314:
36:
179:
344:
are assumed to have been killed or executed in a foreign country while serving as NOC agents. In nations with established and well-developed spy agencies, the majority of captured non-native NOC agents have, however, historically been repatriated through
364:
The degree of sophistication put into non-official cover stories varies considerably. Sometimes, an agent will simply be appointed to a position in a well-established company which can provide the appropriate opportunities. Other times, entire
356:
Some countries have regulations regarding the use of non-official cover: the CIA, for example, has at times been prohibited from disguising agents as members of certain aid organizations, or as members of the
194:
operative is one who assumes a position in an organization with diplomatic ties to the government for which the operative works such as an embassy or consulate. This provides the agent with official
198:, thus protecting them from the steep punishments normally meted out to captured spies. Upon discovery of an official cover agent's secret hostile role, the host nation often declares the agent
329:
An agent sent to spy on a foreign country might, for instance, work as a businessperson, a worker for a non-profit organization (such as a humanitarian group), or an academic. For example, the
1322:
1535:
1086:
313:
1332:
629:
53:
258:, but also denying them any hope of diplomatic legal assistance – or official acknowledgment of their service. Such an operative or agent may be referred to as a
1465:
1129:
1112:
1079:
984:
155:
1528:
1169:
294:
1357:
1327:
1072:
967:
923:
571:
443:
1510:
431:
1159:
918:
100:
72:
673:
1103:
246:
if their espionage activities are discovered. Operatives under non-official cover do not have this "safety net", and if captured and
819:
282:
119:
79:
377:
1460:
1452:
854:
779:
455:
207:
Official cover operatives are granted a set of governmental protections, and if caught in the act of espionage, they can request
1470:
473:
86:
1401:
1141:
254:. Operatives under non-official cover are also usually trained to deny any connection with their government, thus preserving
57:
400:
officer "Nicholas
Anderson" wrote an account of his service in a fictionalized autobiography (as per British law) entitled
1556:
1095:
509:
415:
68:
238:
This is in contrast to an operative with official cover, where they assume a position in their government, such as the
1518:
605:
381:
133:
211:
from their government. In other words, official cover operatives are agents officially recognized by their country.
461:
46:
1433:
1164:
350:
1485:
1475:
1423:
1154:
804:
774:
666:
1561:
1500:
1438:
1418:
1367:
1124:
479:
93:
1387:
1053:
373:
255:
208:
148:
1490:
1428:
1314:
1270:
1255:
1204:
1149:
979:
962:
935:
698:
582:
1523:
1397:
1214:
1041:
945:
527:
521:
424:
The
Volunteer: The Incredible True Story of an Israeli Spy on the Trail of International Terrorists
243:
195:
159:
152:
1495:
1480:
1372:
1347:
1285:
1236:
1221:
930:
897:
871:
849:
844:
814:
799:
659:
503:
485:
366:
162:
is the ostensible identity and/or role or position in an infiltrated organization assumed by a
1337:
1046:
715:
427:
346:
341:
318:
200:
1392:
1342:
1011:
743:
540:
325:
during the Second World War; it gave her the alias of a
Frenchwoman named Marcelle Montagne.
265:
232:
167:
1280:
1209:
1031:
1006:
940:
902:
839:
630:"Our Kind of Traitor: an interview with former MI6 intelligence officer Nicholas Anderson"
576:
545:
298:
231:) are operatives without official ties to the government for which they work who assume
1377:
1197:
709:
515:
1550:
1295:
1275:
1260:
989:
957:
859:
834:
753:
550:
491:
449:
334:
322:
441:, who made a satirical claim to have been a NOC with 33 kills in his book and movie
1382:
1300:
1290:
1231:
1036:
824:
809:
748:
733:
726:
438:
385:
163:
1192:
1026:
892:
738:
497:
302:
35:
17:
1265:
1021:
1001:
994:
974:
881:
422:
officer, operated as a Mossad NOC or "combatant" as described in his memoir,
1246:
1241:
1187:
1179:
1016:
829:
758:
693:
682:
251:
247:
220:
187:
144:
27:
Ostensible identity in an infiltrated organization assumed by a covert agent
1064:
305:
entities are established in order to provide false identities for agents.
1250:
864:
467:
340:
Many of the agents memorialized without names or dates of service on the
239:
178:
950:
419:
358:
369:
can be established in order to provide false identities for agents.
312:
177:
250:
are subject to severe criminal punishments, up to and including
1068:
655:
182:
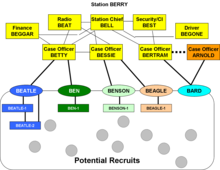
Representative clandestine operations run from diplomatic cover
397:
330:
29:
651:
271:
1536:
Counterintelligence and counter-terrorism organizations
410:
NOC Three Times: Knock-On Effect (Last of the
Trilogy)
283:
274:
268:
1509:
1451:
1411:
1356:
1313:
1178:
1140:
1111:
1102:
911:
880:
790:
767:
689:
60:. Unsourced material may be challenged and removed.
581:
402:NOC: Non-Official Cover: British Secret Operations
384:investigations and made public as a result of the
132:"Undercover" redirects here. For other uses, see
406:NOC Twice: More UK Non-Official Cover Operations
376:, used by the CIA during the Vietnam War, and
1080:
667:
8:
447:. Other examples are featured in the books
1117:
1108:
1087:
1073:
1065:
674:
660:
652:
606:"Tripping Over CIA's Bureaucratic Hurdles"
295:Clandestine HUMINT operational techniques
120:Learn how and when to remove this message
1501:Scientific & Technical intelligence
636:. Immediate Media Company. May 11, 2016
562:
924:Chinese espionage in the United States
426:(Skyhorse Publishing, September 2007,
204:and orders them to leave the country.
570:Shannon, Elaine (February 20, 1995).
349:for other captured NOCs as a form of
7:
1323:By alliances, nations and industries
919:Chinese intelligence activity abroad
58:adding citations to reliable sources
985:Interpersonal (HUMINT) intelligence
437:Fictional notable examples include
337:spent nearly two decades as a NOC.
69:"Cover" intelligence gathering
604:John Weisman (September 7, 2010).
378:Brewster Jennings & Associates
25:
820:Computer and network surveillance
855:Short-range agent communications
264:
34:
1471:Words of estimative probability
1333:Operational platforms by nation
444:Confessions of a Dangerous Mind
45:needs additional citations for
1:
572:"Spies for the New Disorder"
1519:Intelligence cycle security
489:; and the television shows
242:, which provides them with
134:Undercover (disambiguation)
1578:
131:
1120:
456:The Eleventh Commandment
235:roles in organizations.
1486:Intelligence assessment
1476:All-source intelligence
1096:Intelligence management
805:Covert listening device
775:Intelligence assessment
1170:Operational techniques
1125:Special reconnaissance
326:
183:
1054:Targeted surveillance
380:, used by the CIA in
351:gentlemen's agreement
316:
256:plausible deniability
209:diplomatic protection
181:
1557:Covert organizations
1491:Medical intelligence
1461:Competing hypotheses
1271:Industrial espionage
1256:Denial and deception
980:Industrial espionage
780:competing hypotheses
54:improve this article
1524:Counterintelligence
1439:Technical (TECHINT)
1434:Open-source (OSINT)
1424:Geospatial (GEOINT)
1398:Casualty estimation
586:on January 14, 2009
474:The Bourne Identity
462:Mission: Impossible
404:, and two sequels:
244:diplomatic immunity
223:, operatives under
196:diplomatic immunity
160:counterintelligence
1496:Military geography
1481:Basic intelligence
1419:Financial (FININT)
1360:signature (MASINT)
1286:One-way voice link
1222:Concealment device
931:Cold War espionage
898:Front organization
872:Surveillance tools
850:Phone surveillance
845:One-way voice link
800:Concealment device
347:prisoner exchanges
327:
240:diplomatic service
225:non-official cover
215:Non-official cover
184:
156:human intelligence
1544:
1543:
1447:
1446:
1338:Direction finding
1328:In modern history
1309:
1308:
1062:
1061:
716:Agent provocateur
510:The Night Manager
432:978-1-60239-132-1
372:Examples include
342:CIA Memorial Wall
319:birth certificate
201:persona non grata
130:
129:
122:
104:
16:(Redirected from
1569:
1343:Traffic analysis
1315:Signals (SIGINT)
1150:Asset recruiting
1118:
1109:
1089:
1082:
1075:
1066:
676:
669:
662:
653:
646:
645:
643:
641:
634:historyextra.com
626:
620:
619:
617:
616:
610:Washington Times
601:
595:
594:
592:
591:
585:
580:. Archived from
567:
541:Illegals Program
286:
281:
280:
277:
276:
273:
270:
248:charged as spies
168:covert operation
125:
118:
114:
111:
105:
103:
62:
38:
30:
21:
18:Diplomatic cover
1577:
1576:
1572:
1571:
1570:
1568:
1567:
1566:
1547:
1546:
1545:
1540:
1505:
1443:
1429:Imagery (IMINT)
1407:
1368:Electro-optical
1359:
1358:Measurement and
1352:
1305:
1281:Numbers station
1210:Black operation
1174:
1136:
1098:
1093:
1063:
1058:
1032:Sting operation
941:Black operation
907:
903:Limited hangout
885:
876:
840:Numbers station
792:
786:
763:
703:
685:
680:
650:
649:
639:
637:
628:
627:
623:
614:
612:
603:
602:
598:
589:
587:
569:
568:
564:
559:
546:Secret identity
537:
394:
367:front companies
311:
299:front companies
284:
267:
263:
217:
176:
137:
126:
115:
109:
106:
63:
61:
51:
39:
28:
23:
22:
15:
12:
11:
5:
1575:
1573:
1565:
1564:
1559:
1549:
1548:
1542:
1541:
1539:
1538:
1533:
1532:
1531:
1521:
1515:
1513:
1507:
1506:
1504:
1503:
1498:
1493:
1488:
1483:
1478:
1473:
1468:
1466:Target-centric
1463:
1457:
1455:
1449:
1448:
1445:
1444:
1442:
1441:
1436:
1431:
1426:
1421:
1415:
1413:
1409:
1408:
1406:
1405:
1395:
1390:
1388:Radiofrequency
1385:
1380:
1375:
1370:
1364:
1362:
1354:
1353:
1351:
1350:
1345:
1340:
1335:
1330:
1325:
1319:
1317:
1311:
1310:
1307:
1306:
1304:
1303:
1298:
1293:
1288:
1283:
1278:
1273:
1268:
1263:
1258:
1253:
1244:
1239:
1234:
1229:
1224:
1219:
1218:
1217:
1207:
1202:
1201:
1200:
1195:
1184:
1182:
1176:
1175:
1173:
1172:
1167:
1162:
1157:
1152:
1146:
1144:
1138:
1137:
1135:
1134:
1133:
1132:
1121:
1115:
1113:Human (HUMINT)
1106:
1100:
1099:
1094:
1092:
1091:
1084:
1077:
1069:
1060:
1059:
1057:
1056:
1051:
1050:
1049:
1044:
1034:
1029:
1024:
1019:
1014:
1009:
1004:
999:
998:
997:
992:
982:
977:
972:
971:
970:
965:
955:
954:
953:
948:
938:
933:
928:
927:
926:
915:
913:
909:
908:
906:
905:
900:
895:
889:
887:
878:
877:
875:
874:
869:
868:
867:
857:
852:
847:
842:
837:
832:
827:
822:
817:
812:
807:
802:
796:
794:
793:communications
788:
787:
785:
784:
783:
782:
771:
769:
765:
764:
762:
761:
756:
751:
746:
741:
736:
731:
730:
729:
719:
712:
710:Agent handling
706:
704:
702:
701:
696:
690:
687:
686:
681:
679:
678:
671:
664:
656:
648:
647:
621:
596:
561:
560:
558:
555:
554:
553:
548:
543:
536:
533:
516:Covert Affairs
393:
390:
310:
307:
297:). Sometimes,
216:
213:
192:official cover
175:
174:Official cover
172:
128:
127:
42:
40:
33:
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
1574:
1563:
1562:Spies by role
1560:
1558:
1555:
1554:
1552:
1537:
1534:
1530:
1529:organizations
1527:
1526:
1525:
1522:
1520:
1517:
1516:
1514:
1512:
1511:Dissemination
1508:
1502:
1499:
1497:
1494:
1492:
1489:
1487:
1484:
1482:
1479:
1477:
1474:
1472:
1469:
1467:
1464:
1462:
1459:
1458:
1456:
1454:
1450:
1440:
1437:
1435:
1432:
1430:
1427:
1425:
1422:
1420:
1417:
1416:
1414:
1410:
1403:
1399:
1396:
1394:
1391:
1389:
1386:
1384:
1381:
1379:
1376:
1374:
1371:
1369:
1366:
1365:
1363:
1361:
1355:
1349:
1346:
1344:
1341:
1339:
1336:
1334:
1331:
1329:
1326:
1324:
1321:
1320:
1318:
1316:
1312:
1302:
1299:
1297:
1296:Steganography
1294:
1292:
1289:
1287:
1284:
1282:
1279:
1277:
1276:Interrogation
1274:
1272:
1269:
1267:
1264:
1262:
1261:Eavesdropping
1259:
1257:
1254:
1252:
1248:
1245:
1243:
1240:
1238:
1235:
1233:
1230:
1228:
1225:
1223:
1220:
1216:
1213:
1212:
1211:
1208:
1206:
1203:
1199:
1196:
1194:
1191:
1190:
1189:
1186:
1185:
1183:
1181:
1177:
1171:
1168:
1166:
1165:Direct action
1163:
1161:
1160:Covert action
1158:
1156:
1153:
1151:
1148:
1147:
1145:
1143:
1139:
1131:
1130:organizations
1128:
1127:
1126:
1123:
1122:
1119:
1116:
1114:
1110:
1107:
1105:
1101:
1097:
1090:
1085:
1083:
1078:
1076:
1071:
1070:
1067:
1055:
1052:
1048:
1045:
1043:
1040:
1039:
1038:
1035:
1033:
1030:
1028:
1025:
1023:
1020:
1018:
1015:
1013:
1010:
1008:
1005:
1003:
1000:
996:
993:
991:
990:interrogation
988:
987:
986:
983:
981:
978:
976:
973:
969:
966:
964:
961:
960:
959:
958:Eavesdropping
956:
952:
949:
947:
944:
943:
942:
939:
937:
934:
932:
929:
925:
922:
921:
920:
917:
916:
914:
910:
904:
901:
899:
896:
894:
891:
890:
888:
883:
879:
873:
870:
866:
863:
862:
861:
860:Steganography
858:
856:
853:
851:
848:
846:
843:
841:
838:
836:
835:Invisible ink
833:
831:
828:
826:
823:
821:
818:
816:
813:
811:
808:
806:
803:
801:
798:
797:
795:
789:
781:
778:
777:
776:
773:
772:
770:
766:
760:
757:
755:
754:Sleeper agent
752:
750:
747:
745:
742:
740:
737:
735:
732:
728:
725:
724:
723:
720:
718:
717:
713:
711:
708:
707:
705:
700:
697:
695:
692:
691:
688:
684:
677:
672:
670:
665:
663:
658:
657:
654:
635:
631:
625:
622:
611:
607:
600:
597:
584:
579:
578:
573:
566:
563:
556:
552:
551:Sleeper agent
549:
547:
544:
542:
539:
538:
534:
532:
530:
529:
524:
523:
518:
517:
512:
511:
506:
505:
500:
499:
494:
493:
492:The Americans
488:
487:
482:
481:
476:
475:
470:
469:
464:
463:
458:
457:
452:
451:
450:Debt of Honor
446:
445:
440:
435:
433:
429:
425:
421:
417:
413:
411:
407:
403:
399:
391:
389:
387:
383:
379:
375:
370:
368:
362:
360:
354:
352:
348:
343:
338:
336:
335:Ishmael Jones
332:
324:
323:Virginia Hall
320:
315:
308:
306:
304:
300:
296:
292:
288:
287:
279:
261:
257:
253:
249:
245:
241:
236:
234:
230:
226:
222:
214:
212:
210:
205:
203:
202:
197:
193:
189:
180:
173:
171:
169:
165:
161:
157:
154:
150:
146:
142:
135:
124:
121:
113:
102:
99:
95:
92:
88:
85:
81:
78:
74:
71: –
70:
66:
65:Find sources:
59:
55:
49:
48:
43:This article
41:
37:
32:
31:
19:
1301:Surveillance
1291:Resident spy
1232:Cryptography
1226:
1037:Surveillance
825:Cyber spying
810:Cryptography
749:Resident spy
734:Double agent
721:
714:
640:February 21,
638:. Retrieved
633:
624:
613:. Retrieved
609:
599:
588:. Retrieved
583:the original
575:
565:
526:
520:
514:
508:
502:
496:
490:
484:
478:
472:
466:
460:
459:; the films
454:
448:
442:
439:Chuck Barris
436:
423:
416:Michael Ross
414:
409:
405:
401:
395:
386:Plame affair
371:
363:
355:
339:
328:
290:
262:(pronounced
259:
237:
228:
224:
218:
206:
199:
191:
185:
164:covert agent
140:
138:
116:
107:
97:
90:
83:
76:
64:
52:Please help
47:verification
44:
1373:Geophysical
1155:Cell system
1142:Clandestine
1027:Stay-behind
936:Recruitment
893:Canary trap
791:Devices and
739:Field agent
498:Burn Notice
486:The Recruit
418:, a former
374:Air America
289:) or as an
1551:Categories
1402:earthquake
1266:False flag
1104:Collection
1022:Sexpionage
1002:COINTELPRO
995:safe house
975:False flag
912:Operations
886:techniques
882:Tradecraft
615:2010-03-19
590:2008-02-19
557:References
480:Safe House
110:March 2017
80:newspapers
1393:Materials
1247:Defection
1242:Dead drop
1215:black bag
1180:Espionage
946:black bag
830:Dead drop
759:Spymaster
683:Espionage
252:execution
221:espionage
188:espionage
166:during a
1453:Analysis
1251:Turncoat
1198:handling
1012:SHAMROCK
865:microdot
768:Analysis
535:See also
468:Spy Game
392:Examples
321:used by
303:strawman
149:military
1400: (
1378:Nuclear
1348:TEMPEST
1007:MINARET
951:wetwork
528:Patriot
522:The Spy
396:Former
309:History
291:illegal
145:foreign
94:scholar
1237:Cutout
1188:Agents
1042:Global
968:MASINT
963:SIGINT
815:Cutout
699:Assets
694:Agents
525:, and
504:Spooks
483:, and
430:
420:Mossad
359:clergy
233:covert
153:police
96:
89:
82:
75:
67:
1412:Other
1383:Radar
1227:Cover
1205:Asset
1193:field
727:Agent
722:Cover
317:Fake
293:(see
190:, an
141:cover
101:JSTOR
87:books
1047:Mass
1017:FVEY
744:Mole
642:2018
577:Time
453:and
428:ISBN
408:and
73:news
884:and
434:).
398:MI6
382:WMD
333:'s
331:CIA
301:or
285:NOK
260:NOC
229:NOC
219:In
186:In
158:or
151:or
143:in
56:by
1553::
1249:/
632:.
608:.
574:.
531:.
519:,
513:,
507:,
501:,
495:,
477:,
471:,
465:,
412:.
388:.
361:.
353:.
170:.
147:,
139:A
1404:)
1088:e
1081:t
1074:v
675:e
668:t
661:v
644:.
618:.
593:.
278:/
275:k
272:ɒ
269:n
266:/
227:(
136:.
123:)
117:(
112:)
108:(
98:·
91:·
84:·
77:·
50:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.