440:) for restoring long file names. The component became famous in the early 2000s as the subject of an e-mail hoax. The hoax claimed that SULFNBK.EXE was a virus, and contained instructions to locate and delete the file. While the instructions worked, they were needless and (in some rare cases, for example, when the long file names are damaged and need to be restored) can cause disruptions, as SULFNBK.EXE is not a virus, but instead an operating system component.
17:
128:
461:, has been active since 2008. The victim is quoted his or her name and address, and is told: "I'm calling for Microsoft (or an entity that sounds like it is connected to Microsoft, such as the "Windows Service Center" or "Windows Technical Department"). We've had a report from your internet service provider of serious virus problems from your
51:
claimed to originate from reputable computer organizations together with mainstream news media. These bogus sources are quoted in order to give the hoax more credibility. Typically, the warnings use emotive language, stress the urgent nature of the threat and encourage readers to forward the message to other people as soon as possible.
469:, which displays apparently critical warnings, and is directed to a website to download an application to allow the scammer to control his or her computer remotely. The caller supposedly fixes the problems and demands a fee for the service. In addition to the fraudulent fee, the process usually enables
407:
A series of e-mails first sent in
February 2006. The "virus" referred to by the e-mail does not actually exist. The hoax e-mail warns recipients of a recent outbreak of "Olympic Torch" viruses, contained in e-mails titled "Invitation", which erase the hard disk of the user's computer when opened. The
50:
Most hoaxes are sensational in nature and easily identified by the fact that they indicate that the virus will do nearly impossible things, like blow up the recipient's computer and set it on fire, or less sensationally, delete everything on the user's computer. They often include fake announcements
346:
Involved an e-mail spam in 2002 that advised computer users to delete a file named jdbgmgr.exe because it was a computer virus. jdbgmgr.exe, which had a little teddy bear-like icon (The
Microsoft Bear), was actually a valid Microsoft Windows file, the Debugger Registrar for Java (also known as Java
308:
Warnings about a computer virus named "Good Times" began being passed around among
Internet users in 1994. Was supposedly transmitted via an email bearing the subject header "Good Times" or "Goodtimes," hence the virus's name, and the warning recommended deleting any such email unread. The virus
54:
Virus hoaxes are usually harmless and accomplish nothing more than annoying people who identify it as a hoax and wasting the time of people who forward the message. Nevertheless, a number of hoaxes have warned users that vital system files are viruses and encourage the user to delete the file,
113:
Corporate users can get rid of the hoax problem by simply setting a strict company guideline: End users must not forward virus alarms. Ever. It's not the job of an end user anyway. If such message is received, end users could forward it to the IT department but not to anyone else.
269:
A chain message beginning around 2006. It begins with the message warning of a virus that hides in an attachment labeled "Black in White House" or something similar, saying that if the user opens it, then it opens an
Olympic Torch that burns down the C disk.
565:
and uncompress it onto the hard disk. The
Windows Registry is finally deleted and the boot options changed. The virus then reboots the computer, leaving the user facing the Linux login prompt with all their Windows security problems solved.
545:
or other similar low-technology populations who have no computers, programming skills or electricity to create viruses and thus ask users to delete their own hard drive contents manually after forwarding the message to their friends.
326:
An e-mail spam in 2006 that advised computer users to delete an email, with any type of attachment that stated "invitation" because it was a computer virus. This is also known as the
Olympic Torch virus hoax (see below).
364:
Spread through the
Internet around January 2001. It was a virus attached to an e-mail, which was spread around the Internet. The attached file was supposedly called "Life is beautiful.pps" or "La vita è bella.pps".
77:
Hoaxes are distinct from computer pranks, which are harmless programs that perform unwanted and annoying actions on a computer, such as randomly moving the mouse, turning the screen display upside down, etc.
557:, but with its aim of installing Linux on the victim's computer without the owner's permission. The story says that it was spread via e-mail, contained in a message titled "Important Message About
253:
joke and never actually existed, but was mistakenly reported as a real cyberweapon (albeit without mentions of the spread and mutation) by several news organizations well into the early 2000s.
110:
Hoax warnings are typically scare alerts started by malicious people – and passed on by innocent individuals that think they are helping the community by spreading the warning.
960:
926:
1093:
412:, McAfee, and Microsoft as one of the most dangerous viruses yet reported. This email, which was started in February 2006, is safe to delete when the user wants.
1125:
769:
196:
and McAfee named "Antichrist", telling the user that it is installed via an e-mail with the subject line: "SURPRISE?!!!!!!!!!!" after which it destroys the
1420:
585:
245:, that had spread past its intended target and "mutated" to be able to destroy the display of any computer with windowing technology, namely
230:
2139:
432:
SULFNBK.EXE (short for Setup
Utility for Long File Name Backup) is an internal component of the Microsoft Windows operating system (in
386:
Programs were actual, legitimate computer games; author claimed that they were viruses which would "wipe out" the user's hard drive on
498:. The song makes fun of the exaggerated claims that are made in virus hoaxes, such as legally changing your name or opening a rift in
2076:
1118:
485:
of novice computer users convinced to delete files on the basis of hoaxes has been parodied in several popular jokes and songs.
2069:
1857:
964:
934:
580:
135:
86:
Anti-virus specialists agree that recipients should delete virus hoaxes when they receive them, instead of forwarding them.
1060:
71:
796:
96:
We are advising users who receive the email to delete it and DO NOT pass it on as this is how an email HOAX propagates.
1880:
1111:
742:
773:
561:
Security". It was supposed to first spread the virus to other computers, then download a stripped-down version of
489:
42:
that tells the recipients to forward it to everyone they know, but it can also be in the form of a pop-up window.
2149:
2134:
1837:
1198:
530:
1376:
1371:
987:
2101:
2038:
1749:
1686:
1628:
1570:
1560:
1273:
1258:
1038:
178:
1754:
1450:
494:
452:
332:
56:
2129:
2021:
1973:
1953:
1872:
1862:
1646:
1530:
1014:
1988:
1779:
1729:
1465:
1460:
1430:
1293:
197:
1948:
1938:
1895:
1666:
1493:
1455:
1351:
1098:
309:
described in the warnings did not exist, but the warnings themselves, were, in effect, virus-like.
250:
2059:
1822:
1721:
1711:
1661:
1580:
1361:
1356:
1248:
1134:
242:
714:
1968:
1905:
1681:
1651:
1613:
1608:
1603:
1508:
1488:
1346:
1331:
1283:
1228:
558:
462:
35:
2106:
1930:
1910:
1812:
1774:
1759:
1550:
1525:
1399:
1381:
1341:
1238:
1153:
289:
Would supposedly erase the user's hard drive and steal the user's screen name and password.
904:
2096:
2081:
2026:
1847:
1623:
1470:
1445:
1410:
1253:
632:
294:
275:
1010:"Weird Al unleashes his new album with a Bill Plympton Video DON'T DOWNLOAD THIS SONG!!!"
74:—exploiting users' concern, ignorance, and disinclination to investigate before acting.
2144:
1978:
1842:
1827:
1789:
1769:
1706:
1545:
1520:
1425:
1308:
1288:
1243:
1221:
956:
499:
32:
828:
408:
hoax email further purports the virus to be acknowledged by such reputable sources as
2123:
2086:
2043:
1852:
1832:
1671:
1415:
1263:
1168:
801:
604:
554:
67:
1088:
857:
541:
virus, Discount virus and many others. This joke email claims to be authored by the
2091:
2011:
2006:
1890:
1734:
1676:
1656:
1163:
686:
661:
466:
39:
16:
879:
481:
The virus hoax has become part of the culture of the twenty-first century and the
1983:
1943:
1794:
1701:
1696:
1565:
1555:
1540:
1366:
1336:
1318:
1183:
482:
417:
371:
246:
226:
60:
2064:
1963:
1920:
1885:
1804:
1744:
1638:
1394:
1278:
1268:
1193:
1178:
1173:
1148:
1064:
833:
806:
437:
433:
1784:
1764:
1739:
1618:
1590:
1503:
1440:
1326:
1188:
1158:
562:
387:
221:
193:
746:
1915:
1691:
1515:
1498:
1435:
1298:
1216:
1208:
738:
538:
238:
100:
2031:
2016:
1900:
1817:
1535:
1303:
1233:
1009:
575:
553:
virus is another parody of the virus hoax, based on the concept of the
550:
526:
514:
470:
1958:
1103:
710:
522:
89:
20:
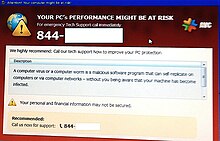
A hoax pop-up message warning of a computer virus, on a Compaq laptop
1998:
1598:
542:
518:
510:
458:
205:
15:
361:
Supposedly a hacker with the alias "Life owner" or "Dono da vida"
1480:
534:
234:
55:
possibly damaging the system. Examples of this type include the
1107:
457:
A telephone scam, commonly operated from call centres based in
409:
122:
513:
Computer Virus, manual virus, the Blond
Computer Virus, the
66:
Some consider virus hoaxes and other chain e-mails to be a
192:
A hoax that warned about a supposed virus discovered by
988:"Virus phone scam being run from call centres in India"
139:
31:
is a message warning the recipients of a non-existent
2052:
1997:
1929:
1871:
1803:
1720:
1637:
1589:
1479:
1390:
1317:
1207:
1141:
465:computer." The victim is then directed to open the
880:"Good Times Virus Hoax Frequently Asked Questions"
856:Mikkelson, Barbara and David P. (January 2008).
685:Mikkelson, Barbara and David P. (January 2008).
660:Mikkelson, Barbara and David P. (January 2008).
200:sector of the hard disk, rendering it unusable.
24:Message warning of a non-existent computer virus
898:
896:
705:
703:
105:
94:
1119:
377:Sometimes included their other game "Y2KGame"
8:
715:"Virus Profile: A Virtual Card For You Hoax"
1126:
1112:
1104:
733:
731:
370:NVISION DESIGN, INC. games ("Frogapult," "
680:
678:
655:
653:
509:which has been circulated under the name
473:to be uploaded to the victim's computer.
961:"FROGAPULT, ELFBOWL, Y2KGAME Virus Hoax"
157:
70:in and of themselves. They replicate by
596:
586:Timeline of computer viruses and worms
505:Another parody of virus hoaxes is the
398:"Postcard" or "Postcard from Hallmark"
905:"Olympic Torch Invitation Virus Hoax"
492:'s song "Virus Alert" from the album
7:
627:
625:
231:United States Intelligence Community
633:"What is a hoax? - Panda Security"
14:
990:. Guardian News and Media Limited
925:Koris, George (15 January 2002).
829:"Black Muslim in the White House"
797:"Iraqi Cyberwar: an Ageless Joke"
126:
1770:Party platforms (or manifestos)
986:Charles Arthur (18 July 2010).
795:Smith, George (10 March 2003).
347:Debug Manager, hence jdbgmgr).
261:Black Muslim in the White House
241:, capable of "eating" a user's
1099:Trend Micro Virus Encyclopedia
903:Christensen, Brett M. (2008).
768:Gutierrez, Ralph (July 2001).
581:Comparison of computer viruses
107:Do not forward hoax messages.
1:
1061:"Attack of the Tuxissa Virus"
317:(Allright now/I'm just sayin)
1858:Rally 'round the flag effect
1059:Baughn, James (March 1999).
878:Jones, Les (December 1998).
1039:"Humor: For a good time..."
38:. The message is usually a
2166:
2140:Computer security exploits
1037:Pearson, Karl (May 2000).
933:. Symantec. Archived from
450:
1199:Manipulation (psychology)
1377:Criticism of advertising
1094:Symantec Threat Explorer
927:"Life is beautiful Hoax"
258:Black in the White House
2039:Promotional merchandise
1750:Character assassination
1687:Narcotizing dysfunction
1561:Photograph manipulation
1274:Guerrilla communication
858:"Budweiser Frogs Virus"
358:Brazil (first reported)
2022:Product demonstrations
1451:Historical negationism
495:Straight Outta Lynwood
453:Technical support scam
116:
98:
57:jdbgmgr.exe virus hoax
21:
1954:Reputation management
1873:Psychological warfare
1722:Political campaigning
1531:Firehose of falsehood
637:www.pandasecurity.com
314:Invitation attachment
19:
1989:Corporate propaganda
957:Symantec Corporation
739:F-Secure Corporation
537:Computer Virus, the
521:Computer Virus, the
517:Computer Virus, the
467:Windows event viewer
225:article detailing a
140:adding missing items
2077:Media concentration
1949:Non-apology apology
1939:Cult of personality
1667:Emotive conjugation
1421:Burying of scholars
1089:McAfee virus hoaxes
1018:. 11 September 2006
687:"SULFNBK.EXE Virus"
662:"JDBGMGR.EXE Virus"
490:"Weird Al" Yankovic
488:One such parody is
29:computer virus hoax
2060:Influence-for-hire
1853:National mythology
1823:Crowd manipulation
1712:Tabloid journalism
1581:Video manipulation
1526:Fictitious entries
1249:Civil disobedience
1135:Media manipulation
1015:Ain't It Cool News
507:honor system virus
210:April Fool's 1991
138:; you can help by
72:social engineering
22:
2115:
2114:
1881:Airborne leaflets
1760:Election promises
1614:Product placement
1489:Alternative facts
1229:Alternative media
1067:on 11 August 2004
959:(February 2007).
776:on 1 January 2007
770:"Antichrist Hoax"
713:(December 2003).
609:Malwarebytes Labs
444:
443:
355:Life is wonderful
352:Life is beautiful
249:. Intended as an
229:developed by the
156:
155:
2157:
2150:Types of malware
2135:Computer viruses
2107:Media proprietor
1931:Public relations
1911:Public diplomacy
1896:Information (IT)
1775:Name recognition
1400:Media regulation
1382:Annoyance factor
1239:Call-out culture
1154:Crowd psychology
1128:
1121:
1114:
1105:
1077:
1076:
1074:
1072:
1063:. Archived from
1056:
1050:
1049:
1047:
1045:
1034:
1028:
1027:
1025:
1023:
1006:
1000:
999:
997:
995:
983:
977:
976:
974:
972:
963:. Archived from
953:
947:
946:
944:
942:
922:
916:
915:
913:
911:
900:
891:
890:
888:
886:
875:
869:
868:
866:
864:
853:
847:
846:
844:
842:
825:
819:
818:
816:
814:
805:. Archived from
792:
786:
785:
783:
781:
772:. Archived from
765:
759:
758:
756:
754:
745:. Archived from
735:
726:
725:
723:
721:
707:
698:
697:
695:
693:
682:
673:
672:
670:
668:
657:
648:
647:
645:
643:
629:
620:
619:
617:
615:
601:
525:Computer Virus,
251:April Fools' Day
233:for use against
158:
151:
148:
130:
129:
123:
2165:
2164:
2160:
2159:
2158:
2156:
2155:
2154:
2120:
2119:
2116:
2111:
2102:Media influence
2097:Media franchise
2082:Media democracy
2048:
1993:
1925:
1867:
1848:Loaded language
1799:
1716:
1633:
1585:
1475:
1404:
1386:
1313:
1254:Culture jamming
1203:
1137:
1132:
1085:
1080:
1070:
1068:
1058:
1057:
1053:
1043:
1041:
1036:
1035:
1031:
1021:
1019:
1008:
1007:
1003:
993:
991:
985:
984:
980:
970:
968:
955:
954:
950:
940:
938:
937:on 7 March 2007
924:
923:
919:
909:
907:
902:
901:
894:
884:
882:
877:
876:
872:
862:
860:
855:
854:
850:
840:
838:
827:
826:
822:
812:
810:
794:
793:
789:
779:
777:
767:
766:
762:
752:
750:
749:on 22 June 2012
743:"Hoax Warnings"
737:
736:
729:
719:
717:
709:
708:
701:
691:
689:
684:
683:
676:
666:
664:
659:
658:
651:
641:
639:
631:
630:
623:
613:
611:
603:
602:
598:
594:
572:
479:
455:
449:
295:Goodtimes virus
276:Budweiser Frogs
152:
146:
143:
127:
121:
84:
48:
25:
12:
11:
5:
2163:
2161:
2153:
2152:
2147:
2142:
2137:
2132:
2122:
2121:
2113:
2112:
2110:
2109:
2104:
2099:
2094:
2089:
2084:
2079:
2074:
2073:
2072:
2062:
2056:
2054:
2050:
2049:
2047:
2046:
2041:
2036:
2035:
2034:
2024:
2019:
2014:
2009:
2003:
2001:
1995:
1994:
1992:
1991:
1986:
1981:
1979:Understatement
1976:
1971:
1966:
1961:
1956:
1951:
1946:
1941:
1935:
1933:
1927:
1926:
1924:
1923:
1918:
1913:
1908:
1903:
1898:
1893:
1888:
1883:
1877:
1875:
1869:
1868:
1866:
1865:
1860:
1855:
1850:
1845:
1843:Indoctrination
1840:
1835:
1830:
1828:Disinformation
1825:
1820:
1815:
1809:
1807:
1801:
1800:
1798:
1797:
1792:
1790:Smear campaign
1787:
1782:
1777:
1772:
1767:
1762:
1757:
1752:
1747:
1742:
1737:
1732:
1726:
1724:
1718:
1717:
1715:
1714:
1709:
1707:Sensationalism
1704:
1699:
1694:
1689:
1684:
1679:
1674:
1669:
1664:
1659:
1654:
1649:
1647:Agenda-setting
1643:
1641:
1635:
1634:
1632:
1631:
1626:
1621:
1616:
1611:
1606:
1601:
1595:
1593:
1587:
1586:
1584:
1583:
1578:
1573:
1568:
1563:
1558:
1553:
1548:
1543:
1538:
1533:
1528:
1523:
1521:False document
1518:
1513:
1512:
1511:
1501:
1496:
1491:
1485:
1483:
1477:
1476:
1474:
1473:
1468:
1463:
1458:
1453:
1448:
1443:
1438:
1433:
1428:
1426:Catch and kill
1423:
1418:
1413:
1407:
1405:
1403:
1402:
1397:
1391:
1388:
1387:
1385:
1384:
1379:
1374:
1369:
1364:
1359:
1354:
1349:
1344:
1339:
1334:
1329:
1323:
1321:
1315:
1314:
1312:
1311:
1306:
1301:
1296:
1291:
1286:
1281:
1276:
1271:
1266:
1261:
1259:Demonstrations
1256:
1251:
1246:
1244:Cancel culture
1241:
1236:
1231:
1226:
1225:
1224:
1213:
1211:
1205:
1204:
1202:
1201:
1196:
1191:
1186:
1181:
1176:
1171:
1166:
1161:
1156:
1151:
1145:
1143:
1139:
1138:
1133:
1131:
1130:
1123:
1116:
1108:
1102:
1101:
1096:
1091:
1084:
1083:External links
1081:
1079:
1078:
1051:
1029:
1001:
978:
967:on 27 May 2009
948:
917:
892:
870:
848:
837:. 20 June 2013
820:
809:on 5 June 2003
787:
760:
727:
699:
674:
649:
621:
595:
593:
590:
589:
588:
583:
578:
571:
568:
500:time and space
478:
475:
451:Main article:
448:
447:Telephone scam
445:
442:
441:
430:
427:
424:
421:
414:
413:
405:
402:
399:
396:
392:
391:
384:
381:
378:
375:
367:
366:
362:
359:
356:
353:
349:
348:
344:
341:
338:
335:
329:
328:
324:
321:
318:
315:
311:
310:
306:
303:
300:
297:
291:
290:
287:
284:
281:
278:
272:
271:
267:
264:
262:
259:
255:
254:
217:
214:
213:United States
211:
208:
202:
201:
190:
189:Dylan Nicholas
187:
186:United Kingdom
184:
181:
175:
174:
171:
168:
165:
162:
154:
153:
133:
131:
120:
117:
83:
80:
47:
46:Identification
44:
33:computer virus
23:
13:
10:
9:
6:
4:
3:
2:
2162:
2151:
2148:
2146:
2143:
2141:
2138:
2136:
2133:
2131:
2128:
2127:
2125:
2118:
2108:
2105:
2103:
2100:
2098:
2095:
2093:
2090:
2088:
2087:Media ecology
2085:
2083:
2080:
2078:
2075:
2071:
2070:United States
2068:
2067:
2066:
2063:
2061:
2058:
2057:
2055:
2051:
2045:
2044:Telemarketing
2042:
2040:
2037:
2033:
2030:
2029:
2028:
2025:
2023:
2020:
2018:
2015:
2013:
2010:
2008:
2005:
2004:
2002:
2000:
1996:
1990:
1987:
1985:
1982:
1980:
1977:
1975:
1972:
1970:
1967:
1965:
1962:
1960:
1957:
1955:
1952:
1950:
1947:
1945:
1942:
1940:
1937:
1936:
1934:
1932:
1928:
1922:
1919:
1917:
1914:
1912:
1909:
1907:
1904:
1902:
1899:
1897:
1894:
1892:
1889:
1887:
1884:
1882:
1879:
1878:
1876:
1874:
1870:
1864:
1861:
1859:
1856:
1854:
1851:
1849:
1846:
1844:
1841:
1839:
1836:
1834:
1833:Fearmongering
1831:
1829:
1826:
1824:
1821:
1819:
1816:
1814:
1811:
1810:
1808:
1806:
1802:
1796:
1793:
1791:
1788:
1786:
1783:
1781:
1778:
1776:
1773:
1771:
1768:
1766:
1763:
1761:
1758:
1756:
1753:
1751:
1748:
1746:
1743:
1741:
1738:
1736:
1733:
1731:
1728:
1727:
1725:
1723:
1719:
1713:
1710:
1708:
1705:
1703:
1700:
1698:
1695:
1693:
1690:
1688:
1685:
1683:
1680:
1678:
1675:
1673:
1672:False balance
1670:
1668:
1665:
1663:
1660:
1658:
1655:
1653:
1650:
1648:
1645:
1644:
1642:
1640:
1636:
1630:
1629:Word of mouth
1627:
1625:
1622:
1620:
1617:
1615:
1612:
1610:
1607:
1605:
1602:
1600:
1597:
1596:
1594:
1592:
1588:
1582:
1579:
1577:
1574:
1572:
1569:
1567:
1564:
1562:
1559:
1557:
1554:
1552:
1549:
1547:
1544:
1542:
1539:
1537:
1534:
1532:
1529:
1527:
1524:
1522:
1519:
1517:
1514:
1510:
1507:
1506:
1505:
1502:
1500:
1497:
1495:
1492:
1490:
1487:
1486:
1484:
1482:
1478:
1472:
1469:
1467:
1464:
1462:
1459:
1457:
1454:
1452:
1449:
1447:
1444:
1442:
1439:
1437:
1434:
1432:
1429:
1427:
1424:
1422:
1419:
1417:
1416:Broadcast law
1414:
1412:
1409:
1408:
1406:
1401:
1398:
1396:
1393:
1392:
1389:
1383:
1380:
1378:
1375:
1373:
1370:
1368:
1365:
1363:
1360:
1358:
1355:
1353:
1350:
1348:
1345:
1343:
1340:
1338:
1335:
1333:
1330:
1328:
1325:
1324:
1322:
1320:
1316:
1310:
1307:
1305:
1302:
1300:
1297:
1295:
1292:
1290:
1287:
1285:
1282:
1280:
1277:
1275:
1272:
1270:
1267:
1265:
1264:Deplatforming
1262:
1260:
1257:
1255:
1252:
1250:
1247:
1245:
1242:
1240:
1237:
1235:
1232:
1230:
1227:
1223:
1220:
1219:
1218:
1215:
1214:
1212:
1210:
1206:
1200:
1197:
1195:
1192:
1190:
1187:
1185:
1182:
1180:
1177:
1175:
1172:
1170:
1169:False balance
1167:
1165:
1162:
1160:
1157:
1155:
1152:
1150:
1147:
1146:
1144:
1140:
1136:
1129:
1124:
1122:
1117:
1115:
1110:
1109:
1106:
1100:
1097:
1095:
1092:
1090:
1087:
1086:
1082:
1066:
1062:
1055:
1052:
1040:
1033:
1030:
1017:
1016:
1011:
1005:
1002:
989:
982:
979:
966:
962:
958:
952:
949:
936:
932:
928:
921:
918:
906:
899:
897:
893:
881:
874:
871:
859:
852:
849:
836:
835:
830:
824:
821:
808:
804:
803:
802:SecurityFocus
798:
791:
788:
775:
771:
764:
761:
748:
744:
740:
734:
732:
728:
716:
712:
706:
704:
700:
688:
681:
679:
675:
663:
656:
654:
650:
638:
634:
628:
626:
622:
610:
606:
600:
597:
591:
587:
584:
582:
579:
577:
574:
573:
569:
567:
564:
560:
556:
555:Melissa virus
552:
547:
544:
540:
536:
532:
528:
524:
520:
516:
512:
508:
503:
501:
497:
496:
491:
486:
484:
476:
474:
472:
468:
464:
460:
454:
446:
439:
435:
431:
428:
425:
422:
419:
416:
415:
411:
406:
403:
400:
397:
395:Olympic Torch
394:
393:
389:
385:
382:
379:
376:
373:
369:
368:
363:
360:
357:
354:
351:
350:
345:
342:
339:
336:
334:
331:
330:
325:
322:
320:United States
319:
316:
313:
312:
307:
304:
301:
298:
296:
293:
292:
288:
285:
282:
279:
277:
274:
273:
268:
265:
263:
260:
257:
256:
252:
248:
244:
240:
236:
232:
228:
224:
223:
218:
215:
212:
209:
207:
204:
203:
199:
195:
191:
188:
185:
182:
180:
177:
176:
172:
169:
166:
163:
160:
159:
150:
141:
137:
134:This list is
132:
125:
124:
118:
115:
111:
108:
104:
102:
97:
93:
91:
87:
81:
79:
75:
73:
69:
68:computer worm
64:
62:
58:
52:
45:
43:
41:
37:
34:
30:
18:
2130:Virus hoaxes
2117:
2092:Media ethics
2012:Door-to-door
2007:Cold calling
1984:Weasel words
1891:Fifth column
1785:Push polling
1735:Astroturfing
1697:Pseudo-event
1677:Infotainment
1652:Broadcasting
1575:
1571:Urban legend
1494:April Fools'
1367:Testimonials
1337:Infomercials
1164:Dumbing down
1069:. Retrieved
1065:the original
1054:
1032:
1020:. Retrieved
1013:
1004:
992:. Retrieved
981:
969:. Retrieved
965:the original
951:
939:. Retrieved
935:the original
931:Symantec.com
930:
920:
908:. Retrieved
883:. Retrieved
873:
861:. Retrieved
851:
839:. Retrieved
832:
823:
811:. Retrieved
807:the original
800:
790:
778:. Retrieved
774:the original
763:
751:. Retrieved
747:the original
718:. Retrieved
690:. Retrieved
665:. Retrieved
640:. Retrieved
636:
612:. Retrieved
608:
605:"Virus hoax"
599:
548:
506:
504:
493:
487:
480:
456:
323:Jim Flanagan
280:BUDSAVER.EXE
220:
173:Description
144:
112:
109:
106:
103:recommends:
99:
95:
88:
85:
76:
65:
53:
49:
40:chain e-mail
28:
26:
1964:Sound bites
1944:Doublespeak
1795:Wedge issue
1755:Dog whistle
1730:Advertising
1556:Lying press
1541:Gaslighting
1319:Advertising
1294:Occupations
1184:Obfuscation
1174:Half-truths
813:13 November
720:30 November
711:McAfee, Inc
533:Virus, the
483:gullibility
418:SULFNBK.EXE
333:Jdbgmgr.exe
247:Windows 3.0
237:during the
227:cyberweapon
216:John Gantz
147:August 2008
61:SULFNBK.EXE
2124:Categories
2065:Media bias
1921:Subversion
1886:False flag
1863:Techniques
1805:Propaganda
1765:Lawn signs
1745:Canvassing
1639:News media
1395:Censorship
1327:Billboards
1279:Hacktivism
1269:Grassroots
1194:Persuasion
1042:Retrieved
841:17 January
834:snopes.com
642:1 December
614:1 December
592:References
438:Windows Me
434:Windows 98
179:Antichrist
164:Alias(es)
136:incomplete
119:Comparison
2027:Promotion
1906:Political
1813:Bandwagon
1740:Attack ad
1619:Publicity
1591:Marketing
1504:Fake news
1466:Religious
1461:Political
1441:Euphemism
1436:Cover-ups
1431:Corporate
1299:Petitions
1189:Orwellian
1159:Deception
563:Slackware
523:Norwegian
388:Christmas
222:InfoWorld
194:Microsoft
1974:Transfer
1916:Sedition
1780:Negative
1692:Newspeak
1682:Managing
1624:Research
1599:Branding
1551:Literary
1516:Fakelore
1509:websites
1499:Deepfake
1456:Internet
1347:Modeling
1304:Protests
1284:Internet
1217:Advocacy
1209:Activism
1071:17 April
1044:8 August
1022:8 August
971:8 August
941:8 August
910:8 August
885:8 August
863:8 August
780:8 August
741:(2009).
692:8 August
667:8 August
570:See also
539:Mac OS 9
527:Albanian
477:Parodies
337:(bear.a)
239:Gulf War
101:F-Secure
59:and the
2053:Related
2032:Spaving
2017:Pricing
1959:Slogans
1901:Lawfare
1838:Framing
1818:Big lie
1609:Product
1604:Loyalty
1536:Forgery
1481:Hoaxing
1362:Slogans
1342:Mobiles
1234:Boycott
1142:Context
753:14 June
576:Malware
559:Windows
551:Tuxissa
529:Virus,
471:malware
463:Windows
429:Unknown
426:Unknown
420:Warning
404:Unknown
401:Unknown
383:Unknown
380:Unknown
372:Elfbowl
343:Unknown
340:Unknown
305:Unknown
302:Unknown
286:Unknown
283:Unknown
266:Unknown
243:windows
219:A 1991
170:Author
167:Origin
1657:Circus
1566:Racial
531:Newfie
519:Syrian
299:(none)
198:zeroth
183:(none)
92:says:
90:McAfee
82:Action
63:hoax.
36:threat
2145:Email
1999:Sales
1702:Scrum
1662:Cycle
1576:Virus
1446:Films
1411:Books
1352:Radio
1332:False
1309:Youth
1289:Media
1222:group
1179:Media
994:1 May
543:Amish
515:Irish
511:Amish
459:India
206:AF/91
161:Name
1969:Spin
1546:List
1471:Self
1149:Bias
1073:2009
1046:2011
1024:2011
996:2012
973:2011
943:2011
912:2011
887:2011
865:2011
843:2014
815:2015
782:2011
755:2012
722:2018
694:2011
669:2011
644:2020
616:2020
549:The
535:Unix
436:and
423:none
235:Iraq
1357:Sex
410:CNN
142:.
2126::
1372:TV
1012:.
929:.
895:^
831:.
799:.
730:^
702:^
677:^
652:^
635:.
624:^
607:.
502:.
390:.
374:")
27:A
1127:e
1120:t
1113:v
1075:.
1048:.
1026:.
998:.
975:.
945:.
914:.
889:.
867:.
845:.
817:.
784:.
757:.
724:.
696:.
671:.
646:.
618:.
149:)
145:(
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.