501:) are available. In theory, TLS could choose appropriate ciphers since SSLv3, but in everyday practice many implementations refused to offer forward secrecy or only provided it with very low encryption grade. This is no longer the case with TLS 1.3, which ensures forward secrecy by leaving ephemeral Diffie–Hellman (finite field and elliptic curve variants) as the only remaining key exchange mechanism.
181:
362:
in non-interactive key exchange, and, as forward security is a desirable property in a key exchange protocol, in non-interactive forward secrecy. This combination has been identified as desirable since at least 1996. However, combining forward secrecy and non-interactivity has proven challenging; it had been suspected that forward secrecy with protection against
433:
Weak perfect forward secrecy (Wpfs) is the weaker property whereby when agents' long-term keys are compromised, the secrecy of previously established session-keys is guaranteed, but only for sessions in which the adversary did not actively interfere. This new notion, and the distinction between this
361:
implementation, rather than requiring sender and recipient to be online at the same time; loosening the bidirectionality requirement can also improve performance even where it is not a strict requirement, for example at connection establishment or resumption. These use cases have stimulated interest
102:
The value of forward secrecy is that it protects past communication. This reduces the motivation for attackers to compromise keys. For instance, if an attacker learns a long-term key, but the compromise is detected and the long-term key is revoked and updated, relatively little information is leaked
78:
of the server. Forward secrecy protects past sessions against future compromises of keys or passwords. By generating a unique session key for every session a user initiates, the compromise of a single session key will not affect any data other than that exchanged in the specific session protected by
119:
to prevent reading past traffic. The ephemeral Diffie–Hellman key exchange is often signed by the server using a static signing key. If an adversary can steal (or obtain through a court order) this static (long term) signing key, the adversary can masquerade as the server to the client and as the
284:
Forward secrecy (achieved by generating new session keys for each message) ensures that past communications cannot be decrypted if one of the keys generated in an iteration of step 2 is compromised, since such a key is only used to encrypt a single message. Forward secrecy also ensures that past
114:
The value of forward secrecy is limited not only by the assumption that an adversary will attack a server by only stealing keys and not modifying the random number generator used by the server but it is also limited by the assumption that the adversary will only passively collect traffic on the
106:
The value of forward secrecy depends on the assumed capabilities of an adversary. Forward secrecy has value if an adversary is assumed to be able to obtain secret keys from a device (read access) but is either detected or unable to modify the way session keys are generated in the device (full
568:
At WWDC 2016, Apple announced that all iOS apps would need to use App
Transport Security (ATS), a feature which enforces the use of HTTPS transmission. Specifically, ATS requires the use of an encryption cipher that provides forward secrecy. ATS became mandatory for apps on January 1, 2017.
321:
attack, an attacker in control of the network may itself store messages while preventing them from reaching the intended recipient; as the messages are never received, the corresponding private keys may not be destroyed or punctured, so a compromise of the private key can lead to successful
301:
being used, since a cryptanalysis consists of finding a way to decrypt an encrypted message without the key, and forward secrecy only protects keys, not the ciphers themselves. A patient attacker can capture a conversation whose confidentiality is protected through the use of
94:
security bug. If forward secrecy is used, encrypted communications and sessions recorded in the past cannot be retrieved and decrypted should long-term secret keys or passwords be compromised in the future, even if the adversary actively interfered, for example via a
564:
also provide forward secrecy. TLS 1.3, published in August 2018, dropped support for ciphers without forward secrecy. As of
February 2019, 96.6% of web servers surveyed support some form of forward secrecy, and 52.1% will use forward secrecy with most browsers.
166:
An encryption system has the property of forward secrecy if plain-text (decrypted) inspection of the data exchange that occurs during key agreement phase of session initiation does not reveal the key that was used to encrypt the remainder of the session.
434:
and forward secrecy was introduced by Hugo
Krawczyk in 2005. This weaker definition implicitly requires that full (perfect) forward secrecy maintains the secrecy of previously established session keys even in sessions where the adversary
31:
380:
With pre-computed keys, many key pairs are created and the public keys shared, with the private keys destroyed after a message has been received using the corresponding public key. This approach has been deployed as part of the
285:
communications cannot be decrypted if the long-term private keys from step 1 are compromised. However, masquerading as Alice or Bob would be possible going forward if this occurred, possibly compromising all future messages.
424:
to use a 0-RTT forward secure and replay-resistant key exchange implemented with puncturable encryption incurred significantly increased resource usage, but not so much as to make practical use infeasible.
293:
Forward secrecy is designed to prevent the compromise of a long-term secret key from affecting the confidentiality of past conversations. However, forward secrecy cannot defend against a successful
537:
Forward secrecy is seen as an important security feature by several large
Internet information providers. Since late 2011, Google provided forward secrecy with TLS by default to users of its
342:, requiring bidirectional communication between the parties. A protocol that permits the sender to transmit data without first needing to receive any replies from the recipient may be called
388:
In puncturable encryption, the recipient modifies their private key after receiving a message in such a way that the new private key cannot read the message but the public key is unchanged.
79:
that particular key. This by itself is not sufficient for forward secrecy which additionally requires that a long-term secret compromise does not affect the security of past session keys.
108:
107:
compromise). In some cases an adversary who can read long-term keys from a device may also be able to modify the functioning of the session key generator, as in the backdoored
1708:
151:
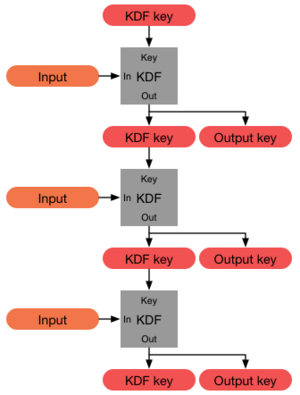
38:(KDF) can help achieve Forward Secrecy. A KDF is a one-way function that generates a new key from the current key. Leaking a key does not allow discovery of prior keys.
280:
The process repeats for each new message sent, starting from step 2 (and switching Alice and Bob's roles as sender/receiver as appropriate). Step 1 is never repeated.
1420:
650:
326:
attack, the attacker sends many messages to the recipient and exhausts the private key material, forcing a protocol to choose between failing closed (and enabling
1984:
1860:
400:, which modifies the private key according to a schedule so that messages sent in previous periods cannot be read with the private key from a later period.
1805:
253:
in person or over an already-authenticated channel. Verification establishes with confidence that the claimed owner of a public key is the actual owner.
1811:
1683:
Dallmeier, Fynn; Drees, Jan P.; Gellert, Kai; Handrik, Tobias; Jager, Tibor; Klauke, Jonas; Nachtigall, Simon; Renzelmann, Timo; Wolf, Rudi (2020).
1229:
Unger, Nik; Dechand, Sergej; Bonneau, Joseph; Fahl, Sascha; Perl, Henning; Goldberg, Ian; Smith, Matthew (17–21 May 2015). "SoK: Secure
Messaging".
111:. If an adversary can make the random number generator predictable, then past traffic will be protected but all future traffic will be compromised.
583:
Forward secrecy is supported on 92.6% of websites on modern browsers, while 0.3% of websites do not support forward secrecy at all as of May 2024.
1360:
1955:
1799:
405:
1586:
1556:
1251:
1066:
868:
702:
1148:
140:
2256:
2077:
1893:
1536:
602:
508:
490:
2291:
1999:
1787:
1758:
228:
317:
Non-interactive forward-secure key exchange protocols face additional threats that are not relevant to interactive protocols. In a
2286:
2220:
202:
1720:
1667:
597:
257:
116:
1912:
1188:
357:
Interactivity is onerous for some applications—for example, in a secure messaging system, it may be desirable to have a
158:, which establishes the related one-party and two-party forward secrecy properties of various standard key agreement schemes.
2225:
1822:
1714:
542:
462:
which provides additional features such as multi-user functionality in such clients, both provide forward secrecy as well as
206:
576:
messaging application employs forward secrecy in its protocol, notably differentiating it from messaging protocols based on
557:
have all provided forward secrecy to users since July 2014 and are requiring the use of forward secrecy since August 2018.
1459:
70:
will not be compromised even if long-term secrets used in the session key exchange are compromised, limiting damage. For
2037:
2007:
1906:
2017:
1887:
486:
314:
to be computed quickly). This would allow the recovery of old plaintexts even in a system employing forward secrecy.
191:
115:
communications link and not be active using a man-in-the-middle attack. Forward secrecy typically uses an ephemeral
560:
Facebook reported as part of an investigation into email encryption that, as of May 2014, 74% of hosts that support
2198:
1961:
607:
409:
311:
1083:
210:
195:
2057:
1989:
1928:
322:
decryption. Proactively retiring private keys on a schedule mitigates, but does not eliminate, this attack. In a
1391:
136:, and Michael James Wiener in 1992 where it was used to describe a property of the Station-to-Station protocol.
2178:
2141:
2108:
1781:
1767:
519:
470:
455:
96:
1051:. Advances in Cryptology – CRYPTO 2005. Lecture Notes in Computer Science. Vol. 3621. pp. 546–566.
241:
The following is a hypothetical example of a simple instant messaging protocol that employs forward secrecy:
2281:
1939:
1923:
1828:
303:
250:
246:
75:
35:
1918:
1882:
1793:
1098:
785:
734:
573:
526:
63:
2245:
2146:
1866:
1751:
366:
was impossible non-interactively, but it has been shown to be possible to achieve all three desiderata.
1230:
1640:
1338:
1209:
554:
1103:
1282:
790:
739:
577:
463:
478:
392:
informally described a puncturable encryption scheme for forward secure key exchange in 1997, and
2162:
1877:
1592:
1257:
1124:
874:
803:
752:
626:
511:
since version 1.0, with a computational overhead of approximately 15% for the initial handshake.
494:
482:
1517:
651:"tls - Does Perfect Forward Secrecy (PFS) make Man-in-the-Middle (MitM) attacks more difficult?"
128:
The term "perfect forward secrecy" was coined by C. G. Günther in 1990 and further discussed by
2113:
1839:
1582:
1552:
1247:
1062:
864:
698:
592:
358:
327:
307:
133:
1309:
2118:
1934:
1872:
1744:
1657:
1649:
1620:
1574:
1566:
1544:
1513:
1239:
1116:
1108:
1052:
856:
795:
744:
389:
271:
129:
1635:
719:
1569:; Miers, Ian (2015). "Forward Secure Asynchronous Messaging from Puncturable Encryption".
515:
416:
use a different construction that can be based on any hierarchical identity-based scheme.
382:
83:
855:. WiSec '08. Alexandria, VA, USA: Association for Computing Machinery. pp. 100–108.
691:
363:
17:
2275:
1899:
1834:
1084:"Beyond eCK: perfect forward secrecy under actor compromise and ephemeral-key reveal"
849:"Key management and secure software updates in wireless process control environments"
474:
458:, a cryptography protocol and library for many instant messaging clients, as well as
294:
267:. They use the keys from step 1 only to authenticate one another during this process.
261:
1726:
1160:
1128:
878:
776:
Jablon, David P. (October 1996). "Strong
Password-Only Authenticated Key Exchange".
2193:
1967:
1709:
Perfect
Forward Secrecy can block the NSA from secure web pages, but no one uses it
1596:
1261:
807:
756:
447:
43:
1434:
1685:"Forward-Secure 0-RTT Goes Live: Implementation and Performance Analysis in QUIC"
847:
Nilsson, Dennis K.; Roosta, Tanya; Lindqvist, Ulf; Valdes, Alfonso (2008-03-31).
1702:
1625:
1532:
1528:
1283:"Wi-Fi Gets More Secure: Everything You Need to Know About WPA3 - IEEE Spectrum"
1238:. San Jose, CA: Institute of Electrical and Electronics Engineers. p. 241.
264:
180:
67:
369:
Broadly, two approaches to non-interactive forward secrecy have been explored,
2240:
1464:
1120:
1112:
446:
Forward secrecy is present in several major protocol implementations, such as
155:
91:
1731:
1653:
1548:
821:
2235:
2047:
2012:
1616:
860:
86:
of a network that uses common transport layer security protocols, including
822:"IEEE 1363-2000 - IEEE Standard Specifications for Public-Key Cryptography"
848:
799:
718:
Diffie, Whitfield; van
Oorschot, Paul C.; Wiener, Michael J. (June 1992).
2052:
2042:
2027:
1662:
1365:
561:
330:
attacks) or failing open (and giving up some amount of forward secrecy).
144:
139:
Forward secrecy has also been used to describe the analogous property of
1057:
2092:
2087:
2072:
2062:
1684:
1605:
1578:
1543:. Lecture Notes in Computer Science. Vol. 2656. pp. 255–271.
1435:"App Transport Security REQUIRED January 2017 | Apple Developer Forums"
1243:
748:
546:
504:
298:
120:
client to the server and implement a classic man-in-the-middle attack.
87:
30:
2250:
2203:
2183:
2082:
2067:
2032:
1604:
Günther, Felix; Hale, Britta; Jager, Tibor; Lauer, Sebastian (2017).
1486:
1395:
1387:
914:
912:
853:
Proceedings of the first ACM conference on
Wireless network security
396:
formally described such a system, building on the related scheme of
2230:
2188:
2022:
1817:
1046:
678:. Advances in Cryptology EUROCRYPT '89 (LNCS 434). pp. 29–37.
538:
498:
459:
451:
71:
29:
1334:
1287:
826:
550:
438:
actively interfere, or attempted to act as a man in the middle.
421:
277:
Bob decrypts Alice's message using the key negotiated in step 2.
1740:
1736:
689:
Menzies, Alfred; van
Oorscot, Paul C; Vanstone, SCOTT (1997).
174:
90:, when its long-term secret keys are compromised, as with the
941:
939:
545:
service, and encrypted search services. Since November 2013,
525:
On the other hand, among popular protocols currently in use,
1032:
417:
306:
and wait until the underlying cipher is broken (e.g. large
968:
966:
1539:(2003). "A Forward-Secure Public-Key Encryption Scheme".
1189:"Protecting data for the long term with forward secrecy"
1460:"WhatsApp, Signal, and dangerously ignorant journalism"
1048:
HMQV: A High-Performance Secure Diffie-Hellman Protocol
109:
Dual Elliptic Curve Deterministic Random Bit Generator
1705:
IETF, H. Orman. The OAKLEY Key Determination Protocol
1020:
918:
413:
2213:
2171:
2155:
2134:
2127:
2101:
1998:
1977:
1948:
1853:
1774:
256:Alice and Bob use a key exchange algorithm such as
143:protocols where the long-term secret is a (shared)
1149:Discussion on the TLS mailing list in October 2007
690:
1183:
1181:
397:
245:Alice and Bob each generate a pair of long-term,
720:"Authentication and Authenticated Key Exchanges"
549:provided forward secrecy with TLS to its users.
270:Alice sends Bob a message, encrypting it with a
1782:Transport Layer Security / Secure Sockets Layer
1361:"The Current State of SMTP STARTTLS Deployment"
1606:"0-RTT Key Exchange with Full Forward Secrecy"
1161:"A Detailed Look at RFC 8446 (a.k.a. TLS 1.3)"
1985:Export of cryptography from the United States
1752:
529:did not support forward secrecy before WPA3.
8:
1861:Automated Certificate Management Environment
1634:Boyd, Colin; Gellert, Kai (24 August 2020).
1571:2015 IEEE Symposium on Security and Privacy
1232:2015 IEEE Symposium on Security and Privacy
1008:
984:
945:
930:
903:
891:
274:using the session key negotiated in step 2.
209:. Unsourced material may be challenged and
2131:
1806:DNS-based Authentication of Named Entities
1759:
1745:
1737:
1715:SSL: Intercepted today, decrypted tomorrow
972:
401:
393:
1812:DNS Certification Authority Authorization
1661:
1102:
1056:
789:
738:
627:"/docs/man1.1.1/man3/SSL_set_tmp_dh.html"
229:Learn how and when to remove this message
996:
74:, the long-term secret is typically the
1541:Advances in Cryptology — EUROCRYPT 2003
1210:"SSL/TLS & Perfect Forward Secrecy"
676:An identity-based key-exchange protocol
618:
1956:Domain Name System Security Extensions
1800:Application-Layer Protocol Negotiation
1518:"Two Remarks on Public Key Cryptology"
406:hierarchical identity-based encryption
1648:(4) (published April 2021): 639–652.
1082:Cremers, Cas; Feltz, Michèle (2015).
82:Forward secrecy protects data on the
7:
957:
420:experimentally found that modifying
207:adding citations to reliable sources
141:password-authenticated key agreement
1636:"A Modern View on Forward Security"
1208:Vincent Bernat (28 November 2011).
655:Information Security Stack Exchange
1894:Online Certificate Status Protocol
247:asymmetric public and private keys
25:
1788:Datagram Transport Layer Security
1621:"non-interactive forward secrecy"
778:ACM Computer Communication Review
398:Canetti, Halevi & Katz (2003)
310:could be created which allow the
2221:Certificate authority compromise
1670:from the original on 7 June 2021
693:Handbook of Applied Cryptography
338:Most key exchange protocols are
179:
2226:Random number generator attacks
1913:Extended Validation Certificate
1091:Designs, Codes and Cryptography
727:Designs, Codes and Cryptography
507:supports forward secrecy using
334:Non-interactive forward secrecy
97:man-in-the-middle (MITM) attack
1823:HTTP Strict Transport Security
1727:SSL Labs test for web browsers
1458:Evans, Jon (22 January 2017).
450:and as an optional feature in
1:
1732:SSL Labs test for web servers
1487:"Qualys SSL Labs - SSL Pulse"
603:Elliptic curve Diffie–Hellman
509:elliptic curve Diffie–Hellman
491:elliptic curve Diffie–Hellman
1907:Domain-validated certificate
1310:"Forward Secrecy at Twitter"
522:to provide forward secrecy.
429:Weak perfect forward secrecy
103:in a forward secure system.
62:), is a feature of specific
1888:Certificate revocation list
1711:Computerworld June 21, 2013
598:Diffie–Hellman key exchange
117:Diffie–Hellman key exchange
66:that gives assurances that
2308:
1962:Internet Protocol Security
1775:Protocols and technologies
1439:forums.developer.apple.com
1335:"Tech/News/2014/27 - Meta"
608:Harvest now, decrypt later
410:attribute-based encryption
312:discrete logarithm problem
260:, to securely agree on an
1990:Server-Gated Cryptography
1929:Public key infrastructure
1854:Public-key infrastructure
1721:Deploying Forward Secrecy
1113:10.1007/s10623-013-9852-1
2292:Transport Layer Security
2142:Man-in-the-middle attack
2109:Certificate Transparency
1549:10.1007/3-540-39200-9_16
1308:Hoffman-Andrews, Jacob.
520:Double Ratchet Algorithm
471:Transport Layer Security
456:Off-the-Record Messaging
402:Green & Miers (2015)
394:Green & Miers (2015)
324:malicious key exhaustion
27:Practice in cryptography
2287:Public-key cryptography
2253:(in regards to TLS 1.0)
2206:(in regards to SSL 3.0)
1940:Self-signed certificate
1924:Public-key cryptography
1845:Perfect forward secrecy
1829:HTTP Public Key Pinning
1045:Krawczyk, Hugo (2005).
1009:Boyd & Gellert 2020
985:Boyd & Gellert 2020
946:Boyd & Gellert 2020
931:Boyd & Gellert 2020
904:Boyd & Gellert 2020
892:Boyd & Gellert 2020
861:10.1145/1352533.1352550
674:Günther, C. G. (1990).
418:Dallmeier et al. (2020)
304:public-key cryptography
251:public-key fingerprints
64:key-agreement protocols
56:perfect forward secrecy
36:Key derivation function
18:Perfect Forward Secrecy
2257:Kazakhstan MITM attack
1919:Public key certificate
1883:Certificate revocation
1794:Server Name Indication
1723:SSL Labs June 25, 2013
1717:Netcraft June 25, 2013
1654:10.1093/comjnl/bxaa104
973:Green & Miers 2015
375:puncturable encryption
39:
2246:Lucky Thirteen attack
2147:Padding oracle attack
1867:Certificate authority
1033:Dallmeier et al. 2020
800:10.1145/242896.242897
414:Günther et al. (2017)
33:
1641:The Computer Journal
1619:(6 September 1996).
1573:. pp. 305–320.
1339:Wikimedia Foundation
555:Wikimedia Foundation
493:key exchange (ECDHE-
203:improve this section
1401:on 15 February 2019
1165:The Cloudflare Blog
1058:10.1007/11535218_33
1021:Günther et al. 2017
919:Günther et al. 2017
464:deniable encryption
319:message suppression
2163:Bar mitzvah attack
1878:Certificate policy
1579:10.1109/SP.2015.26
1244:10.1109/SP.2015.22
1121:20.500.11850/73097
1011:, p. 643-644.
987:, p. 644-645.
906:, p. 639-640.
749:10.1007/BF00124891
481:key exchange (DHE-
297:of the underlying
40:
2269:
2268:
2265:
2264:
1840:Opportunistic TLS
1588:978-1-4673-6949-7
1567:Green, Matthew D.
1558:978-3-540-14039-9
1399:(3 February 2019)
1253:978-1-4673-6949-7
1068:978-3-540-28114-6
870:978-1-59593-814-5
704:978-0-8493-8523-0
593:Forward anonymity
371:pre-computed keys
359:store-and-forward
328:denial of service
308:quantum computers
239:
238:
231:
134:Paul van Oorschot
54:), also known as
16:(Redirected from
2299:
2132:
2119:HTTPS Everywhere
1935:Root certificate
1873:CA/Browser Forum
1761:
1754:
1747:
1738:
1691:
1689:
1679:
1677:
1675:
1665:
1630:
1612:
1610:
1600:
1562:
1524:
1522:
1501:
1500:
1498:
1497:
1483:
1477:
1476:
1474:
1472:
1455:
1449:
1448:
1446:
1445:
1431:
1425:
1424:
1417:
1411:
1410:
1408:
1406:
1400:
1394:. Archived from
1384:
1378:
1377:
1375:
1373:
1357:
1351:
1350:
1348:
1346:
1331:
1325:
1324:
1322:
1320:
1305:
1299:
1298:
1296:
1295:
1279:
1273:
1272:
1270:
1268:
1237:
1226:
1220:
1219:
1217:
1216:
1205:
1199:
1198:
1196:
1195:
1185:
1176:
1175:
1173:
1172:
1157:
1151:
1146:
1140:
1139:
1137:
1135:
1106:
1088:
1079:
1073:
1072:
1060:
1042:
1036:
1035:, p. 18-19.
1030:
1024:
1018:
1012:
1006:
1000:
994:
988:
982:
976:
970:
961:
955:
949:
943:
934:
928:
922:
916:
907:
901:
895:
889:
883:
882:
844:
838:
837:
835:
834:
818:
812:
811:
793:
773:
767:
766:
764:
763:
742:
724:
715:
709:
708:
696:
686:
680:
679:
671:
665:
664:
662:
661:
647:
641:
640:
638:
637:
623:
390:Ross J. Anderson
272:symmetric cipher
234:
227:
223:
220:
214:
183:
175:
130:Whitfield Diffie
21:
2307:
2306:
2302:
2301:
2300:
2298:
2297:
2296:
2272:
2271:
2270:
2261:
2209:
2167:
2151:
2128:Vulnerabilities
2123:
2097:
2000:Implementations
1994:
1973:
1944:
1849:
1770:
1765:
1698:
1687:
1682:
1673:
1671:
1633:
1629:(Mailing list).
1615:
1608:
1603:
1589:
1565:
1559:
1527:
1520:
1512:
1509:
1504:
1495:
1493:
1491:www.ssllabs.com
1485:
1484:
1480:
1470:
1468:
1457:
1456:
1452:
1443:
1441:
1433:
1432:
1428:
1419:
1418:
1414:
1404:
1402:
1398:
1388:Qualys SSL Labs
1386:
1385:
1381:
1371:
1369:
1359:
1358:
1354:
1344:
1342:
1333:
1332:
1328:
1318:
1316:
1307:
1306:
1302:
1293:
1291:
1281:
1280:
1276:
1266:
1264:
1254:
1235:
1228:
1227:
1223:
1214:
1212:
1207:
1206:
1202:
1193:
1191:
1187:
1186:
1179:
1170:
1168:
1159:
1158:
1154:
1147:
1143:
1133:
1131:
1104:10.1.1.692.1406
1086:
1081:
1080:
1076:
1069:
1044:
1043:
1039:
1031:
1027:
1019:
1015:
1007:
1003:
995:
991:
983:
979:
971:
964:
956:
952:
944:
937:
929:
925:
917:
910:
902:
898:
890:
886:
871:
846:
845:
841:
832:
830:
820:
819:
815:
775:
774:
770:
761:
759:
722:
717:
716:
712:
705:
688:
687:
683:
673:
672:
668:
659:
657:
649:
648:
644:
635:
633:
631:www.openssl.org
625:
624:
620:
616:
589:
535:
516:Signal Protocol
444:
431:
383:Signal protocol
352:zero round trip
344:non-interactive
336:
291:
235:
224:
218:
215:
200:
184:
173:
164:
154:first ratified
126:
84:transport layer
48:forward secrecy
28:
23:
22:
15:
12:
11:
5:
2305:
2303:
2295:
2294:
2289:
2284:
2282:Key management
2274:
2273:
2267:
2266:
2263:
2262:
2260:
2259:
2254:
2248:
2243:
2238:
2233:
2228:
2223:
2217:
2215:
2214:Implementation
2211:
2210:
2208:
2207:
2201:
2196:
2191:
2186:
2181:
2175:
2173:
2169:
2168:
2166:
2165:
2159:
2157:
2153:
2152:
2150:
2149:
2144:
2138:
2136:
2129:
2125:
2124:
2122:
2121:
2116:
2111:
2105:
2103:
2099:
2098:
2096:
2095:
2090:
2085:
2080:
2075:
2070:
2065:
2060:
2055:
2050:
2045:
2040:
2035:
2030:
2025:
2020:
2015:
2010:
2004:
2002:
1996:
1995:
1993:
1992:
1987:
1981:
1979:
1975:
1974:
1972:
1971:
1965:
1959:
1952:
1950:
1946:
1945:
1943:
1942:
1937:
1932:
1926:
1921:
1916:
1910:
1904:
1903:
1902:
1897:
1891:
1880:
1875:
1870:
1864:
1857:
1855:
1851:
1850:
1848:
1847:
1842:
1837:
1832:
1826:
1820:
1815:
1809:
1803:
1797:
1791:
1785:
1778:
1776:
1772:
1771:
1766:
1764:
1763:
1756:
1749:
1741:
1735:
1734:
1729:
1724:
1718:
1712:
1706:
1697:
1696:External links
1694:
1693:
1692:
1680:
1631:
1613:
1601:
1587:
1563:
1557:
1537:Katz, Jonathan
1525:
1514:Anderson, Ross
1508:
1505:
1503:
1502:
1478:
1450:
1426:
1412:
1379:
1352:
1326:
1300:
1274:
1252:
1221:
1200:
1177:
1152:
1141:
1097:(1): 183–218.
1074:
1067:
1037:
1025:
1013:
1001:
989:
977:
962:
950:
948:, p. 643.
935:
933:, p. 640.
923:
908:
896:
894:, p. 645.
884:
869:
839:
813:
791:10.1.1.81.2594
768:
740:10.1.1.59.6682
733:(2): 107–125.
710:
703:
681:
666:
642:
617:
615:
612:
611:
610:
605:
600:
595:
588:
585:
553:hosted by the
534:
531:
479:Diffie–Hellman
443:
440:
430:
427:
364:replay attacks
335:
332:
290:
287:
282:
281:
278:
275:
268:
258:Diffie–Hellman
254:
249:, then verify
237:
236:
187:
185:
178:
172:
169:
163:
160:
125:
122:
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
2304:
2293:
2290:
2288:
2285:
2283:
2280:
2279:
2277:
2258:
2255:
2252:
2249:
2247:
2244:
2242:
2239:
2237:
2234:
2232:
2229:
2227:
2224:
2222:
2219:
2218:
2216:
2212:
2205:
2202:
2200:
2197:
2195:
2192:
2190:
2187:
2185:
2182:
2180:
2177:
2176:
2174:
2170:
2164:
2161:
2160:
2158:
2154:
2148:
2145:
2143:
2140:
2139:
2137:
2133:
2130:
2126:
2120:
2117:
2115:
2112:
2110:
2107:
2106:
2104:
2100:
2094:
2091:
2089:
2086:
2084:
2081:
2079:
2076:
2074:
2071:
2069:
2066:
2064:
2061:
2059:
2056:
2054:
2051:
2049:
2046:
2044:
2041:
2039:
2036:
2034:
2031:
2029:
2026:
2024:
2021:
2019:
2016:
2014:
2011:
2009:
2008:Bouncy Castle
2006:
2005:
2003:
2001:
1997:
1991:
1988:
1986:
1983:
1982:
1980:
1976:
1969:
1966:
1963:
1960:
1957:
1954:
1953:
1951:
1947:
1941:
1938:
1936:
1933:
1930:
1927:
1925:
1922:
1920:
1917:
1914:
1911:
1908:
1905:
1901:
1900:OCSP stapling
1898:
1895:
1892:
1889:
1886:
1885:
1884:
1881:
1879:
1876:
1874:
1871:
1868:
1865:
1862:
1859:
1858:
1856:
1852:
1846:
1843:
1841:
1838:
1836:
1835:OCSP stapling
1833:
1830:
1827:
1824:
1821:
1819:
1816:
1813:
1810:
1807:
1804:
1801:
1798:
1795:
1792:
1789:
1786:
1783:
1780:
1779:
1777:
1773:
1769:
1762:
1757:
1755:
1750:
1748:
1743:
1742:
1739:
1733:
1730:
1728:
1725:
1722:
1719:
1716:
1713:
1710:
1707:
1704:
1700:
1699:
1695:
1686:
1681:
1669:
1664:
1663:11250/2730309
1659:
1655:
1651:
1647:
1643:
1642:
1637:
1632:
1628:
1627:
1622:
1618:
1614:
1607:
1602:
1598:
1594:
1590:
1584:
1580:
1576:
1572:
1568:
1564:
1560:
1554:
1550:
1546:
1542:
1538:
1534:
1530:
1526:
1519:
1515:
1511:
1510:
1506:
1492:
1488:
1482:
1479:
1467:
1466:
1461:
1454:
1451:
1440:
1436:
1430:
1427:
1422:
1416:
1413:
1397:
1393:
1389:
1383:
1380:
1368:
1367:
1362:
1356:
1353:
1340:
1336:
1330:
1327:
1315:
1311:
1304:
1301:
1290:
1289:
1284:
1278:
1275:
1263:
1259:
1255:
1249:
1245:
1241:
1234:
1233:
1225:
1222:
1211:
1204:
1201:
1190:
1184:
1182:
1178:
1166:
1162:
1156:
1153:
1150:
1145:
1142:
1130:
1126:
1122:
1118:
1114:
1110:
1105:
1100:
1096:
1092:
1085:
1078:
1075:
1070:
1064:
1059:
1054:
1050:
1049:
1041:
1038:
1034:
1029:
1026:
1022:
1017:
1014:
1010:
1005:
1002:
998:
997:Anderson 2002
993:
990:
986:
981:
978:
974:
969:
967:
963:
959:
954:
951:
947:
942:
940:
936:
932:
927:
924:
920:
915:
913:
909:
905:
900:
897:
893:
888:
885:
880:
876:
872:
866:
862:
858:
854:
850:
843:
840:
829:
828:
823:
817:
814:
809:
805:
801:
797:
792:
787:
783:
779:
772:
769:
758:
754:
750:
746:
741:
736:
732:
728:
721:
714:
711:
706:
700:
695:
694:
685:
682:
677:
670:
667:
656:
652:
646:
643:
632:
628:
622:
619:
613:
609:
606:
604:
601:
599:
596:
594:
591:
590:
586:
584:
581:
579:
575:
570:
566:
563:
558:
556:
552:
548:
544:
540:
532:
530:
528:
523:
521:
517:
512:
510:
506:
502:
500:
496:
492:
488:
484:
480:
476:
475:cipher suites
472:
467:
465:
461:
457:
453:
449:
441:
439:
437:
428:
426:
423:
419:
415:
411:
407:
403:
399:
395:
391:
386:
384:
378:
376:
372:
367:
365:
360:
355:
353:
349:
345:
341:
333:
331:
329:
325:
320:
315:
313:
309:
305:
300:
296:
295:cryptanalysis
288:
286:
279:
276:
273:
269:
266:
263:
259:
255:
252:
248:
244:
243:
242:
233:
230:
222:
219:February 2018
212:
208:
204:
198:
197:
193:
188:This section
186:
182:
177:
176:
170:
168:
161:
159:
157:
153:
148:
146:
142:
137:
135:
131:
123:
121:
118:
112:
110:
104:
100:
98:
93:
89:
85:
80:
77:
73:
69:
65:
61:
57:
53:
49:
45:
37:
32:
19:
1968:Secure Shell
1844:
1672:. Retrieved
1645:
1639:
1624:
1570:
1540:
1533:Halevi, Shai
1529:Canetti, Ran
1507:Bibliography
1494:. Retrieved
1490:
1481:
1469:. Retrieved
1463:
1453:
1442:. Retrieved
1438:
1429:
1415:
1403:. Retrieved
1396:the original
1382:
1370:. Retrieved
1364:
1355:
1343:. Retrieved
1341:. 2014-06-30
1329:
1317:. Retrieved
1313:
1303:
1292:. Retrieved
1286:
1277:
1265:. Retrieved
1231:
1224:
1213:. Retrieved
1203:
1192:. Retrieved
1169:. Retrieved
1167:. 2018-08-10
1164:
1155:
1144:
1132:. Retrieved
1094:
1090:
1077:
1047:
1040:
1028:
1023:, p. 5.
1016:
1004:
992:
980:
975:, p. 1.
953:
926:
921:, p. 1.
899:
887:
852:
842:
831:. Retrieved
825:
816:
781:
777:
771:
760:. Retrieved
730:
726:
713:
697:. CRC Pres.
692:
684:
675:
669:
658:. Retrieved
654:
645:
634:. Retrieved
630:
621:
582:
571:
567:
559:
536:
527:WPA Personal
524:
513:
503:
468:
454:(RFC 2412).
445:
435:
432:
404:make use of
387:
379:
374:
370:
368:
356:
351:
348:asynchronous
347:
343:
339:
337:
323:
318:
316:
292:
283:
240:
225:
216:
201:Please help
189:
165:
150:In 2000 the
149:
138:
127:
113:
105:
101:
81:
68:session keys
59:
55:
51:
47:
44:cryptography
41:
2114:Convergence
1768:TLS and SSL
1626:Cypherpunks
1405:25 February
1392:"SSL Pulse"
1319:25 November
784:(5): 5–26.
543:Google Docs
340:interactive
265:session key
76:private key
2276:Categories
2241:Heartbleed
1617:Back, Adam
1496:2024-05-25
1465:TechCrunch
1444:2016-10-20
1294:2024-05-04
1267:4 December
1215:2012-11-05
1194:2012-11-05
1171:2019-02-26
1134:8 December
833:2018-06-14
762:2013-09-07
660:2020-10-11
636:2024-05-25
614:References
162:Definition
92:Heartbleed
2236:goto fail
2048:MatrixSSL
2013:BoringSSL
1784:(TLS/SSL)
1701:RFC
1421:"iOS 9.0"
1099:CiteSeerX
958:Back 1996
786:CiteSeerX
735:CiteSeerX
541:service,
518:uses the
477:based on
442:Protocols
354:(0-RTT).
262:ephemeral
190:does not
156:IEEE 1363
2172:Protocol
2102:Notaries
2078:SChannel
2053:mbed TLS
2043:LibreSSL
2028:cryptlib
1958:(DNSSEC)
1949:See also
1668:Archived
1516:(2002).
1471:18 April
1366:Facebook
1129:53306672
879:15382932
587:See also
562:STARTTLS
497:, ECDHE-
412:, while
145:password
2093:wolfSSL
2088:stunnel
2073:s2n-tls
2063:OpenSSL
1978:History
1964:(IPsec)
1597:9171925
1345:30 June
1314:Twitter
1262:2471650
808:2870433
757:7356608
547:Twitter
505:OpenSSL
473:(TLS),
299:ciphers
289:Attacks
211:removed
196:sources
171:Example
124:History
88:OpenSSL
2251:POODLE
2204:POODLE
2199:Logjam
2184:BREACH
2156:Cipher
2135:Theory
2083:SSLeay
2068:Rustls
2033:GnuTLS
1896:(OCSP)
1863:(ACME)
1831:(HPKP)
1825:(HSTS)
1808:(DANE)
1802:(ALPN)
1790:(DTLS)
1674:8 June
1595:
1585:
1555:
1372:7 June
1260:
1250:
1127:
1101:
1065:
877:
867:
806:
788:
755:
737:
701:
574:Signal
489:) and
485:, DHE-
2231:FREAK
2194:DROWN
2189:CRIME
2179:BEAST
2023:BSAFE
2018:Botan
1970:(SSH)
1931:(PKI)
1890:(CRL)
1818:HTTPS
1814:(CAA)
1796:(SNI)
1688:(PDF)
1609:(PDF)
1593:S2CID
1521:(PDF)
1258:S2CID
1236:(PDF)
1125:S2CID
1087:(PDF)
875:S2CID
804:S2CID
753:S2CID
723:(PDF)
551:Wikis
539:Gmail
499:ECDSA
460:OMEMO
452:IPsec
350:, or
346:, or
72:HTTPS
2038:JSSE
1915:(EV)
1909:(DV)
1869:(CA)
1703:2412
1676:2021
1583:ISBN
1553:ISBN
1473:2018
1407:2019
1374:2014
1347:2014
1321:2013
1288:IEEE
1269:2015
1248:ISBN
1136:2015
1063:ISBN
865:ISBN
827:IEEE
699:ISBN
572:The
514:The
422:QUIC
408:and
373:and
194:any
192:cite
152:IEEE
2058:NSS
1658:hdl
1650:doi
1575:doi
1545:doi
1240:doi
1117:hdl
1109:doi
1053:doi
857:doi
796:doi
745:doi
578:PGP
533:Use
495:RSA
487:DSA
483:RSA
469:In
448:SSH
436:did
205:by
60:PFS
42:In
2278::
1666:.
1656:.
1646:64
1644:.
1638:.
1623:.
1591:.
1581:.
1551:.
1535:;
1531:;
1489:.
1462:.
1437:.
1390:.
1363:.
1337:.
1312:.
1285:.
1256:.
1246:.
1180:^
1163:.
1123:.
1115:.
1107:.
1095:74
1093:.
1089:.
1061:.
965:^
938:^
911:^
873:.
863:.
851:.
824:.
802:.
794:.
782:26
780:.
751:.
743:.
729:.
725:.
653:.
629:.
580:.
466:.
385:.
377:.
147:.
132:,
99:.
52:FS
46:,
34:A
1760:e
1753:t
1746:v
1690:.
1678:.
1660::
1652::
1611:.
1599:.
1577::
1561:.
1547::
1523:.
1499:.
1475:.
1447:.
1423:.
1409:.
1376:.
1349:.
1323:.
1297:.
1271:.
1242::
1218:.
1197:.
1174:.
1138:.
1119::
1111::
1071:.
1055::
999:.
960:.
881:.
859::
836:.
810:.
798::
765:.
747::
731:2
707:.
663:.
639:.
232:)
226:(
221:)
217:(
213:.
199:.
58:(
50:(
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.