256:
122:
403:
25:
246:
There is also the cultural onion which has seven layers to it including artifacts, behaviors, feelings, values, beliefs, worldview and ultimate allegiance. These layers organize a person's reality and life. The outer most layers are the most accessible while the in-depth ones are only accessible with
242:
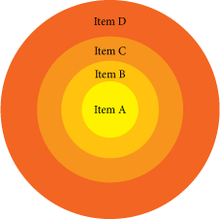
The onion diagram is able to show layers of a complete system in a few circles. Each of the circles is able to represent a component that is dependent upon the component on the inside of it shown by the circle inside of it. The main concept of the diagram is shown by the center circle of the diagram.
265:
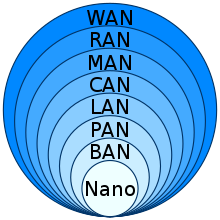
The onion model in computing is used as a metaphor for the complex structure of information systems. The system is split into layers to make it easier to understand. A simple example is to start with the program, operating system and hardware layers. Each of these layers can then be subdivided.
220:
156:
objects) is bisected by a plane that intersects the center or the innermost shell. The outer layers in the model typically add size and/or complexity, incrementally, around the inner layers they enclose.
200:
where in each case m > n). (Some applications of the concept, however, may fail to benefit from the mathematical and otherwise rigorous properties of the model.)
239:
among parts of an organization or process. The chart displays items in concentric circles, where the items in each ring depend on the items in the smaller rings.
247:
connections to the person. The seven layers are integrated into three structural levels, which are the foundational, the evaluating, and the actualizing level.
444:
243:
This chart is used due to the fact that it has a clear visual representation that is easy to read, and it has a strong visual impact.
330:
108:
437:
236:
46:
473:
89:
386:
137:
61:
42:
430:
255:
468:
68:
121:
35:
295:
126:
75:
354:
57:
280:
204:
463:
336:
326:
173:
414:
259:
290:
144:
and conceptual model for describing relationships among levels of a hierarchy, evoking a
82:
375:
300:
285:
275:
387:
https://www.slideshare.net/MdRokibulIslam2/mis-management-information-system-lecture-1
457:
165:
161:
402:
169:
24:
340:
219:
320:
208:
153:
145:
141:
410:
189:
184:(but perhaps potentially or conceptually infinite) where each set A
254:
232:
218:
149:
120:
18:
418:
49:. Unsourced material may be challenged and removed.
438:
8:
296:Social penetration theory § Onion model
281:Information security § Defense in depth
445:
431:
286:Learning cycle § Levels of reflection
109:Learn how and when to remove this message
325:. Indianapolis, IN: Wiley. p. 235.
148:of the layered "shells" exposed when an
311:
301:Start With Why § The golden circle
260:Computer network types by spatial scope
211:wizard invoke the term "stacked Venn".
16:Diagram of hierarchical relationships
7:
399:
397:
47:adding citations to reliable sources
172:diagram composed of a hierarchy of
417:. You can help Knowledge (XXG) by
14:
152:(or other concentric assembly of
401:
223:A template for an onion diagram.
23:
34:needs additional citations for
1:
357:. End Violence Against Women
355:"Rainbow and onion diagrams"
196:(and by recursion, of all A
490:
396:
203:Such formats supported by
164:can be represented as an
127:social penetration theory
319:Biafore, Bonnie (2004).
125:An onion model used in
413:-related article is a
262:
224:
129:
258:
222:
124:
474:Systems theory stubs
205:Microsoft PowerPoint
43:improve this article
263:
225:
130:
469:Scientific models
426:
425:
376:The Culture Onion
119:
118:
111:
93:
481:
447:
440:
433:
405:
398:
389:
384:
378:
373:
367:
366:
364:
362:
351:
345:
344:
322:Visio 2003 Bible
316:
114:
107:
103:
100:
94:
92:
51:
27:
19:
489:
488:
484:
483:
482:
480:
479:
478:
454:
453:
452:
451:
394:
392:
385:
381:
374:
370:
360:
358:
353:
352:
348:
333:
318:
317:
313:
309:
291:Matryoshka doll
272:
253:
235:that shows the
217:
199:
195:
187:
183:
179:
115:
104:
98:
95:
52:
50:
40:
28:
17:
12:
11:
5:
487:
485:
477:
476:
471:
466:
456:
455:
450:
449:
442:
435:
427:
424:
423:
406:
391:
390:
379:
368:
346:
331:
310:
308:
305:
304:
303:
298:
293:
288:
283:
278:
276:Onion (Arendt)
271:
268:
252:
249:
216:
213:
197:
193:
185:
181:
177:
117:
116:
31:
29:
22:
15:
13:
10:
9:
6:
4:
3:
2:
486:
475:
472:
470:
467:
465:
462:
461:
459:
448:
443:
441:
436:
434:
429:
428:
422:
420:
416:
412:
407:
404:
400:
395:
388:
383:
380:
377:
372:
369:
356:
350:
347:
342:
338:
334:
332:0-7645-7294-6
328:
324:
323:
315:
312:
306:
302:
299:
297:
294:
292:
289:
287:
284:
282:
279:
277:
274:
273:
269:
267:
261:
257:
250:
248:
244:
240:
238:
234:
231:is a kind of
230:
229:onion diagram
221:
214:
212:
210:
206:
201:
191:
175:
171:
167:
163:
162:onion diagram
158:
155:
151:
147:
143:
139:
135:
128:
123:
113:
110:
102:
91:
88:
84:
81:
77:
74:
70:
67:
63:
60: –
59:
58:"Onion model"
55:
54:Find sources:
48:
44:
38:
37:
32:This article
30:
26:
21:
20:
419:expanding it
408:
393:
382:
371:
359:. Retrieved
349:
321:
314:
264:
251:In computing
245:
241:
237:dependencies
228:
226:
202:
188:is a strict
159:
133:
131:
105:
96:
86:
79:
72:
65:
53:
41:Please help
36:verification
33:
215:In business
134:onion model
458:Categories
361:17 October
307:References
154:spheroidal
99:April 2018
69:newspapers
464:Diagrams
341:55217040
270:See also
209:SmartArt
146:metaphor
411:systems
142:diagram
140:-based
83:scholar
339:
329:
190:subset
85:
78:
71:
64:
56:
409:This
233:chart
166:Euler
150:onion
138:graph
136:is a
90:JSTOR
76:books
415:stub
363:2013
337:OCLC
327:ISBN
192:of A
180:...A
174:sets
170:Venn
132:The
62:news
227:An
207:'s
186:n+1
176:, A
168:or
160:An
45:by
460::
335:.
446:e
439:t
432:v
421:.
365:.
343:.
198:m
194:n
182:k
178:1
112:)
106:(
101:)
97:(
87:·
80:·
73:·
66:·
39:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.