20
411:
157:and the closely related
4017:Public-key cryptography
4007:Symmetric-key algorithm
3810:Key derivation function
3770:Cryptographic primitive
3763:Authentication protocol
3753:Outline of cryptography
3748:History of cryptography
2929:"libc/gen/arc4random.c"
2780:"draft: IETF QUIC HTTP"
3758:Cryptographic protocol
2412:. eSTREAM. 2007-03-26.
1122:on an Intel Core 2 Duo
432:d ^= ROTL(c + b,13), \
429:c ^= ROTL(b + a, 9), \
426:b ^= ROTL(a + d, 7), \
204:in software on modern
135:on an Intel Core 2 Duo
3911:End-to-end encryption
3857:Cryptojacking malware
3686:stream cipher attacks
3277:Salsa20 specification
2321:Daniel J. Bernstein.
2293:Daniel J. Bernstein.
179:pseudorandom function
4027:Quantum cryptography
3951:Trusted timestamping
3681:correlation immunity
3212:. Jason A. Donenfeld
3176:. pp. 294–299.
2972:chacha_encrypt_bytes
2956:"kern/subr_csprng.c"
2784:datatracker.ietf.org
2759:datatracker.ietf.org
1835:Reduced-round ChaCha
1814:, a finalist in the
435:a ^= ROTL(d + c,18))
55:2007 (designed 2005)
3790:Cryptographic nonce
3609:shrinking generator
3359:Widely used ciphers
3259:Header of RFC 7539.
3011:NetBSD Manual Pages
2733:The Cloudflare Blog
2715:Cryptography Primer
2239:(28 January 2008),
2069:Use of ChaCha20 in
2008:
1960:, which mostly use
1954:AES instruction set
1812:BLAKE hash function
1149:
1044:Daniel J. Bernstein
1019:
320:
224:), 32-bit addition
167:Daniel J. Bernstein
46:Daniel J. Bernstein
21:
4100:Internet Standards
3896:Subliminal channel
3880:Pseudorandom noise
3827:Key (cryptography)
3676:correlation attack
3035:Corbet, Jonathan.
2480:10.1007/11941378_2
2006:
1975:Internet standards
1147:
318:
4077:
4076:
4073:
4072:
3956:Key-based routing
3946:Trapdoor function
3817:Digital signature
3698:
3697:
3694:
3693:
3466:
3465:
3191:978-1-7281-3483-3
3041:Linux Weekly News
2876:"Revision 317015"
2544:978-3-642-37681-8
2489:978-3-540-49767-7
2428:www.ecrypt.eu.org
2237:Bernstein, Daniel
2120:ChaCha20-Poly1305
2067:
2066:
1876:ChaCha20-Poly1305
1847:ChaCha20 adoption
1322:#define ROUNDS 20
1291:
1290:
1208:
1207:
1126:
1125:
438:#define ROUNDS 20
383:
382:
297:
296:
152:
151:
4112:
4063:
4062:
3891:Insecure channel
3727:
3720:
3713:
3704:
3407:
3345:
3338:
3331:
3322:
3318:
3314:
3260:
3257:
3251:
3250:
3245:
3244:
3239:
3231:
3222:
3221:
3219:
3217:
3202:
3196:
3195:
3166:
3160:
3159:
3152:
3146:
3145:
3131:
3125:
3124:
3112:
3106:
3105:
3103:
3102:
3084:
3078:
3077:
3072:
3071:
3057:
3051:
3050:
3048:
3047:
3032:
3026:
3025:
3023:
3022:
3003:
2997:
2996:
2994:
2993:
2982:
2976:
2975:
2973:
2968:
2967:
2952:
2946:
2945:
2940:
2939:
2924:
2918:
2917:
2912:
2911:
2896:
2890:
2889:
2884:
2883:
2872:
2866:
2865:
2863:
2862:
2850:
2844:
2843:
2841:
2840:
2825:
2819:
2818:
2816:
2815:
2800:
2794:
2793:
2791:
2790:
2775:
2769:
2768:
2766:
2765:
2750:
2744:
2743:
2741:
2740:
2725:
2719:
2718:
2707:
2701:
2700:
2689:
2680:
2679:
2677:
2666:
2660:
2659:
2656:Ietf Datatracker
2647:
2641:
2640:
2632:
2626:
2625:
2616:
2615:
2606:, archived from
2597:
2591:
2590:
2582:
2571:
2570:
2564:
2555:
2549:
2548:
2522:
2516:
2515:
2509:
2500:
2494:
2493:
2473:
2458:M. J. B. Robshaw
2453:
2447:
2446:
2438:
2432:
2431:
2420:
2414:
2413:
2411:
2403:
2397:
2396:
2388:
2382:
2381:
2370:
2364:
2363:
2361:
2360:
2346:
2340:
2339:
2337:
2336:
2327:
2318:
2312:
2311:
2309:
2308:
2299:
2290:
2284:
2283:
2276:
2270:
2269:
2261:
2255:
2254:
2253:
2252:
2247:
2233:
2220:
2219:
2213:
2204:
2191:
2190:
2182:
2176:
2175:
2169:
2160:
2141:
2137:
2009:
1912:
1897:
1806:
1803:
1800:
1797:
1794:
1791:
1788:
1785:
1782:
1779:
1776:
1773:
1770:
1767:
1764:
1761:
1758:
1755:
1752:
1749:
1746:
1743:
1740:
1737:
1734:
1731:
1728:
1725:
1722:
1719:
1716:
1713:
1710:
1707:
1704:
1701:
1698:
1695:
1692:
1689:
1686:
1683:
1680:
1677:
1674:
1671:
1668:
1665:
1662:
1659:
1656:
1653:
1650:
1647:
1644:
1641:
1638:
1635:
1632:
1629:
1626:
1623:
1620:
1617:
1614:
1611:
1608:
1605:
1602:
1599:
1596:
1593:
1590:
1587:
1584:
1581:
1578:
1575:
1572:
1569:
1566:
1563:
1560:
1557:
1554:
1551:
1548:
1545:
1542:
1539:
1536:
1533:
1530:
1527:
1524:
1521:
1518:
1515:
1512:
1509:
1506:
1503:
1500:
1497:
1494:
1491:
1488:
1485:
1482:
1479:
1476:
1473:
1470:
1467:
1464:
1461:
1458:
1455:
1452:
1449:
1446:
1443:
1440:
1437:
1434:
1431:
1428:
1425:
1422:
1419:
1416:
1413:
1410:
1407:
1404:
1401:
1398:
1395:
1392:
1389:
1386:
1383:
1380:
1377:
1374:
1371:
1368:
1365:
1362:
1359:
1356:
1353:
1350:
1347:
1344:
1341:
1338:
1335:
1332:
1329:
1326:
1323:
1320:
1317:
1314:
1311:
1308:
1305:
1233:
1213:
1150:
1027:
1020:
990:In 2007, Tsunoo
922:
919:
916:
913:
910:
907:
904:
901:
898:
895:
892:
889:
886:
883:
880:
877:
874:
871:
868:
865:
862:
859:
856:
853:
850:
847:
844:
841:
838:
835:
832:
829:
826:
823:
820:
817:
814:
811:
808:
805:
802:
799:
796:
793:
790:
787:
784:
781:
778:
775:
772:
769:
766:
763:
760:
757:
754:
751:
748:
745:
742:
739:
736:
733:
730:
727:
724:
721:
718:
715:
712:
709:
706:
703:
700:
697:
694:
691:
688:
685:
682:
679:
676:
673:
670:
667:
664:
661:
658:
655:
652:
649:
646:
643:
640:
637:
634:
631:
628:
625:
622:
619:
616:
613:
610:
607:
604:
601:
598:
595:
592:
589:
586:
583:
580:
577:
574:
571:
568:
565:
562:
559:
556:
553:
550:
547:
544:
541:
538:
535:
532:
529:
526:
523:
520:
517:
514:
511:
508:
505:
502:
499:
496:
493:
490:
487:
484:
481:
478:
475:
472:
469:
466:
463:
460:
457:
454:
451:
448:
445:
442:
439:
436:
433:
430:
427:
424:
421:
418:
417:<stdint.h>
415:
402:
392:
359:
354:
321:
314:
310:
306:
302:
239:
29:
22:
4120:
4119:
4115:
4114:
4113:
4111:
4110:
4109:
4080:
4079:
4078:
4069:
4051:
3980:
3736:
3731:
3690:
3664:
3623:
3597:
3462:
3436:
3395:
3354:
3349:
3268:
3263:
3258:
3254:
3242:
3240:
3237:
3233:
3232:
3225:
3215:
3213:
3204:
3203:
3199:
3192:
3168:
3167:
3163:
3154:
3153:
3149:
3133:
3132:
3128:
3114:
3113:
3109:
3100:
3098:
3088:Michael Larabel
3086:
3085:
3081:
3069:
3067:
3059:
3058:
3054:
3045:
3043:
3034:
3033:
3029:
3020:
3018:
3007:"arc4random(3)"
3005:
3004:
3000:
2991:
2989:
2984:
2983:
2979:
2971:
2965:
2963:
2954:
2953:
2949:
2937:
2935:
2926:
2925:
2921:
2909:
2907:
2898:
2897:
2893:
2881:
2879:
2874:
2873:
2869:
2860:
2858:
2852:
2851:
2847:
2838:
2836:
2827:
2826:
2822:
2813:
2811:
2802:
2801:
2797:
2788:
2786:
2777:
2776:
2772:
2763:
2761:
2752:
2751:
2747:
2738:
2736:
2727:
2726:
2722:
2709:
2708:
2704:
2691:
2690:
2683:
2675:
2672:Too Much Crypto
2668:
2667:
2663:
2649:
2648:
2644:
2634:
2633:
2629:
2613:
2611:
2599:
2598:
2594:
2584:
2583:
2574:
2562:
2557:
2556:
2552:
2545:
2524:
2523:
2519:
2507:
2502:
2501:
2497:
2490:
2471:10.1.1.121.7248
2455:
2454:
2450:
2440:
2439:
2435:
2422:
2421:
2417:
2409:
2405:
2404:
2400:
2390:
2389:
2385:
2372:
2371:
2367:
2358:
2356:
2348:
2347:
2343:
2334:
2332:
2325:
2320:
2319:
2315:
2306:
2304:
2297:
2292:
2291:
2287:
2278:
2277:
2273:
2263:
2262:
2258:
2250:
2248:
2245:
2235:
2234:
2223:
2211:
2206:
2205:
2194:
2184:
2183:
2179:
2167:
2162:
2161:
2154:
2150:
2145:
2144:
2138:
2134:
2129:
2110:
1977:
1910:
1894:
1886:and is used by
1849:
1837:
1824:
1808:
1807:
1804:
1801:
1798:
1795:
1792:
1789:
1786:
1783:
1780:
1777:
1774:
1771:
1768:
1765:
1762:
1759:
1756:
1753:
1750:
1747:
1744:
1741:
1738:
1735:
1732:
1729:
1726:
1723:
1720:
1717:
1714:
1711:
1708:
1705:
1702:
1699:
1696:
1693:
1690:
1687:
1684:
1681:
1678:
1675:
1672:
1669:
1666:
1663:
1660:
1657:
1654:
1651:
1648:
1645:
1642:
1639:
1636:
1633:
1630:
1627:
1624:
1621:
1618:
1615:
1612:
1609:
1606:
1603:
1600:
1597:
1594:
1591:
1588:
1585:
1582:
1579:
1576:
1573:
1570:
1567:
1564:
1561:
1558:
1555:
1552:
1549:
1546:
1543:
1540:
1537:
1534:
1531:
1528:
1525:
1522:
1519:
1516:
1513:
1510:
1507:
1504:
1501:
1498:
1495:
1492:
1489:
1486:
1483:
1480:
1477:
1474:
1471:
1468:
1465:
1462:
1459:
1456:
1453:
1450:
1447:
1444:
1441:
1438:
1435:
1432:
1429:
1426:
1423:
1420:
1417:
1414:
1411:
1408:
1405:
1402:
1399:
1396:
1393:
1390:
1387:
1384:
1381:
1378:
1375:
1372:
1369:
1366:
1363:
1360:
1357:
1354:
1351:
1348:
1345:
1342:
1339:
1336:
1333:
1330:
1327:
1324:
1321:
1318:
1315:
1312:
1309:
1306:
1303:
1297:
1218:
1211:
1084:128 or 256 bits
1066:Related to
1050:First published
1030:
1015:
977:
961:
952:provably secure
948:
924:
923:
920:
917:
914:
911:
908:
905:
902:
899:
896:
893:
890:
887:
884:
881:
878:
875:
872:
869:
866:
863:
860:
857:
854:
851:
848:
845:
842:
839:
836:
833:
830:
827:
824:
821:
818:
815:
812:
809:
806:
803:
800:
797:
794:
791:
788:
785:
782:
779:
776:
773:
770:
767:
764:
761:
758:
755:
752:
749:
746:
743:
740:
737:
734:
731:
728:
725:
722:
719:
716:
713:
710:
707:
704:
701:
698:
695:
692:
689:
686:
683:
680:
677:
674:
671:
668:
665:
662:
659:
656:
653:
650:
647:
644:
641:
638:
635:
632:
629:
626:
623:
620:
617:
614:
611:
608:
605:
602:
599:
596:
593:
590:
587:
584:
581:
578:
575:
572:
569:
566:
563:
560:
557:
554:
551:
548:
545:
542:
539:
536:
533:
530:
527:
524:
521:
518:
515:
512:
509:
506:
503:
500:
497:
494:
491:
488:
485:
482:
479:
476:
473:
470:
467:
464:
461:
458:
455:
452:
449:
446:
443:
440:
437:
434:
431:
428:
425:
422:
419:
416:
413:
407:
400:
397:
390:
312:
308:
304:
300:
218:
202:cycles per byte
97:128 or 256 bits
68:Related to
52:First published
32:
17:
12:
11:
5:
4118:
4116:
4108:
4107:
4102:
4097:
4092:
4090:Stream ciphers
4082:
4081:
4075:
4074:
4071:
4070:
4068:
4067:
4056:
4053:
4052:
4050:
4049:
4044:
4042:Random numbers
4039:
4034:
4029:
4024:
4019:
4014:
4009:
4004:
3999:
3994:
3988:
3986:
3982:
3981:
3979:
3978:
3973:
3968:
3966:Garlic routing
3963:
3958:
3953:
3948:
3943:
3938:
3933:
3928:
3923:
3918:
3913:
3908:
3903:
3898:
3893:
3888:
3886:Secure channel
3883:
3877:
3876:
3875:
3864:
3859:
3854:
3849:
3847:Key stretching
3844:
3839:
3834:
3829:
3824:
3819:
3814:
3813:
3812:
3807:
3797:
3795:Cryptovirology
3792:
3787:
3782:
3780:Cryptocurrency
3777:
3772:
3767:
3766:
3765:
3755:
3750:
3744:
3742:
3738:
3737:
3732:
3730:
3729:
3722:
3715:
3707:
3700:
3699:
3696:
3695:
3692:
3691:
3689:
3688:
3683:
3678:
3672:
3670:
3666:
3665:
3663:
3662:
3657:
3652:
3647:
3642:
3640:shift register
3637:
3631:
3629:
3625:
3624:
3622:
3621:
3616:
3611:
3605:
3603:
3599:
3598:
3596:
3595:
3590:
3585:
3580:
3575:
3570:
3565:
3560:
3555:
3550:
3545:
3540:
3535:
3530:
3525:
3520:
3515:
3510:
3505:
3500:
3495:
3490:
3485:
3480:
3474:
3472:
3468:
3467:
3464:
3463:
3461:
3460:
3455:
3450:
3444:
3442:
3438:
3437:
3435:
3434:
3429:
3424:
3419:
3413:
3411:
3404:
3397:
3396:
3394:
3393:
3388:
3383:
3378:
3373:
3368:
3362:
3360:
3356:
3355:
3352:Stream ciphers
3350:
3348:
3347:
3340:
3333:
3325:
3311:
3310:
3305:
3300:
3295:
3290:
3284:
3274:
3267:
3266:External links
3264:
3262:
3261:
3252:
3223:
3197:
3190:
3161:
3147:
3141:Stack Exchange
3126:
3107:
3090:(2016-07-25).
3079:
3052:
3027:
2998:
2977:
2947:
2919:
2891:
2867:
2845:
2820:
2795:
2770:
2745:
2720:
2702:
2681:
2661:
2642:
2627:
2592:
2572:
2550:
2543:
2517:
2495:
2488:
2448:
2433:
2415:
2398:
2383:
2365:
2341:
2313:
2285:
2271:
2256:
2221:
2192:
2177:
2151:
2149:
2146:
2143:
2142:
2131:
2130:
2128:
2125:
2124:
2123:
2117:
2109:
2106:
2065:
2064:
2061:
2058:
2055:
2051:
2050:
2047:
2044:
2041:
2037:
2036:
2033:
2030:
2027:
2023:
2022:
2019:
2016:
2013:
1976:
1973:
1958:mobile devices
1848:
1845:
1841:security level
1836:
1833:
1823:
1820:
1302:
1295:
1289:
1288:
1285:
1282:
1279:
1275:
1274:
1271:
1268:
1265:
1261:
1260:
1257:
1254:
1251:
1247:
1246:
1243:
1240:
1237:
1216:
1212:QR(a, b, c, d)
1206:
1205:
1202:
1199:
1196:
1192:
1191:
1188:
1185:
1182:
1178:
1177:
1174:
1171:
1168:
1164:
1163:
1160:
1157:
1154:
1124:
1123:
1116:
1112:
1111:
1108:
1102:
1101:
1098:
1094:
1093:
1090:
1086:
1085:
1082:
1076:
1075:
1071:
1070:
1067:
1063:
1062:
1059:
1055:
1054:
1051:
1047:
1046:
1041:
1037:
1036:
1032:
1031:
1028:
1014:
1013:ChaCha variant
1011:
976:
973:
960:
957:
947:
944:
412:
405:
401:QR(a, b, c, d)
395:
391:QR(a, b, c, d)
381:
380:
377:
374:
371:
367:
366:
363:
360:
355:
349:
348:
345:
342:
339:
335:
334:
331:
328:
325:
295:
294:
291:
288:
285:
281:
280:
277:
274:
271:
267:
266:
263:
260:
257:
253:
252:
249:
246:
243:
234:timing attacks
217:
214:
183:add–rotate–XOR
163:stream ciphers
150:
149:
145:
144:
137:
136:
129:
125:
124:
121:
115:
114:
111:
107:
106:
103:
99:
98:
95:
89:
88:
84:
83:
77:
73:
72:
69:
65:
64:
61:
57:
56:
53:
49:
48:
43:
39:
38:
34:
33:
30:
16:Stream ciphers
15:
13:
10:
9:
6:
4:
3:
2:
4117:
4106:
4103:
4101:
4098:
4096:
4093:
4091:
4088:
4087:
4085:
4066:
4058:
4057:
4054:
4048:
4047:Steganography
4045:
4043:
4040:
4038:
4035:
4033:
4030:
4028:
4025:
4023:
4020:
4018:
4015:
4013:
4010:
4008:
4005:
4003:
4002:Stream cipher
4000:
3998:
3995:
3993:
3990:
3989:
3987:
3983:
3977:
3974:
3972:
3969:
3967:
3964:
3962:
3961:Onion routing
3959:
3957:
3954:
3952:
3949:
3947:
3944:
3942:
3941:Shared secret
3939:
3937:
3934:
3932:
3929:
3927:
3924:
3922:
3919:
3917:
3914:
3912:
3909:
3907:
3904:
3902:
3899:
3897:
3894:
3892:
3889:
3887:
3884:
3881:
3878:
3873:
3870:
3869:
3868:
3865:
3863:
3860:
3858:
3855:
3853:
3850:
3848:
3845:
3843:
3840:
3838:
3837:Key generator
3835:
3833:
3830:
3828:
3825:
3823:
3820:
3818:
3815:
3811:
3808:
3806:
3803:
3802:
3801:
3800:Hash function
3798:
3796:
3793:
3791:
3788:
3786:
3783:
3781:
3778:
3776:
3775:Cryptanalysis
3773:
3771:
3768:
3764:
3761:
3760:
3759:
3756:
3754:
3751:
3749:
3746:
3745:
3743:
3739:
3735:
3728:
3723:
3721:
3716:
3714:
3709:
3708:
3705:
3701:
3687:
3684:
3682:
3679:
3677:
3674:
3673:
3671:
3667:
3661:
3658:
3656:
3653:
3651:
3648:
3646:
3643:
3641:
3638:
3636:
3633:
3632:
3630:
3626:
3620:
3617:
3615:
3612:
3610:
3607:
3606:
3604:
3600:
3594:
3591:
3589:
3586:
3584:
3581:
3579:
3576:
3574:
3571:
3569:
3566:
3564:
3561:
3559:
3556:
3554:
3551:
3549:
3546:
3544:
3541:
3539:
3536:
3534:
3531:
3529:
3526:
3524:
3521:
3519:
3516:
3514:
3511:
3509:
3506:
3504:
3501:
3499:
3496:
3494:
3491:
3489:
3486:
3484:
3481:
3479:
3476:
3475:
3473:
3471:Other ciphers
3469:
3459:
3456:
3454:
3451:
3449:
3446:
3445:
3443:
3439:
3433:
3430:
3428:
3425:
3423:
3420:
3418:
3415:
3414:
3412:
3408:
3405:
3402:
3398:
3392:
3389:
3387:
3384:
3382:
3379:
3377:
3374:
3372:
3369:
3367:
3364:
3363:
3361:
3357:
3353:
3346:
3341:
3339:
3334:
3332:
3327:
3326:
3323:
3319:
3315:
3309:
3306:
3304:
3301:
3299:
3296:
3294:
3291:
3288:
3285:
3282:
3278:
3275:
3273:
3270:
3269:
3265:
3256:
3253:
3249:
3236:
3230:
3228:
3224:
3211:
3207:
3201:
3198:
3193:
3187:
3183:
3179:
3175:
3174:
3165:
3162:
3157:
3151:
3148:
3144:. 2016-04-12.
3143:
3142:
3139:Cryptography
3136:
3130:
3127:
3122:
3118:
3111:
3108:
3097:
3093:
3089:
3083:
3080:
3076:
3066:
3062:
3056:
3053:
3042:
3038:
3031:
3028:
3017:on 2020-07-06
3016:
3012:
3008:
3002:
2999:
2987:
2981:
2978:
2974:
2961:
2957:
2951:
2948:
2944:
2934:
2930:
2923:
2920:
2916:
2906:
2902:
2895:
2892:
2888:
2877:
2871:
2868:
2856:
2849:
2846:
2835:
2831:
2824:
2821:
2810:
2806:
2799:
2796:
2785:
2781:
2774:
2771:
2760:
2756:
2749:
2746:
2734:
2730:
2724:
2721:
2716:
2712:
2706:
2703:
2698:
2694:
2688:
2686:
2682:
2674:
2673:
2665:
2662:
2657:
2653:
2646:
2643:
2638:
2631:
2628:
2624:
2622:
2610:on 2017-03-28
2609:
2605:
2604:
2596:
2593:
2588:
2581:
2579:
2577:
2573:
2568:
2561:
2554:
2551:
2546:
2540:
2536:
2532:
2528:
2521:
2518:
2513:
2506:
2499:
2496:
2491:
2485:
2481:
2477:
2472:
2467:
2463:
2459:
2452:
2449:
2444:
2437:
2434:
2429:
2425:
2419:
2416:
2408:
2402:
2399:
2394:
2387:
2384:
2380:. 2008-04-29.
2379:
2375:
2369:
2366:
2355:
2351:
2345:
2342:
2331:
2324:
2317:
2314:
2303:
2296:
2289:
2286:
2282:. 2007-05-11.
2281:
2275:
2272:
2267:
2260:
2257:
2244:
2243:
2238:
2232:
2230:
2228:
2226:
2222:
2217:
2210:
2203:
2201:
2199:
2197:
2193:
2188:
2181:
2178:
2173:
2166:
2159:
2157:
2153:
2147:
2136:
2133:
2126:
2121:
2118:
2115:
2112:
2111:
2107:
2105:
2103:
2099:
2094:
2092:
2088:
2084:
2080:
2076:
2072:
2062:
2059:
2056:
2053:
2052:
2048:
2045:
2042:
2039:
2038:
2034:
2031:
2028:
2025:
2024:
2020:
2017:
2014:
2011:
2010:
2004:
2002:
1998:
1994:
1990:
1986:
1982:
1974:
1972:
1970:
1965:
1963:
1959:
1955:
1951:
1946:
1944:
1940:
1936:
1932:
1931:DragonFly BSD
1928:
1924:
1920:
1916:
1907:
1905:
1901:
1896:
1891:
1889:
1885:
1881:
1877:
1873:
1869:
1865:
1861:
1857:
1853:
1846:
1844:
1842:
1834:
1832:
1829:
1821:
1819:
1817:
1813:
1742:// diagonal 4
1709:// diagonal 3
1676:// diagonal 2
1610:// Even round
1300:
1294:
1286:
1283:
1280:
1277:
1276:
1272:
1269:
1266:
1263:
1262:
1258:
1255:
1252:
1249:
1248:
1244:
1241:
1238:
1235:
1234:
1231:
1228:
1222:
1221:output bits.
1215:
1203:
1200:
1197:
1194:
1193:
1189:
1186:
1183:
1180:
1179:
1175:
1172:
1169:
1166:
1165:
1161:
1158:
1155:
1152:
1151:
1145:
1143:
1139:
1134:
1131:
1121:
1117:
1113:
1109:
1107:
1103:
1099:
1095:
1091:
1087:
1083:
1081:
1077:
1074:Cipher detail
1072:
1068:
1064:
1060:
1056:
1052:
1048:
1045:
1042:
1038:
1033:
1026:
1021:
1012:
1010:
1008:
1003:
1000:
996:
993:
988:
986:
980:
974:
972:
969:
966:
958:
956:
953:
945:
943:
939:
937:
933:
929:
726:// Even round
444:salsa20_block
410:
404:
394:
388:
378:
375:
372:
369:
368:
364:
361:
356:
351:
350:
346:
343:
340:
337:
336:
332:
329:
326:
323:
322:
316:
292:
289:
286:
283:
282:
278:
275:
272:
269:
268:
264:
261:
258:
255:
254:
250:
247:
244:
241:
240:
237:
235:
231:
227:
223:
215:
213:
211:
210:public domain
207:
203:
199:
195:
192:
188:
184:
180:
175:
172:
168:
165:developed by
164:
160:
156:
146:
143:
142:cryptanalysis
138:
134:
130:
126:
122:
120:
116:
112:
108:
104:
100:
96:
94:
90:
87:Cipher detail
85:
81:
78:
76:Certification
74:
70:
66:
62:
58:
54:
50:
47:
44:
40:
35:
28:
23:
3997:Block cipher
3842:Key schedule
3832:Key exchange
3822:Kleptography
3785:Cryptosystem
3734:Cryptography
3426:
3255:
3247:
3241:. Retrieved
3214:. Retrieved
3209:
3200:
3172:
3164:
3150:
3138:
3129:
3120:
3110:
3099:. Retrieved
3082:
3074:
3068:. Retrieved
3064:
3055:
3044:. Retrieved
3040:
3030:
3019:. Retrieved
3015:the original
3010:
3001:
2990:. Retrieved
2988:. 2016-09-07
2980:
2970:
2964:. Retrieved
2962:. 2015-11-04
2959:
2950:
2942:
2936:. Retrieved
2932:
2922:
2914:
2908:. Retrieved
2904:
2894:
2886:
2880:. Retrieved
2878:. 2017-04-16
2870:
2859:. Retrieved
2848:
2837:. Retrieved
2823:
2812:. Retrieved
2808:
2798:
2787:. Retrieved
2783:
2773:
2762:. Retrieved
2758:
2748:
2737:. Retrieved
2735:. 2015-02-23
2732:
2723:
2714:
2705:
2696:
2671:
2664:
2655:
2645:
2630:
2620:
2618:
2612:, retrieved
2608:the original
2602:
2595:
2566:
2553:
2526:
2520:
2511:
2498:
2461:
2451:
2436:
2427:
2418:
2401:
2386:
2368:
2357:. Retrieved
2353:
2350:"Salsa20/12"
2344:
2333:. Retrieved
2329:
2316:
2305:. Retrieved
2301:
2288:
2274:
2259:
2249:, retrieved
2241:
2215:
2180:
2171:
2135:
2095:
2068:
1978:
1966:
1947:
1939:/dev/urandom
1908:
1892:
1850:
1838:
1827:
1825:
1809:
1475:// Odd round
1328:chacha_block
1298:
1292:
1223:
1219:
1209:
1135:
1129:
1127:
1058:Derived from
1004:
1001:
997:
991:
989:
981:
978:
970:
962:
949:
940:
927:
925:
591:// Odd round
408:
398:
384:
298:
222:exclusive OR
219:
176:
158:
154:
153:
140:Best public
3985:Mathematics
3976:Mix network
2623:instruction
1607:// column 4
1574:// column 3
1541:// column 2
1508:// column 1
723:// column 4
690:// column 3
657:// column 2
624:// column 1
196:, a 64-bit
4084:Categories
3936:Ciphertext
3906:Decryption
3901:Encryption
3862:Ransomware
3655:T-function
3602:Generators
3478:Achterbahn
3243:2017-08-07
3101:2016-10-03
3070:2016-09-20
3046:2016-09-20
3021:2016-09-07
2992:2016-09-07
2966:2016-09-07
2938:2016-09-07
2910:2016-09-07
2882:2018-03-16
2861:2016-09-07
2857:. Slashdot
2839:2016-09-07
2814:2016-09-07
2789:2021-07-13
2764:2021-07-13
2755:"RFC 9001"
2739:2021-07-13
2614:2016-09-07
2395:. eSTREAM.
2359:2017-08-22
2335:2022-08-18
2307:2022-08-18
2251:2018-06-03
2148:References
1911:arc4random
1898:cipher in
1225:efficient
1089:State size
928:invertible
102:State size
60:Successors
3926:Plaintext
3568:SOBER-128
3498:KCipher-2
3432:SOSEMANUK
3403:Portfolio
3210:WireGuard
2466:CiteSeerX
2354:ECRYPT II
1969:WireGuard
1929:, and in
1097:Structure
1080:Key sizes
1040:Designers
216:Structure
181:based on
110:Structure
93:Key sizes
82:portfolio
42:Designers
4065:Category
3971:Kademlia
3931:Codetext
3874:(CSPRNG)
3441:Hardware
3410:Software
3381:Crypto-1
3096:Phoronix
2834:Slashdot
2711:"ChaCha"
2330:cr.yp.to
2302:cr.yp.to
2172:cr.yp.to
2108:See also
2054:Counter
1933:for the
1856:Poly1305
1367:uint32_t
1343:uint32_t
1334:uint32_t
1198:Counter
1195:Counter
1092:512 bits
934:through
858:// row 4
825:// row 3
792:// row 2
759:// row 1
483:uint32_t
459:uint32_t
450:uint32_t
414:#include
187:rotation
105:512 bits
3741:General
3669:Attacks
3458:Trivium
3427:Salsa20
3401:eSTREAM
2378:eSTREAM
2140:faster.
2021:"te k"
2018:"2-by"
2015:"nd 3"
2012:"expa"
1919:OpenBSD
1915:FreeBSD
1904:OpenSSL
1900:OpenSSH
1828:XChaCha
1822:XChaCha
1162:"te k"
1159:"2-by"
1156:"nd 3"
1153:"expa"
1069:Rumba20
1061:Salsa20
1035:General
965:eSTREAM
379:"te k"
362:"2-by"
341:"nd 3"
324:"expa"
191:256-bit
171:eSTREAM
155:Salsa20
80:eSTREAM
71:Rumba20
37:General
20:Salsa20
3852:Keygen
3628:Theory
3578:Turing
3573:Spritz
3548:Scream
3518:Phelix
3513:Panama
3483:F-FCSR
3453:MICKEY
3422:Rabbit
3417:HC-128
3376:ChaCha
3216:4 July
3188:
3121:go.dev
2697:GitHub
2621:pshufb
2541:
2512:ECRYPT
2486:
2468:
2100:
2089:
2081:
2063:Nonce
2060:Nonce
2057:Nonce
1999:
1987:. The
1983:
1943:Golang
1935:CSPRNG
1923:NetBSD
1921:, and
1888:HTTP/3
1852:Google
1454:ROUNDS
1214:with:
1204:Nonce
1201:Nonce
1140:
1130:ChaCha
1106:Rounds
1018:ChaCha
992:et al.
570:ROUNDS
347:Nonce
344:Nonce
313:
309:
305:
301:
159:ChaCha
119:Rounds
63:ChaCha
3882:(PRN)
3650:NLFSR
3563:SOBER
3493:ISAAC
3448:Grain
3289:(PDF)
3238:(PDF)
2676:(PDF)
2563:(PDF)
2508:(PDF)
2410:(PDF)
2326:(PDF)
2298:(PDF)
2246:(PDF)
2212:(PDF)
2168:(PDF)
2127:Notes
2114:Speck
2075:IPsec
1866:over
1346:const
1118:3.95
1115:Speed
936:SHA-2
462:const
198:nonce
131:3.91
128:Speed
3645:LFSR
3593:WAKE
3588:VMPC
3583:VEST
3558:SNOW
3553:SEAL
3543:RC4A
3538:RC4+
3533:QUAD
3523:Pike
3508:ORYX
3503:MUGI
3488:FISH
3371:A5/2
3366:A5/1
3218:2018
3186:ISBN
2539:ISBN
2484:ISBN
2102:8439
2091:7905
2083:7634
2073:and
2049:Key
2046:Key
2043:Key
2040:Key
2035:Key
2032:Key
2029:Key
2026:Key
2001:7539
1989:IETF
1985:7539
1884:SPDY
1880:QUIC
1860:SPDY
1769:<
1451:<
1397:<
1325:void
1190:Key
1187:Key
1184:Key
1181:Key
1176:Key
1173:Key
1170:Key
1167:Key
1142:7539
1053:2008
885:<
567:<
513:<
441:void
376:Key
373:Key
370:Key
365:Key
358:Pos.
353:Pos.
338:Key
333:Key
330:Key
327:Key
161:are
3391:RC4
3281:PDF
3178:doi
2531:doi
2476:doi
2098:RFC
2087:RFC
2079:RFC
2071:IKE
1997:RFC
1993:GiB
1981:RFC
1962:ARM
1927:RC4
1868:TCP
1864:TLS
1787:out
1748:for
1430:for
1376:for
1358:int
1337:out
1287:15
1273:11
1227:SSE
1138:RFC
1120:cpb
1100:ARX
938:.)
932:MD4
903:out
864:for
546:for
492:for
474:int
453:out
315:):
293:15
279:11
226:mod
206:x86
194:key
133:cpb
113:ARX
4086::
3660:IV
3528:Py
3386:E0
3246:.
3226:^
3208:.
3184:.
3137:.
3119:.
3094:.
3073:.
3063:.
3039:.
3009:.
2969:.
2958:.
2941:.
2931:.
2913:.
2903:.
2885:.
2832:.
2807:.
2782:.
2757:.
2731:.
2713:.
2695:.
2684:^
2654:.
2617:,
2575:^
2565:.
2537:.
2510:.
2482:.
2474:.
2426:.
2376:.
2352:.
2328:.
2300:.
2224:^
2214:.
2195:^
2170:.
2155:^
2093:.
1917:,
1890:.
1799:in
1778:++
1772:16
1739:);
1712:QR
1706:);
1679:QR
1673:);
1646:QR
1640:);
1613:QR
1604:);
1577:QR
1571:);
1544:QR
1538:);
1511:QR
1505:);
1478:QR
1463:+=
1421:in
1406:++
1400:16
1349:in
1284:14
1281:13
1278:12
1270:10
1259:7
1245:3
1110:20
915:in
894:++
888:16
855:);
828:QR
822:);
795:QR
789:);
762:QR
756:);
729:QR
720:);
693:QR
687:);
660:QR
654:);
627:QR
621:);
594:QR
579:+=
537:in
522:++
516:16
465:in
290:14
287:13
284:12
276:10
265:7
251:3
123:20
3726:e
3719:t
3712:v
3344:e
3337:t
3330:v
3283:)
3279:(
3220:.
3194:.
3180::
3158:.
3123:.
3104:.
3049:.
3024:.
2995:.
2864:.
2842:.
2817:.
2792:.
2767:.
2742:.
2717:.
2699:.
2658:.
2639:.
2589:.
2569:.
2547:.
2533::
2514:.
2492:.
2478::
2445:.
2430:.
2362:.
2338:.
2310:.
2268:.
2218:.
2189:.
2174:.
1805:}
1802:;
1796:+
1793:x
1790:=
1784:)
1781:i
1775:;
1766:i
1763:;
1760:0
1757:=
1754:i
1751:(
1745:}
1736:x
1733:,
1730:x
1727:,
1724:x
1721:,
1718:x
1715:(
1703:x
1700:,
1697:x
1694:,
1691:x
1688:,
1685:x
1682:(
1670:x
1667:,
1664:x
1661:,
1658:x
1655:,
1652:x
1649:(
1637:x
1634:,
1631:x
1628:,
1625:x
1622:,
1619:x
1616:(
1601:x
1598:,
1595:x
1592:,
1589:x
1586:,
1583:x
1580:(
1568:x
1565:,
1562:x
1559:,
1556:x
1553:,
1550:x
1547:(
1535:x
1532:,
1529:x
1526:,
1523:x
1520:,
1517:x
1514:(
1502:x
1499:,
1496:x
1493:,
1490:x
1487:,
1484:x
1481:(
1472:{
1469:)
1466:2
1460:i
1457:;
1448:i
1445:;
1442:0
1439:=
1436:i
1433:(
1424:;
1418:=
1415:x
1412:)
1409:i
1403:;
1394:i
1391:;
1388:0
1385:=
1382:i
1379:(
1373:;
1370:x
1364:;
1361:i
1355:{
1352:)
1340:,
1331:(
1267:9
1264:8
1256:6
1253:5
1250:4
1242:2
1239:1
1236:0
921:}
918:;
912:+
909:x
906:=
900:)
897:i
891:;
882:i
879:;
876:0
873:=
870:i
867:(
861:}
852:x
849:,
846:x
843:,
840:x
837:,
834:x
831:(
819:x
816:,
813:x
810:,
807:x
804:,
801:x
798:(
786:x
783:,
780:x
777:,
774:x
771:,
768:x
765:(
753:x
750:,
747:x
744:,
741:x
738:,
735:x
732:(
717:x
714:,
711:x
708:,
705:x
702:,
699:x
696:(
684:x
681:,
678:x
675:,
672:x
669:,
666:x
663:(
651:x
648:,
645:x
642:,
639:x
636:,
633:x
630:(
618:x
615:,
612:x
609:,
606:x
603:,
600:x
597:(
588:{
585:)
582:2
576:i
573:;
564:i
561:;
558:0
555:=
552:i
549:(
540:;
534:=
531:x
528:)
525:i
519:;
510:i
507:;
504:0
501:=
498:i
495:(
489:;
486:x
480:;
477:i
471:{
468:)
456:,
447:(
273:9
270:8
262:6
259:5
256:4
248:2
245:1
242:0
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.