650:, are used to detect a stack buffer overflow before execution of malicious code can occur. This method works by placing a small integer, the value of which is randomly chosen at program start, in memory just before the stack return pointer. Most buffer overflows overwrite memory from lower to higher memory addresses, so in order to overwrite the return pointer (and thus take control of the process) the canary value must also be overwritten. This value is checked to make sure it has not changed before a routine uses the return pointer on the stack. This technique can greatly increase the difficulty of exploiting a stack buffer overflow because it forces the attacker to gain control of the instruction pointer by some non-traditional means such as corrupting other important variables on the stack.
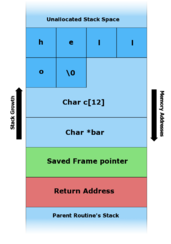
218:. This works fine for command-line arguments smaller than 12 characters (as can be seen in figure B below). Any arguments larger than 11 characters long will result in corruption of the stack. (The maximum number of characters that is safe is one less than the size of the buffer here because in the C programming language, strings are terminated by a null byte character. A twelve-character input thus requires thirteen bytes to store, the input followed by the sentinel zero byte. The zero byte then ends up overwriting a memory location that's one byte beyond the end of the buffer.)
46:. Stack buffer overflow bugs are caused when a program writes more data to a buffer located on the stack than what is actually allocated for that buffer. This almost always results in corruption of adjacent data on the stack, and in cases where the overflow was triggered by mistake, will often cause the program to crash or operate incorrectly. Stack buffer overflow is a type of the more general programming malfunction known as
253:
243:
233:
668:, "Write XOR Execute"). This means that in order to execute shellcode from the stack an attacker must either find a way to disable the execution protection from memory, or find a way to put their shellcode payload in a non-protected region of memory. This method is becoming more popular now that hardware support for the no-execute flag is available in most desktop processors.
701:
stack) or one is constructed using code reuse such as in ret2libc or return-oriented programming (ROP). Randomizing the memory layout will, as a concept, prevent the attacker from knowing where any code is. However, implementations typically will not randomize everything; usually the executable itself is loaded at a fixed address and hence even when
565:-style machine architectures will not allow unaligned access to memory. Combined with a fixed length for machine opcodes, this machine limitation can make the technique of jumping to the stack almost impossible to implement (with the one exception being when the program actually contains the unlikely code to explicitly jump to the stack register).
679:
method for shellcode creation. In this attack the malicious payload will load the stack not with shellcode, but with a proper call stack so that execution is vectored to a chain of standard library calls, usually with the effect of disabling memory execute protections and allowing shellcode to run as
560:
A number of platforms have subtle differences in their implementation of the call stack that can affect the way a stack buffer overflow exploit will work. Some machine architectures store the top-level return address of the call stack in a register. This means that any overwritten return address will
779:
A limitation of ASLR realization on 64-bit systems is that it is vulnerable to memory disclosure and information leakage attacks. The attacker can launch the ROP by revealing a single function address using information leakage attack. The following section describes the similar existing strategy for
691:
each accomplish some simple register manipulation or similar execution before returning, and stringing them together achieves the attacker's ends. It is even possible to use "returnless" return-oriented programming by exploiting instructions or groups of instructions that behave much like a return
700:
Instead of separating the code from the data, another mitigation technique is to introduce randomization to the memory space of the executing program. Since the attacker needs to determine where executable code that can be used resides, either an executable payload is provided (with an executable
573:
Within the topic of stack buffer overflows, an often-discussed-but-rarely-seen architecture is one in which the stack grows in the opposite direction. This change in architecture is frequently suggested as a solution to the stack buffer overflow problem because any overflow of a stack buffer that
574:
occurs within the same stack frame cannot overwrite the return pointer. However, any overflow that occurs in a buffer from a previous stack frame will still overwrite a return pointer and allow for malicious exploitation of the bug. For instance, in the example above, the return pointer for
709:(position-independent executables) such that even this region of memory is randomized. The entropy of the randomization is different from implementation to implementation and a low enough entropy can in itself be a problem in terms of brute forcing the memory space that is randomized.
762:
Consists to overwrite the return pointer a bit before a return instruction (ret in x86) of the program. The instructions between the new return pointer and the return instruction will be executed and the return instruction will return to the payload controlled by the exploiter.
671:
While this method prevents the canonical stack smashing exploit, stack overflows can be exploited in other ways. First, it is common to find ways to store shellcode in unprotected memory regions like the heap, and so very little need change in the way of exploitation.
551:
There are typically two methods that are used to alter the stored address in the stack - direct and indirect. Attackers started developing indirect attacks, which have fewer dependencies, in order to bypass protection measures that were made to reduce direct attacks.
65:. If the stack buffer is filled with data supplied from an untrusted user then that user can corrupt the stack in such a way as to inject executable code into the running program and take control of the process. This is one of the oldest and more reliable methods for
687:(ROP), which sets up a series of return addresses, each of which executes a small sequence of cherry-picked machine instructions within the existing program code or system libraries, sequence which ends with a return. These so-called
598:
will be overwritten. At most, this means that growing the stack in the opposite direction will change some details of how stack buffer overflows are exploitable, but it will not reduce significantly the number of exploitable bugs.
272:
returns, it pops the return address off the stack and jumps to that address (i.e. starts executing instructions from that address). Thus, the attacker has overwritten the return address with a pointer to the stack buffer
50:(or buffer overrun). Overfilling a buffer on the stack is more likely to derail program execution than overfilling a buffer on the heap because the stack contains the return addresses for all active function calls.
717:
The previous mitigations make the steps of the exploitation harder. But it is still possible to exploit a stack buffer overflow if some vulnerabilities are presents or if some conditions are met.
858:
which involves using an SD card to load a specially prepared file into the in-game level editor. Though both can be used to execute any arbitrary code, the latter is often used to simply reload
561:
not be used until a later unwinding of the call stack. Another example of a machine-specific detail that can affect the choice of exploitation techniques is the fact that most
705:(address space layout randomization) is combined with a non-executable stack the attacker can use this fixed region of memory. Therefore, all programs should be compiled with
81:
a stack-based buffer overflow is to overwrite the function return address with a pointer to attacker-controlled data (usually on the stack itself). This is illustrated with
1174:
664:
Another approach to preventing stack buffer overflow exploitation is to enforce a memory policy on the stack memory region that disallows execution from the stack (
746:
is enabled to forbid any execute access to the stack, the attacker can still use the overwritten return address (the instruction pointer) to point to data in a
1065:
846:
allowing arbitrary code to be run on an unmodified system. The "Twilight hack" which involves giving a lengthy name to the main character's horse in
1473:
1308:
Checkoway, S.; Davi, L.; Dmitrienko, A.; Sadeghi, A. R.; Shacham, H.; Winandy, M. (October 2010). "Return-Oriented
Programming without Returns".
848:
1325:
617:
schemes have been developed to inhibit malicious stack buffer overflow exploitation. These may usually be classified into three categories:
1594:
823:
1267:
973:
838:
1090:
1254:
20:
1374:
937:
277:, which now contains attacker-supplied data. In an actual stack buffer overflow exploit the string of "A"'s would instead be
1589:
731:
684:
659:
78:
608:
66:
57:. If the affected program is running with special privileges, or accepts data from untrusted network hosts (e.g. a
834:
743:
706:
590:
will have a numerically higher memory address than the buffer. This means that instead of the return pointer for
1112:
Kuperman, Benjamin A.; Brodley, Carla E.; Ozdoganoglu, Hilmi; Vijaykumar, T. N.; Jalote, Ankit (November 2005).
1023:
1599:
771:
Jump
Oriented Programming is a technique that uses jump instructions to reuse code instead of ret instruction.
1072:
902:
854:
628:
Prevent the execution of malicious code from the stack without directly detecting the stack buffer overflow.
1584:
614:
62:
1489:
Butt, Muhammad Arif; Ajmal, Zarafshan; Khan, Zafar Iqbal; Idrees, Muhammad; Javed, Yasir (January 2022).
1432:
Butt, Muhammad Arif; Ajmal, Zarafshan; Khan, Zafar Iqbal; Idrees, Muhammad; Javed, Yasir (January 2022).
1388:
Butt, Muhammad Arif; Ajmal, Zarafshan; Khan, Zafar Iqbal; Idrees, Muhammad; Javed, Yasir (January 2022).
676:
289:), then the attacker could use this vulnerability to gain superuser privileges on the affected machine.
268:
overwrites local stack data, the saved frame pointer, and most importantly, the return address. When
622:
1331:
1141:
1046:
863:
754:
on Linux) or every other executable section of the program. The goal is to reuse existing code.
281:
suitable to the platform and desired function. If this program had special privileges (e.g. the
1189:
292:
The attacker can also modify internal variable values to exploit some bugs. With this example:
1512:
1455:
1411:
1368:
1321:
1284:
1263:
1168:
1133:
969:
913:
1502:
1445:
1401:
1313:
1125:
1038:
891:
797:
647:
214:
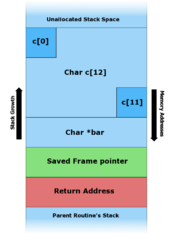
This code takes an argument from the command line and copies it to a local stack variable
47:
35:
814:
264:
In figure C above, when an argument larger than 11 bytes is supplied on the command line
1310:
Proceedings of the 17th ACM conference on
Computer and communications security - CCS '10
578:
will not be overwritten because the overflow actually occurs within the stack frame for
1229:
965:
907:
1350:
1098:
1578:
1335:
886:
680:
normal. This works because the execution never actually vectors to the stack itself.
621:
Detect that a stack buffer overflow has occurred and thus prevent redirection of the
1050:
819:
747:
641:
1145:
998:
1113:
53:
A stack buffer overflow can be caused deliberately as part of an attack known as
806:
801:
790:
631:
Randomize the memory space such that finding executable code becomes unreliable.
43:
256:
C. - "AAAAAAAAAAAAAAAAAAAA\x08\x35\xC0\x80" is the first command line argument.
252:
242:
232:
1160:
994:
881:
876:
830:
39:
1516:
1459:
1415:
1137:
1317:
1129:
810:
286:
278:
58:
1214:
1507:
1490:
1450:
1433:
1406:
1389:
1042:
42:
outside of the intended data structure, which is usually a fixed-length
1491:"An In-Depth Survey of Bypassing Buffer Overflow Mitigation Techniques"
1434:"An In-Depth Survey of Bypassing Buffer Overflow Mitigation Techniques"
1390:"An In-Depth Survey of Bypassing Buffer Overflow Mitigation Techniques"
941:
1253:
Foster, James C.; Osipov, Vitaly; Bhalla, Nish; Heinen, Niels (2005).
1024:"Beyond Stack Smashing: Recent Advances in Exploiting Buffer Overruns"
1289:
1234:
1194:
1003:
896:
282:
83:
1215:
Where's the FEEB? The
Effectiveness of Instruction Set Randomization
793:
in 1988 spread in part by exploiting a stack buffer overflow in the
1530:
822:
in 2003 spread by exploiting a stack buffer overflow in
Microsoft
251:
241:
231:
1554:
794:
702:
665:
582:. However, because the buffer that overflows during the call to
562:
1095:
MUSESS '02: McMaster
University Software Engineering Symposium
843:
734:
for revealing the memory locations in the vulnerable program.
726:
Information leak with format string vulnerability exploitation
1190:"Reverse engineering - PowerPC Cracking on Mac OS X with GDB"
417:
memcpy will put 0x1010C042 (little endian) in My_Float value.
833:
in 2004 spread by exploiting a stack buffer overflow in the
1114:"Detection and prevention of stack buffer overflow attacks"
960:
Dowd, Mark; McDonald, John; Schuh, Justin (November 2006).
1285:"The advanced return-into-lib(c) exploits: PaX case study"
586:
resides in a previous stack frame, the return pointer for
809:
in 2003 spread by exploiting a stack buffer overflow in
420:~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~*/
414:
foo("my string is too long !!!!! XXXXX");
390:/* ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
1262:. United States of America: Syngress Publishing, Inc.
1213:Sovarel, Ana Nora; Evans, David; Paul, Nathanael.
1161:"Exploiting SPARC Buffer Overflow vulnerabilities"
936:Fithen, William L.; Seacord, Robert (2007-03-27).
1256:Buffer Overflow Attacks: Detect, Exploit, Prevent
246:B. - "hello" is the first command line argument.
646:Stack canaries, named for their analogy to a
8:
1173:: CS1 maint: numeric names: authors list (
69:to gain unauthorized access to a computer.
1091:"OpenBSD: Fix the Bugs, Secure the System"
1022:Pincus, J.; Baker, B. (July–August 2004).
594:being overwritten, the return pointer for
1506:
1449:
1405:
989:
987:
985:
999:"Smashing The Stack for Fun and Profit"
962:The Art Of Software Security Assessment
931:
929:
925:
525:"my string is too long !!!!!
1366:
1166:
955:
953:
951:
849:The Legend of Zelda: Twilight Princess
842:There are a couple of examples of the
405:0x0023FF30 0x0023FF4C
1427:
1425:
7:
899:– no-execute bit for areas of memory
938:"VT-MB. Violation of Memory Bounds"
780:breaking down the ASLR protection.
730:An attacker is able to exploit the
1031:IEEE Security and Privacy Magazine
399:# : My_Float allocated memory
34:occurs when a program writes to a
14:
1351:"Memory Errors, program security"
910:– when the stack itself overflows
411:@@@@@@@@@@@@@@@@@@@@@@@@@@@@#####
402:*c *My_Float
73:Exploiting stack buffer overflows
1475:Sécurité matérielle des systèmes
675:Another attack is the so-called
1230:"HP-UX (PA-RISC 1.1) Overflows"
683:A variant of return-to-libc is
21:Stack overflow (disambiguation)
61:) then the bug is a potential
1:
408:| |
613:Over the years, a number of
556:Platform-related differences
738:Non executable stack bypass
732:format string vulnerability
685:return-oriented programming
660:Executable space protection
396:@ : c allocated memory
236:A. - Before data is copied.
1618:
1595:Computer security exploits
1373:: CS1 maint: url-status (
657:
639:
609:Buffer overflow protection
606:
250:
240:
230:
87:in the following example:
18:
1531:"Twilight Hack - WiiBrew"
1118:Communications of the ACM
835:Internet Security Systems
744:Data Execution Prevention
465:"My Float value = %f
372:"My Float value = %f
77:The canonical method for
38:address on the program's
1478:(in French). 2022-09-03.
1089:Bertrand, Louis (2002).
852:, and "Smash Stack" for
453:// no bounds checking...
294:
89:
1555:"Smash Stack - WiiBrew"
1318:10.1145/1866307.1866370
1130:10.1145/1096000.1096004
903:Security-Enhanced Linux
855:Super Smash Bros. Brawl
837:BlackICE Desktop Agent.
456:// Will print 96.031372
363:// Will print 10.500000
1349:Shoshitaishvili, Yan.
1228:Zhodiac (2001-12-28).
1188:Curious (2005-01-08).
1078:on September 28, 2007.
713:Bypass countermeasures
615:control-flow integrity
285:bit set to run as the
257:
247:
237:
63:security vulnerability
1283:Nergal (2001-12-28).
648:canary in a coal mine
640:Further information:
255:
245:
235:
225:with various inputs:
221:The program stack in
149:// no bounds checking
28:stack buffer overflow
1312:. pp. 559–572.
968:. pp. 169–196.
775:Randomization bypass
360:// Addr = 0x0023FF30
348:// Addr = 0x0023FF4C
32:stack buffer overrun
19:For other uses, see
1508:10.3390/app12136702
1451:10.3390/app12136702
1407:10.3390/app12136702
1043:10.1109/MSP.2004.36
721:Stack canary bypass
654:Nonexecutable stack
623:instruction pointer
569:Stacks that grow up
1590:Software anomalies
625:to malicious code.
603:Protection schemes
258:
248:
238:
1327:978-1-4503-0245-6
1066:"Stack Overflows"
914:Storage violation
262:
261:
1607:
1569:
1568:
1566:
1565:
1551:
1545:
1544:
1542:
1541:
1527:
1521:
1520:
1510:
1495:Applied Sciences
1486:
1480:
1479:
1470:
1464:
1463:
1453:
1438:Applied Sciences
1429:
1420:
1419:
1409:
1394:Applied Sciences
1385:
1379:
1378:
1372:
1364:
1362:
1361:
1346:
1340:
1339:
1305:
1299:
1298:
1280:
1274:
1273:
1261:
1250:
1244:
1243:
1225:
1219:
1218:
1210:
1204:
1203:
1185:
1179:
1178:
1172:
1164:
1156:
1150:
1149:
1109:
1103:
1102:
1097:. Archived from
1086:
1080:
1079:
1077:
1071:. Archived from
1070:
1061:
1055:
1054:
1028:
1019:
1013:
1012:
991:
980:
979:
957:
946:
945:
933:
892:Integer overflow
784:Notable examples
753:
597:
593:
589:
585:
581:
577:
547:
544:
541:
538:
535:
532:
529:
528:\x10\x10\xc0\x42
526:
523:
520:
517:
514:
511:
508:
505:
502:
499:
496:
493:
490:
487:
484:
481:
478:
475:
472:
469:
466:
463:
460:
457:
454:
451:
448:
445:
442:
439:
436:
433:
430:
427:
424:
421:
418:
415:
412:
409:
406:
403:
400:
397:
394:
391:
388:
385:
382:
379:
376:
373:
370:
367:
364:
361:
358:
355:
352:
349:
346:
343:
340:
337:
334:
331:
328:
325:
322:
319:
316:
313:
310:
307:
304:
301:
300:<string.h>
298:
276:
271:
267:
228:
227:
224:
217:
210:
207:
204:
201:
198:
195:
192:
189:
186:
183:
180:
177:
174:
171:
168:
165:
162:
159:
156:
153:
150:
147:
144:
141:
138:
135:
132:
129:
126:
123:
120:
117:
114:
111:
108:
105:
102:
99:
96:
95:<string.h>
93:
86:
16:Software anomaly
1617:
1616:
1610:
1609:
1608:
1606:
1605:
1604:
1600:Computer errors
1575:
1574:
1573:
1572:
1563:
1561:
1553:
1552:
1548:
1539:
1537:
1529:
1528:
1524:
1488:
1487:
1483:
1472:
1471:
1467:
1431:
1430:
1423:
1387:
1386:
1382:
1365:
1359:
1357:
1348:
1347:
1343:
1328:
1307:
1306:
1302:
1282:
1281:
1277:
1270:
1259:
1252:
1251:
1247:
1227:
1226:
1222:
1212:
1211:
1207:
1187:
1186:
1182:
1165:
1158:
1157:
1153:
1111:
1110:
1106:
1088:
1087:
1083:
1075:
1068:
1063:
1062:
1058:
1026:
1021:
1020:
1016:
993:
992:
983:
976:
959:
958:
949:
935:
934:
927:
922:
873:
786:
777:
769:
760:
751:
740:
728:
723:
715:
698:
662:
656:
644:
638:
611:
605:
595:
591:
587:
583:
579:
575:
571:
558:
549:
548:
545:
542:
539:
536:
533:
530:
527:
524:
521:
518:
515:
512:
509:
506:
503:
500:
497:
494:
491:
488:
485:
482:
479:
476:
473:
470:
467:
464:
461:
458:
455:
452:
449:
446:
443:
440:
437:
434:
431:
428:
425:
422:
419:
416:
413:
410:
407:
404:
401:
398:
395:
392:
389:
386:
383:
380:
377:
374:
371:
368:
365:
362:
359:
356:
353:
350:
347:
344:
341:
338:
335:
332:
329:
326:
323:
320:
317:
314:
311:
308:
306:<stdio.h>
305:
302:
299:
296:
274:
269:
265:
222:
215:
212:
211:
208:
205:
202:
199:
196:
193:
190:
187:
184:
181:
178:
175:
172:
169:
166:
163:
160:
157:
154:
151:
148:
145:
142:
139:
136:
133:
130:
127:
124:
121:
118:
115:
112:
109:
106:
103:
100:
97:
94:
91:
82:
75:
48:buffer overflow
26:In software, a
24:
17:
12:
11:
5:
1615:
1614:
1611:
1603:
1602:
1597:
1592:
1587:
1577:
1576:
1571:
1570:
1546:
1522:
1481:
1465:
1421:
1380:
1341:
1326:
1300:
1275:
1268:
1245:
1220:
1205:
1180:
1151:
1104:
1101:on 2007-09-30.
1081:
1056:
1014:
997:(1996-11-08).
981:
974:
966:Addison Wesley
947:
924:
923:
921:
918:
917:
916:
911:
908:Stack overflow
905:
900:
894:
889:
884:
879:
872:
869:
868:
867:
840:
827:
816:
813:'s SQL server.
803:
785:
782:
776:
773:
768:
765:
759:
756:
739:
736:
727:
724:
722:
719:
714:
711:
697:
694:
677:return to libc
658:Main article:
655:
652:
637:
636:Stack canaries
634:
633:
632:
629:
626:
607:Main article:
604:
601:
570:
567:
557:
554:
295:
260:
259:
249:
239:
90:
74:
71:
55:stack smashing
15:
13:
10:
9:
6:
4:
3:
2:
1613:
1612:
1601:
1598:
1596:
1593:
1591:
1588:
1586:
1585:Software bugs
1583:
1582:
1580:
1560:
1556:
1550:
1547:
1536:
1532:
1526:
1523:
1518:
1514:
1509:
1504:
1500:
1496:
1492:
1485:
1482:
1477:
1476:
1469:
1466:
1461:
1457:
1452:
1447:
1444:(13): 12–13.
1443:
1439:
1435:
1428:
1426:
1422:
1417:
1413:
1408:
1403:
1399:
1395:
1391:
1384:
1381:
1376:
1370:
1356:
1352:
1345:
1342:
1337:
1333:
1329:
1323:
1319:
1315:
1311:
1304:
1301:
1296:
1292:
1291:
1286:
1279:
1276:
1271:
1269:1-932266-67-4
1265:
1258:
1257:
1249:
1246:
1241:
1237:
1236:
1231:
1224:
1221:
1216:
1209:
1206:
1201:
1197:
1196:
1191:
1184:
1181:
1176:
1170:
1162:
1155:
1152:
1147:
1143:
1139:
1135:
1131:
1127:
1124:(11): 50–56.
1123:
1119:
1115:
1108:
1105:
1100:
1096:
1092:
1085:
1082:
1074:
1067:
1060:
1057:
1052:
1048:
1044:
1040:
1036:
1032:
1025:
1018:
1015:
1010:
1006:
1005:
1000:
996:
990:
988:
986:
982:
977:
975:0-321-44442-6
971:
967:
963:
956:
954:
952:
948:
943:
939:
932:
930:
926:
919:
915:
912:
909:
906:
904:
901:
898:
895:
893:
890:
888:
887:Heap overflow
885:
883:
880:
878:
875:
874:
870:
865:
864:modifications
861:
857:
856:
851:
850:
845:
841:
839:
836:
832:
828:
825:
821:
817:
815:
812:
808:
804:
802:
799:
796:
792:
788:
787:
783:
781:
774:
772:
766:
764:
757:
755:
749:
745:
737:
735:
733:
725:
720:
718:
712:
710:
708:
704:
696:Randomization
695:
693:
692:instruction.
690:
686:
681:
678:
673:
669:
667:
661:
653:
651:
649:
643:
635:
630:
627:
624:
620:
619:
618:
616:
610:
602:
600:
568:
566:
564:
555:
553:
293:
290:
288:
284:
280:
254:
244:
234:
229:
226:
219:
88:
85:
80:
72:
70:
68:
64:
60:
56:
51:
49:
45:
41:
37:
33:
29:
22:
1562:. Retrieved
1558:
1549:
1538:. Retrieved
1534:
1525:
1501:(16): 6702.
1498:
1494:
1484:
1474:
1468:
1441:
1437:
1400:(26): 6702.
1397:
1393:
1383:
1358:. Retrieved
1354:
1344:
1309:
1303:
1294:
1288:
1278:
1255:
1248:
1239:
1233:
1223:
1208:
1199:
1193:
1183:
1154:
1121:
1117:
1107:
1099:the original
1094:
1084:
1073:the original
1059:
1037:(4): 20–27.
1034:
1030:
1017:
1008:
1002:
961:
862:itself with
859:
853:
847:
820:Blaster worm
807:Slammer worm
778:
770:
761:
748:code segment
741:
729:
716:
699:
688:
682:
674:
670:
663:
645:
642:Canary value
612:
572:
559:
550:
291:
263:
220:
213:
76:
54:
52:
31:
27:
25:
1559:wiibrew.org
1535:wiibrew.org
1355:pwn college
1064:Burebista.
995:Levy, Elias
791:Morris worm
393:Memory map:
1579:Categories
1564:2018-01-18
1540:2018-01-18
1360:2024-09-07
920:References
882:ExecShield
877:Cybercrime
831:Witty worm
79:exploiting
40:call stack
1517:2076-3417
1460:2076-3417
1416:2076-3417
1336:207182734
1242:(58): 11.
1217:(Report).
1202:(63): 16.
1138:0001-0782
1011:(49): 14.
811:Microsoft
767:Jop chain
758:Rop chain
287:superuser
279:shellcode
67:attackers
59:webserver
1369:cite web
1297:(58): 4.
1169:cite web
871:See also
866:applied.
826:service.
477:My_Float
384:My_Float
336:My_Float
303:#include
297:#include
92:#include
84:strcpy()
1051:6647392
942:US CERT
800:server.
689:gadgets
1515:
1458:
1414:
1334:
1324:
1290:Phrack
1266:
1235:Phrack
1195:Phrack
1146:120462
1144:
1136:
1049:
1004:Phrack
972:
897:NX Bit
798:finger
596:memcpy
588:memcpy
584:memcpy
580:memcpy
537:return
531:"
471:"
459:printf
441:strlen
423:memcpy
378:"
366:printf
275:char c
200:return
131:strcpy
44:buffer
36:memory
1332:S2CID
1260:(PDF)
1159:pr1.
1142:S2CID
1076:(PDF)
1069:(PDF)
1047:S2CID
1027:(PDF)
860:Brawl
752:.text
742:When
333:float
270:foo()
266:foo()
223:foo()
1513:ISSN
1456:ISSN
1412:ISSN
1375:link
1322:ISBN
1264:ISBN
1175:link
1134:ISSN
970:ISBN
829:The
824:DCOM
818:The
805:The
795:Unix
789:The
703:ASLR
563:RISC
510:argv
504:char
498:argc
489:main
351:char
342:10.5
318:char
309:void
283:SUID
194:argv
179:argv
173:char
167:argc
158:main
122:char
107:char
98:void
1503:doi
1446:doi
1402:doi
1314:doi
1126:doi
1039:doi
844:Wii
707:PIE
666:W^X
592:foo
576:foo
519:foo
495:int
486:int
450:));
447:bar
435:bar
324:bar
312:foo
188:foo
164:int
155:int
143:bar
113:bar
101:foo
30:or
1581::
1557:.
1533:.
1511:.
1499:12
1497:.
1493:.
1454:.
1442:12
1440:.
1436:.
1424:^
1410:.
1398:12
1396:.
1392:.
1371:}}
1367:{{
1353:.
1330:.
1320:.
1295:11
1293:.
1287:.
1240:11
1238:.
1232:.
1200:11
1198:.
1192:.
1171:}}
1167:{{
1140:.
1132:.
1122:48
1120:.
1116:.
1093:.
1045:.
1033:.
1029:.
1007:.
1001:.
984:^
964:.
950:^
940:.
928:^
534:);
507:**
480:);
468:\n
387:);
375:\n
197:);
176:**
146:);
1567:.
1543:.
1519:.
1505::
1462:.
1448::
1418:.
1404::
1377:)
1363:.
1338:.
1316::
1272:.
1177:)
1163:.
1148:.
1128::
1053:.
1041::
1035:2
1009:7
978:.
944:.
750:(
546:}
543:;
540:0
522:(
516:{
513:)
501:,
492:(
483:}
474:,
462:(
444:(
438:,
432:,
429:c
426:(
381:,
369:(
357:;
354:c
345:;
339:=
330:{
327:)
321:*
315:(
216:c
209:}
206:;
203:0
191:(
185:{
182:)
170:,
161:(
152:}
140:,
137:c
134:(
128:;
125:c
119:{
116:)
110:*
104:(
23:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.