941:'s MapViewOfFile, because inter-file pointers do not work when mapping files into semi-arbitrary places. In Multics, a file (or a segment from a multi-segment file) is mapped into a segment in the address space, so files are always mapped at a segment boundary. A file's linkage section can contain pointers for which an attempt to load the pointer into a register or make an indirect reference through it causes a trap. The unresolved pointer contains an indication of the name of the segment to which the pointer refers and an offset within the segment; the handler for the trap maps the segment into the address space, puts the segment number into the pointer, changes the tag field in the pointer so that it no longer causes a trap, and returns to the code where the trap occurred, re-executing the instruction that caused the trap. This eliminates the need for a
876:
thrashing happens. The process that has the token is given a privilege to allocate more physical memory pages to build its working set, which is expected to quickly finish its execution and to release the memory pages to other processes. A time stamp is used to handover the token one by one. The first version of swap-token was implemented in Linux 2.6. The second version is called preempt swap-token and is also in Linux 2.6. In this updated swap-token implementation, a priority counter is set for each process to track the number of swap-out pages. The token is always given to the process with a high priority, which has a high number of swap-out pages. The length of the time stamp is not a constant but is determined by the priority: the higher the number of swap-out pages of a process, the longer the time stamp for it will be.
380:) by which one can program as if there were only one storage." This is exactly the situation in computers with cache memory, one of the earliest commercial examples of which was the IBM System/360 Model 85. In the Model 85 all addresses were real addresses referring to the main core store. A semiconductor cache store, invisible to the user, held the contents of parts of the main store in use by the currently executing program. This is exactly analogous to Güntsch's system, designed as a means to improve performance, rather than to solve the problems involved in multi-programming.
384:
2277:
2758:
2748:
2738:
2728:
2718:
530:
617:. Each entry in the page table holds a flag indicating whether the corresponding page is in real memory or not. If it is in real memory, the page table entry will contain the real memory address at which the page is stored. When a reference is made to a page by the hardware, if the page table entry for the page indicates that it is not currently in real memory, the hardware raises a
44:
972:, provides for marking an address space as unswappable; doing so does not pin any pages in the address space. This can be done for the duration of a job by entering the name of an eligible main program in the Program Properties Table with an unswappable flag. In addition, privileged code can temporarily make an address space unswappable using a SYSEVENT
415:. The addition of virtual memory into the Atlas also eliminated a looming programming problem: planning and scheduling data transfers between main and secondary memory and recompiling programs for each change of size of main memory. The first Atlas was commissioned in 1962 but working prototypes of paging had been developed by 1959. In 1961, the
957:, in addition to whatever facilities they have for paging and segmentation. When this occurs, the OS writes those pages and segments currently in real memory to swap files. In a swap-in, the OS reads back the data from the swap files but does not automatically read back pages that had been paged out at the time of the swap out operation.
783:
of one second) whereas I/O buffers are usually short-term fixed (usually measured in significantly less than wall-clock time, possibly for tens of milliseconds). Indeed, the OS has a special facility for "fast fixing" these short-term fixed data buffers (fixing which is performed without resorting to a time-consuming
376:, since his high-speed memory was intended to contain a copy of some blocks of code or data taken from the drums. Indeed, he wrote (as quoted in translation): "The programmer need not respect the existence of the primary memory (he need not even know that it exists), for there is only one sort of addresses (
925:
solutions combined paging and segmentation because x86 paging offers only two protection domains whereas a VMM, guest OS or guest application stack needs three. The difference between paging and segmentation systems is not only about memory division; segmentation is visible to user processes, as part
279:
During the 1960s and early '70s, computer memory was very expensive. The introduction of virtual memory provided an ability for software systems with large memory demands to run on computers with less real memory. The savings from this provided a strong incentive to switch to virtual memory for all
871:
is the minimum set of pages that should be in memory in order for it to make useful progress. Thrashing occurs when there is insufficient memory available to store the working sets of all active programs. Adding real memory is the simplest response, but improving application design, scheduling, and
782:
and successor systems, the term is "fixed", and such pages may be long-term fixed, or may be short-term fixed, or may be unfixed (i.e., pageable). System control structures are often long-term fixed (measured in wall-clock time, i.e., time measured in seconds, rather than time measured in fractions
674:
Typically, a page fault that cannot be resolved results in an abnormal termination of the application. However, some systems allow the application to have exception handlers for such errors. The paging supervisor may handle a page fault exception in several different ways, depending on the details:
466:
showed that their virtual memory overlay system consistently worked better than the best manually controlled systems. Throughout the 1970s, the IBM 370 series running their virtual-storage based operating systems provided a means for business users to migrate multiple older systems into fewer, more
631:
Systems can have, e.g., one page table for the whole system, separate page tables for each address space or process, separate page tables for each segment; similarly, systems can have, e.g., no segment table, one segment table for the whole system, separate segment tables for each address space or
321:
that may produce unwanted and unpredictable delays in response to input, especially if the trap requires that data be read into main memory from secondary memory. The hardware to translate virtual addresses to physical addresses typically requires a significant chip area to implement, and not all
929:
This difference has important consequences; a segment is not a page with variable length or a simple way to lengthen the address space. Segmentation that can provide a single-level memory model in which there is no differentiation between process memory and file system consists of only a list of
875:
A system thrashing is often a result of a sudden spike in page demand from a small number of running programs. Swap-token is a lightweight and dynamic thrashing protection mechanism. The basic idea is to set a token in the system, which is randomly given to a process that has page faults when
457:
Before virtual memory could be implemented in mainstream operating systems, many problems had to be addressed. Dynamic address translation required expensive and difficult-to-build specialized hardware; initial implementations slowed down access to memory slightly. There were worries that new
671:(LRU) algorithm. Stolen page frames that have been modified are written back to auxiliary storage before they are added to the free queue. On some systems the paging supervisor is also responsible for managing translation registers that are not automatically loaded from page tables.
742:. If the pages containing these pointers or the code that they invoke were pageable, interrupt-handling would become far more complex and time-consuming, particularly in the case of page fault interruptions. Hence, some part of the page table structures is not pageable.
774:, transfers cannot be stopped if a page fault occurs and then restarted when the page fault has been processed. For example, the data could come from a measurement sensor unit and lost real time data that got lost because of a page fault can not be recovered.
920:
linear, paged address space. Segments can be moved in and out of that space; pages there can "page" in and out of main memory, providing two levels of virtual memory; few if any operating systems do so, instead using only paging. Early non-hardware-assisted
662:
This part of the operating system creates and manages page tables and lists of free page frames. In order to ensure that there will be enough free page frames to quickly resolve page faults, the system may periodically steal allocated page frames, using a
640:
use different parts of a single range of virtual addresses. If there are multiple page or segment tables, there are multiple virtual address spaces and concurrent applications with separate page tables redirect to different real addresses.
846:
mechanisms, for the paging supervisor and page tables in older systems, and for application programs using non-standard I/O management. For example, IBM's z/OS has 3 modes (virtual-virtual, virtual-real and virtual-fixed).
2296:, University of Michigan Engineering Summer Conference 1970 (revised May 1971), compares the scheduling and resource allocation approaches, including virtual memory and paging, used in four mainframe operating systems:
749:
The paging supervisor code and drivers for secondary storage devices on which pages reside must be permanently pinned, as otherwise paging would not even work because the necessary code would not be available.
458:
system-wide algorithms utilizing secondary storage would be less effective than previously used application-specific algorithms. By 1969, the debate over virtual memory for commercial computers was over; an
2787:
691:
For a fault due to a write attempt into a read-protected page, if it is a copy-on-write page then a free page frame will be assigned and the contents of the old page copied; otherwise it is treated as an
896:
supports a similar segmentation scheme as an option, but it is rarely used. Segmentation and paging can be used together by dividing each segment into pages; systems with this memory structure, such as
872:
memory usage can help. Another solution is to reduce the number of active tasks on the system. This reduces demand on real memory by swapping out the entire working set of one or more processes.
699:
In most cases, there will be an update to the page table, possibly followed by purging the
Translation Lookaside Buffer (TLB), and the system restarts the instruction that causes the exception.
842:
and similar OSes, some parts of systems memory are managed in "virtual-real" mode, called "V=R". In this mode every virtual address corresponds to the same real address. This mode is used for
75:
technique that provides an "idealized abstraction of the storage resources that are actually available on a given machine" which "creates the illusion to users of a very large (main) memory".
280:
systems. The additional capability of providing virtual address spaces added another level of security and reliability, thus making virtual memory even more attractive to the marketplace.
510:. However, loading segment descriptors was an expensive operation, causing operating system designers to rely strictly on paging rather than a combination of paging and segmentation.
368:
does not stand up to careful scrutiny. The computer proposed by Güntsch (but never built) had an address space of 10 words which mapped exactly onto the 10 words of the drums,
892:
instead of paging, dividing virtual address spaces into variable-length segments. A virtual address here consists of a segment number and an offset within the segment. The
131:
between processes, increased security due to memory isolation, and being able to conceptually use more memory than might be physically available, using the technique of
867:" can occur, in which the computer spends an unsuitably large amount of time transferring pages to and from a backing store, hence slowing down useful work. A task's
745:
Some pages may be pinned for short periods of time, others may be pinned for long periods of time, and still others may need to be permanently pinned. For example:
334:. Virtual memory was therefore introduced not only to extend primary memory, but to make such an extension as easy as possible for programmers to use. To allow for
120:(MMU), automatically translates virtual addresses to physical addresses. Software within the operating system may extend these capabilities, utilizing, e.g.,
2698:
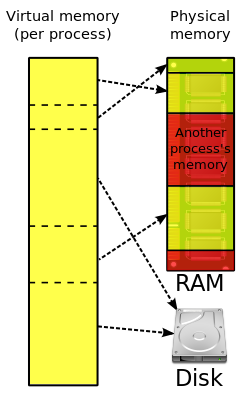
124:, to provide a virtual address space that can exceed the capacity of real memory and thus reference more memory than is physically present in the computer.
2359:
313:
and other special-purpose computer systems that require very fast and/or very consistent response times may opt not to use virtual memory due to decreased
979:
Swapping does not necessarily require memory management hardware, if, for example, multiple jobs are swapped in and out of the same area of storage.
1598:
372:
the addresses were real addresses and there was no form of indirect mapping, a key feature of virtual memory. What Güntsch did invent was a form of
2407:
1412:
1184:
127:
The primary benefits of virtual memory include freeing applications from having to manage a shared memory space, ability to share memory used by
801:
refer to pages temporarily made nonpageable (as for I/O buffers) as "locked", and simply "nonpageable" for those that are never pageable. The
2751:
2555:
2379:
2284:
2161:
1837:
1683:
1566:
1009:
682:
If the page is valid and the page information is not loaded into the MMU, the page information will be stored into one of the page registers.
304:
72:
197:
can employ hardware support to increase performance of their virtual memory implementations. Older operating systems, such as those for the
2741:
976:(SVC); certain changes in the address space properties require that the OS swap it out and then swap it back in, using SYSEVENT TRANSWAP.
1191:
695:
If the virtual address is a valid page in a memory-mapped file or a paging file, a free page frame will be assigned and the page read in.
2761:
1898:
Song Jiang; Xiaodong Zhang (2005). "Token-ordered LRU: an effective page replacement policy and its implementation in Linux systems".
1803:
1255:
2327:
2233:
2195:
1221:
1029:
569:
407:
mechanism to map the virtual addresses available to the programmer onto the real memory that consisted of 16,384 words of primary
1709:
926:
of memory model semantics. Hence, instead of memory that looks like a single large space, it is structured into multiple spaces.
770:
to which they are attached expect to find data buffers located at physical memory addresses; regardless of whether the bus has a
361:
2578:
2352:
547:
322:
chips used in embedded systems include that hardware, which is another reason some of those systems do not use virtual memory.
1625:
2703:
551:
30:
This article is about the computer memory management technique. For the technique of pooling multiple storage devices, see
1639:
268:
156:
2563:
2401:
864:
366:
Logical Design of a
Digital Computer with Multiple Asynchronous Rotating Drums and Automatic High Speed Memory Operation
52:
945:
completely and works when different processes map the same file into different places in their private address spaces.
2540:
973:
784:
636:
in a tree of region tables for each address space or process. If there is only one page table, different applications
291:. Each program thus appears to have sole access to the virtual memory. However, some older operating systems (such as
219:
2598:
116:
and the assignment of real memory to virtual memory. Address translation hardware in the CPU, often referred to as a
2328:
The
Virtual-Memory Manager in Windows NT, Randy Kath, Microsoft Developer Network Technology Group, 12 December 1992
1951:
383:
2721:
2608:
2588:
2441:
2345:
2053:
1350:
999:
703:
664:
35:
1982:
1654:
540:
342:, many early systems divided memory between multiple programs without virtual memory, such as early models of the
205:), generally have no virtual memory functionality, though notable exceptions for mainframes of the 1960s include:
2667:
802:
2527:
2305:
396:
241:
144:
1158:
594:
in size; systems with large virtual address ranges or amounts of real memory generally use larger page sizes.
1325:
2782:
2731:
2593:
2568:
2474:
1700:
1100:
1079:
314:
253:
186:
2545:
330:
In the 1950s, all larger programs had to contain logic for managing primary and secondary storage, such as
2497:
2395:
2249:, by Remzi H. Arpaci-Dusseau and Andrea C. Arpaci-Dusseau. Arpaci-Dusseau Books, 2014. Relevant chapters:
2087:
2009:
1113:
1075:
994:
614:
587:
357:
182:
117:
31:
1960:
965:
889:
885:
650:
583:
503:
451:
424:
416:
339:
331:
233:
178:
166:
152:
148:
113:
88:
2573:
702:
If the free page frame queue is empty then the paging supervisor must free a page frame using the same
1165:
590:, blocks of contiguous virtual memory addresses. Pages on contemporary systems are usually at least 4
759:
408:
155:
explicitly); and, when each process is run in its own dedicated address space, by obviating the need
48:
613:
to process instructions; such hardware that handles this specific translation is often known as the
2451:
2092:
2013:
1590:
1488:
668:
284:
128:
109:
2693:
2677:
2603:
2271:
2105:
1936:
1774:
1456:
1307:
942:
922:
347:
198:
1536:
766:
must reside in pinned pages while the I/O operation is in progress because such devices and the
2202:. z/OS MVS Programming: Authorized Assembler Services Reference SET-WTO SA23-1375-00. 1990–2014
2469:
2368:
2229:
2157:
1915:
1860:
1833:
1799:
1793:
1679:
1633:
1562:
1514:
Kilburn, T.; Edwards, D.B.G.; Lanigan, M.J.; Sumner, F.H. (1962), "One-level
Storage System",
1448:
1299:
1251:
1245:
1217:
1059:
1004:
798:
610:
1827:
1757:
Sayre, D. (1969). "Is automatic "folding" of programs efficient enough to displace manual?".
2646:
2641:
2484:
2256:
2097:
1907:
1766:
1713:
1607:
1519:
1497:
1440:
1385:
1291:
989:
688:
If there is a stolen page frame containing the desired page, that page frame will be reused.
637:
625:
621:
606:
335:
318:
223:
214:
210:
79:
2265:
17:
2636:
2535:
2331:
2268:
767:
310:
194:
160:
97:
2253:
498:
processor, but its segment swapping technique scaled poorly to larger segment sizes. The
2651:
2618:
2613:
2459:
1937:"Swap Token effectively minimizes system thrasing effects and is adopted in OS kernels"
1087:
1014:
491:
443:
400:
388:
272:
83:
2259:
2776:
2628:
2431:
2426:
2250:
1867:
1740:
z/VM built on IBM Virtualization
Technology General Information Version 4 Release 3.0
1554:
954:
902:
519:
288:
262:
229:
105:
2262:
2150:
1778:
1460:
1311:
1280:"Direct address translation for virtual memory in energy-efficient embedded systems"
2109:
1055:
507:
468:
373:
296:
121:
101:
2321:
1486:
Liptay, J.S. (1968), "Structural
Aspects of the System/360 Model 85 – The Cache",
446:
as
Virtual Machine Facility/370. IBM introduced the Start Interpretive Execution (
1673:
1279:
1211:
307:
that run all processes in a single address space composed of virtualized memory.
2672:
1051:
909:
893:
868:
763:
755:
529:
506:
layer, enabling the page fault exception to chain with other exceptions without
499:
495:
463:
412:
201:
of the 1960s, and those for personal computers of the early to mid-1980s (e.g.,
1911:
1389:
679:
If the virtual address is invalid, the paging supervisor treats it as an error.
181:; implementations usually require hardware support, typically in the form of a
2436:
779:
739:
618:
602:
431:
419:
independently released the first commercial computer with virtual memory, the
1919:
1523:
1452:
1303:
2583:
2464:
2075:
1295:
905:, are usually paging-predominant, segmentation providing memory protection.
843:
827:
823:
731:
475:; during the 1970s, other minicomputers implemented virtual memory, notably
435:
354:
190:
60:
43:
685:
If the page is uninitialized, a new page frame may be assigned and cleared.
147:
of physical memory; by delegating to the kernel the burden of managing the
2123:
2101:
1770:
1738:
1717:
1444:
752:
Timing-dependent components may be pinned to avoid variable paging delays.
2517:
2512:
2502:
2492:
605:
are used to translate the virtual addresses seen by the application into
591:
353:
A claim that the concept of virtual memory was first developed by German
2246:
1611:
1354:
283:
Most modern operating systems that support virtual memory also run each
2507:
2309:
2301:
2038:
2016:
1658:
1501:
898:
794:
790:
645:
554: in this section. Unsourced material may be challenged and removed.
480:
258:
245:
2176:
The most important requirement is that the program be APF authorized.
1167:
System/360 Model 67 Time
Sharing System Preliminary Technical Summary
1121:
1117:
917:
860:
856:
839:
472:
404:
343:
292:
249:
169:
can be considered a generalization of the concept of virtual memory.
132:
2337:
2074:
Bensoussan, André; Clingen, CharlesT.; Daley, Robert C. (May 1972).
930:
segments (files) mapped into the process's potential address space.
467:
powerful, mainframes that had improved price/performance. The first
734:
mechanisms rely on an array of pointers to their handlers, such as
450:) instruction as part of 370-XA on the 3081, and VM/XA versions of
2297:
1134:
938:
913:
771:
439:
420:
382:
300:
236:
2056:
Virtual
Machines: Architectures, Implementations and Applications
1032:, a series of specifications intended to unify CPU and GPU memory
933:
This is not the same as the mechanisms provided by calls such as
644:
Some earlier systems with smaller real memory sizes, such as the
395:
The first true virtual memory system was that implemented at the
1795:
IBM Power
Systems Performance Guide: Implementing and Optimizing
1083:
1024:
969:
934:
2341:
1431:
Jessen, E. (1996). "Die Entwicklung des virtuellen Speichers".
1953:
Burroughs B5500 Information Processing System Reference Manual
1876:
1018:
961:
735:
582:
Nearly all current implementations of virtual memory divide a
523:
487:
476:
459:
202:
143:
Virtual memory makes application programming easier by hiding
1410:
Jessen, Elke (2004). "Origin of the Virtual Memory Concept".
1213:
Architectural and Operating System Support for Virtual Memory
1193:
z/OS Version 2 Release 4 z/OS Introduction and Release Guide
2039:"System Design of a Computer for Time Sharing Applications"
718:(never swapped to secondary storage). Other terms used are
1137:
there is a 3-level tree of regions for each address space.
758:
that are accessed directly by peripheral devices that use
654:
instead of page tables in memory for address translation.
2788:
Department of Computer Science, University of Manchester
2037:
Glaser, Edward L.; Couleur, John F. & Oliver, G. A.
226:(software based virtual memory without hardware support)
104:, as seen by a process or task, appears as a contiguous
2315:
2380:
Memory management as a function of an operating system
805:
also uses the term "locked" in the specification for
391:
was the first computer to feature true virtual memory.
1074:
on mainframe operating systems. This usage runs from
82:, using a combination of hardware and software, maps
1397:
In the Beginning: Recollections of Software Pioneers
1244:
Haldar, Sibsankar; Aravind, Alex Alagarsamy (2010).
1099:
IBM had previously used the term hypervisor for the
399:
to create a one-level storage system as part of the
2686:
2660:
2627:
2554:
2526:
2483:
2450:
2417:
2388:
2152:
The Multics System: An Examination of Its Structure
953:Some operating systems provide for swapping entire
815:
806:
2149:
1931:
1929:
1278:Zhou, Xiangrong; Petrov, Peter (1 December 2008).
1199:. IBM. 22 September 2020. p. 3. GA32-0887-40.
624:, invoking the paging supervisor component of the
502:introduced paging support underneath the existing
2076:"The Multics Virtual Memory: Concepts and Design"
2017:"Introduction and Overview of the Multics System"
1537:"Ferranti Atlas 1 & 2 – Systems Architecture"
1702:System/370 integrated emulation under OS and DOS
1210:Bhattacharjee, Abhishek; Lustig, Daniel (2017).
151:(eliminating the need for the program to handle
2196:"Control swapping (DONTSWAP, OKSWAP, TRANSWAP)"
1628:. Archived from the original on 6 October 2014.
1216:. Morgan & Claypool Publishers. p. 1.
317:; virtual memory systems trigger unpredictable
177:Virtual memory is an integral part of a modern
2226:Computer Architecture, A Quantitative Approach
1678:. Jones and Bartlett Publishers. p. 113.
1591:"The origin of the VM/370 time-sharing system"
1353:. Microsoft. 23 September 2011. Archived from
1284:ACM Transactions on Embedded Computing Systems
471:to introduce virtual memory was the Norwegian
55:to form a large range of contiguous addresses.
2353:
714:Operating systems have memory areas that are
411:with an additional 98,304 words of secondary
8:
2699:International Symposium on Memory Management
2224:Hennessy, John L.; and Patterson, David A.;
1879:. May 2022. pp. 3-46–3-53. SA22-7832-13
1561:. John Wiley and Sons. pp. 1832–1835.
2360:
2346:
2338:
2052:Smith, J. E.; Uhlig, R. (14 August 2005).
1792:Quintero, Dino; et al. (1 May 2013).
1712:. Vol. 38. AFIPS Press. p. 164.
1380:
1378:
1376:
1374:
1372:
632:process, separate segment tables for each
2091:
1599:IBM Journal of Research & Development
1103:, but that did not involve virtual memory
570:Learn how and when to remove this message
2185:e.g., requesting use of preferred memory
1869:z/Architecture - Principles of Operation
1250:. Pearson Education India. p. 269.
42:
1675:Memory Systems and Pipelined Processors
1413:IEEE Annals of the History of Computing
1159:"SYSTEM COMPONENTS: Dynamic Relocation"
1150:
1043:
2294:Advanced Topics in Systems Programming
1631:
1473:
305:single address space operating systems
159:program code or to access memory with
1010:Memory management (operating systems)
916:processors, the segments reside in a
486:Virtual memory was introduced to the
7:
2247:Operating Systems: Three Easy Pieces
1553:Denning, Peter J. (1 January 2003).
1173:. IBM. 1966. p. 21. C20-1647-0.
1021:mode that allows for virtual memory.
552:adding citations to reliable sources
27:Computer memory management technique
2408:Input–output memory management unit
2278:"Time-Sharing Supervisor Programs"
2058:, HOTCHIPS 17, Tutorial 1, part 2"
442:, and in 1972 provided it for the
25:
1832:. Excel Books India. p. 62.
1030:Heterogeneous System Architecture
2757:
2756:
2747:
2746:
2737:
2736:
2727:
2726:
2717:
2716:
2316:LinuxMM: Linux Memory Management
1798:. IBM Corporation. p. 138.
1710:Spring Joint Computer Conference
1589:Creasy, R. J. (September 1981).
1559:Encyclopedia of Computer Science
528:
364:in 1956 in his doctoral thesis,
299:) and even modern ones (such as
2579:Concurrent mark sweep collector
2124:"Multics Execution Environment"
1829:Foundation of Operating Systems
1124:only supported 2 KB pages.
778:In IBM's operating systems for
539:needs additional citations for
112:. The operating system manages
47:Virtual memory combines active
2704:Region-based memory management
1990:. January 1968. pp. 21–30
1746:. 12 April 2002. GC24-5991-04.
772:memory management unit for I/O
1:
2148:Organick, Elliott I. (1972).
430:IBM developed the concept of
387:The University of Manchester
362:Technische Universität Berlin
269:Time Sharing Operating System
34:. For the TBN game show, see
2752:Memory management algorithms
2564:Automatic Reference Counting
2402:Translation lookaside buffer
2334: (archived 22 June 2010)
1185:"BCP (Base Control Program)"
863:are used, a problem called "
108:or collection of contiguous
2742:Automatic memory management
2541:C dynamic memory allocation
2292:by Michael T. Alexander in
1699:Gary R. Allred (May 1971).
1390:"Before Memory Was Virtual"
1054:; contemporary systems use
974:Supervisor Call instruction
785:Supervisor Call instruction
220:THE multiprogramming system
18:Virtual address translation
2804:
2762:Memory management software
2609:Tracing garbage collection
2442:Virtual memory compression
2324:, mailing list discussion.
1912:10.1016/j.peva.2004.10.002
1672:Cragon, Harvey G. (1996).
1000:Cache replacement policies
884:Some systems, such as the
704:page replacement algorithm
665:page replacement algorithm
517:
86:used by a program, called
36:Virtual Memory (game show)
29:
2712:
2375:
2080:Communications of the ACM
1759:Communications of the ACM
1638:: CS1 maint: unfit URL (
1351:"Windows Version History"
803:Single UNIX Specification
2536:Static memory allocation
2528:Manual memory management
1524:10.1109/TEC.1962.5219356
880:Segmented virtual memory
638:running at the same time
397:University of Manchester
2594:Garbage-first collector
2569:Boehm garbage collector
2475:x86 memory segmentation
1875:(Fourteenth ed.).
1296:10.1145/1457246.1457251
793:used the term "wired".
254:IBM System/360 Model 67
189:. While not necessary,
51:and inactive memory on
2599:Mark–compact algorithm
2396:Memory management unit
2260:Introduction to Paging
1900:Performance Evaluation
1326:"AMD-V™ Nested Paging"
995:Page (computer memory)
949:Address space swapping
834:Virtual-real operation
615:memory management unit
490:architecture with the
392:
183:memory management unit
118:memory management unit
114:virtual address spaces
56:
32:Storage virtualization
2322:Birth of Linux Kernel
2102:10.1145/355602.361306
1961:Burroughs Corporation
1771:10.1145/363626.363629
1718:10.1109/AFIPS.1971.58
1445:10.1007/s002870050034
730:pages. For example,
584:virtual address space
462:research team led by
417:Burroughs Corporation
386:
287:in its own dedicated
179:computer architecture
167:Memory virtualization
46:
2546:new and delete (C++)
2269:Swapping: Mechanisms
2266:Advanced Page Tables
2200:IBM Knowledge Center
1984:GE-645 System Manual
1861:"Translation Tables"
760:direct memory access
548:improve this article
514:Paged virtual memory
427:rather than paging.
358:Fritz-Rudolf Güntsch
2452:Memory segmentation
2290:on 1 November 2012.
2254:Address Translation
1826:Sharma, Dp (2009).
1612:10.1147/rd.255.0483
1542:. 12 November 2009.
1489:IBM Systems Journal
1433:Informatik-Spektrum
1050:Early systems used
706:for page stealing.
669:Least recently used
161:relative addressing
2694:Automatic variable
2678:Unreachable memory
2604:Reference counting
2574:Cheney's algorithm
2556:Garbage collection
2272:Swapping: Policies
1950:Burroughs (1964).
1502:10.1147/sj.71.0015
1070:IBM uses the term
1060:solid state memory
1025:CUDA Pinned memory
923:x86 virtualization
607:physical addresses
393:
94:physical addresses
57:
2770:
2769:
2722:Memory management
2470:Virtual 8086 mode
2369:Memory management
2163:978-0-262-15012-5
1839:978-81-7446-626-6
1685:978-0-86720-474-2
1568:978-0-470-86412-8
1357:on 8 January 2015
1247:Operating Systems
1005:Memory management
658:Paging supervisor
580:
579:
572:
135:or segmentation.
89:virtual addresses
73:memory management
16:(Redirected from
2795:
2760:
2759:
2750:
2749:
2740:
2739:
2730:
2729:
2720:
2719:
2647:Dangling pointer
2642:Buffer over-read
2614:Strong reference
2485:Memory allocator
2362:
2355:
2348:
2339:
2291:
2289:
2283:. Archived from
2282:
2212:
2211:
2209:
2207:
2192:
2186:
2183:
2177:
2174:
2168:
2167:
2155:
2145:
2139:
2138:
2136:
2134:
2120:
2114:
2113:
2095:
2071:
2065:
2064:
2062:
2049:
2043:
2042:
2034:
2028:
2027:
2025:
2023:
2014:Vyssotsky, V. A.
2006:
2000:
1999:
1997:
1995:
1989:
1979:
1973:
1972:
1970:
1968:
1958:
1947:
1941:
1940:
1933:
1924:
1923:
1895:
1889:
1888:
1886:
1884:
1874:
1865:
1857:
1851:
1850:
1848:
1846:
1823:
1817:
1816:
1814:
1812:
1789:
1783:
1782:
1754:
1748:
1747:
1745:
1735:
1729:
1728:
1726:
1724:
1707:
1696:
1690:
1689:
1669:
1663:
1662:
1657:. Archived from
1650:
1644:
1643:
1637:
1629:
1622:
1616:
1615:
1595:
1586:
1580:
1579:
1577:
1575:
1555:"Virtual memory"
1550:
1544:
1543:
1541:
1533:
1527:
1526:
1511:
1505:
1504:
1483:
1477:
1471:
1465:
1464:
1428:
1422:
1421:
1407:
1401:
1400:
1394:
1382:
1367:
1366:
1364:
1362:
1347:
1341:
1340:
1338:
1336:
1330:
1322:
1316:
1315:
1275:
1269:
1268:
1266:
1264:
1241:
1235:
1234:
1232:
1230:
1207:
1201:
1200:
1198:
1189:
1181:
1175:
1174:
1172:
1163:
1155:
1138:
1131:
1125:
1110:
1104:
1097:
1091:
1068:
1062:
1048:
990:Processor design
966:OS/VS2 Release 2
822:
821:
818:
813:
812:
809:
626:operating system
575:
568:
564:
561:
555:
532:
524:
454:to exploit it.
336:multiprogramming
311:Embedded systems
224:Electrologica X8
211:Atlas Supervisor
195:virtual machines
149:memory hierarchy
84:memory addresses
80:operating system
21:
2803:
2802:
2798:
2797:
2796:
2794:
2793:
2792:
2773:
2772:
2771:
2766:
2708:
2682:
2656:
2637:Buffer overflow
2623:
2550:
2522:
2479:
2446:
2413:
2384:
2371:
2366:
2332:Wayback Machine
2287:
2280:
2276:
2243:
2221:
2219:Further reading
2216:
2215:
2205:
2203:
2194:
2193:
2189:
2184:
2180:
2175:
2171:
2164:
2147:
2146:
2142:
2132:
2130:
2122:
2121:
2117:
2073:
2072:
2068:
2060:
2051:
2050:
2046:
2036:
2035:
2031:
2021:
2019:
2008:
2007:
2003:
1993:
1991:
1987:
1981:
1980:
1976:
1966:
1964:
1956:
1949:
1948:
1944:
1935:
1934:
1927:
1897:
1896:
1892:
1882:
1880:
1872:
1863:
1859:
1858:
1854:
1844:
1842:
1840:
1825:
1824:
1820:
1810:
1808:
1806:
1791:
1790:
1786:
1765:(12): 656–660.
1756:
1755:
1751:
1743:
1737:
1736:
1732:
1722:
1720:
1705:
1698:
1697:
1693:
1686:
1671:
1670:
1666:
1661:on 10 May 2017.
1652:
1651:
1647:
1630:
1624:
1623:
1619:
1593:
1588:
1587:
1583:
1573:
1571:
1569:
1552:
1551:
1547:
1539:
1535:
1534:
1530:
1516:IRE Trans EC-11
1513:
1512:
1508:
1485:
1484:
1480:
1472:
1468:
1430:
1429:
1425:
1409:
1408:
1404:
1392:
1384:
1383:
1370:
1360:
1358:
1349:
1348:
1344:
1334:
1332:
1328:
1324:
1323:
1319:
1277:
1276:
1272:
1262:
1260:
1258:
1243:
1242:
1238:
1228:
1226:
1224:
1209:
1208:
1204:
1196:
1187:
1183:
1182:
1178:
1170:
1161:
1157:
1156:
1152:
1147:
1142:
1141:
1132:
1128:
1111:
1107:
1098:
1094:
1072:virtual storage
1069:
1065:
1049:
1045:
1040:
1035:
985:
951:
882:
853:
836:
819:
816:
810:
807:
738:completion and
712:
660:
600:
576:
565:
559:
556:
545:
533:
522:
516:
479:models running
328:
185:built into the
175:
141:
98:computer memory
78:The computer's
69:virtual storage
39:
28:
23:
22:
15:
12:
11:
5:
2801:
2799:
2791:
2790:
2785:
2783:Virtual memory
2775:
2774:
2768:
2767:
2765:
2764:
2754:
2744:
2734:
2732:Virtual memory
2724:
2713:
2710:
2709:
2707:
2706:
2701:
2696:
2690:
2688:
2684:
2683:
2681:
2680:
2675:
2670:
2664:
2662:
2658:
2657:
2655:
2654:
2652:Stack overflow
2649:
2644:
2639:
2633:
2631:
2625:
2624:
2622:
2621:
2619:Weak reference
2616:
2611:
2606:
2601:
2596:
2591:
2586:
2581:
2576:
2571:
2566:
2560:
2558:
2552:
2551:
2549:
2548:
2543:
2538:
2532:
2530:
2524:
2523:
2521:
2520:
2515:
2510:
2505:
2500:
2495:
2489:
2487:
2481:
2480:
2478:
2477:
2472:
2467:
2462:
2460:Protected mode
2456:
2454:
2448:
2447:
2445:
2444:
2439:
2434:
2429:
2423:
2421:
2419:Virtual memory
2415:
2414:
2412:
2411:
2405:
2399:
2392:
2390:
2386:
2385:
2383:
2382:
2376:
2373:
2372:
2367:
2365:
2364:
2357:
2350:
2342:
2336:
2335:
2325:
2319:
2313:
2274:
2251:Address Spaces
2242:
2241:External links
2239:
2238:
2237:
2220:
2217:
2214:
2213:
2187:
2178:
2169:
2162:
2140:
2128:Multicians.org
2115:
2093:10.1.1.10.6731
2086:(5): 308–318.
2066:
2044:
2029:
2001:
1974:
1942:
1925:
1890:
1852:
1838:
1818:
1805:978-0738437668
1804:
1784:
1749:
1730:
1691:
1684:
1664:
1645:
1617:
1581:
1567:
1545:
1528:
1518:(2): 223–235,
1506:
1478:
1466:
1439:(4): 216–219.
1423:
1402:
1386:Denning, Peter
1368:
1342:
1317:
1270:
1257:978-8131730225
1256:
1236:
1222:
1202:
1176:
1149:
1148:
1146:
1143:
1140:
1139:
1126:
1105:
1092:
1088:z/Architecture
1063:
1042:
1041:
1039:
1036:
1034:
1033:
1027:
1022:
1015:Protected mode
1012:
1007:
1002:
997:
992:
986:
984:
981:
955:address spaces
950:
947:
881:
878:
852:
849:
835:
832:
776:
775:
753:
750:
711:
708:
697:
696:
693:
689:
686:
683:
680:
659:
656:
651:page registers
599:
596:
578:
577:
536:
534:
527:
515:
512:
492:protected mode
401:Atlas Computer
389:Atlas Computer
327:
324:
277:
276:
273:RCA Spectra 70
265:
256:
239:
227:
217:
174:
171:
140:
137:
65:virtual memory
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
2800:
2789:
2786:
2784:
2781:
2780:
2778:
2763:
2755:
2753:
2745:
2743:
2735:
2733:
2725:
2723:
2715:
2714:
2711:
2705:
2702:
2700:
2697:
2695:
2692:
2691:
2689:
2685:
2679:
2676:
2674:
2671:
2669:
2668:Fragmentation
2666:
2665:
2663:
2659:
2653:
2650:
2648:
2645:
2643:
2640:
2638:
2635:
2634:
2632:
2630:
2629:Memory safety
2626:
2620:
2617:
2615:
2612:
2610:
2607:
2605:
2602:
2600:
2597:
2595:
2592:
2590:
2587:
2585:
2582:
2580:
2577:
2575:
2572:
2570:
2567:
2565:
2562:
2561:
2559:
2557:
2553:
2547:
2544:
2542:
2539:
2537:
2534:
2533:
2531:
2529:
2525:
2519:
2516:
2514:
2511:
2509:
2506:
2504:
2501:
2499:
2496:
2494:
2491:
2490:
2488:
2486:
2482:
2476:
2473:
2471:
2468:
2466:
2463:
2461:
2458:
2457:
2455:
2453:
2449:
2443:
2440:
2438:
2435:
2433:
2432:Memory paging
2430:
2428:
2427:Demand paging
2425:
2424:
2422:
2420:
2416:
2409:
2406:
2403:
2400:
2397:
2394:
2393:
2391:
2387:
2381:
2378:
2377:
2374:
2370:
2363:
2358:
2356:
2351:
2349:
2344:
2343:
2340:
2333:
2329:
2326:
2323:
2320:
2317:
2314:
2311:
2307:
2303:
2299:
2295:
2286:
2279:
2275:
2273:
2270:
2267:
2264:
2261:
2258:
2255:
2252:
2248:
2245:
2244:
2240:
2235:
2234:1-55860-724-2
2231:
2227:
2223:
2222:
2218:
2201:
2197:
2191:
2188:
2182:
2179:
2173:
2170:
2165:
2159:
2156:. MIT Press.
2154:
2153:
2144:
2141:
2129:
2125:
2119:
2116:
2111:
2107:
2103:
2099:
2094:
2089:
2085:
2081:
2077:
2070:
2067:
2059:
2057:
2048:
2045:
2040:
2033:
2030:
2018:
2015:
2011:
2010:Corbató, F.J.
2005:
2002:
1986:
1985:
1978:
1975:
1962:
1955:
1954:
1946:
1943:
1938:
1932:
1930:
1926:
1921:
1917:
1913:
1909:
1906:(1–4): 5–29.
1905:
1901:
1894:
1891:
1878:
1871:
1870:
1862:
1856:
1853:
1841:
1835:
1831:
1830:
1822:
1819:
1807:
1801:
1797:
1796:
1788:
1785:
1780:
1776:
1772:
1768:
1764:
1760:
1753:
1750:
1742:
1741:
1734:
1731:
1719:
1715:
1711:
1704:
1703:
1695:
1692:
1687:
1681:
1677:
1676:
1668:
1665:
1660:
1656:
1653:Joyner, Ian.
1649:
1646:
1641:
1635:
1627:
1621:
1618:
1613:
1609:
1605:
1601:
1600:
1592:
1585:
1582:
1570:
1564:
1560:
1556:
1549:
1546:
1538:
1532:
1529:
1525:
1521:
1517:
1510:
1507:
1503:
1499:
1495:
1491:
1490:
1482:
1479:
1475:
1474:Jessen (2004)
1470:
1467:
1462:
1458:
1454:
1450:
1446:
1442:
1438:
1435:(in German).
1434:
1427:
1424:
1419:
1415:
1414:
1406:
1403:
1398:
1391:
1387:
1381:
1379:
1377:
1375:
1373:
1369:
1356:
1352:
1346:
1343:
1327:
1321:
1318:
1313:
1309:
1305:
1301:
1297:
1293:
1289:
1285:
1281:
1274:
1271:
1259:
1253:
1249:
1248:
1240:
1237:
1225:
1223:9781627056021
1219:
1215:
1214:
1206:
1203:
1195:
1194:
1186:
1180:
1177:
1169:
1168:
1160:
1154:
1151:
1144:
1136:
1130:
1127:
1123:
1119:
1115:
1109:
1106:
1102:
1096:
1093:
1089:
1085:
1081:
1077:
1073:
1067:
1064:
1061:
1057:
1053:
1047:
1044:
1037:
1031:
1028:
1026:
1023:
1020:
1016:
1013:
1011:
1008:
1006:
1003:
1001:
998:
996:
993:
991:
988:
987:
982:
980:
977:
975:
971:
967:
963:
958:
956:
948:
946:
944:
940:
936:
931:
927:
924:
919:
915:
911:
906:
904:
903:IBM System/38
900:
895:
891:
887:
879:
877:
873:
870:
866:
862:
861:page stealing
858:
850:
848:
845:
841:
833:
831:
829:
825:
804:
800:
796:
792:
788:
786:
781:
773:
769:
765:
761:
757:
754:
751:
748:
747:
746:
743:
741:
737:
733:
729:
725:
721:
717:
709:
707:
705:
700:
694:
690:
687:
684:
681:
678:
677:
676:
672:
670:
666:
657:
655:
653:
652:
647:
642:
639:
635:
629:
627:
623:
620:
616:
612:
608:
604:
597:
595:
593:
589:
585:
574:
571:
563:
560:December 2010
553:
549:
543:
542:
537:This section
535:
531:
526:
525:
521:
520:Memory paging
513:
511:
509:
505:
501:
497:
493:
489:
484:
482:
478:
474:
470:
465:
461:
455:
453:
449:
445:
441:
437:
433:
428:
426:
422:
418:
414:
410:
406:
402:
398:
390:
385:
381:
379:
375:
371:
367:
363:
359:
356:
351:
349:
345:
341:
337:
333:
325:
323:
320:
316:
312:
308:
306:
302:
298:
294:
290:
289:address space
286:
281:
274:
270:
266:
264:
260:
257:
255:
251:
247:
243:
240:
238:
235:
231:
228:
225:
221:
218:
216:
212:
208:
207:
206:
204:
200:
196:
192:
188:
184:
180:
172:
170:
168:
164:
162:
158:
154:
150:
146:
145:fragmentation
138:
136:
134:
130:
125:
123:
119:
115:
111:
107:
106:address space
103:
99:
95:
91:
90:
85:
81:
76:
74:
70:
66:
62:
54:
50:
45:
41:
37:
33:
19:
2418:
2293:
2285:the original
2257:Segmentation
2225:
2204:. Retrieved
2199:
2190:
2181:
2172:
2151:
2143:
2131:. Retrieved
2127:
2118:
2083:
2079:
2069:
2055:
2047:
2032:
2020:. Retrieved
2004:
1992:. Retrieved
1983:
1977:
1965:. Retrieved
1952:
1945:
1903:
1899:
1893:
1881:. Retrieved
1868:
1855:
1843:. Retrieved
1828:
1821:
1809:. Retrieved
1794:
1787:
1762:
1758:
1752:
1739:
1733:
1721:. Retrieved
1701:
1694:
1674:
1667:
1659:the original
1648:
1620:
1603:
1597:
1584:
1572:. Retrieved
1558:
1548:
1531:
1515:
1509:
1493:
1487:
1481:
1469:
1436:
1432:
1426:
1417:
1411:
1405:
1396:
1359:. Retrieved
1355:the original
1345:
1333:. Retrieved
1320:
1287:
1283:
1273:
1261:. Retrieved
1246:
1239:
1227:. Retrieved
1212:
1205:
1192:
1179:
1166:
1153:
1129:
1108:
1095:
1071:
1066:
1046:
978:
959:
952:
932:
928:
907:
890:segmentation
883:
874:
854:
837:
814:, as do the
789:
777:
764:I/O channels
756:Data buffers
744:
727:
723:
719:
715:
713:
710:Pinned pages
701:
698:
673:
661:
649:
643:
633:
630:
609:used by the
601:
581:
566:
557:
546:Please help
541:verification
538:
508:double fault
504:segmentation
485:
469:minicomputer
456:
447:
429:
425:segmentation
403:. It used a
394:
377:
374:cache memory
369:
365:
352:
340:multitasking
329:
309:
282:
278:
176:
165:
142:
126:
122:disk storage
102:Main storage
93:
87:
77:
68:
64:
58:
40:
2673:Memory leak
2022:13 November
1994:25 February
1967:28 November
1655:"Burroughs"
1626:"The Atlas"
1420:(4): 71–72.
1290:(1): 1–31.
910:Intel 80386
894:Intel 80286
888:B5500, use
869:working set
603:Page tables
598:Page tables
500:Intel 80386
496:Intel 80286
464:David Sayre
432:hypervisors
413:drum memory
409:core memory
315:determinism
157:to relocate
2777:Categories
2437:Page table
1883:18 January
1606:(5): 486.
1574:10 January
1263:16 October
1229:16 October
1145:References
912:and later
780:System/370
740:page fault
667:, e.g., a
619:page fault
518:See also:
332:overlaying
297:OS/VS2 SVS
199:mainframes
139:Properties
2584:Finalizer
2465:Real mode
2206:9 October
2133:9 October
2088:CiteSeerX
1963:. 1021326
1920:0166-5316
1496:: 15–21,
1453:0170-6012
1304:1539-9087
886:Burroughs
865:thrashing
851:Thrashing
844:interrupt
830:systems.
828:Unix-like
824:man pages
732:interrupt
622:exception
592:kilobytes
434:in their
355:physicist
348:registers
234:Burroughs
191:emulators
129:libraries
61:computing
2518:ptmalloc
2513:mimalloc
2503:jemalloc
2493:dlmalloc
2389:Hardware
1779:15655353
1634:cite web
1461:11514875
1388:(1997).
1335:28 April
1312:18156695
1082:through
983:See also
968:through
826:on many
611:hardware
271:for the
261:for the
252:for the
232:for the
222:for the
213:for the
153:overlays
110:segments
2589:Garbage
2508:libumem
2410:(IOMMU)
2330:at the
2310:Multics
2302:TSS/360
2110:6434322
1845:18 July
1811:18 July
1723:12 June
1708:. 1971
1361:9 March
1078:on the
964:, from
908:In the
899:Multics
799:Windows
795:OpenVMS
791:Multics
648:, used
646:SDS 940
494:of the
423:, with
360:at the
326:History
285:process
259:Multics
246:TSS/360
92:, into
71:, is a
2661:Issues
2308:, and
2232:
2160:
2108:
2090:
1918:
1836:
1802:
1777:
1682:
1565:
1459:
1451:
1310:
1302:
1254:
1220:
1122:DOS/VS
1118:OS/VS1
1114:DOS/VS
1101:360/65
1080:360/67
960:IBM's
943:linker
918:32-bit
857:paging
840:OS/VS1
720:locked
716:pinned
692:error.
634:region
473:NORD-1
405:paging
344:PDP-10
303:) are
293:OS/VS1
263:GE 645
250:CP/CMS
133:paging
2687:Other
2498:Hoard
2404:(TLB)
2398:(MMU)
2298:CP-67
2288:(PDF)
2281:(PDF)
2106:S2CID
2061:(PDF)
1988:(PDF)
1957:(PDF)
1873:(PDF)
1864:(PDF)
1775:S2CID
1744:(PDF)
1706:(PDF)
1594:(PDF)
1540:(PDF)
1457:S2CID
1393:(PDF)
1331:. AMD
1329:(PDF)
1308:S2CID
1197:(PDF)
1188:(PDF)
1171:(PDF)
1162:(PDF)
1135:IBM Z
1056:disks
1052:drums
1038:Notes
1017:, an
939:Win32
914:IA-32
855:When
817:mlock
808:mlock
768:buses
728:wired
726:, or
724:fixed
588:pages
586:into
444:S/370
440:CP-67
436:CP-40
421:B5000
319:traps
301:IBM i
237:B5000
215:Atlas
173:Usage
67:, or
2263:TLBs
2230:ISBN
2208:2016
2158:ISBN
2135:2016
2024:2007
1996:2022
1969:2013
1916:ISSN
1885:2023
1847:2017
1834:ISBN
1813:2017
1800:ISBN
1725:2022
1680:ISBN
1640:link
1576:2023
1563:ISBN
1449:ISSN
1363:2015
1337:2015
1300:ISSN
1265:2017
1252:ISBN
1231:2017
1218:ISBN
1120:and
1112:IBM
1084:z/OS
970:z/OS
937:and
935:mmap
901:and
859:and
797:and
438:and
370:i.e.
346:via
338:and
295:and
267:The
248:and
209:the
193:and
53:DASD
2306:MTS
2098:doi
1908:doi
1877:IBM
1767:doi
1714:doi
1608:doi
1520:doi
1498:doi
1441:doi
1292:doi
1133:On
1086:on
1076:TSS
1058:or
1019:x86
962:MVS
838:In
787:).
762:or
736:I/O
550:by
488:x86
481:VMS
477:VAX
460:IBM
448:SIE
378:sic
275:/46
242:MTS
230:MCP
203:DOS
187:CPU
96:in
59:In
49:RAM
2779::
2304:,
2300:,
2198:.
2126:.
2104:.
2096:.
2084:15
2082:.
2078:.
2012:;
1959:.
1928:^
1914:.
1904:60
1902:.
1866:.
1773:.
1763:12
1761:.
1636:}}
1632:{{
1604:25
1602:.
1596:.
1557:.
1492:,
1455:.
1447:.
1437:19
1418:26
1416:.
1395:.
1371:^
1306:.
1298:.
1286:.
1282:.
1190:.
1164:.
1116:,
820:()
811:()
722:,
628:.
483:.
452:VM
350:.
244:,
163:.
100:.
63:,
2361:e
2354:t
2347:v
2318:.
2312:.
2236:)
2228:(
2210:.
2166:.
2137:.
2112:.
2100::
2063:.
2054:"
2041:.
2026:.
1998:.
1971:.
1939:.
1922:.
1910::
1887:.
1849:.
1815:.
1781:.
1769::
1727:.
1716::
1688:.
1642:)
1614:.
1610::
1578:.
1522::
1500::
1494:7
1476:.
1463:.
1443::
1399:.
1365:.
1339:.
1314:.
1294::
1288:8
1267:.
1233:.
1090:.
573:)
567:(
562:)
558:(
544:.
38:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.