686:
38:
449:
The edition was released in
October 2011, and included a free, web-based user interface for Metasploit. Metasploit Community Edition was based on the commercial functionality of the paid-for editions with a reduced set of features, including network discovery, module browsing and manual exploitation.
656:
Metasploit
Framework operates as an open-source project and accepts contributions from the community through GitHub.com pull requests. Submissions are reviewed by a team consisting of both Rapid7 employees and senior external contributors. The majority of contributions add new modules, such as
461:
The edition was released in April 2010, and was an open-core commercial edition for security teams who need to verify vulnerabilities. It offers a graphical user interface, It integrated nmap for discovery, and added smart brute-forcing as well as automated evidence collection.
302:
exploit development framework led to the release of software vulnerability advisories often accompanied by a third party
Metasploit exploit module that highlights the exploitability, risk and remediation of that particular bug. Metasploit 3.0 began to include
47:
431:
In
October 2010, Rapid7 added Metasploit Pro, an open-core commercial Metasploit edition for penetration testers. Metasploit Pro adds onto Metasploit Express with features such as Quick Start Wizards/MetaModules, building and managing
647:
The
Metasploit Framework includes hundreds of auxiliary modules that can perform scanning, fuzzing, sniffing, and much more. There are three types of auxiliary modules namely scanners, admin and server modules.
373:
This modular approach – allowing the combination of any exploit with any payload – is the major advantage of the
Framework. It facilitates the tasks of attackers, exploit writers and payload writers.
403:
can detect target system vulnerabilities. Metasploit can import vulnerability scanner data and compare the identified vulnerabilities to existing exploit modules for accurate exploitation.
379:
To choose an exploit and payload, some information about the target system is needed, such as operating system version and installed network services. This information can be gleaned with
419:
The free version. It contains a command line interface, third-party import, manual exploitation and manual brute forcing. This free version of the
Metasploit project also includes
436:
campaigns, web application testing, an advanced Pro
Console, dynamic payloads for anti-virus evasion, integration with Nexpose for ad-hoc vulnerability scans, and VPN pivoting.
1285:
280:. On October 21, 2009, the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability management solutions.
1065:
366:
Choosing the encoding technique so that hexadecimal opcodes known as "bad characters" are removed from the payload, these characters will cause the exploit to fail.
1036:
453:
On July 18, 2019, Rapid7 announced the end-of-sale of
Metasploit Community Edition. Existing users were able to continue using it until their license expired.
498:
Cobalt Strike is a collection of threat emulation tools provided by HelpSystems to work with the
Metasploit Framework. Cobalt Strike includes all features of
1173:
728:
1198:
1300:
291:
tools, Metasploit can be used for both legitimate and unauthorized activities. Since the acquisition of the Metasploit Framework, Rapid7 has added an
376:
Metasploit runs on Unix (including Linux and macOS) and on Windows. The Metasploit Framework can be extended to use add-ons in multiple languages.
1330:
1006:
929:
793:
307:
tools, used to discover software vulnerabilities, rather than just exploits for known bugs. This avenue can be seen with the integration of the
1320:
1325:
1290:
632:
Meterpreter (the Metasploit Interpreter) enables users to control the screen of a device using VNC and to browse, upload and download files.
852:
691:
1144:
1310:
1238:
1315:
759:
216:
476:
is a graphical cyber attack management tool for the Metasploit Project that visualizes targets and recommends exploits. It is a
1295:
1275:
1270:
947:
822:
287:' Core Impact, Metasploit can be used to test the vulnerability of computer systems or to break into remote systems. Like many
260:
and evasion tools, some of which are built into the Metasploit Framework. In various operating systems it comes pre installed.
1057:
1280:
587:
433:
411:
There are several interfaces for Metasploit available. The most popular are maintained by Rapid7 and Strategic Cyber LLC.
1222:
423:, a well known security scanner, and a compiler for Ruby, the language in which this version of Metasploit was written.
124:
1241:). Written by Vincent Liu, chapter 12 explains how to use Metasploit to develop a buffer overflow exploit from scratch.
908:
595:
547:
384:
277:
246:
145:
101:
1028:
599:
515:
284:
224:
638:
Static payloads enable static IP address/port forwarding for communication between the host and the client system.
1305:
1231:
Sockets, Shellcode, Porting & Coding: Reverse Engineering Exploits and Tool Coding for Security Professionals
1090:
973:
360:
591:
877:
1165:
724:
1194:
257:
1119:
487:
collaboration allowing for shared sessions, data, and communication through a single Metasploit instance.
359:(code that will be executed on the target system upon successful entry; for instance, a remote shell or a
392:
998:
933:
783:
499:
477:
473:
288:
239:
220:
164:
930:"ACSSEC-2005-11-25-0x1 VMWare Workstation 5.5.0 <= build-18007 GSX Server Variants And Others"
629:
Command shell enables users to run collection scripts or run arbitrary commands against the host.
355:
249:
code against a remote target machine. Other important sub-projects include the Opcode Database,
844:
1140:
37:
1234:
396:
335:
212:
169:
480:
176:
152:
951:
635:
Dynamic payloads enable users to evade anti-virus defense by generating unique payloads.
157:
749:
510:
Metasploit currently has over 2074 exploits, organized under the following platforms:
1264:
380:
51:
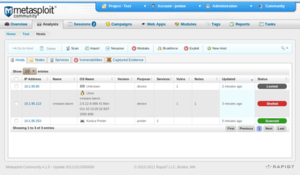
Metasploit Community showing three hosts, two of which were compromised by an exploit
814:
46:
331:
323:
Optionally checking whether the intended target system is vulnerable to an exploit.
664:
269:
182:
62:
948:"Month of Kernel Bugs – Broadcom Wireless Driver Probe Response SSID Overflow"
681:
551:
69:
57:
502:
and adds post-exploitation tools, in addition to report generation features.
900:
559:
292:
250:
617:
is based on FreeBSD, and some FreeBSD exploits may work, while most won't.
484:
299:
874:"Vulnerability exploitation tools – SecTools Top Network Security Tools"
1112:"Adversary Simulation and Red Team Operations Software - Cobalt Strike"
607:
575:
567:
535:
531:
400:
304:
1086:
965:
276:. By 2007, the Metasploit Framework had been completely rewritten in
17:
788:
754:
571:
563:
420:
319:
The basic steps for exploiting a system using the Framework include.
308:
228:
330:(code that enters a target system by taking advantage of one of its
873:
704:
579:
555:
539:
527:
347:
343:
465:
On June 4, 2019, Rapid7 discontinued Metasploit Express Edition.
283:
Like comparable commercial products such as Immunity's Canvas or
699:
603:
543:
523:
388:
339:
311:
wireless (802.11) toolset into Metasploit 3.0 in November 2006.
273:
625:
Metasploit currently has over 592 payloads. Some of them are:
966:"Penetration Testing Tool, Metasploit, Free Download - Rapid7"
614:
583:
519:
511:
194:
1253:
1111:
130:
1058:"Announcement: End of Life for Metasploit Express Edition"
363:). Metasploit often recommends a payload that should work.
450:
Metasploit Community was included in the main installer.
1223:
Powerful payloads: The evolution of exploit frameworks
993:
991:
673:
Dean McNamee (Spoonm) (core developer from 2003–2008)
189:
175:
163:
151:
141:
123:
100:
78:
68:
56:
1029:"End of Sale Announced for Metasploit Community"
845:"Metasploit Editions: Network Pen Testing Tool"
8:
778:
776:
562:, multi (applicable to multiple platforms),
490:The latest release of Armitage was in 2015.
30:
1286:Free and open-source software organizations
670:Matt Miller (core developer from 2004–2008)
295:proprietary edition called Metasploit Pro.
36:
29:
272:in 2003 as a portable network tool using
231:, Massachusetts-based security company,
215:project that provides information about
107:6.3.36 / September 28, 2023
716:
1229:Chapter 12: Writing Exploits III from
483:tool notable for its contributions to
298:Metasploit's emerging position as the
245:, a tool for developing and executing
976:from the original on 24 December 2017
707:Open Web Application Security Project
7:
880:from the original on 17 October 2011
750:"Tags · rapid7/Metasploit-framework"
692:Free and open-source software portal
185:, Community/Express/Pro: Proprietary
950:. November 11, 2006. Archived from
932:. December 20, 2005. Archived from
334:; about 900 different exploits for
1141:"Armitage vs Cobalt Hooked Strike"
1009:from the original on 10 March 2015
238:Its best-known sub-project is the
25:
825:from the original on 15 July 2011
1301:Free software programmed in Ruby
1226:, searchsecurity.com, 2005-10-20
684:
256:The Metasploit Project includes
45:
1201:from the original on 2016-09-24
1176:from the original on 2018-07-26
1147:from the original on 2016-03-19
1122:from the original on 2019-01-28
1093:from the original on 2016-01-14
1087:"Armitage A GUI for Metasploit"
1068:from the original on 2020-07-16
1039:from the original on 2020-07-13
911:from the original on 2017-01-16
855:from the original on 2023-07-20
796:from the original on 2021-01-30
762:from the original on 2022-12-19
731:from the original on 2023-08-03
725:"A Brief History of Metasploit"
1331:Software using the BSD license
253:archive and related research.
27:Computer security testing tool
1:
1321:Unix network-related software
1166:"rapid7/metasploit-framework"
667:(founder and chief architect)
660:List of original developers:
1326:Pentesting software toolkits
1291:Cross-platform free software
1195:"Contributing to Metasploit"
326:Choosing and configuring an
227:development. It is owned by
385:TCP/IP stack fingerprinting
353:Choosing and configuring a
84:; 21 years ago
1347:
285:Core Security Technologies
268:Metasploit was created by
1311:Windows security software
119:
96:
44:
35:
217:security vulnerabilities
1316:MacOS security software
1143:. Strategic Cyber LLC.
1089:. Strategic Cyber LLC.
1296:Free security software
1276:Security testing tools
1271:Anti-forensic software
815:"Rapid7 Press Release"
784:"3-clause BSD license"
657:exploits or scanners.
393:Vulnerability scanners
369:Executing the exploit.
350:systems are included).
1281:Cryptographic attacks
999:"Metasploit editions"
440:Discontinued editions
1233:by James C. Foster (
478:free and open source
289:information security
243:Metasploit Framework
954:on January 3, 2013.
221:penetration testing
32:
905:www.exploit-db.com
434:social engineering
209:Metasploit Project
58:Original author(s)
643:Auxiliary modules
415:Framework Edition
213:computer security
205:
204:
16:(Redirected from
1338:
1306:Software testing
1257:
1256:
1254:Official website
1210:
1209:
1207:
1206:
1191:
1185:
1184:
1182:
1181:
1162:
1156:
1155:
1153:
1152:
1137:
1131:
1130:
1128:
1127:
1116:cobaltstrike.com
1108:
1102:
1101:
1099:
1098:
1083:
1077:
1076:
1074:
1073:
1054:
1048:
1047:
1045:
1044:
1025:
1019:
1018:
1016:
1014:
995:
986:
985:
983:
981:
962:
956:
955:
944:
938:
937:
926:
920:
919:
917:
916:
896:
890:
889:
887:
885:
870:
864:
863:
861:
860:
841:
835:
834:
832:
830:
811:
805:
804:
802:
801:
780:
771:
770:
768:
767:
746:
740:
739:
737:
736:
721:
694:
689:
688:
687:
481:network security
201:
198:
196:
153:Operating system
137:
134:
132:
114:
112:
92:
90:
85:
49:
40:
33:
21:
1346:
1345:
1341:
1340:
1339:
1337:
1336:
1335:
1261:
1260:
1252:
1251:
1248:
1218:
1216:Further reading
1213:
1204:
1202:
1197:. Rapid7, Inc.
1193:
1192:
1188:
1179:
1177:
1164:
1163:
1159:
1150:
1148:
1139:
1138:
1134:
1125:
1123:
1110:
1109:
1105:
1096:
1094:
1085:
1084:
1080:
1071:
1069:
1056:
1055:
1051:
1042:
1040:
1027:
1026:
1022:
1012:
1010:
997:
996:
989:
979:
977:
964:
963:
959:
946:
945:
941:
928:
927:
923:
914:
912:
898:
897:
893:
883:
881:
872:
871:
867:
858:
856:
843:
842:
838:
828:
826:
813:
812:
808:
799:
797:
782:
781:
774:
765:
763:
748:
747:
743:
734:
732:
723:
722:
718:
714:
690:
685:
683:
680:
654:
645:
623:
508:
496:
471:
459:
447:
442:
429:
417:
409:
317:
266:
193:
129:
115:
110:
108:
88:
86:
83:
79:Initial release
52:
28:
23:
22:
15:
12:
11:
5:
1344:
1342:
1334:
1333:
1328:
1323:
1318:
1313:
1308:
1303:
1298:
1293:
1288:
1283:
1278:
1273:
1263:
1262:
1259:
1258:
1247:
1246:External links
1244:
1243:
1242:
1227:
1217:
1214:
1212:
1211:
1186:
1157:
1132:
1103:
1078:
1064:. 2018-06-04.
1049:
1035:. 2019-07-18.
1020:
987:
957:
939:
936:on 2007-01-07.
921:
891:
865:
836:
806:
772:
741:
715:
713:
710:
709:
708:
702:
696:
695:
679:
676:
675:
674:
671:
668:
653:
650:
644:
641:
640:
639:
636:
633:
630:
622:
619:
507:
504:
495:
492:
470:
467:
458:
455:
446:
443:
441:
438:
428:
425:
416:
413:
408:
405:
387:tools such as
371:
370:
367:
364:
351:
324:
316:
313:
265:
262:
203:
202:
191:
187:
186:
179:
173:
172:
167:
161:
160:
158:Cross-platform
155:
149:
148:
143:
139:
138:
127:
121:
120:
117:
116:
106:
104:
102:Stable release
98:
97:
94:
93:
80:
76:
75:
72:
66:
65:
60:
54:
53:
50:
42:
41:
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
1343:
1332:
1329:
1327:
1324:
1322:
1319:
1317:
1314:
1312:
1309:
1307:
1304:
1302:
1299:
1297:
1294:
1292:
1289:
1287:
1284:
1282:
1279:
1277:
1274:
1272:
1269:
1268:
1266:
1255:
1250:
1249:
1245:
1240:
1239:1-59749-005-9
1236:
1232:
1228:
1225:
1224:
1220:
1219:
1215:
1200:
1196:
1190:
1187:
1175:
1171:
1167:
1161:
1158:
1146:
1142:
1136:
1133:
1121:
1117:
1113:
1107:
1104:
1092:
1088:
1082:
1079:
1067:
1063:
1059:
1053:
1050:
1038:
1034:
1030:
1024:
1021:
1008:
1004:
1000:
994:
992:
988:
975:
971:
967:
961:
958:
953:
949:
943:
940:
935:
931:
925:
922:
910:
906:
902:
895:
892:
879:
875:
869:
866:
854:
850:
846:
840:
837:
824:
820:
816:
810:
807:
795:
791:
790:
785:
779:
777:
773:
761:
757:
756:
751:
745:
742:
730:
726:
720:
717:
711:
706:
703:
701:
698:
697:
693:
682:
677:
672:
669:
666:
663:
662:
661:
658:
651:
649:
642:
637:
634:
631:
628:
627:
626:
620:
618:
616:
611:
609:
605:
601:
597:
593:
589:
585:
581:
577:
573:
569:
565:
561:
557:
553:
549:
545:
541:
537:
533:
529:
525:
521:
517:
513:
505:
503:
501:
494:Cobalt Strike
493:
491:
488:
486:
482:
479:
475:
468:
466:
463:
456:
454:
451:
444:
439:
437:
435:
426:
424:
422:
414:
412:
406:
404:
402:
398:
394:
390:
386:
382:
381:port scanning
377:
374:
368:
365:
362:
358:
357:
352:
349:
345:
341:
337:
333:
329:
325:
322:
321:
320:
314:
312:
310:
306:
301:
296:
294:
290:
286:
281:
279:
275:
271:
263:
261:
259:
258:anti-forensic
254:
252:
248:
244:
241:
236:
234:
230:
226:
225:IDS signature
222:
218:
214:
210:
200:
192:
188:
184:
180:
178:
174:
171:
168:
166:
162:
159:
156:
154:
150:
147:
144:
140:
136:
128:
126:
122:
118:
105:
103:
99:
95:
81:
77:
73:
71:
67:
64:
61:
59:
55:
48:
43:
39:
34:
19:
1230:
1221:
1203:. Retrieved
1189:
1178:. Retrieved
1169:
1160:
1149:. Retrieved
1135:
1124:. Retrieved
1115:
1106:
1095:. Retrieved
1081:
1070:. Retrieved
1061:
1052:
1041:. Retrieved
1032:
1023:
1011:. Retrieved
1002:
978:. Retrieved
969:
960:
952:the original
942:
934:the original
924:
913:. Retrieved
904:
901:"Metasploit"
899:Metasploit.
894:
882:. Retrieved
868:
857:. Retrieved
848:
839:
827:. Retrieved
818:
809:
798:. Retrieved
787:
764:. Retrieved
753:
744:
733:. Retrieved
719:
659:
655:
652:Contributors
646:
624:
612:
509:
497:
489:
472:
464:
460:
452:
448:
430:
418:
410:
378:
375:
372:
354:
327:
318:
297:
282:
267:
255:
242:
237:
232:
219:and aids in
208:
206:
74:Rapid7, Inc.
70:Developer(s)
1062:Rapid7 Blog
1033:Rapid7 Blog
1013:16 February
980:18 February
884:18 February
829:18 February
665:H. D. Moore
270:H. D. Moore
240:open-source
197:.metasploit
181:Framework:
63:H. D. Moore
1265:Categories
1205:2014-06-09
1180:2017-01-14
1151:2013-11-18
1126:2019-01-22
1097:2013-11-18
1072:2020-07-13
1043:2020-07-13
1005:. rapid7.
1003:rapid7.com
915:2017-01-14
859:2023-08-03
800:2013-06-24
766:2024-05-23
735:2024-05-23
712:References
613:Note that
552:JavaScript
407:Interfaces
361:VNC server
142:Written in
125:Repository
111:2023-09-28
31:Metasploit
615:Apple iOS
560:mainframe
445:Community
315:Framework
293:open core
251:shellcode
1199:Archived
1174:Archived
1145:Archived
1120:Archived
1091:Archived
1066:Archived
1037:Archived
1007:Archived
974:Archived
909:Archived
878:Archived
853:Archived
823:Archived
794:Archived
760:Archived
729:Archived
678:See also
621:Payloads
506:Exploits
500:Armitage
485:red team
474:Armitage
469:Armitage
395:such as
300:de facto
170:Security
608:Windows
600:Solaris
576:OpenBSD
568:NetWare
536:FreeBSD
532:Firefox
516:Android
457:Express
401:OpenVAS
356:payload
336:Windows
328:exploit
305:fuzzing
264:History
247:exploit
190:Website
177:License
135:/rapid7
109: (
87: (
1237:
1170:GitHub
970:Rapid7
849:Rapid7
819:Rapid7
789:GitHub
755:GitHub
606:, and
588:Python
572:NodeJS
564:NetBSD
421:Zenmap
399:, and
397:Nessus
309:lorcon
233:Rapid7
229:Boston
131:github
18:Rapid7
705:OWASP
580:macOS
556:Linux
540:HP-UX
528:Cisco
348:macOS
344:Linux
211:is a
1235:ISBN
1015:2013
982:2015
886:2015
831:2015
700:w3af
604:Unix
596:Ruby
548:Java
544:Irix
524:BSDi
389:Nmap
383:and
346:and
340:Unix
332:bugs
278:Ruby
274:Perl
223:and
207:The
199:.com
165:Type
146:Ruby
133:.com
89:2003
82:2003
584:PHP
520:BSD
512:AIX
427:Pro
195:www
183:BSD
1267::
1172:.
1168:.
1118:.
1114:.
1060:.
1031:.
1001:.
990:^
972:.
968:.
907:.
903:.
876:.
851:.
847:.
821:.
817:.
792:.
786:.
775:^
758:.
752:.
727:.
610:.
602:,
598:,
594:,
590:,
586:,
582:,
578:,
574:,
570:,
566:,
558:,
554:,
550:,
546:,
542:,
538:,
534:,
530:,
526:,
522:,
518:,
514:,
391:.
338:,
235:.
1208:.
1183:.
1154:.
1129:.
1100:.
1075:.
1046:.
1017:.
984:.
918:.
888:.
862:.
833:.
803:.
769:.
738:.
592:R
342:/
113:)
91:)
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.