25:
279:, p0f does not generate traffic. Instead, it determines the operating system of the remote host by analyzing certain fields in the captured packets. This can have benefits in environments where actively creating network traffic would cause unhelpful side effects. In particular, the remote system will not be able to detect the packet capture and inspection.
129:
267:
By inspecting network traffic passively, p0f can attempt to identify the operating systems on remote machines that send TCP packets to the detecting machine's network interface, or to a physical subnet that the detecting machine can listen on. Since version 3, p0f is also able to deduce aspects of
287:
Signatures used for packet inspection are stored in a simple text file. This allows them to be modified without recompiling p0f. The user is allowed to use a different fingerprinting file by selecting another one at
271:
p0f can also check for firewall presence. It can estimate the distance to a remote system and calculate its uptime. It also guesses the remote system's means of connecting to the network (DSL, OC3, etc.).
255:
tool. p0f can attempt to identify the system running on machines that send network traffic to the box it is running on, or to a machine that
289:
108:
390:
46:
385:
252:
220:
159:
89:
61:
188:
35:
68:
259:
with the machine it is running on. p0f can also assist in analysing other aspects of the remote system.
75:
42:
215:
148:
57:
208:
195:
379:
256:
296:
82:
24:
143:
204:
343:
368:
322:
231:
200:
268:
the remote system by inspecting application-level HTTP messages.
295:
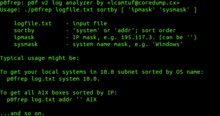
p0f does not use a graphical user interface: it is run from the
276:
128:
18:
226:
214:
194:
184:
158:
142:
134:
49:. Unsourced material may be challenged and removed.
8:
317:
315:
313:
311:
121:
127:
120:
109:Learn how and when to remove this message
307:
7:
47:adding citations to reliable sources
14:
23:
16:TCP/IP stack fingerprinting tool
344:"p0f v3: passive fingerprinter"
34:needs additional citations for
1:
165:3.09b / 18 April 2016
253:TCP/IP stack fingerprinting
221:TCP/IP stack fingerprinting
407:
180:
154:
126:
391:Unix security software
167:; 8 years ago
43:improve this article
123:
386:Internet protocols
275:Unlike tools like
246:
245:
209:Microsoft Windows
119:
118:
111:
93:
398:
372:
371:
369:Official website
355:
354:
352:
350:
340:
334:
333:
331:
329:
319:
242:
239:
237:
235:
233:
196:Operating system
175:
173:
168:
136:
131:
124:
114:
107:
103:
100:
94:
92:
51:
27:
19:
406:
405:
401:
400:
399:
397:
396:
395:
376:
375:
367:
366:
363:
358:
348:
346:
342:
341:
337:
327:
325:
321:
320:
309:
305:
285:
265:
257:shares a medium
230:
176:
171:
169:
166:
149:Michał Zalewski
138:
115:
104:
98:
95:
52:
50:
40:
28:
17:
12:
11:
5:
404:
402:
394:
393:
388:
378:
377:
374:
373:
362:
361:External links
359:
357:
356:
335:
306:
304:
301:
284:
281:
264:
261:
244:
243:
228:
224:
223:
218:
212:
211:
198:
192:
191:
186:
182:
181:
178:
177:
164:
162:
160:Stable release
156:
155:
152:
151:
146:
140:
139:
132:
117:
116:
31:
29:
22:
15:
13:
10:
9:
6:
4:
3:
2:
403:
392:
389:
387:
384:
383:
381:
370:
365:
364:
360:
345:
339:
336:
324:
318:
316:
314:
312:
308:
302:
300:
298:
293:
291:
282:
280:
278:
273:
269:
262:
260:
258:
254:
251:is a passive
250:
241:
229:
225:
222:
219:
217:
213:
210:
206:
202:
199:
197:
193:
190:
187:
183:
179:
163:
161:
157:
153:
150:
147:
145:
141:
130:
125:
113:
110:
102:
91:
88:
84:
81:
77:
74:
70:
67:
63:
60: –
59:
55:
54:Find sources:
48:
44:
38:
37:
32:This article
30:
26:
21:
20:
347:. Retrieved
338:
326:. Retrieved
297:command line
294:
286:
274:
270:
266:
248:
247:
144:Developer(s)
105:
96:
86:
79:
72:
65:
53:
41:Please help
36:verification
33:
380:Categories
303:References
185:Written in
172:2016-04-18
99:April 2010
69:newspapers
234:.coredump
205:Macintosh
349:13 April
328:13 April
323:"p0f v3"
299:prompt.
290:run time
263:Overview
232:lcamtuf
227:Website
170: (
137:command
83:scholar
85:
78:
71:
64:
56:
283:Usage
238:/p0f3
201:Linux
90:JSTOR
76:books
58:"P0f"
351:2017
330:2017
277:nmap
216:Type
133:The
62:news
249:p0f
236:.cx
135:p0f
122:p0f
45:by
382::
310:^
292:.
207:,
203:,
353:.
332:.
240:/
189:C
174:)
112:)
106:(
101:)
97:(
87:·
80:·
73:·
66:·
39:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.