1090:– uses partial hash inversions to prove that work was done, to unlock a mining reward in Bitcoin, and as a good-will token to send an e-mail in Hashcash. The sender is required to find a message whose hash value begins with a number of zero bits. The average work that the sender needs to perform in order to find a valid message is exponential in the number of zero bits required in the hash value, while the recipient can verify the validity of the message by executing a single hash function. For instance, in Hashcash, a sender is asked to generate a header whose 160-bit SHA-1 hash value has the first 20 bits as zeros. The sender will, on average, have to try
133:
1319:
6199:
5235:
4163:
36:
5259:
6209:
5247:
1299:. General-purpose ciphers tend to have different design goals. In particular, AES has key and block sizes that make it nontrivial to use to generate long hash values; AES encryption becomes less efficient when the key changes each block; and related-key attacks make it potentially less secure for use in a hash function than for encryption.
1331:. The compression function can either be specially designed for hashing or be built from a block cipher. A hash function built with the Merkle–Damgård construction is as resistant to collisions as is its compression function; any collision for the full hash function can be traced back to a collision in the compression function.
1695:, and Christian Winnerlein with the goal of replacing the widely used but broken MD5 and SHA-1 algorithms. When run on 64-bit x64 and ARM architectures, BLAKE2b is faster than SHA-3, SHA-2, SHA-1, and MD5. Although BLAKE and BLAKE2 have not been standardized as SHA-3 has, BLAKE2 has been used in many protocols including the
1800:
Passwords may still be retrieved by an attacker from the hashes, because most people choose passwords in predictable ways. Lists of common passwords are widely circulated and many passwords are short enough that even all possible combinations may be tested if calculation of the hash does not take too
1591:
project. The original specification – now commonly called SHA-0 – of the algorithm was published in 1993 under the title Secure Hash
Standard, FIPS PUB 180, by U.S. government standards agency NIST (National Institute of Standards and Technology). It was withdrawn by the NSA shortly after publication
712:
Collision resistance implies second pre-image resistance but does not imply pre-image resistance. The weaker assumption is always preferred in theoretical cryptography, but in practice, a hash-function that is only second pre-image resistant is considered insecure and is therefore not recommended for
1210:
in the United States which required the storage of enormous numbers of documents for long periods and retrieved only rarely. Ever-increasing performance of traditional file systems and new software systems have eroded the value of legacy CAS systems, which have become increasingly rare after roughly
792:
In practice, collision resistance is insufficient for many practical uses. In addition to collision resistance, it should be impossible for an adversary to find two messages with substantially similar digests; or to infer any useful information about the data, given only its digest. In particular, a
1796:
Rather than store plain user passwords, controlled-access systems frequently store the hash of each user's password in a file or database. When someone requests access, the password they submit is hashed and compared with the stored value. If the database is stolen (an all-too-frequent occurrence),
1739:
against a weakened variant may undermine the experts' confidence. For instance, in August 2004 collisions were found in several then-popular hash functions, including MD5. These weaknesses called into question the security of stronger algorithms derived from the weak hash functions – in particular,
1669:
SHA-3 (Secure Hash
Algorithm 3) was released by NIST on August 5, 2015. SHA-3 is a subset of the broader cryptographic primitive family Keccak. The Keccak algorithm is the work of Guido Bertoni, Joan Daemen, Michael Peeters, and Gilles Van Assche. Keccak is based on a sponge construction, which can
1647:
SHA-2 basically consists of two hash algorithms: SHA-256 and SHA-512. SHA-224 is a variant of SHA-256 with different starting values and truncated output. SHA-384 and the lesser-known SHA-512/224 and SHA-512/256 are all variants of SHA-512. SHA-512 is more secure than SHA-256 and is commonly faster
1643:
SHA-2 (Secure Hash
Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA), first published in 2001. They are built using the Merkle–Damgård structure, from a one-way compression function itself built using the Davies–Meyer structure from a
1203:
stores these addresses and a pointer to the physical storage of the content. Because an attempt to store the same file will generate the same key, CAS systems ensure that the files within them are unique, and because changing the file will result in a new key, CAS systems provide assurance that the
1163:
However, compared with standard hash functions, cryptographic hash functions tend to be much more expensive computationally. For this reason, they tend to be used in contexts where it is necessary for users to protect themselves against the possibility of forgery (the creation of data with the same
829:
In cryptographic practice, "difficult" generally means "almost certainly beyond the reach of any adversary who must be prevented from breaking the system for as long as the security of the system is deemed important". The meaning of the term is therefore somewhat dependent on the application since
720:
cannot replace or modify the input data without changing its digest. Thus, if two strings have the same digest, one can be very confident that they are identical. Second pre-image resistance prevents an attacker from crafting a document with the same hash as a document the attacker cannot control.
1755:
In
February 2005, an attack on SHA-1 was reported that would find collision in about 2 hashing operations, rather than the 2 expected for a 160-bit hash function. In August 2005, another attack on SHA-1 was reported that would find collisions in 2 operations. Other theoretical weaknesses of SHA-1
1727:
There is a long list of cryptographic hash functions but many have been found to be vulnerable and should not be used. For instance, NIST selected 51 hash functions as candidates for round 1 of the SHA-3 hash competition, of which 10 were considered broken and 16 showed significant weaknesses and
1018:
can result in a massive security breach if the password file is compromised. One way to reduce this danger is to only store the hash digest of each password. To authenticate a user, the password presented by the user is hashed and compared with the stored hash. A password reset method is required
999:
schemes require a cryptographic hash to be calculated over the message. This allows the signature calculation to be performed on the relatively small, statically sized hash digest. The message is considered authentic if the signature verification succeeds given the signature and recalculated hash
899:
and claims that she has solved it. Bob would like to try it himself, but would yet like to be sure that Alice is not bluffing. Therefore, Alice writes down her solution, computes its hash, and tells Bob the hash value (whilst keeping the solution secret). Then, when Bob comes up with the solution
1714:
BLAKE3, an improved version of BLAKE2, was announced on
January 9, 2020. It was created by Jack O'Connor, Jean-Philippe Aumasson, Samuel Neves, and Zooko Wilcox-O'Hearn. BLAKE3 is a single algorithm, in contrast to BLAKE and BLAKE2, which are algorithm families with multiple variants. The BLAKE3
1613:
RIPEMD (RACE Integrity
Primitives Evaluation Message Digest) is a family of cryptographic hash functions developed in Leuven, Belgium, by Hans Dobbertin, Antoon Bosselaers, and Bart Preneel at the COSIC research group at the Katholieke Universiteit Leuven, and first published in 1996. RIPEMD was
1081:
and other service abuses such as spam on a network by requiring some work from the service requester, usually meaning processing time by a computer. A key feature of these schemes is their asymmetry: the work must be moderately hard (but feasible) on the requester side but easy to check for the
1294:
needs to implement both encryption and hashing with minimal code size or hardware area. However, that approach can have costs in efficiency and security. The ciphers in hash functions are built for hashing: they use large keys and blocks, can efficiently change keys every block, and have been
1572:
in 1991 to replace an earlier hash function, MD4, and was specified in 1992 as RFC 1321. Collisions against MD5 can be calculated within seconds, which makes the algorithm unsuitable for most use cases where a cryptographic hash is required. MD5 produces a digest of 128 bits (16 bytes).
830:
the effort that a malicious agent may put into the task is usually proportional to their expected gain. However, since the needed effort usually multiplies with the digest length, even a thousand-fold advantage in processing power can be neutralized by adding a dozen bits to the latter.
1022:
However, use of standard cryptographic hash functions, such as the SHA series, is no longer considered safe for password storage. These algorithms are designed to be computed quickly, so if the hashed values are compromised, it is possible to try guessed passwords at high rates. Common
1628:
Whirlpool is a cryptographic hash function designed by
Vincent Rijmen and Paulo S. L. M. Barreto, who first described it in 2000. Whirlpool is based on a substantially modified version of the Advanced Encryption Standard (AES). Whirlpool produces a hash digest of 512 bits (64 bytes).
1743:
On August 12, 2004, Joux, Carribault, Lemuel, and Jalby announced a collision for the full SHA-0 algorithm. Joux et al. accomplished this using a generalization of the
Chabaud and Joux attack. They found that the collision had complexity 2 and took about 80,000 CPU hours on a
1782:. This makes the MD5, SHA-1, RIPEMD-160, Whirlpool, and the SHA-256 / SHA-512 hash algorithms all vulnerable to this specific attack. SHA-3, BLAKE2, BLAKE3, and the truncated SHA-2 variants are not vulnerable to this type of attack.
1614:
based upon the design principles used in MD4 and is similar in performance to the more popular SHA-1. RIPEMD-160 has, however, not been broken. As the name implies, RIPEMD-160 produces a hash digest of 160 bits (20 bytes).
1184:(CAS), also referred to as content-addressed storage or fixed-content storage, is a way to store information so it can be retrieved based on its content, not its name or location. It has been used for high-speed storage and
1326:
A hash function must be able to process an arbitrary-length message into a fixed-length output. This can be achieved by breaking the input up into a series of equally sized blocks, and operating on them in sequence using a
805:
function, which can be rigorously proven to be collision-resistant assuming that certain problems on ideal lattices are computationally difficult, but, as a linear function, does not satisfy these additional properties.
1532:-collisions: if it is feasible for an attacker to find two messages with the same MD5 hash, then they can find as many additional messages with that same MD5 hash as they desire, with no greater difficulty. Among those
1483:
to generate internal tables, which are then used in a keystream generator more or less unrelated to the hash algorithm. SEAL is not guaranteed to be as strong (or weak) as SHA-1. Similarly, the key expansion of the
900:
himself a few days later, Alice can prove that she had the solution earlier by revealing it and having Bob hash it and check that it matches the hash value given to him before. (This is an example of a simple
1058:
value that can be stored with the password hash. The salt is hashed with the password, altering the password hash mapping for each password, thereby making it infeasible for an adversary to store tables of
1756:
have been known, and in
February 2017 Google announced a collision in SHA-1. Security researchers recommend that new applications can avoid these problems by using later members of the SHA family, such as
1699:
password hash, for the high efficiency that it offers on modern CPUs. As BLAKE was a candidate for SHA-3, BLAKE and BLAKE2 both offer the same output sizes as SHA-3 – including a configurable output size.
2589:
837:
or other short messages, it can be feasible to invert a hash by trying all possible messages in the set. Because cryptographic hash functions are typically designed to be computed quickly, special
1592:
and was superseded by the revised version, published in 1995 in FIPS PUB 180-1 and commonly designated SHA-1. Collisions against the full SHA-1 algorithm can be produced using the
1538:
messages with the same MD5 hash, there is likely to be a collision in SHA-1. The additional work needed to find the SHA-1 collision (beyond the exponential birthday search) requires only
1655:
The output size in bits is given by the extension to the "SHA" name, so SHA-224 has an output size of 224 bits (28 bytes); SHA-256, 32 bytes; SHA-384, 48 bytes; and SHA-512, 64 bytes.
4143:
3973:
1468:
1550:
There are many cryptographic hash algorithms; this section lists a few algorithms that are referenced relatively often. A more extensive list can be found on the page containing a
2482:
1503:
outputs from multiple hash functions provide collision resistance as good as the strongest of the algorithms included in the concatenated result. For example, older versions of
1358:
A straightforward application of the Merkle–Damgård construction, where the size of hash output is equal to the internal state size (between each compression step), results in a
1211:
2018. However, the principles of content addressability continue to be of great interest to computer scientists, and form the core of numerous emerging technologies, such as
432:
resistance strength, with the same expectations, refers to a similar problem of finding a second message that matches the given hash value when one message is already known;
2558:
927:. Comparing message digests (hash digests over the message) calculated before, and after, transmission can determine whether any changes have been made to the message or
5297:
2090:
1715:
compression function is closely based on that of BLAKE2s, with the biggest difference being that the number of rounds is reduced from 10 to 7. Internally, BLAKE3 is a
817:, are designed to meet much weaker requirements and are generally unsuitable as cryptographic hash functions. For example, a CRC was used for message integrity in the
329:
419:
1817:
469:
3826:
392:
368:
295:
267:
2961:"Cryptographic Hash-Function Basics: Definitions, Implications, and Separations for Preimage Resistance, Second-Preimage Resistance, and Collision Resistance"
3746:
53:
1137:-variant hash is combined with the file size, providing sufficient information for locating file sources, downloading the file, and verifying its contents.
904:; in actual practice, Alice and Bob will often be computer programs, and the secret would be something less easily spoofed than a claimed puzzle solution.)
3134:
2581:
864:
1670:
also be used to build other cryptographic primitives such as a stream cipher. SHA-3 provides the same output sizes as SHA-2: 224, 256, 384, and 512 bits.
4203:
3163:
1863:
1551:
1975:
1122:
of various types of content (file content, directory trees, ancestry information, etc.) to uniquely identify them. Hashes are used to identify files on
1000:
digest over the message. So the message integrity property of the cryptographic hash is used to create secure and efficient digital signature schemes.
1366:, multicollisions, long message attacks, generate-and-paste attacks, and also cannot be parallelized. As a result, modern hash functions are built on
2048:
5195:
1923:
1673:
Configurable output sizes can also be obtained using the SHAKE-128 and SHAKE-256 functions. Here the -128 and -256 extensions to the name imply the
945:
hash digests are sometimes published on websites or forums to allow verification of integrity for downloaded files, including files retrieved using
1370:
constructions that have a larger internal state size – which range from tweaks of the Merkle–Damgård construction to new constructions such as the
1599:
Documents may refer to SHA-1 as just "SHA", even though this may conflict with the other Secure Hash
Algorithms such as SHA-0, SHA-2, and SHA-3.
2450:
2276:, p. 99: the concatenation of hash functions as suggested in the TLS... is guaranteed to be as secure as the candidate that remains secure.
5816:
2663:
Harnik, Danny; Kilian, Joe; Naor, Moni; Reingold, Omer; Rosen, Alon (2005). "On Robust Combiners for Oblivious Transfer and Other Primitives".
2424:
1263:, are built from block-cipher-like components designed for the purpose, with feedback to ensure that the resulting function is not invertible.
1195:
CAS systems work by passing the content of the file through a cryptographic hash function to generate a unique key, the "content address". The
6238:
5175:
3032:
3011:
2941:
2902:
2865:
2836:
2796:
2755:
2715:
2680:
2402:
1430:
or other construction. That cipher can also be used in a conventional mode of operation, without the same security guarantees; for example,
5441:
5290:
1418:
constructions using hash functions can be provably secure if the underlying hash function is secure. Also, many hash functions (including
724:
A function meeting these criteria may still have undesirable properties. Currently, popular cryptographic hash functions are vulnerable to
100:
2980:
2644:
2305:
1043:– commonly use repeated invocations of a cryptographic hash to increase the time (and in some cases computer memory) required to perform
871:
algorithm can sometimes still be fast enough to make a feasible attack. Conversely, a polynomial-time algorithm (e.g., one that requires
5572:
2474:
2350:
1515:
sums. This ensures that a method to find collisions in one of the hash functions does not defeat data protected by both hash functions.
853:
72:
3690:
2619:
1775:
1519:
1339:
1313:
5991:
3523:
704:. It requires a hash value at least twice as long as that required for pre-image resistance; otherwise, collisions may be found by a
6233:
6046:
5185:
3819:
2974:
564:. In theoretical cryptography, the security level of a cryptographic hash function has been defined using the following properties:
220:
119:
79:
3066:
1691:
BLAKE2, an improved version of BLAKE, was announced on December 21, 2012. It was created by Jean-Philippe Aumasson, Samuel Neves,
1522:
hash functions, the concatenated function is as collision-resistant as its strongest component, but not more collision-resistant.
6212:
2698:
Hoch, Jonathan J.; Shamir, Adi (2008). "On the Strength of the Concatenated Hash Combiner when All the Hash Functions Are Weak".
2238:
1188:
of fixed content, such as documents stored for compliance with government regulations. Content-addressable storage is similar to
2883:
Mendel, Florian; Rechberger, Christian; Schläffer, Martin (2009). "MD5 is Weaker Than Weak: Attacks on Concatenated Combiners".
511:
to detect accidental data corruption. Indeed, in information-security contexts, cryptographic hash values are sometimes called (
6202:
5283:
4586:
3127:
2554:
2301:
1933:
1244:
849:
530:
3088:
1063:
hash values to which the password hash digest can be compared or to test a large number of purloined hash values in parallel.
4196:
4022:
3731:
3216:
3168:
2082:
1729:
1379:
1264:
537:
and to detect accidental errors; their constructions frequently provide no resistance to a deliberate attack. For example, a
86:
57:
1448:(PRNGs) can be built using hash functions. This is done by combining a (secret) random seed with a counter and hashing it.
2846:
Lyubashevsky, Vadim; Micciancio, Daniele; Peikert, Chris; Rosen, Alon (2008). "SWIFFT: A Modest Proposal for FFT Hashing".
2264:, p. 145:Concatenating ... is often used by implementors to "hedge bets" on hash functions. A combiner of the form MD5
5165:
4591:
3518:
1445:
5537:
5512:
4637:
4296:
3812:
3736:
1427:
1328:
1287:
1237:
1160:. Being hash functions of a particular kind, cryptographic hash functions lend themselves well to this application too.
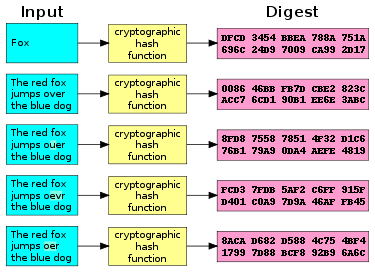
140:) at work. A small change in the input (in the word "over") drastically changes the output (digest). This is called the
68:
6118:
2740:. Lecture Notes in Computer Science. Vol. 3152. Berlin, Heidelberg: Springer Berlin Heidelberg. pp. 306–316.
2531:
1467:, and stream ciphers can also be built from fixed-length digest hash functions. Often this is done by first building a
5522:
4138:
3505:
3147:
2504:
1903:
1400:
1181:
1174:
488:
171:
801:
in proofs of security) while still being deterministic and efficiently computable. This rules out functions like the
1385:
Meanwhile, truncating the output of a longer hash, such as used in SHA-512/256, also defeats many of these attacks.
5079:
4711:
4017:
3120:
1189:
2369:
46:
5916:
5552:
5251:
5239:
5205:
5180:
5160:
4835:
4825:
4632:
4189:
4133:
3762:
3401:
3058:
1848:. For KDFs that perform multiple hashes to slow execution, NIST recommends an iteration count of 10,000 or more.
1623:
1212:
554:
1778:. All cryptographic hashes that directly use the full output of a Merkle–Damgård construction are vulnerable to
6152:
6056:
6026:
5721:
5499:
5398:
5263:
5210:
5130:
4850:
4123:
4113:
3968:
3741:
3577:
3276:
3271:
1768:
1504:
1078:
1024:
818:
717:
538:
527:, even though all these terms stand for more general functions with rather different properties and purposes.
2810:
2196:
2152:
1983:
6147:
6016:
5886:
5602:
4888:
4764:
4744:
4359:
4118:
4108:
3911:
3871:
3864:
3854:
3849:
3664:
3484:
1893:
1821:
1779:
1740:
SHA-1 (a strengthened version of SHA-0), RIPEMD-128, and RIPEMD-160 (both strengthened versions of RIPEMD).
1692:
1588:
1394:
1363:
966:
838:
814:
725:
542:
504:
2044:
1207:
961:. Using a cryptographic hash and a chain of trust detects malicious changes to the file. Non-cryptographic
6174:
6167:
6006:
5781:
5145:
4991:
4878:
4716:
4701:
4686:
4612:
4553:
4512:
4231:
3859:
3772:
3158:
2522:
Sotirov, A; Stevens, M; Appelbaum, J; Lenstra, A; Molnar, D; Osvik, D A; de Weger, B (December 30, 2008).
1335:
1103:
1019:
when password hashing is performed; original passwords cannot be recalculated from the stored hash value.
821:
encryption standard, but an attack was readily discovered, which exploited the linearity of the checksum.
649:
167:
151:
1728:
therefore did not make it to the next round; more information can be found on the main article about the
1397:. For these other primitives to be cryptographically secure, care must be taken to build them correctly.
93:
6179:
5200:
5155:
4815:
4785:
4721:
4533:
4507:
4498:
4251:
4246:
4236:
4166:
4012:
3958:
3787:
3437:
3391:
3281:
3239:
3224:
3206:
1868:
1596:
and the hash function should be considered broken. SHA-1 produces a hash digest of 160 bits (20 bytes).
1452:
1272:
1220:
1200:
1185:
213:
4749:
1995:
Much more than encryption algorithms, one-way hash functions are the workhorses of modern cryptography.
5387:
4820:
4739:
4706:
4691:
4617:
4128:
4052:
3457:
3361:
3311:
3286:
2442:
1736:
1111:
962:
957:
as long as the hashes are posted on a trusted site – usually the originating site – authenticated by
655:
480:
2421:
5971:
5459:
5377:
5367:
5362:
5306:
5001:
4754:
4681:
3891:
3782:
3659:
3608:
3547:
3366:
3326:
3306:
1805:
1371:
1268:
1115:
1055:
721:
Collision resistance prevents an attacker from creating two distinct documents with the same hash.
5961:
5766:
5756:
4805:
4759:
4305:
4276:
4256:
3997:
3981:
3928:
3716:
3700:
3649:
3234:
1813:
1375:
1296:
1044:
842:
1206:
CAS became a significant market during the 2000s, especially after the introduction of the 2002
785:. This property can be used to break naive authentication schemes based on hash functions. The
5729:
5610:
5357:
5342:
5062:
4538:
4266:
4261:
4057:
4047:
3918:
3593:
3038:
3028:
3007:
2970:
2964:
2960:
2947:
2937:
2908:
2898:
2871:
2861:
2832:
2826:
2802:
2792:
2761:
2751:
2721:
2711:
2686:
2676:
2640:
2398:
2313:
1791:
1761:
1674:
1138:
996:
990:
924:
918:
901:
484:
347:
246:
132:
2999:
2736:(2004). "Multicollisions in Iterated Hash Functions. Application to Cascaded Constructions".
2612:"Use an 8-char Windows NTLM password? Don't. Every single one can be cracked in under 2.5hrs"
2385:
Alshaikhli, Imad Fakhri; AlAhmad, Mohammad Abdulateef (2015), "Cryptographic Hash Function",
2347:
1014:
Password verification commonly relies on cryptographic hashes. Storing all user passwords as
6243:
5701:
5220:
5170:
5150:
5006:
4986:
4956:
4676:
4671:
4652:
4409:
3992:
3680:
3634:
3396:
2929:
2888:
2851:
2782:
2741:
2703:
2668:
2611:
2390:
2346:
Andrew Regenscheid, Ray Perlner, Shu-Jen Chang, John Kelsey, Mridul Nandi, Souradyuti Paul,
2122:
1858:
1009:
978:
868:
595:
472:
304:
206:
141:
397:
6021:
5951:
5881:
5810:
5776:
5761:
5673:
5640:
5615:
5190:
5140:
4951:
3695:
3644:
3639:
3427:
2475:"Google Just 'Shattered' An Old Crypto Algorithm – Here's Why That's Big For Web Security"
2428:
2373:
2354:
2231:
1841:
1539:
1291:
1280:
974:
856:
794:
705:
599:
3092:
1414:
can be used to build hash functions, hash functions can be used to build block ciphers.
1027:
can try billions of possible passwords each second. Password hash functions that perform
446:
331:(as for any good hash), so the hash value can be used as a representative of the message;
2530:. Department of Mathematics and Computer Science of Eindhoven University of Technology.
1338:; this is crucial to the security of this construction. This construction is called the
1318:
541:
on hash tables is possible if the collisions are easy to find, as in the case of linear
5711:
5507:
5016:
4946:
4896:
4800:
4572:
4543:
4315:
4310:
4281:
4212:
4067:
3987:
3948:
3896:
3881:
3685:
3413:
2417:
1971:
1812:. But searches on the order of 100 billion tests per second are possible with high-end
1216:
1107:
1083:
1060:
1028:
954:
950:
697:
492:
377:
353:
280:
252:
242:
2348:
Status Report on the First Round of the SHA-3 Cryptographic Hash Algorithm Competition
6227:
6157:
5956:
5630:
5069:
4330:
4320:
4148:
4103:
4062:
4042:
3938:
3901:
3876:
3777:
3654:
3356:
2921:
1918:
1913:
1809:
1745:
1569:
1500:
1476:
1464:
1460:
1439:
1435:
1153:
1072:
928:
896:
892:
798:
782:
561:
496:
2394:
5896:
5688:
5451:
5314:
4467:
4354:
4098:
3943:
3933:
3923:
3886:
3835:
3075:(companion web site contains online cryptography course that covers hash functions)
2733:
2585:
2119:
SP 800-63B-3 – Digital Identity Guidelines, Authentication and Lifecycle Management
1523:
1415:
1411:
1233:
1123:
1102:
A message digest can also serve as a means of reliably identifying a file; several
946:
867:
but do not usually have a strong connection to practical security. For example, an
270:
3079:
1077:
A proof-of-work system (or protocol, or function) is an economic measure to deter
3022:
2998:
Menezes, Alfred J.; van Oorschot, Paul C.; Vanstone, Scott A. (7 December 2018).
2969:. Vol. 3017. Lecture Notes in Computer Science: Springer. pp. 371–388.
2933:
2746:
2707:
1824:(KDFs) that have been created to slow brute force searches. Slow hashes include
1290:
can be used in place of these custom block ciphers; that might be useful when an
5986:
5906:
5851:
5771:
5215:
5104:
4976:
4840:
4077:
3767:
3613:
3542:
3538:
3447:
2893:
2856:
2387:
Handbook of Research on Threat Detection and Countermeasures in Network Security
1878:
1808:
prevents some attacks, such as building files of precomputing hash values, e.g.
1716:
1196:
1146:
1126:
35:
1403:(MACs) (also called keyed hash functions) are often built from hash functions.
6092:
6036:
5966:
5841:
5836:
5786:
5751:
5744:
5706:
5696:
5635:
5421:
5332:
5322:
5135:
5026:
4971:
4858:
4810:
4731:
4433:
4428:
4226:
4037:
4007:
4002:
3963:
3042:
1888:
1608:
1157:
534:
500:
394:
bits, unless the space of possible input values is significantly smaller than
298:
17:
2951:
2912:
2875:
2806:
2765:
2725:
2690:
5933:
5923:
5911:
5901:
5866:
5831:
5826:
5739:
5645:
5547:
5479:
5416:
5327:
4966:
4868:
4795:
4696:
4548:
4027:
3442:
3099:
3070:
2523:
2126:
1845:
1749:
1472:
1142:
1130:
1015:
891:
An illustration of the potential use of a cryptographic hash is as follows:
841:
that require greater computing resources have been developed that make such
3229:
2508:
2230:
Dobraunig, Christoph; Eichlseder, Maria; Mendel, Florian (February 2015).
1752:
processors – equivalent to 13 days of full-time use of the supercomputer.
852:"difficult" has a specific mathematical meaning, such as "not solvable in
6108:
6082:
6011:
5871:
5861:
5846:
5791:
5668:
5620:
5587:
5562:
5542:
5527:
5372:
5337:
5275:
4961:
4941:
4921:
4911:
4906:
4830:
4790:
4769:
4627:
4607:
4601:
4581:
4558:
4528:
4458:
4448:
4443:
4403:
4394:
4379:
4374:
4369:
4271:
4072:
4032:
3721:
3618:
3603:
3598:
3588:
3552:
3472:
3386:
3266:
1873:
1087:
834:
508:
435:
finding any pair of different messages that yield the same hash value (a
2787:
6131:
6126:
6077:
5891:
5625:
5592:
5582:
5557:
5517:
5489:
5469:
5411:
5352:
5346:
5109:
5074:
5031:
4926:
4901:
4873:
4642:
4384:
4349:
3557:
3513:
3291:
3100:
Open source python based application with GUI used to verify downloads.
2928:. Lecture Notes in Computer Science. Vol. 6498. pp. 144–162.
2887:. Lecture Notes in Computer Science. Vol. 5912. pp. 144–161.
2781:. Lecture Notes in Computer Science. Vol. 3494. pp. 474–490.
2702:. Lecture Notes in Computer Science. Vol. 5126. pp. 616–630.
2672:
2366:
1767:
A successful, practical attack broke MD5 (used within certificates for
1489:
1247:
usually used for encryption. Many well-known hash functions, including
1119:
2775:"Second Preimages on n-Bit Hash Functions for Much Less than 2 n Work"
2667:. Lecture Notes in Computer Science. Vol. 3494. pp. 96–113.
2582:"25-GPU cluster cracks every standard Windows password in <6 hours"
1267:
finalists included functions with block-cipher-like components (e.g.,
249:
of an arbitrary binary string to a binary string with a fixed size of
6184:
6031:
5941:
5577:
5532:
5484:
5436:
5084:
5011:
4931:
4916:
4863:
4662:
4596:
4488:
4438:
4419:
3953:
3726:
3467:
3462:
3432:
3422:
3381:
3376:
3371:
3351:
3346:
3321:
3316:
3301:
3261:
3063:
Understanding Cryptography, A Textbook for Students and Practitioners
2850:. Lecture Notes in Computer Science. Vol. 5086. pp. 54–72.
1908:
1898:
1837:
1833:
1829:
1825:
1709:
1696:
1686:
1649:
1485:
1456:
1431:
1276:
1040:
1036:
1032:
802:
1164:
digest as the expected data) by potentially malicious participants.
1054:
A password hash also requires the use of a large random, non-secret
4181:
3024:
Serious Cryptography: A Practical Introduction to Modern Encryption
2774:
2186:
2144:
1816:, making direct attacks possible even with salt. The United States
6087:
6061:
6001:
5976:
5734:
5678:
5663:
5567:
5474:
5431:
5426:
5406:
5114:
5052:
5036:
4996:
4981:
4936:
4647:
4472:
4340:
3452:
3341:
3296:
3244:
3201:
3196:
3190:
2068:
1928:
1757:
1664:
1638:
1593:
1582:
1512:
1480:
1423:
1419:
1343:
1317:
1260:
1256:
1141:
are another example. Such file hashes are often the top hash of a
958:
942:
938:
833:
For messages selected from a limited set of messages, for example
810:
560:
A cryptographic hash function must be able to withstand all known
195:
191:
187:
183:
137:
131:
923:
An important application of secure hashes is the verification of
439:) is also infeasible: a cryptographic hash is expected to have a
5876:
5655:
4364:
4286:
3567:
3562:
3533:
3528:
3492:
1883:
1404:
786:
5279:
4185:
3808:
3116:
2966:
Fast Software Encryption: 11th International Workshop, FSE 2004
2524:"MD5 considered harmful today: Creating a rogue CA certificate"
1362:
hash design. This design causes many inherent flaws, including
5946:
5856:
5464:
5057:
5021:
4622:
3336:
3331:
3184:
1563:
1508:
1347:
1252:
1248:
1134:
934:
557:
of any length as input and produce a fixed-length hash value.
507:, to detect duplicate data or uniquely identify files, and as
29:
2367:
Collisions for Hash Functions MD4, MD5, HAVAL-128, and RIPEMD
1797:
the thief will only have the hash values, not the passwords.
1719:, and it supports higher degrees of parallelism than BLAKE2.
1505:
Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
3089:"Series of mini-lectures about cryptographic hash functions"
2232:
Security Evaluation of SHA-224, SHA-512/224, and SHA-512/256
1958:
334:
finding an input string that matches a given hash value (a
2261:
1820:
recommends storing passwords using special hashes called
1463:, output an arbitrarily long stream and can be used as a
1426:) are built by using a special-purpose block cipher in a
553:
Most cryptographic hash functions are designed to take a
2273:
1976:"Cryptanalysis of MD5 and SHA: Time for a New Standard"
1236:
to build a cryptographic hash function, specifically a
793:
hash function should behave as much as possible like a
3974:
Cryptographically secure pseudorandom number generator
2463:
Summarizes Wang et al. results and their implications.
1469:
cryptographically secure pseudorandom number generator
1334:
The last block processed should also be unambiguously
660:
It should be difficult to find two different messages
648:. Functions that lack this property are vulnerable to
598:. Functions that lack this property are vulnerable to
27:
Hash function that is suitable for use in cryptography
1677:
of the function rather than the output size in bits.
1587:
SHA-1 was developed as part of the U.S. Government's
449:
400:
380:
356:
307:
283:
255:
3104:
2922:"Speeding up the Wide-Pipe: Secure and Fast Hashing"
883:-digit keys) may be too slow for any practical use.
6140:
6117:
6101:
6070:
6045:
5985:
5932:
5809:
5720:
5687:
5654:
5601:
5498:
5450:
5397:
5386:
5313:
5123:
5097:
5045:
4887:
4849:
4778:
4730:
4661:
4571:
4521:
4497:
4481:
4457:
4418:
4393:
4339:
4329:
4295:
4219:
4086:
3842:
3755:
3709:
3673:
3627:
3576:
3504:
3481:
3410:
3254:
3215:
3177:
2284:
2282:
617:, it should be difficult to find a different input
177:
157:
150:
60:. Unsourced material may be challenged and removed.
2555:"The 15 biggest data breaches of the 21st century"
2365:XiaoyunWang, Dengguo Feng, Xuejia Lai, Hongbo Yu,
1342:. Most common classical hash functions, including
1047:on stored password hash digests. For details, see
463:
413:
386:
362:
323:
289:
269:bits) that has special properties desirable for a
261:
1735:Even if a hash function has never been broken, a
2188:A Framework for Iterative Hash Functions – HAIFA
2030:
1048:
422:
2145:"Design Principles for Iterated Hash Functions"
1082:service provider. One popular system – used in
2553:Swinhoe, Dan; Hill, Michael (April 17, 2020).
2172:
2045:"Flickr's API Signature Forgery Vulnerability"
1818:National Institute of Standards and Technology
1389:Use in building other cryptographic primitives
973:alterations of the file, since an intentional
340:assuming all input strings are equally likely.
5291:
4197:
3820:
3128:
2641:"Mind-blowing development in GPU performance"
2185:Biham, Eli; Dunkelman, Orr (24 August 2006).
2083:"Use MD5 hashes to verify software downloads"
1471:and then using its stream of random bytes as
1382:use a classical Merkle–Damgård construction.
913:Verifying the integrity of messages and files
577:, it should be difficult to find any message
214:
8:
865:provably secure cryptographic hash functions
700:. This property is sometimes referred to as
644:. This property is sometimes referred to as
136:A cryptographic hash function (specifically
3021:Aumasson, Jean-Philippe (6 November 2017).
2505:"Randomized Hashing and Digital Signatures"
2191:. Second NIST Cryptographic Hash Workshop.
2112:
2110:
2108:
2018:
1774:Many cryptographic hashes are based on the
301:) for a random input string ("message") is
5394:
5298:
5284:
5276:
5258:
5042:
4336:
4204:
4190:
4182:
3827:
3813:
3805:
3135:
3121:
3113:
3109:
3105:
2334:
1864:Comparison of cryptographic hash functions
1764:that do not require collision resistance.
1552:comparison of cryptographic hash functions
1393:Hash functions can be used to build other
1156:is to allow the fast look-up of data in a
789:construction works around these problems.
221:
207:
2892:
2855:
2786:
2745:
2217:
2138:
2136:
1959:Menezes, van Oorschot & Vanstone 2018
716:Informally, these properties mean that a
453:
448:
405:
399:
379:
370:bits of hash value is expected to have a
355:
312:
306:
282:
254:
120:Learn how and when to remove this message
2920:Nandi, Mridul; Paul, Souradyuti (2010).
2825:Katz, Jonathan; Lindell, Yehuda (2014).
2006:
1924:Security of cryptographic hash functions
1723:Attacks on cryptographic hash algorithms
1648:than SHA-256 on 64-bit machines such as
1275:) though the function finally selected,
1149:, which allows for additional benefits.
696:. Such a pair is called a cryptographic
2926:Progress in Cryptology - INDOCRYPT 2010
2885:Advances in Cryptology – ASIACRYPT 2009
2779:Advances in Cryptology – EUROCRYPT 2005
2665:Advances in Cryptology – EUROCRYPT 2005
1951:
1644:(classified) specialized block cipher.
594:. This concept is related to that of a
479:Cryptographic hash functions have many
2773:Kelsey, John; Schneier, Bruce (2005).
2561:from the original on November 24, 2020
1488:stream ciphers makes heavy use of the
1295:designed and vetted for resistance to
147:
5176:Decentralized autonomous organization
2610:Claburn, Thomas (February 14, 2019).
2453:from the original on January 16, 2013
2441:Schneier, Bruce (February 18, 2005).
2093:from the original on October 18, 2012
1228:Hash functions based on block ciphers
985:Signature generation and verification
421:(a practical example can be found in
7:
6208:
5246:
2738:Advances in Cryptology – CRYPTO 2004
2422:Finding Collisions in the Full SHA-1
2288:
1322:The Merkle–Damgård hash construction
495:. They can also be used as ordinary
58:adding citations to reliable sources
3057:Paar, Christof; Pelzl, Jan (2009).
2959:Rogaway, P.; Shrimpton, T. (2004).
2828:Introduction to Modern Cryptography
2700:Automata, Languages and Programming
2534:from the original on March 25, 2017
2306:"More Problems with Hash Functions"
1526:observed that 2-collisions lead to
1232:There are several methods to use a
977:can readily be crafted to have the
3080:"The ECRYPT Hash Function Website"
2199:from the original on 28 April 2017
1152:One of the main applications of a
1049:§ Attacks on hashed passwords
423:§ Attacks on hashed passwords
25:
5186:Distributed ledger technology law
2647:from the original on Apr 9, 2023.
2473:Brewster, Thomas (Feb 23, 2017).
2081:Perrin, Chad (December 5, 2007).
6207:
6198:
6197:
5257:
5245:
5234:
5233:
4162:
4161:
3004:Handbook of Applied Cryptography
1286:A standard block cipher such as
1173:This section is an excerpt from
531:Non-cryptographic hash functions
346:to such search is quantified as
277:the probability of a particular
34:
2983:from the original on 2022-11-30
2963:. In Roy, B.; Mier, W. (eds.).
2813:from the original on 2017-03-16
2622:from the original on 2020-04-25
2592:from the original on 2020-11-21
2485:from the original on 2017-02-24
2395:10.4018/978-1-4666-6583-5.ch006
2244:from the original on 2016-12-27
2155:from the original on 2017-05-21
2051:from the original on 2013-08-15
1934:Universal one-way hash function
1730:NIST hash function competitions
1245:block cipher modes of operation
45:needs additional citations for
4023:Information-theoretic security
3732:NIST hash function competition
2503:Halevi, Shai; Krawczyk, Hugo.
2389:, IGI Global, pp. 80–94,
1760:, or using techniques such as
1446:Pseudorandom number generators
1380:NIST hash function competition
1378:. None of the entrants in the
1094:times to find a valid header.
953:. This practice establishes a
895:poses a tough math problem to
863:are important in the study of
1:
2643:. Improsec. January 3, 2020.
2310:The Cryptography Mailing List
2043:Duong, Thai; Rizzo, Juliano.
2021:, pp. 155–157, 190, 232.
1546:Cryptographic hash algorithms
1479:is a stream cipher that uses
1451:Some hash functions, such as
1354:Wide pipe versus narrow pipe
1129:networks. For example, in an
809:Checksum algorithms, such as
562:types of cryptanalytic attack
69:"Cryptographic hash function"
6239:Cryptographic hash functions
3737:Password Hashing Competition
3148:message authentication codes
3144:Cryptographic hash functions
2934:10.1007/978-3-642-17401-8_12
2747:10.1007/978-3-540-28628-8_19
2708:10.1007/978-3-540-70583-3_50
2117:Grassi Paul A. (June 2017).
2031:Rogaway & Shrimpton 2004
1401:Message authentication codes
1329:one-way compression function
1238:one-way compression function
489:message authentication codes
350:: a cryptographic hash with
6163:Cryptographic hash function
4242:Cryptographic hash function
4139:Message authentication code
4094:Cryptographic hash function
3907:Cryptographic hash function
3691:Merkle–Damgård construction
3006:. CRC Press. pp. 33–.
2894:10.1007/978-3-642-10366-7_9
2857:10.1007/978-3-540-71039-4_4
2831:(2nd ed.). CRC Press.
1904:Message authentication code
1786:Attacks on hashed passwords
1776:Merkle–Damgård construction
1520:Merkle–Damgård construction
1340:Merkle–Damgård construction
1314:Merkle–Damgård construction
1308:Merkle–Damgård construction
1182:Content-addressable storage
1175:Content-addressable storage
1168:Content-addressable storage
859:". Such interpretations of
702:strong collision resistance
605:Second pre-image resistance
491:(MACs), and other forms of
235:cryptographic hash function
6260:
4018:Harvest now, decrypt later
2580:Goodin, Dan (2012-12-10).
2173:Kelsey & Schneier 2005
2033:, in Sec. 5. Implications.
1789:
1707:
1684:
1662:
1636:
1621:
1606:
1580:
1561:
1311:
1190:content-addressable memory
1172:
1070:
1007:
988:
916:
762:an attacker can calculate
6193:
5229:
5206:Initial exchange offering
5181:Decentralized application
5161:Cryptocurrency in Nigeria
4157:
4134:Post-quantum cryptography
3804:
3154:
3112:
3108:
2193:Cryptology ePrint Archive
2149:Cryptology ePrint Archive
1844:and some recent modes of
1624:Whirlpool (hash function)
1243:The methods resemble the
1213:peer-to-peer file sharing
1079:denial-of-service attacks
1025:graphics processing units
753:, by choosing a suitable
646:weak collision resistance
483:applications, notably in
202:
182:
162:
6234:Cryptographic primitives
6153:Timeline of cryptography
5211:List of cryptocurrencies
5098:Crypto service companies
4889:Cryptocurrency exchanges
4124:Quantum key distribution
4114:Authenticated encryption
3969:Random number generation
3485:key derivation functions
2848:Fast Software Encryption
2443:"Cryptanalysis of SHA-1"
2069:Lyubashevsky et al. 2008
1822:key derivation functions
1780:length extension attacks
1769:Transport Layer Security
1395:cryptographic primitives
967:cyclic redundancy checks
839:key derivation functions
815:cyclic redundancy checks
539:denial-of-service attack
6148:Outline of cryptography
6119:Anti–computer forensics
4119:Public-key cryptography
4109:Symmetric-key algorithm
3912:Key derivation function
3872:Cryptographic primitive
3865:Authentication protocol
3855:Outline of cryptography
3850:History of cryptography
3763:Hash-based cryptography
3665:Length extension attack
2127:10.6028/NIST.SP.800-63b
2019:Katz & Lindell 2014
1894:Length extension attack
1098:File or data identifier
650:second-preimage attacks
543:cyclic redundancy check
471:bits (lower due to the
6175:Homomorphic encryption
6168:List of hash functions
5307:Cryptographic software
5146:Complementary currency
4247:Decentralized exchange
4232:Cryptocurrency tumbler
3860:Cryptographic protocol
3773:Message authentication
2335:Hoch & Shamir 2008
2143:Lucks, Stefan (2004).
1323:
1104:source code management
465:
415:
388:
364:
325:
324:{\displaystyle 2^{-n}}
291:
263:
152:Secure Hash Algorithms
145:
6180:End-to-end encryption
5201:Initial coin offering
5156:Cryptocurrency bubble
4682:Basic Attention Token
4252:Decentralized finance
4237:Cryptocurrency wallet
4013:End-to-end encryption
3959:Cryptojacking malware
2218:Nandi & Paul 2010
1869:Cryptographic agility
1321:
1221:distributed computing
1004:Password verification
969:only prevent against
963:error-detecting codes
466:
416:
414:{\displaystyle 2^{n}}
389:
365:
326:
292:
264:
135:
5196:Environmental impact
5166:Cryptocurrency scams
4129:Quantum cryptography
4053:Trusted timestamping
3059:"11: Hash Functions"
2447:Schneier on Security
1693:Zooko Wilcox-O'Hearn
1568:MD5 was designed by
1303:Hash function design
1281:cryptographic sponge
850:theoretical analyses
825:Degree of difficulty
656:Collision resistance
568:Pre-image resistance
481:information-security
447:
441:collision resistance
398:
378:
354:
305:
297:-bit output result (
281:
253:
54:improve this article
4851:Inactive currencies
3892:Cryptographic nonce
3660:Side-channel attack
3087:Buldas, A. (2011).
3027:. No Starch Press.
2788:10.1007/11426639_28
2337:, pp. 616–630.
2304:(August 20, 2004).
2195:. Report 2007/278.
2175:, pp. 474–490.
2151:. Report 2004/253.
1814:graphics processors
1372:sponge construction
1297:related-key attacks
1204:file is unchanged.
1106:systems, including
1045:brute-force attacks
843:brute-force attacks
718:malicious adversary
713:real applications.
571:Given a hash value
499:, to index data in
464:{\displaystyle n/2}
372:preimage resistance
5767:Facebook Messenger
4306:Proof of authority
4277:Non-fungible token
4257:Distributed ledger
3998:Subliminal channel
3982:Pseudorandom noise
3929:Key (cryptography)
3717:CAESAR Competition
3701:HAIFA construction
3650:Brute-force attack
2673:10.1007/11426639_6
2427:2017-07-15 at the
2420:, and Hongbo Yu, "
2372:2004-12-20 at the
2353:2018-06-05 at the
2274:Harnik et al. 2005
1806:cryptographic salt
1762:randomized hashing
1507:used concatenated
1376:HAIFA construction
1350:, take this form.
1324:
1208:Sarbanes–Oxley Act
485:digital signatures
461:
411:
384:
360:
321:
287:
259:
146:
6221:
6220:
6071:Service providers
5805:
5804:
5611:Check Point VPN-1
5273:
5272:
5093:
5092:
4750:First Digital USD
4567:
4566:
4267:Lightning Network
4179:
4178:
4175:
4174:
4058:Key-based routing
4048:Trapdoor function
3919:Digital signature
3800:
3799:
3796:
3795:
3594:ChaCha20-Poly1305
3411:Password hashing/
3034:978-1-59327-826-7
3013:978-0-429-88132-9
2943:978-3-642-17400-1
2904:978-3-642-10365-0
2867:978-3-540-71038-7
2838:978-1-4665-7026-9
2798:978-3-540-25910-7
2757:978-3-540-22668-0
2717:978-3-540-70582-6
2682:978-3-540-25910-7
2404:978-1-4666-6583-5
2071:, pp. 54–72.
1792:Password cracking
1737:successful attack
1675:security strength
1486:HC-128 and HC-256
1279:, was built on a
997:digital signature
991:Digital signature
925:message integrity
919:File verification
902:commitment scheme
545:(CRC) functions.
387:{\displaystyle n}
363:{\displaystyle n}
348:security strength
338:) is infeasible,
290:{\displaystyle n}
262:{\displaystyle n}
231:
230:
130:
129:
122:
104:
16:(Redirected from
6251:
6211:
6210:
6201:
6200:
6049:operating system
6047:Security-focused
5995:
5820:
5395:
5300:
5293:
5286:
5277:
5261:
5260:
5249:
5248:
5237:
5236:
5221:Virtual currency
5171:Digital currency
5151:Crypto-anarchism
5043:
4796:HBAR (Hashgraph)
4779:Other currencies
4410:Ethereum Classic
4337:
4213:Cryptocurrencies
4206:
4199:
4192:
4183:
4165:
4164:
3993:Insecure channel
3829:
3822:
3815:
3806:
3681:Avalanche effect
3635:Collision attack
3178:Common functions
3137:
3130:
3123:
3114:
3110:
3106:
3096:
3091:. Archived from
3083:
3074:
3069:. Archived from
3046:
3017:
3000:"Hash functions"
2991:
2989:
2988:
2955:
2916:
2896:
2879:
2859:
2842:
2821:
2819:
2818:
2790:
2769:
2749:
2729:
2694:
2649:
2648:
2637:
2631:
2630:
2628:
2627:
2607:
2601:
2600:
2598:
2597:
2577:
2571:
2570:
2568:
2566:
2557:. CSO Magazine.
2550:
2544:
2543:
2541:
2539:
2519:
2513:
2512:
2511:on May 22, 2022.
2507:. Archived from
2500:
2494:
2493:
2491:
2490:
2470:
2464:
2462:
2460:
2458:
2438:
2432:
2414:
2408:
2407:
2382:
2376:
2363:
2357:
2344:
2338:
2332:
2326:
2325:
2323:
2321:
2316:on April 9, 2016
2312:. Archived from
2298:
2292:
2286:
2277:
2271:
2265:
2259:
2253:
2252:
2250:
2249:
2243:
2236:
2227:
2221:
2215:
2209:
2208:
2206:
2204:
2182:
2176:
2170:
2164:
2163:
2161:
2160:
2140:
2131:
2130:
2114:
2103:
2102:
2100:
2098:
2078:
2072:
2066:
2060:
2059:
2057:
2056:
2040:
2034:
2028:
2022:
2016:
2010:
2004:
1998:
1997:
1992:
1991:
1982:. Archived from
1968:
1962:
1956:
1859:Avalanche effect
1594:shattered attack
1537:
1531:
1364:length-extension
1217:cryptocurrencies
1093:
1010:Password hashing
882:
876:
869:exponential-time
845:more difficult.
797:(often called a
780:
776:
774:
761:
760:
752:
746:
738:
727:length-extension
695:
677:
668:
643:
625:
616:
600:preimage attacks
596:one-way function
593:
582:
576:
473:birthday paradox
470:
468:
467:
462:
457:
420:
418:
417:
412:
410:
409:
393:
391:
390:
385:
369:
367:
366:
361:
330:
328:
327:
322:
320:
319:
296:
294:
293:
288:
268:
266:
265:
260:
223:
216:
209:
148:
142:avalanche effect
125:
118:
114:
111:
105:
103:
62:
38:
30:
21:
6259:
6258:
6254:
6253:
6252:
6250:
6249:
6248:
6224:
6223:
6222:
6217:
6189:
6136:
6113:
6097:
6066:
6048:
6041:
5989:
5981:
5952:Java Anon Proxy
5928:
5814:
5813:
5811:Disk encryption
5801:
5777:Google Messages
5762:Signal Protocol
5716:
5683:
5650:
5597:
5494:
5446:
5389:
5382:
5309:
5304:
5274:
5269:
5225:
5191:Double-spending
5141:Blockchain game
5119:
5089:
5041:
4883:
4845:
4774:
4726:
4657:
4563:
4517:
4493:
4477:
4453:
4414:
4389:
4325:
4291:
4215:
4210:
4180:
4171:
4153:
4082:
3838:
3833:
3792:
3751:
3710:Standardization
3705:
3696:Sponge function
3669:
3645:Birthday attack
3640:Preimage attack
3623:
3579:
3572:
3500:
3483:
3482:General purpose
3477:
3412:
3406:
3255:Other functions
3250:
3217:SHA-3 finalists
3211:
3173:
3150:
3141:
3086:
3078:
3056:
3053:
3035:
3020:
3014:
2997:
2994:
2986:
2984:
2977:
2958:
2944:
2919:
2905:
2882:
2868:
2845:
2839:
2824:
2816:
2814:
2799:
2772:
2758:
2732:
2718:
2697:
2683:
2662:
2658:
2653:
2652:
2639:
2638:
2634:
2625:
2623:
2609:
2608:
2604:
2595:
2593:
2579:
2578:
2574:
2564:
2562:
2552:
2551:
2547:
2537:
2535:
2521:
2520:
2516:
2502:
2501:
2497:
2488:
2486:
2472:
2471:
2467:
2456:
2454:
2440:
2439:
2435:
2429:Wayback Machine
2415:
2411:
2405:
2384:
2383:
2379:
2374:Wayback Machine
2364:
2360:
2355:Wayback Machine
2345:
2341:
2333:
2329:
2319:
2317:
2300:
2299:
2295:
2287:
2280:
2272:
2268:
2260:
2256:
2247:
2245:
2241:
2234:
2229:
2228:
2224:
2216:
2212:
2202:
2200:
2184:
2183:
2179:
2171:
2167:
2158:
2156:
2142:
2141:
2134:
2116:
2115:
2106:
2096:
2094:
2080:
2079:
2075:
2067:
2063:
2054:
2052:
2042:
2041:
2037:
2029:
2025:
2017:
2013:
2005:
2001:
1989:
1987:
1972:Schneier, Bruce
1970:
1969:
1965:
1957:
1953:
1948:
1943:
1938:
1854:
1794:
1788:
1725:
1712:
1706:
1689:
1683:
1667:
1661:
1641:
1635:
1626:
1620:
1611:
1605:
1585:
1579:
1566:
1560:
1548:
1540:polynomial time
1533:
1527:
1498:
1492:hash function.
1407:is such a MAC.
1391:
1356:
1316:
1310:
1305:
1292:embedded system
1230:
1225:
1224:
1178:
1170:
1100:
1091:
1075:
1069:
1012:
1006:
993:
987:
921:
915:
910:
889:
878:
872:
857:polynomial time
827:
795:random function
778:
772:
763:
758:
754:
748:
740:
732:
706:birthday attack
693:
686:
679:
676:
670:
667:
661:
641:
634:
627:
624:
618:
615:
609:
608:Given an input
584:
578:
572:
551:
445:
444:
430:second preimage
401:
396:
395:
376:
375:
352:
351:
308:
303:
302:
279:
278:
251:
250:
227:
198:
126:
115:
109:
106:
63:
61:
51:
39:
28:
23:
22:
15:
12:
11:
5:
6257:
6255:
6247:
6246:
6241:
6236:
6226:
6225:
6219:
6218:
6216:
6215:
6205:
6194:
6191:
6190:
6188:
6187:
6182:
6177:
6172:
6171:
6170:
6165:
6158:Hash functions
6155:
6150:
6144:
6142:
6141:Related topics
6138:
6137:
6135:
6134:
6129:
6123:
6121:
6115:
6114:
6112:
6111:
6105:
6103:
6099:
6098:
6096:
6095:
6090:
6085:
6080:
6074:
6072:
6068:
6067:
6065:
6064:
6059:
6053:
6051:
6043:
6042:
6040:
6039:
6034:
6029:
6024:
6019:
6014:
6009:
6004:
5998:
5996:
5983:
5982:
5980:
5979:
5974:
5969:
5964:
5959:
5954:
5949:
5944:
5938:
5936:
5930:
5929:
5927:
5926:
5921:
5920:
5919:
5909:
5904:
5899:
5894:
5889:
5884:
5879:
5874:
5869:
5864:
5859:
5854:
5849:
5844:
5839:
5834:
5829:
5823:
5821:
5807:
5806:
5803:
5802:
5800:
5799:
5796:
5795:
5794:
5789:
5784:
5779:
5774:
5769:
5759:
5754:
5749:
5748:
5747:
5742:
5732:
5726:
5724:
5718:
5717:
5715:
5714:
5709:
5704:
5699:
5693:
5691:
5685:
5684:
5682:
5681:
5676:
5671:
5666:
5660:
5658:
5652:
5651:
5649:
5648:
5643:
5638:
5633:
5628:
5623:
5618:
5613:
5607:
5605:
5599:
5598:
5596:
5595:
5590:
5585:
5580:
5575:
5570:
5565:
5560:
5555:
5550:
5545:
5540:
5535:
5530:
5525:
5520:
5515:
5510:
5508:BBM Enterprise
5504:
5502:
5496:
5495:
5493:
5492:
5487:
5482:
5477:
5472:
5467:
5462:
5456:
5454:
5448:
5447:
5445:
5444:
5439:
5434:
5429:
5424:
5419:
5414:
5409:
5403:
5401:
5392:
5384:
5383:
5381:
5380:
5375:
5370:
5365:
5360:
5355:
5350:
5340:
5335:
5330:
5325:
5319:
5317:
5311:
5310:
5305:
5303:
5302:
5295:
5288:
5280:
5271:
5270:
5268:
5267:
5255:
5243:
5230:
5227:
5226:
5224:
5223:
5218:
5213:
5208:
5203:
5198:
5193:
5188:
5183:
5178:
5173:
5168:
5163:
5158:
5153:
5148:
5143:
5138:
5133:
5127:
5125:
5124:Related topics
5121:
5120:
5118:
5117:
5112:
5107:
5101:
5099:
5095:
5094:
5091:
5090:
5088:
5087:
5082:
5077:
5072:
5067:
5066:
5065:
5055:
5049:
5047:
5040:
5039:
5034:
5029:
5024:
5019:
5014:
5009:
5004:
4999:
4994:
4989:
4984:
4979:
4974:
4969:
4964:
4959:
4954:
4949:
4944:
4939:
4934:
4929:
4924:
4919:
4914:
4909:
4904:
4899:
4893:
4891:
4885:
4884:
4882:
4881:
4876:
4871:
4866:
4861:
4855:
4853:
4847:
4846:
4844:
4843:
4838:
4833:
4828:
4823:
4818:
4813:
4808:
4803:
4798:
4793:
4788:
4782:
4780:
4776:
4775:
4773:
4772:
4767:
4762:
4757:
4752:
4747:
4742:
4736:
4734:
4728:
4727:
4725:
4724:
4719:
4714:
4709:
4704:
4699:
4694:
4689:
4684:
4679:
4674:
4668:
4666:
4659:
4658:
4656:
4655:
4650:
4645:
4640:
4635:
4630:
4625:
4620:
4615:
4610:
4605:
4599:
4594:
4589:
4584:
4578:
4576:
4573:Proof of stake
4569:
4568:
4565:
4564:
4562:
4561:
4556:
4551:
4546:
4544:Nervos Network
4541:
4536:
4531:
4525:
4523:
4519:
4518:
4516:
4515:
4510:
4504:
4502:
4495:
4494:
4492:
4491:
4485:
4483:
4479:
4478:
4476:
4475:
4470:
4464:
4462:
4455:
4454:
4452:
4451:
4446:
4441:
4436:
4431:
4425:
4423:
4416:
4415:
4413:
4412:
4407:
4400:
4398:
4391:
4390:
4388:
4387:
4382:
4377:
4372:
4367:
4362:
4357:
4352:
4346:
4344:
4334:
4327:
4326:
4324:
4323:
4318:
4316:Proof of stake
4313:
4311:Proof of space
4308:
4302:
4300:
4293:
4292:
4290:
4289:
4284:
4282:Smart contract
4279:
4274:
4269:
4264:
4259:
4254:
4249:
4244:
4239:
4234:
4229:
4223:
4221:
4217:
4216:
4211:
4209:
4208:
4201:
4194:
4186:
4177:
4176:
4173:
4172:
4170:
4169:
4158:
4155:
4154:
4152:
4151:
4146:
4144:Random numbers
4141:
4136:
4131:
4126:
4121:
4116:
4111:
4106:
4101:
4096:
4090:
4088:
4084:
4083:
4081:
4080:
4075:
4070:
4068:Garlic routing
4065:
4060:
4055:
4050:
4045:
4040:
4035:
4030:
4025:
4020:
4015:
4010:
4005:
4000:
3995:
3990:
3988:Secure channel
3985:
3979:
3978:
3977:
3966:
3961:
3956:
3951:
3949:Key stretching
3946:
3941:
3936:
3931:
3926:
3921:
3916:
3915:
3914:
3909:
3899:
3897:Cryptovirology
3894:
3889:
3884:
3882:Cryptocurrency
3879:
3874:
3869:
3868:
3867:
3857:
3852:
3846:
3844:
3840:
3839:
3834:
3832:
3831:
3824:
3817:
3809:
3802:
3801:
3798:
3797:
3794:
3793:
3791:
3790:
3785:
3780:
3775:
3770:
3765:
3759:
3757:
3753:
3752:
3750:
3749:
3744:
3739:
3734:
3729:
3724:
3719:
3713:
3711:
3707:
3706:
3704:
3703:
3698:
3693:
3688:
3686:Hash collision
3683:
3677:
3675:
3671:
3670:
3668:
3667:
3662:
3657:
3652:
3647:
3642:
3637:
3631:
3629:
3625:
3624:
3622:
3621:
3616:
3611:
3606:
3601:
3596:
3591:
3585:
3583:
3574:
3573:
3571:
3570:
3565:
3560:
3555:
3550:
3545:
3536:
3531:
3526:
3521:
3516:
3510:
3508:
3502:
3501:
3499:
3498:
3495:
3489:
3487:
3479:
3478:
3476:
3475:
3470:
3465:
3460:
3455:
3450:
3445:
3440:
3435:
3430:
3425:
3419:
3417:
3414:key stretching
3408:
3407:
3405:
3404:
3399:
3394:
3389:
3384:
3379:
3374:
3369:
3364:
3359:
3354:
3349:
3344:
3339:
3334:
3329:
3324:
3319:
3314:
3309:
3304:
3299:
3294:
3289:
3284:
3279:
3274:
3269:
3264:
3258:
3256:
3252:
3251:
3249:
3248:
3242:
3237:
3232:
3227:
3221:
3219:
3213:
3212:
3210:
3209:
3204:
3199:
3194:
3188:
3181:
3179:
3175:
3174:
3172:
3171:
3166:
3161:
3155:
3152:
3151:
3142:
3140:
3139:
3132:
3125:
3117:
3103:
3102:
3097:
3095:on 2012-12-06.
3084:
3076:
3073:on 2012-12-08.
3052:
3051:External links
3049:
3048:
3047:
3033:
3018:
3012:
2993:
2992:
2975:
2956:
2942:
2917:
2903:
2880:
2866:
2843:
2837:
2822:
2797:
2770:
2756:
2730:
2716:
2695:
2681:
2659:
2657:
2654:
2651:
2650:
2632:
2602:
2572:
2545:
2514:
2495:
2465:
2433:
2418:Yiqun Lisa Yin
2416:Xiaoyun Wang,
2409:
2403:
2377:
2358:
2339:
2327:
2293:
2278:
2266:
2254:
2222:
2210:
2177:
2165:
2132:
2104:
2073:
2061:
2035:
2023:
2011:
2009:, p. 106.
1999:
1963:
1950:
1949:
1947:
1944:
1942:
1939:
1937:
1936:
1931:
1926:
1921:
1916:
1911:
1906:
1901:
1896:
1891:
1886:
1881:
1876:
1871:
1866:
1861:
1855:
1853:
1850:
1810:rainbow tables
1790:Main article:
1787:
1784:
1724:
1721:
1708:Main article:
1705:
1702:
1685:Main article:
1682:
1679:
1663:Main article:
1660:
1657:
1637:Main article:
1634:
1631:
1622:Main article:
1619:
1616:
1607:Main article:
1604:
1601:
1581:Main article:
1578:
1575:
1562:Main article:
1559:
1556:
1547:
1544:
1497:
1494:
1390:
1387:
1355:
1352:
1312:Main article:
1309:
1306:
1304:
1301:
1229:
1226:
1179:
1171:
1169:
1166:
1099:
1096:
1084:Bitcoin mining
1071:Main article:
1068:
1065:
1029:key stretching
1008:Main article:
1005:
1002:
989:Main article:
986:
983:
979:colliding code
955:chain of trust
917:Main article:
914:
911:
909:
906:
888:
885:
826:
823:
710:
709:
698:hash collision
691:
684:
674:
665:
658:
653:
639:
632:
622:
613:
606:
603:
569:
550:
547:
505:fingerprinting
497:hash functions
493:authentication
477:
476:
460:
456:
452:
433:
426:
408:
404:
383:
359:
332:
318:
315:
311:
286:
258:
243:hash algorithm
229:
228:
226:
225:
218:
211:
203:
200:
199:
180:
179:
178:Main standards
175:
174:
164:hash functions
160:
159:
155:
154:
128:
127:
42:
40:
33:
26:
24:
18:Message digest
14:
13:
10:
9:
6:
4:
3:
2:
6256:
6245:
6242:
6240:
6237:
6235:
6232:
6231:
6229:
6214:
6206:
6204:
6196:
6195:
6192:
6186:
6183:
6181:
6178:
6176:
6173:
6169:
6166:
6164:
6161:
6160:
6159:
6156:
6154:
6151:
6149:
6146:
6145:
6143:
6139:
6133:
6130:
6128:
6125:
6124:
6122:
6120:
6116:
6110:
6107:
6106:
6104:
6100:
6094:
6091:
6089:
6086:
6084:
6081:
6079:
6076:
6075:
6073:
6069:
6063:
6060:
6058:
6055:
6054:
6052:
6050:
6044:
6038:
6035:
6033:
6030:
6028:
6025:
6023:
6020:
6018:
6015:
6013:
6010:
6008:
6005:
6003:
6000:
5999:
5997:
5993:
5988:
5984:
5978:
5975:
5973:
5970:
5968:
5965:
5963:
5960:
5958:
5955:
5953:
5950:
5948:
5945:
5943:
5940:
5939:
5937:
5935:
5931:
5925:
5922:
5918:
5915:
5914:
5913:
5910:
5908:
5905:
5903:
5900:
5898:
5895:
5893:
5890:
5888:
5885:
5883:
5880:
5878:
5875:
5873:
5870:
5868:
5865:
5863:
5860:
5858:
5855:
5853:
5850:
5848:
5845:
5843:
5840:
5838:
5835:
5833:
5830:
5828:
5825:
5824:
5822:
5818:
5812:
5808:
5797:
5793:
5790:
5788:
5785:
5783:
5780:
5778:
5775:
5773:
5770:
5768:
5765:
5764:
5763:
5760:
5758:
5755:
5753:
5750:
5746:
5743:
5741:
5738:
5737:
5736:
5733:
5731:
5728:
5727:
5725:
5723:
5719:
5713:
5710:
5708:
5705:
5703:
5700:
5698:
5695:
5694:
5692:
5690:
5686:
5680:
5677:
5675:
5672:
5670:
5667:
5665:
5662:
5661:
5659:
5657:
5653:
5647:
5644:
5642:
5639:
5637:
5634:
5632:
5631:SoftEther VPN
5629:
5627:
5624:
5622:
5619:
5617:
5614:
5612:
5609:
5608:
5606:
5604:
5600:
5594:
5591:
5589:
5586:
5584:
5581:
5579:
5576:
5574:
5571:
5569:
5566:
5564:
5561:
5559:
5556:
5554:
5551:
5549:
5546:
5544:
5541:
5539:
5536:
5534:
5531:
5529:
5526:
5524:
5521:
5519:
5516:
5514:
5513:Bouncy Castle
5511:
5509:
5506:
5505:
5503:
5501:
5500:TLS & SSL
5497:
5491:
5488:
5486:
5483:
5481:
5478:
5476:
5473:
5471:
5468:
5466:
5463:
5461:
5458:
5457:
5455:
5453:
5449:
5443:
5440:
5438:
5435:
5433:
5430:
5428:
5425:
5423:
5420:
5418:
5415:
5413:
5410:
5408:
5405:
5404:
5402:
5400:
5396:
5393:
5391:
5390:communication
5385:
5379:
5376:
5374:
5371:
5369:
5366:
5364:
5361:
5359:
5356:
5354:
5351:
5348:
5344:
5341:
5339:
5336:
5334:
5331:
5329:
5326:
5324:
5321:
5320:
5318:
5316:
5315:Email clients
5312:
5308:
5301:
5296:
5294:
5289:
5287:
5282:
5281:
5278:
5266:
5265:
5256:
5254:
5253:
5244:
5242:
5241:
5232:
5231:
5228:
5222:
5219:
5217:
5214:
5212:
5209:
5207:
5204:
5202:
5199:
5197:
5194:
5192:
5189:
5187:
5184:
5182:
5179:
5177:
5174:
5172:
5169:
5167:
5164:
5162:
5159:
5157:
5154:
5152:
5149:
5147:
5144:
5142:
5139:
5137:
5134:
5132:
5129:
5128:
5126:
5122:
5116:
5113:
5111:
5108:
5106:
5103:
5102:
5100:
5096:
5086:
5083:
5081:
5078:
5076:
5073:
5071:
5070:LocalBitcoins
5068:
5064:
5061:
5060:
5059:
5056:
5054:
5051:
5050:
5048:
5044:
5038:
5035:
5033:
5030:
5028:
5025:
5023:
5020:
5018:
5015:
5013:
5010:
5008:
5005:
5003:
5002:ItBit (Paxos)
5000:
4998:
4995:
4993:
4990:
4988:
4985:
4983:
4980:
4978:
4975:
4973:
4970:
4968:
4965:
4963:
4960:
4958:
4955:
4953:
4950:
4948:
4945:
4943:
4940:
4938:
4935:
4933:
4930:
4928:
4925:
4923:
4920:
4918:
4915:
4913:
4910:
4908:
4905:
4903:
4900:
4898:
4895:
4894:
4892:
4890:
4886:
4880:
4877:
4875:
4872:
4870:
4867:
4865:
4862:
4860:
4857:
4856:
4854:
4852:
4848:
4842:
4839:
4837:
4834:
4832:
4829:
4827:
4824:
4822:
4819:
4817:
4814:
4812:
4809:
4807:
4804:
4802:
4799:
4797:
4794:
4792:
4789:
4787:
4784:
4783:
4781:
4777:
4771:
4768:
4766:
4763:
4761:
4758:
4756:
4753:
4751:
4748:
4746:
4743:
4741:
4738:
4737:
4735:
4733:
4729:
4723:
4720:
4718:
4715:
4713:
4710:
4708:
4705:
4703:
4700:
4698:
4695:
4693:
4690:
4688:
4685:
4683:
4680:
4678:
4675:
4673:
4670:
4669:
4667:
4664:
4660:
4654:
4651:
4649:
4646:
4644:
4641:
4639:
4636:
4634:
4631:
4629:
4626:
4624:
4621:
4619:
4616:
4614:
4611:
4609:
4606:
4603:
4600:
4598:
4595:
4593:
4590:
4588:
4585:
4583:
4580:
4579:
4577:
4574:
4570:
4560:
4557:
4555:
4552:
4550:
4547:
4545:
4542:
4540:
4537:
4535:
4532:
4530:
4527:
4526:
4524:
4520:
4514:
4511:
4509:
4506:
4505:
4503:
4500:
4496:
4490:
4487:
4486:
4484:
4482:RandomX-based
4480:
4474:
4471:
4469:
4466:
4465:
4463:
4460:
4456:
4450:
4447:
4445:
4442:
4440:
4437:
4435:
4432:
4430:
4427:
4426:
4424:
4421:
4417:
4411:
4408:
4405:
4402:
4401:
4399:
4396:
4392:
4386:
4383:
4381:
4378:
4376:
4373:
4371:
4368:
4366:
4363:
4361:
4358:
4356:
4353:
4351:
4348:
4347:
4345:
4342:
4338:
4335:
4332:
4331:Proof of work
4328:
4322:
4321:Proof of work
4319:
4317:
4314:
4312:
4309:
4307:
4304:
4303:
4301:
4298:
4294:
4288:
4285:
4283:
4280:
4278:
4275:
4273:
4270:
4268:
4265:
4263:
4260:
4258:
4255:
4253:
4250:
4248:
4245:
4243:
4240:
4238:
4235:
4233:
4230:
4228:
4225:
4224:
4222:
4218:
4214:
4207:
4202:
4200:
4195:
4193:
4188:
4187:
4184:
4168:
4160:
4159:
4156:
4150:
4149:Steganography
4147:
4145:
4142:
4140:
4137:
4135:
4132:
4130:
4127:
4125:
4122:
4120:
4117:
4115:
4112:
4110:
4107:
4105:
4104:Stream cipher
4102:
4100:
4097:
4095:
4092:
4091:
4089:
4085:
4079:
4076:
4074:
4071:
4069:
4066:
4064:
4063:Onion routing
4061:
4059:
4056:
4054:
4051:
4049:
4046:
4044:
4043:Shared secret
4041:
4039:
4036:
4034:
4031:
4029:
4026:
4024:
4021:
4019:
4016:
4014:
4011:
4009:
4006:
4004:
4001:
3999:
3996:
3994:
3991:
3989:
3986:
3983:
3980:
3975:
3972:
3971:
3970:
3967:
3965:
3962:
3960:
3957:
3955:
3952:
3950:
3947:
3945:
3942:
3940:
3939:Key generator
3937:
3935:
3932:
3930:
3927:
3925:
3922:
3920:
3917:
3913:
3910:
3908:
3905:
3904:
3903:
3902:Hash function
3900:
3898:
3895:
3893:
3890:
3888:
3885:
3883:
3880:
3878:
3877:Cryptanalysis
3875:
3873:
3870:
3866:
3863:
3862:
3861:
3858:
3856:
3853:
3851:
3848:
3847:
3845:
3841:
3837:
3830:
3825:
3823:
3818:
3816:
3811:
3810:
3807:
3803:
3789:
3786:
3784:
3781:
3779:
3778:Proof of work
3776:
3774:
3771:
3769:
3766:
3764:
3761:
3760:
3758:
3754:
3748:
3745:
3743:
3740:
3738:
3735:
3733:
3730:
3728:
3725:
3723:
3720:
3718:
3715:
3714:
3712:
3708:
3702:
3699:
3697:
3694:
3692:
3689:
3687:
3684:
3682:
3679:
3678:
3676:
3672:
3666:
3663:
3661:
3658:
3656:
3655:Rainbow table
3653:
3651:
3648:
3646:
3643:
3641:
3638:
3636:
3633:
3632:
3630:
3626:
3620:
3617:
3615:
3612:
3610:
3607:
3605:
3602:
3600:
3597:
3595:
3592:
3590:
3587:
3586:
3584:
3581:
3578:Authenticated
3575:
3569:
3566:
3564:
3561:
3559:
3556:
3554:
3551:
3549:
3546:
3544:
3540:
3537:
3535:
3532:
3530:
3527:
3525:
3522:
3520:
3517:
3515:
3512:
3511:
3509:
3507:
3506:MAC functions
3503:
3496:
3494:
3491:
3490:
3488:
3486:
3480:
3474:
3471:
3469:
3466:
3464:
3461:
3459:
3456:
3454:
3451:
3449:
3446:
3444:
3441:
3439:
3436:
3434:
3431:
3429:
3426:
3424:
3421:
3420:
3418:
3415:
3409:
3403:
3400:
3398:
3395:
3393:
3390:
3388:
3385:
3383:
3380:
3378:
3375:
3373:
3370:
3368:
3365:
3363:
3360:
3358:
3355:
3353:
3350:
3348:
3345:
3343:
3340:
3338:
3335:
3333:
3330:
3328:
3325:
3323:
3320:
3318:
3315:
3313:
3310:
3308:
3305:
3303:
3300:
3298:
3295:
3293:
3290:
3288:
3285:
3283:
3280:
3278:
3275:
3273:
3270:
3268:
3265:
3263:
3260:
3259:
3257:
3253:
3246:
3243:
3241:
3238:
3236:
3233:
3231:
3228:
3226:
3223:
3222:
3220:
3218:
3214:
3208:
3205:
3203:
3200:
3198:
3195:
3193:(compromised)
3192:
3189:
3187:(compromised)
3186:
3183:
3182:
3180:
3176:
3170:
3169:Known attacks
3167:
3165:
3162:
3160:
3157:
3156:
3153:
3149:
3145:
3138:
3133:
3131:
3126:
3124:
3119:
3118:
3115:
3111:
3107:
3101:
3098:
3094:
3090:
3085:
3081:
3077:
3072:
3068:
3064:
3060:
3055:
3054:
3050:
3044:
3040:
3036:
3030:
3026:
3025:
3019:
3015:
3009:
3005:
3001:
2996:
2995:
2982:
2978:
2976:3-540-22171-9
2972:
2968:
2967:
2962:
2957:
2953:
2949:
2945:
2939:
2935:
2931:
2927:
2923:
2918:
2914:
2910:
2906:
2900:
2895:
2890:
2886:
2881:
2877:
2873:
2869:
2863:
2858:
2853:
2849:
2844:
2840:
2834:
2830:
2829:
2823:
2812:
2808:
2804:
2800:
2794:
2789:
2784:
2780:
2776:
2771:
2767:
2763:
2759:
2753:
2748:
2743:
2739:
2735:
2734:Joux, Antoine
2731:
2727:
2723:
2719:
2713:
2709:
2705:
2701:
2696:
2692:
2688:
2684:
2678:
2674:
2670:
2666:
2661:
2660:
2655:
2646:
2642:
2636:
2633:
2621:
2617:
2613:
2606:
2603:
2591:
2587:
2583:
2576:
2573:
2560:
2556:
2549:
2546:
2533:
2529:
2525:
2518:
2515:
2510:
2506:
2499:
2496:
2484:
2480:
2476:
2469:
2466:
2452:
2448:
2444:
2437:
2434:
2430:
2426:
2423:
2419:
2413:
2410:
2406:
2400:
2396:
2392:
2388:
2381:
2378:
2375:
2371:
2368:
2362:
2359:
2356:
2352:
2349:
2343:
2340:
2336:
2331:
2328:
2315:
2311:
2307:
2303:
2297:
2294:
2290:
2285:
2283:
2279:
2275:
2270:
2267:
2263:
2262:Mendel et al.
2258:
2255:
2240:
2233:
2226:
2223:
2219:
2214:
2211:
2198:
2194:
2190:
2189:
2181:
2178:
2174:
2169:
2166:
2154:
2150:
2146:
2139:
2137:
2133:
2128:
2124:
2120:
2113:
2111:
2109:
2105:
2092:
2088:
2084:
2077:
2074:
2070:
2065:
2062:
2050:
2046:
2039:
2036:
2032:
2027:
2024:
2020:
2015:
2012:
2008:
2007:Aumasson 2017
2003:
2000:
1996:
1986:on 2016-03-16
1985:
1981:
1980:Computerworld
1977:
1973:
1967:
1964:
1961:, p. 33.
1960:
1955:
1952:
1945:
1940:
1935:
1932:
1930:
1927:
1925:
1922:
1920:
1919:Random oracle
1917:
1915:
1914:PGP word list
1912:
1910:
1907:
1905:
1902:
1900:
1897:
1895:
1892:
1890:
1887:
1885:
1882:
1880:
1877:
1875:
1872:
1870:
1867:
1865:
1862:
1860:
1857:
1856:
1851:
1849:
1847:
1843:
1839:
1835:
1831:
1827:
1823:
1819:
1815:
1811:
1807:
1802:
1798:
1793:
1785:
1783:
1781:
1777:
1772:
1770:
1765:
1763:
1759:
1753:
1751:
1747:
1746:supercomputer
1741:
1738:
1733:
1731:
1722:
1720:
1718:
1711:
1703:
1701:
1698:
1694:
1688:
1680:
1678:
1676:
1671:
1666:
1658:
1656:
1653:
1651:
1645:
1640:
1632:
1630:
1625:
1617:
1615:
1610:
1602:
1600:
1597:
1595:
1590:
1584:
1576:
1574:
1571:
1570:Ronald Rivest
1565:
1557:
1555:
1553:
1545:
1543:
1541:
1536:
1530:
1525:
1521:
1516:
1514:
1510:
1506:
1502:
1501:Concatenating
1496:Concatenation
1495:
1493:
1491:
1487:
1482:
1478:
1474:
1470:
1466:
1465:stream cipher
1462:
1458:
1454:
1449:
1447:
1443:
1441:
1437:
1433:
1429:
1425:
1421:
1417:
1413:
1412:block ciphers
1408:
1406:
1402:
1398:
1396:
1388:
1386:
1383:
1381:
1377:
1373:
1369:
1365:
1361:
1353:
1351:
1349:
1345:
1341:
1337:
1336:length padded
1332:
1330:
1320:
1315:
1307:
1302:
1300:
1298:
1293:
1289:
1284:
1282:
1278:
1274:
1270:
1266:
1262:
1258:
1254:
1250:
1246:
1241:
1239:
1235:
1227:
1222:
1218:
1214:
1209:
1205:
1202:
1198:
1193:
1191:
1187:
1183:
1176:
1167:
1165:
1161:
1159:
1155:
1154:hash function
1150:
1148:
1144:
1140:
1136:
1132:
1128:
1125:
1121:
1117:
1113:
1109:
1105:
1097:
1095:
1089:
1085:
1080:
1074:
1073:Proof of work
1067:Proof-of-work
1066:
1064:
1062:
1057:
1052:
1050:
1046:
1042:
1038:
1034:
1030:
1026:
1020:
1017:
1011:
1003:
1001:
998:
992:
984:
982:
980:
976:
972:
971:non-malicious
968:
964:
960:
956:
952:
948:
944:
940:
936:
932:
930:
926:
920:
912:
907:
905:
903:
898:
894:
886:
884:
881:
875:
870:
866:
862:
858:
855:
851:
846:
844:
840:
836:
831:
824:
822:
820:
816:
812:
807:
804:
800:
799:random oracle
796:
790:
788:
784:
783:concatenation
771:
767:
757:
751:
744:
736:
730:
728:
722:
719:
714:
707:
703:
699:
690:
683:
673:
664:
659:
657:
654:
651:
647:
638:
631:
621:
612:
607:
604:
601:
597:
591:
587:
581:
575:
570:
567:
566:
565:
563:
558:
556:
548:
546:
544:
540:
536:
532:
528:
526:
522:
518:
514:
510:
506:
502:
498:
494:
490:
486:
482:
474:
458:
454:
450:
442:
438:
434:
431:
427:
424:
406:
402:
381:
373:
357:
349:
345:
341:
337:
333:
316:
313:
309:
300:
284:
276:
275:
274:
273:application:
272:
271:cryptographic
256:
248:
244:
240:
236:
224:
219:
217:
212:
210:
205:
204:
201:
197:
193:
189:
185:
181:
176:
173:
169:
165:
161:
156:
153:
149:
143:
139:
134:
124:
121:
113:
102:
99:
95:
92:
88:
85:
81:
78:
74:
71: –
70:
66:
65:Find sources:
59:
55:
49:
48:
43:This article
41:
37:
32:
31:
19:
6162:
5987:File systems
5897:Private Disk
5262:
5250:
5238:
5115:Initiative Q
4468:Bitcoin Gold
4360:Counterparty
4355:Bitcoin Cash
4241:
4099:Block cipher
4093:
3944:Key schedule
3934:Key exchange
3924:Kleptography
3906:
3887:Cryptosystem
3836:Cryptography
3143:
3093:the original
3071:the original
3062:
3023:
3003:
2985:. Retrieved
2965:
2925:
2884:
2847:
2827:
2815:. Retrieved
2778:
2737:
2699:
2664:
2635:
2624:. Retrieved
2616:The Register
2615:
2605:
2594:. Retrieved
2586:Ars Technica
2575:
2565:November 25,
2563:. Retrieved
2548:
2536:. Retrieved
2527:
2517:
2509:the original
2498:
2487:. Retrieved
2478:
2468:
2455:. Retrieved
2446:
2436:
2412:
2386:
2380:
2361:
2342:
2330:
2318:. Retrieved
2314:the original
2309:
2296:
2269:
2257:
2246:. Retrieved
2225:
2213:
2201:. Retrieved
2192:
2187:
2180:
2168:
2157:. Retrieved
2148:
2118:
2095:. Retrieved
2087:TechRepublic
2086:
2076:
2064:
2053:. Retrieved
2038:
2026:
2014:
2002:
1994:
1988:. Retrieved
1984:the original
1979:
1966:
1954:
1803:
1799:
1795:
1773:
1766:
1754:
1742:
1734:
1726:
1713:
1690:
1672:
1668:
1654:
1646:
1642:
1627:
1612:
1598:
1586:
1567:
1549:
1534:
1528:
1524:Antoine Joux
1517:
1499:
1450:
1444:
1428:Davies–Meyer
1416:Luby-Rackoff
1409:
1399:
1392:
1384:
1367:
1359:
1357:
1333:
1325:
1285:
1242:
1234:block cipher
1231:
1194:
1180:
1162:
1151:
1139:Magnet links
1124:peer-to-peer
1101:
1076:
1053:
1021:
1013:
994:
970:
947:file sharing
933:
922:
908:Applications
890:
887:Illustration
879:
873:
860:
847:
832:
828:
808:
791:
769:
765:
755:
749:
742:
734:
726:
723:
715:
711:
701:
688:
681:
671:
662:
645:
636:
629:
619:
610:
589:
585:
579:
573:
559:
552:
533:are used in
529:
524:
520:
517:fingerprints
516:
512:
478:
443:strength of
440:
436:
429:
374:strength of
371:
343:
339:
335:
238:
234:
232:
163:
116:
107:
97:
90:
83:
76:
64:
52:Please help
47:verification
44:
6102:Educational
5907:Sentry 2020
5852:DriveSentry
5772:Google Allo
5378:Thunderbird
5216:Token money
5105:Hyperledger
4977:EDX Markets
4841:WhopperCoin
4732:Stablecoins
4087:Mathematics
4078:Mix network
3768:Merkle tree
3756:Utilization
3742:NSA Suite B
2302:Finney, Hal
1879:File fixity
1804:The use of
1801:much time.
1771:) in 2008.
1717:Merkle tree
1360:narrow-pipe
1197:file system
1127:filesharing
1061:precomputed
995:Almost all
535:hash tables
525:hash values
501:hash tables
6228:Categories
6093:NordLocker
6037:Tahoe-LAFS
6027:Rubberhose
5967:RetroShare
5842:Cryptoloop
5837:CrossCrypt
5817:Comparison
5787:TextSecure
5745:ChatSecure
5707:RetroShare
5697:Bitmessage
5636:strongSwan
5422:ChatSecure
5333:Claws Mail
5323:Apple Mail
5136:BitLicense
5080:QuadrigaCX
5063:bankruptcy
5027:ShapeShift
4972:Crypto.com
4859:BitConnect
4811:MobileCoin
4575:currencies
4434:Bitconnect
4429:Auroracoin
4333:currencies
4299:mechanisms
4227:Blockchain
4220:Technology
4038:Ciphertext
4008:Decryption
4003:Encryption
3964:Ransomware
3580:encryption
3357:RadioGatún
3164:Comparison
3043:1012843116
2987:2022-11-30
2817:2017-07-18
2626:2020-11-26
2596:2020-11-23
2489:2017-02-24
2248:2017-07-18
2237:(Report).
2159:2017-07-18
2055:2012-12-07
1990:2016-04-20
1941:References
1889:Hash chain
1846:Unix crypt
1609:RIPEMD-160
1603:RIPEMD-160
1461:RadioGatún
1158:hash table
1118:, use the
1031:– such as
877:steps for
861:difficulty
854:asymptotic
813:and other
678:such that
626:such that
583:such that
549:Properties
523:, or just
344:resistance
299:hash value
80:newspapers
5934:Anonymity
5924:VeraCrypt
5912:TrueCrypt
5902:Scramdisk
5867:FileVault
5832:BitLocker
5827:BestCrypt
5740:Cryptocat
5646:WireGuard
5548:MatrixSSL
5518:BoringSSL
5480:SecureCRT
5442:Profanity
5417:Centericq
5328:Autocrypt
4967:Coincheck
4869:KodakCoin
4712:Shiba Inu
4697:KodakCoin
4687:Chainlink
4613:Injective
4587:Avalanche
4549:Primecoin
4297:Consensus
4028:Plaintext
3497:KDF1/KDF2
3416:functions
3402:Whirlpool
2952:0302-9743
2913:0302-9743
2876:0302-9743
2807:0302-9743
2766:0302-9743
2726:0302-9743
2691:0302-9743
2538:March 29,
2528:HashClash
2457:March 30,
2289:Joux 2004
1946:Citations
1750:Itanium 2
1748:with 256
1618:Whirlpool
1473:keystream
1368:wide-pipe
1283:instead.
1201:directory
1186:retrieval
1147:hash tree
1143:hash list
1131:ed2k link
1112:Mercurial
1016:cleartext
951:mirroring
835:passwords
687:) = hash(
635:) = hash(
521:checksums
509:checksums
437:collision
336:pre-image
314:−
6203:Category
6109:CrypTool
6083:Tresorit
6012:eCryptfs
5972:Ricochet
5872:FreeOTFE
5862:eCryptfs
5847:dm-crypt
5792:WhatsApp
5669:Linphone
5621:Openswan
5588:TeamNote
5573:SChannel
5563:mbed TLS
5543:LibreSSL
5528:cryptlib
5460:Dropbear
5373:Sylpheed
5338:Enigmail
5240:Category
4962:Coinbase
4942:Bitstamp
4922:Bitpanda
4912:bitFlyer
4907:Bitfinex
4831:SafeMoon
4791:Filecoin
4770:USD Coin
4633:Polkadot
4628:Peercoin
4608:Gridcoin
4602:Ethereum
4582:Algorand
4559:Vertcoin
4529:AmbaCoin
4459:Equihash
4449:Litecoin
4444:Dogecoin
4404:Ethereum
4380:Peercoin
4375:Namecoin
4370:MazaCoin
4272:MetaMask
4167:Category
4073:Kademlia
4033:Codetext
3976:(CSPRNG)
3722:CRYPTREC
3553:Poly1305
3473:yescrypt
3387:Streebog
3267:CubeHash
3247:(winner)
3067:Springer
2981:Archived
2811:Archived
2645:Archived
2620:Archived
2590:Archived
2559:Archived
2532:Archived
2483:Archived
2451:Archived
2425:Archived
2370:Archived
2351:Archived
2239:Archived
2197:Archived
2153:Archived
2121:. NIST.
2097:March 2,
2091:Archived
2049:Archived
1874:CRYPTREC
1852:See also
1589:Capstone
1410:Just as
1116:Monotone
1088:Hashcash
965:such as
949:such as
848:In some
781:denotes
777:, where
747:but not
731:: given
158:Concepts
110:May 2016
6244:Hashing
6213:Commons
6132:BusKill
6127:USBKill
6078:Freenet
5962:Vidalia
5917:History
5892:PGPDisk
5798:SimpleX
5757:Session
5752:Proteus
5626:OpenVPN
5616:Hamachi
5593:wolfSSL
5583:stunnel
5558:OpenSSL
5490:wolfSSH
5470:OpenSSH
5412:BitlBee
5358:Outlook
5353:Kontact
5347:Gpg4win
5252:Commons
5131:Airdrop
5110:IQ.Wiki
5075:Mt. Gox
5046:Defunct
5032:Uniswap
4992:Genesis
4927:Bithumb
4902:Binance
4874:OneCoin
4836:Stellar
4717:The DAO
4707:Polygon
4677:Aventus
4592:Cardano
4385:Titcoin
4350:Bitcoin
4341:SHA-256
3843:General
3628:Attacks
3558:SipHash
3514:CBC-MAC
3448:LM hash
3428:Balloon
3292:HAS-160
2656:Sources
2320:May 25,
2203:18 July
1842:Balloon
1490:SHA-256
1120:sha1sum
981:value.
729:attacks
588:= hash(
513:digital
241:) is a
94:scholar
6185:S/MIME
6032:StegFS
5942:GNUnet
5782:Signal
5730:Matrix
5578:SSLeay
5533:GnuTLS
5485:WinSCP
5437:Kopete
5388:Secure
5085:Thodex
5012:Kucoin
5007:Kraken
4987:Gemini
4957:Circle
4932:BitMEX
4917:Bitkub
4864:Coinye
4826:Ripple
4801:Helium
4765:Tether
4665:tokens
4663:ERC-20
4638:Solana
4597:EOS.IO
4501:-based
4489:Monero
4461:-based
4439:Coinye
4422:-based
4420:Scrypt
4397:-based
4395:Ethash
4343:-based
3954:Keygen
3788:Pepper
3727:NESSIE
3674:Design
3468:scrypt
3463:PBKDF2
3438:Catena
3433:bcrypt
3423:Argon2
3382:Snefru
3377:Shabal
3372:SWIFFT
3352:RIPEMD
3347:N-hash
3322:MASH-2
3317:MASH-1
3302:Kupyna
3262:BLAKE3
3245:Keccak
3230:Grøstl
3207:BLAKE2
3041:
3031:
3010:
2973:
2950:
2940:
2911:
2901:
2874:
2864:
2835:
2805:
2795:
2764:
2754:
2724:
2714:
2689:
2679:
2479:Forbes
2401:
1909:NESSIE
1899:MD5CRK
1838:argon2
1834:scrypt
1830:bcrypt
1826:pbkdf2
1710:BLAKE3
1704:BLAKE3
1697:Argon2
1687:BLAKE2
1681:BLAKE2
1459:, and
1457:Keccak
1432:SHACAL
1277:Keccak
1219:, and
1041:Argon2
1037:scrypt
1033:PBKDF2
803:SWIFFT
555:string
503:, for
96:
89:
82:
75:
67:
6088:Wuala
6062:Qubes
6057:Tails
6002:EncFS
5977:Wickr
5735:OMEMO
5702:Briar
5679:Zfone
5664:Jitsi
5568:BSAFE
5523:Botan
5475:PuTTY
5432:Jitsi
5427:climm
5407:Adium
5053:BTC-e
5037:Upbit
4997:Huobi
4982:eToro
4937:Bitso
4879:Petro
4760:Terra
4702:Minds
4672:Augur
4648:Tezos
4643:Steem
4604:(2.0)
4554:Verge
4522:Other
4513:Petro
4473:Zcash
4406:(1.0)
3984:(PRN)
3582:modes
3458:Makwa
3453:Lyra2
3443:crypt
3392:Tiger
3342:MDC-2
3297:HAVAL
3282:Fugue
3240:Skein
3225:BLAKE
3202:SHA-3
3197:SHA-2
3191:SHA-1
2242:(PDF)
2235:(PDF)
1929:SHA-3
1758:SHA-2
1665:SHA-3
1659:SHA-3
1650:AMD64
1639:SHA-2
1633:SHA-2
1583:SHA-1
1577:SHA-1
1513:SHA-1
1481:SHA-1
1453:Skein
1424:SHA-2
1420:SHA-1
1344:SHA-1
1273:BLAKE
1269:Skein
1265:SHA-3
1261:SHA-2
1257:SHA-1
1145:or a
1133:, an
975:spoof
959:HTTPS
943:SHA-2
941:, or
939:SHA-1
893:Alice
811:CRC32
764:hash(
733:hash(
680:hash(
628:hash(
196:SHA-3
192:SHA-2
188:SHA-1
184:SHA-0
138:SHA-1
101:JSTOR
87:books
6022:PEFS
6017:LUKS
5992:List
5887:LUKS
5882:geli
5877:GBDE
5674:Jami
5656:ZRTP
5641:Tinc
5538:JSSE
5264:List
5017:Kuna
4947:BTCC
4897:Abra
4816:Nano
4806:Luna
4786:Chia
4745:Diem
4722:TRON
4539:IOTA
4534:Firo
4508:Dash
4365:LBRY
4287:Web3
4262:Fork
3783:Salt
3747:CNSA
3614:IAPM
3568:VMAC
3563:UMAC
3548:PMAC
3543:CMAC
3539:OMAC
3534:NMAC
3529:HMAC
3524:GMAC
3493:HKDF
3362:SIMD
3312:Lane
3287:GOST
3272:ECOH
3159:List
3146:and
3039:OCLC
3029:ISBN
3008:ISBN
2971:ISBN
2948:ISSN
2938:ISBN
2909:ISSN
2899:ISBN
2872:ISSN
2862:ISBN
2833:ISBN
2803:ISSN
2793:ISBN
2762:ISSN
2752:ISBN
2722:ISSN
2712:ISBN
2687:ISSN
2677:ISBN
2567:2020
2540:2009
2459:2009
2399:ISBN
2322:2016
2205:2017
2099:2013
1884:HMAC
1518:For
1511:and
1477:SEAL
1440:LION
1438:and
1436:BEAR
1422:and
1405:HMAC
1374:and
1346:and
1259:and
1114:and
1086:and
1056:salt
929:file
787:HMAC
741:len(
739:and
669:and
342:The
73:news
6007:EFS
5957:Tor
5947:I2P
5857:E4M
5722:DRA
5712:Tox
5689:P2P
5603:VPN
5553:NSS
5465:lsh
5452:SSH
5399:OTR
5368:PGP
5363:p≡p
5343:GPG
5058:FTX
5022:OKX
4952:BUX
4821:NEO
4755:Pax
4740:Dai
4692:Kin
4653:TON
4623:Nxt
4618:Kin
4499:X11
3619:OCB
3609:GCM
3604:EAX
3599:CWC
3589:CCM
3519:DAA
3397:VSH
3367:SM3
3337:MD6
3332:MD4
3327:MD2
3307:LSH
3277:FSB
3185:MD5
2930:doi
2889:doi
2852:doi
2783:doi
2742:doi
2704:doi
2669:doi
2391:doi
2123:doi
1564:MD5
1558:MD5
1509:MD5
1348:MD5
1288:AES
1253:MD5
1249:MD4
1199:'s
1135:MD4
1108:Git
1039:or
935:MD5
897:Bob
819:WEP
247:map
245:(a
239:CHF
172:DSA
168:SHA
56:by
6230::
3235:JH
3065:.
3061:.
3037:.
3002:.
2979:.
2946:.
2936:.
2924:.
2907:.
2897:.
2870:.
2860:.
2809:.
2801:.
2791:.
2777:.
2760:.
2750:.
2720:.
2710:.
2685:.
2675:.
2618:.
2614:.
2588:.
2584:.
2526:.
2481:.
2477:.
2449:.
2445:.
2431:".
2397:,
2308:.
2281:^
2147:.
2135:^
2107:^
2089:.
2085:.
2047:.
1993:.
1978:.
1974:.
1840:,
1836:,
1832:,
1828:,
1732:.
1652:.
1554:.
1542:.
1475:.
1455:,
1442:.
1434:,
1271:,
1255:,
1251:,
1240:.
1215:,
1192:.
1110:,
1051:.
1035:,
937:,
931:.
768:∥
519:,
515:)
487:,
475:).
428:a
425:);
233:A
194:,
190:,
186:,
170:,
166:,
5994:)
5990:(
5819:)
5815:(
5349:)
5345:(
5299:e
5292:t
5285:v
4205:e
4198:t
4191:v
3828:e
3821:t
3814:v
3541:/
3136:e
3129:t
3122:v
3082:.
3045:.
3016:.
2990:.
2954:.
2932::
2915:.
2891::
2878:.
2854::
2841:.
2820:.
2785::
2768:.
2744::
2728:.
2706::
2693:.
2671::
2629:.
2599:.
2569:.
2542:.
2492:.
2461:.
2393::
2324:.
2291:.
2251:.
2220:.
2207:.
2162:.
2129:.
2125::
2101:.
2058:.
1535:n
1529:n
1223:.
1177:.
1092:2
880:n
874:n
779:∥
775:)
773:′
770:m
766:m
759:′
756:m
750:m
745:)
743:m
737:)
735:m
708:.
694:)
692:2
689:m
685:1
682:m
675:2
672:m
666:1
663:m
652:.
642:)
640:2
637:m
633:1
630:m
623:2
620:m
614:1
611:m
602:.
592:)
590:m
586:h
580:m
574:h
459:2
455:/
451:n
407:n
403:2
382:n
358:n
317:n
310:2
285:n
257:n
237:(
222:e
215:t
208:v
144:.
123:)
117:(
112:)
108:(
98:·
91:·
84:·
77:·
50:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.