1377:(NTP) is through a command called monlist, which sends the details of the last 600 hosts that have requested the time from the NTP server back to the requester. A small request to this time server can be sent using a spoofed source IP address of some victim, which results in a response 556.9 times the size of the request being sent to the victim. This becomes amplified when using botnets that all send requests with the same spoofed IP source, which will result in a massive amount of data being sent back to the victim. It is very difficult to defend against these types of attacks because the response data is coming from legitimate servers. These attack requests are also sent through UDP, which does not require a connection to the server. This means that the source IP is not verified when a request is received by the server. To bring awareness of these vulnerabilities, campaigns have been started that are dedicated to finding amplification vectors which have led to people fixing their resolvers or having the resolvers shut down completely.
529:(ISO). The model groups similar communication functions into one of seven logical layers. A layer serves the layer above it and is served by the layer below it. For example, a layer that provides error-free communications across a network provides the communications path needed by applications above it, while it calls the next lower layer to send and receive packets that traverse that path. In the OSI model, the definition of its application layer is narrower in scope than is often implemented. The OSI model defines the application layer as being the user interface. The OSI application layer is responsible for displaying data and images to the user in a human-recognizable format and to interface with the
566:. These attacks can persist for weeks; the longest continuous period noted so far lasted 38 days. This attack involved approximately 50+ petabits (50,000+ terabits) of malicious traffic. Attackers in this scenario may tactically switch between several targets to create a diversion to evade defensive DDoS countermeasures but all the while eventually concentrating the main thrust of the attack onto a single victim. In this scenario, attackers with continuous access to several very powerful network resources are capable of sustaining a prolonged campaign generating enormous levels of unamplified DDoS traffic. APDoS attacks are characterized by:
480:. The attacker generates a flood of traffic until a cloud-hosted service scales outwards to handle the increase of traffic, then halts the attack, leaving the victim with over-provisioned resources. When the victim scales back down, the attack resumes, causing resources to scale back up again. This can result in a reduced quality of service during the periods of scaling up and down and a financial drain on resources during periods of over-provisioning while operating with a lower cost for an attacker compared to a normal DDoS attack, as it only needs to be generating traffic for a portion of the attack period.
1800:. In essence, these techniques are statistical methods of assessing the behavior of incoming requests to detect if something unusual or abnormal is going on. An analogy is to a brick-and-mortar department store where customers spend, on average, a known percentage of their time on different activities such as picking up items and examining them, putting them back, filling a basket, waiting to pay, paying, and leaving. If a mob of customers arrived in the store and spent all their time picking up items and putting them back, but never made any purchases, this could be flagged as unusual behavior.
752:. In this case, normally application-used resources are tied to a needed quality of service (QoS) level (e.g. responses should be less than 200 ms) and this rule is usually linked to automated software (e.g. Amazon CloudWatch) to raise more virtual resources from the provider to meet the defined QoS levels for the increased requests. The main incentive behind such attacks may be to drive the application owner to raise the elasticity levels to handle the increased application traffic, to cause financial losses, or force them to become less competitive. A
201:), the incoming traffic flooding the victim originates from many different sources. More sophisticated strategies are required to mitigate this type of attack; simply attempting to block a single source is insufficient as there are multiple sources. A DoS or DDoS attack is analogous to a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, thus disrupting trade and losing the business money. Criminal perpetrators of DoS attacks often target sites or services hosted on high-profile
505:, there have been "51 percent more application layer attacks" from Q4 2013 to Q4 2014 and "16 percent more" from Q3 2014 to Q4 2014. In November 2017; Junade Ali, an engineer at Cloudflare noted that whilst network-level attacks continue to be of high capacity, they were occurring less frequently. Ali further noted that although network-level attacks were becoming less frequent, data from Cloudflare demonstrated that application-layer attacks were still showing no sign of slowing down.
546:. An application layer DDoS attack is done mainly for specific targeted purposes, including disrupting transactions and access to databases. It requires fewer resources than network layer attacks but often accompanies them. An attack may be disguised to look like legitimate traffic, except it targets specific application packets or functions. The attack on the application layer can disrupt services such as the retrieval of information or search functions on a website.
142:
241:
2074:
1673:(UPnP) protocol to get past network security and flood a target's network and servers. The attack is based on a DNS amplification technique, but the attack mechanism is a UPnP router that forwards requests from one outer source to another. The UPnP router returns the data on an unexpected UDP port from a bogus IP address, making it harder to take simple action to shut down the traffic flood. According to the
1945:
well-prepared site, for example, as part of a news story. The result is that a significant proportion of the primary site's regular users – potentially hundreds of thousands of people – click that link in the space of a few hours, having the same effect on the target website as a DDoS attack. A VIPDoS is the same, but specifically when the link was posted by a celebrity. When
6546:
1865:
incoming traffic on this port because doing so will prevent the server from receiving and serving legitimate traffic. Additionally, firewalls may be too deep in the network hierarchy, with routers being adversely affected before the traffic gets to the firewall. Also, many security tools still do not support IPv6 or may not be configured properly, so the firewalls may be bypassed during the attacks.
444:) further complicating identifying and defeating the attack. These attacker advantages cause challenges for defense mechanisms. For example, merely purchasing more incoming bandwidth than the current volume of the attack might not help, because the attacker might be able to simply add more attack machines. The scale of DDoS attacks has continued to rise over recent years, by 2016 exceeding a
773:, can be more difficult to detect and can disrupt and hamper connection to websites for prolonged periods of time, potentially causing more overall disruption than a denial-of-service attack. Exposure of degradation-of-service attacks is complicated further by the matter of discerning whether the server is really being attacked or is experiencing higher than normal legitimate traffic loads.
43:
1922:(bogus IP filtering) to detect and remediate DoS attacks through automatic rate filtering and WAN Link failover and balancing. These schemes will work as long as the DoS attacks can be prevented by using them. For example, SYN flood can be prevented using delayed binding or TCP splicing. Similarly, content-based DoS may be prevented using deep packet inspection. Attacks using
943:(URIs) in the requests require complicated time-consuming algorithms or database operations which may exhaust the resources of the targeted web server. In 2004, a Chinese hacker nicknamed KiKi invented a hacking tool to send these kinds of requests to attack a NSFOCUS firewall named Collapsar, and thus the hacking tool was known as Challenge Collapsar, or
2005:: massive numbers of would-be YouTube.com users accidentally typed the tube company's URL, utube.com. As a result, the tube company ended up having to spend large amounts of money on upgrading its bandwidth. The company appears to have taken advantage of the situation, with utube.com now containing ads for advertisement revenue. In March 2014, after
6199:
which was owned by Sony when it suffered at the hands of DerpTrolling. Between
December 2013 and January 2014, Thompson also brought down Valve's Steam – the largest digital distribution platform for PC gaming – as well as Electronic Arts' Origin service and Blizzard's BattleNet. The disruption lasted anywhere from hours to days.
1505:, send back a TCP/SYN-ACK packet, and wait for a packet in response from the sender address. However, because the sender's address is forged, the response never comes. These half-open connections exhaust the available connections the server can make, keeping it from responding to legitimate requests until after the attack ends.
1604:: A scammer contacts consumers with a bogus debt collection demand and threatens to send police; when the victim balks, the scammer floods local police numbers with calls on which caller ID is spoofed to display the victim's number. Police soon arrive at the victim's residence attempting to find the origin of the calls.
726:. Attacks may use specific packet types or connection requests to saturate finite resources by, for example, occupying the maximum number of open connections or filling the victim's disk space with logs. An attacker with shell-level access to a victim's computer may slow it until it is unusable or crash it by using a
6198:
Austin
Thompson, aka DerpTrolling, who came to prominence in 2013 by launching Distributed Denial of Service (DDoS) attacks against major video game companies, has been sentenced to 27 months in prison by a federal court. Thompson, a resident of Utah, will also have to pay $ 95,000 to Daybreak Games,
2149:
announced that "actions are currently underway worldwide to track down the users" of
Webstresser.org, a former DDoS marketplace that was shut down in April 2018 as part of Operation Power Off. Europol said UK police were conducting a number of "live operations" targeting over 250 users of Webstresser
1944:
An unintentional denial-of-service can occur when a system ends up denied, not due to a deliberate attack by a single individual or group of individuals, but simply due to a sudden enormous spike in popularity. This can happen when an extremely popular website posts a prominent link to a second, less
810:
to connect to handlers, which are compromised systems that issue commands to the zombie agents, which in turn facilitate the DDoS attack. Agents are compromised via the handlers by the attacker. Each handler can control up to a thousand agents. In some cases a machine may become part of a DDoS attack
185:
the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. The range of attacks varies widely, spanning from inundating a server with millions of requests to slow its performance, overwhelming a server
1851:
More focused on the problem than IPS, a DoS defense system (DDS) can block connection-based DoS attacks and those with legitimate content but bad intent. A DDS can also address both protocol attacks (such as teardrop and ping of death) and rate-based attacks (such as ICMP floods and SYN floods). DDS
1479:
A slow read attack sends legitimate application layer requests, but reads responses very slowly, keeping connections open longer hoping to exhaust the server's connection pool. The slow read is achieved by advertising a very small number for the TCP Receive Window size, and at the same time emptying
1393:
to infect hundreds of thousands of IoT devices across the internet. The worm propagates through networks and systems taking control of poorly protected IoT devices such as thermostats, Wi-Fi-enabled clocks, and washing machines. The owner or user will usually have no immediate indication of when the
1109:
the device, rendering it unusable for its original purpose until it can be repaired or replaced. The PDoS is a pure hardware-targeted attack that can be much faster and requires fewer resources than using a botnet in a DDoS attack. Because of these features, and the potential and high probability of
1084:
Permanent denial-of-service (PDoS), also known loosely as phlashing, is an attack that damages a system so badly that it requires replacement or reinstallation of hardware. Unlike the distributed denial-of-service attack, a PDoS attack exploits security flaws which allow remote administration on the
913:
field in the header, and wait for the entire body of the message to be transmitted, which can take a very long time. The attacker establishes hundreds or even thousands of such connections until all resources for incoming connections on the victim server are exhausted, making any further connections
500:
processes. The attack over-exercises specific functions or features of a website with the intention to disable those functions or features. This application-layer attack is different from an entire network attack, and is often used against financial institutions to distract IT and security personnel
349:
significantly shaped the cyberthreat landscape, with an increase in cyberattacks attributed to both state-sponsored actors and global hacktivist activities. The most notable event was a DDoS attack in
February, the largest Ukraine has encountered, disrupting government and financial sector services.
1748:
Defensive responses to denial-of-service attacks typically involve the use of a combination of attack detection, traffic classification and response tools, aiming to block traffic the tools identify as illegitimate and allow traffic that they identify as legitimate. A list of response tools include
1362:
amplification attacks involves an attacker sending a DNS name lookup request to one or more public DNS servers, spoofing the source IP address of the targeted victim. The attacker tries to request as much information as possible, thus amplifying the DNS response that is sent to the targeted victim.
612:
services, which have simple web-based front ends, and accept payment over the web. Marketed and promoted as stress-testing tools, they can be used to perform unauthorized denial-of-service attacks, and allow technically unsophisticated attackers access to sophisticated attack tools. Usually powered
435:
Multiple attack machines can generate more attack traffic than a single machine and are harder to disable, and the behavior of each attack machine can be stealthier, making the attack harder to track and shut down. Since the incoming traffic flooding the victim originates from different sources, it
1795:
Approaches to detection of DDoS attacks against cloud-based applications may be based on an application layer analysis, indicating whether incoming bulk traffic is legitimate. These approaches mainly rely on an identified path of value inside the application and monitor the progress of requests on
1561:
field, indicating the starting position, or offset, of the data contained in a fragmented packet relative to the data in the original packet. If the sum of the offset and size of one fragmented packet differs from that of the next fragmented packet, the packets overlap. When this happens, a server
1488:
A sophisticated low-bandwidth DDoS attack is a form of DoS that uses less traffic and increases its effectiveness by aiming at a weak point in the victim's system design, i.e., the attacker sends traffic consisting of complicated requests to the system. Essentially, a sophisticated DDoS attack is
1770:
traffic (DDoS and also other common internet attacks) and only passes good legitimate traffic to the victim server. The victim needs central connectivity to the
Internet to use this kind of service unless they happen to be located within the same facility as the cleaning center. DDoS attacks can
971:
packets with the source address faked to appear to be the address of the victim. Most devices on a network will, by default, respond to this by sending a reply to the source IP address. If the number of machines on the network that receive and respond to these packets is very large, the victim's
357:
In
February 2023, Cloudflare faced a 71 million/requests per second attack which Cloudflare claims was the largest HTTP DDoS attack at the time. HTTP DDoS attacks are measured by HTTP requests per second instead of packets per second or bits per second. On July 10, 2023, the fanfiction platform
1864:
can be adjusted to deny all incoming traffic from the attackers, based on protocols, ports, or the originating IP addresses. More complex attacks will however be hard to block with simple rules: for example, if there is an ongoing attack on port 80 (web service), it is not possible to drop all
541:
The simplest DoS attack relies primarily on brute force, flooding the target with an overwhelming flux of packets, oversaturating its connection bandwidth or depleting the target's system resources. Bandwidth-saturating floods rely on the attacker's ability to generate the overwhelming flux of
781:
If an attacker mounts an attack from a single host, it would be classified as a DoS attack. Any attack against availability would be classed as a denial-of-service attack. On the other hand, if an attacker uses many systems to simultaneously launch attacks against a remote host, this would be
1146:) can be considered one form of reflected attack, as the flooding hosts send Echo Requests to the broadcast addresses of mis-configured networks, thereby enticing hosts to send Echo Reply packets to the victim. Some early DDoS programs implemented a distributed form of this attack.
1985:
routers have overloaded NTP servers by flooding them without respecting the restrictions of client types or geographical limitations. Similar unintentional denial-of-service can also occur via other media, e.g. when a URL is mentioned on television. If a server is being indexed by
1154:
Amplification attacks are used to magnify the bandwidth that is sent to a victim. Many services can be exploited to act as reflectors, some harder to block than others. US-CERT have observed that different services may result in different amplification factors, as tabulated below:
689:
which in turn facilitate the DDoS attack. Agents are compromised via the handlers by the attacker using automated routines to exploit vulnerabilities in programs that accept remote connections running on the targeted remote hosts. Each handler can control up to a thousand agents.
1589:
A scammer contacts the victim's banker or broker, impersonating the victim to request a funds transfer. The banker's attempt to contact the victim for verification of the transfer fails as the victim's telephone lines are being flooded with bogus calls, rendering the victim
908:
field to specify the size of the message body to follow. However, the attacker then proceeds to send the actual message body at an extremely slow rate (e.g. 1 byte/110 seconds). Due to the entire message being correct and complete, the target server will attempt to obey the
1394:
device becomes infected. The IoT device itself is not the direct target of the attack, it is used as a part of a larger attack. Once the hacker has enslaved the desired number of devices, they instruct the devices to try to contact an ISP. In
October 2016, a Mirai botnet
411:
Denial-of-service attacks are characterized by an explicit attempt by attackers to prevent legitimate use of a service. There are two general forms of DoS attacks: those that crash services and those that flood services. The most serious attacks are distributed.
2017:
service on which users could help search for the missing jet in satellite images. The response overwhelmed the company's servers. An unintentional denial-of-service may also result from a prescheduled event created by the website itself, as was the case of the
1949:
in 2009, websites such as Google and
Twitter slowed down or even crashed. Many sites' servers thought the requests were from a virus or spyware trying to cause a denial-of-service attack, warning users that their queries looked like "automated requests from a
1881:
capabilities. They, too, are manually set. Most routers can be easily overwhelmed under a DoS attack. Nokia SR-OS using FP4 or FP5 processors offers DDoS protection. Nokia SR-OS also uses big data analytics-based Nokia
Deepfield Defender for DDoS protection.
1831:(IPS) are effective if the attacks have signatures associated with them. However, the trend among attacks is to have legitimate content but bad intent. Intrusion-prevention systems that work on content recognition cannot block behavior-based DoS attacks. An
869:
and attempt to exhaust the destination SYN queue or the server bandwidth. Because the source IP addresses can be trivially spoofed, an attack could come from a limited set of sources, or may even originate from a single host. Stack enhancements such as
366:, claiming the attack for religious and political reasons, was viewed skeptically by AO3 and experts. Flashpoint, a threat intelligence vendor, noted the group's past activities but doubted their stated motives. AO3, supported by the non-profit
1641:) by the number of calls originated. By occupying lines continuously with repeated automated calls, the victim is prevented from making or receiving both routine and emergency telephone calls. Related exploits include SMS flooding attacks and
390:. Switzerland's National Cyber Security Centre quickly mitigated the attack, ensuring core federal services remained secure, despite temporary accessibility issues on some websites. In October 2023, exploitation of a new vulnerability in the
1414:
RUDY attack targets web applications by starvation of available sessions on the web server. Much like
Slowloris, RUDY keeps sessions at halt using never-ending POST transmissions and sending an arbitrarily large content-length header value.
2049:
sent to the victim. In general, the victim machine cannot distinguish between the spoofed packets and legitimate packets, so the victim responds to the spoofed packets as it normally would. These response packets are known as backscatter.
1935:
Threats may be associated with specific TCP or UDP port numbers. Blocking these ports at the firewall can mitigated the attack. For example, in an SSDP reflection attack; the key mitigation is to block incoming UDP traffic on port 1900.
887:
In 2015, DDoS botnets such as DD4BC grew in prominence, taking aim at financial institutions. Cyber-extortionists typically begin with a low-level attack and a warning that a larger attack will be carried out if a ransom is not paid in
1620:
were used to flood political opponents with spurious calls to jam phone banks on election day. Widespread publication of a number can also flood it with enough calls to render it unusable, as happened by accident in 1981 with multiple
922:
will, by default, accept requests up to 2GB in size, this attack can be particularly powerful. HTTP slow POST attacks are difficult to differentiate from legitimate connections and are therefore able to bypass some protection systems.
440:. It also makes it difficult to distinguish legitimate user traffic from attack traffic when spread across multiple points of origin. As an alternative or augmentation of a DDoS, attacks may involve forging of IP sender addresses (
1957:
News sites and link sites – sites whose primary function is to provide links to interesting content elsewhere on the Internet – are most likely to cause this phenomenon. The canonical example is the
874:
may be effective mitigation against SYN queue flooding but do not address bandwidth exhaustion. In 2022, TCP attacks were the leading method in DDoS incidents, accounting for 63% of all DDoS activity. This includes tactics like
768:
Pulsing zombies are compromised computers that are directed to launch intermittent and short-lived floodings of victim websites with the intent of merely slowing it rather than crashing it. This type of attack, referred to as
394:
protocol resulted in the record for largest HTTP DDoS attack being broken twice, once with a 201 million requests per second attack observed by Cloudflare, and again with a 398 million requests per second attack observed by
1597:
for thousands of dollars. When the consumer objects, the scammer retaliates by flooding the victim's employer with automated calls. In some cases, the displayed caller ID is spoofed to impersonate police or law enforcement
1926:
can be prevented using bogon filtering. Automatic rate filtering can work as long as set rate thresholds have been set correctly. WAN-link failover will work as long as both links have a DoS prevention mechanism.
802:. Attackers can also break into systems using automated tools that exploit flaws in programs that listen for connections from remote hosts. This scenario primarily concerns systems acting as servers on the web.
1765:
via various methods such as: changing the victim IP address in the DNS system, tunneling methods (GRE/VRF, MPLS, SDN), proxies, digital cross connects, or even direct circuits. The cleaning center separates
914:
impossible until all data has been sent. It is notable that unlike many other DDoS or DDoS attacks, which try to subdue the server by overloading its network or CPU, an HTTP slow POST attack targets the
709:
a wide variety of DDoS tools are available today, including paid and free versions, with different features available. There is an underground market for these in hacker-related forums and IRC channels.
4726:
756:
is another particular type of DoS. It involves redirecting outgoing messages from the client back onto the client, preventing outside access, as well as flooding the client with the sent packets. A
2123:, was sentenced to 27 months in prison and $ 95,000 restitution by a federal court for conducting multiple DDoS attacks on major video gaming companies, disrupting their systems from hours to days.
1711:
of thousands of devices, the attackers can generate sufficient packet rates and occupy bandwidth to saturate links, causing the denial of services. Because of this weakness, the network company
2611:
858:(IoT) devices that have been involved in denial of service attacks. In one noted attack that was made peaked at around 20,000 requests per second which came from around 900 CCTV cameras. UK's
1489:
lower in cost due to its use of less traffic, is smaller in size making it more difficult to identify, and it has the ability to hurt systems which are protected by flow control mechanisms.
3163:
2221:
865:
Simple attacks such as SYN floods may appear with a wide range of source IP addresses, giving the appearance of a distributed DoS. These flood attacks do not require completion of the TCP
6317:
1613:
892:. Security experts recommend targeted websites to not pay the ransom. The attackers tend to get into an extended extortion scheme once they recognize that the target is ready to pay.
5700:
Kousiouris, George (2014). "KEY COMPLETION INDICATORS:minimizing the effect of DoS attacks on elastic Cloud-based applications based on application-level markov chain checkpoints".
1771:
overwhelm any type of hardware firewall, and passing malicious traffic through large and mature networks becomes more and more effective and economically sustainable against DDoS.
1501:
occurs when a host sends a flood of TCP/SYN packets, often with a forged sender address. Each of these packets is handled like a connection request, causing the server to spawn a
399:. In August 2024 Global Secure Layer observed and reported on a record-breaking packet DDoS at 3.15 billion packets per second, which targeted an undisclosed number of unofficial
6343:
846:(a resource starvation attack) may also be used. Newer tools can use DNS servers for DoS purposes. Unlike MyDoom's DDoS mechanism, botnets can be turned against any IP address.
5609:
5569:
2045:
In computer network security, backscatter is a side-effect of a spoofed denial-of-service attack. In this kind of attack, the attacker spoofs (or forges) the source address in
432:. A distributed denial of service attack typically involves more than around 3–5 nodes on different networks; fewer nodes may qualify as a DoS attack but is not a DDoS attack.
428:
or resources of a targeted system, usually one or more web servers. A DDoS attack uses more than one unique IP address or machines, often from thousands of hosts infected with
2552:
2053:
If the attacker is spoofing source addresses randomly, the backscatter response packets from the victim will be sent back to random destinations. This effect can be used by
3541:
2885:
1779:
Application front-end hardware is intelligent hardware placed on the network before traffic reaches the servers. It can be used on networks in conjunction with routers and
1130:, the source address is set to that of the targeted victim, which means all the replies will go to (and flood) the target. This reflected attack form is sometimes called a
6077:
748:, an attack running on mobile devices. Another target of DDoS attacks may be to produce added costs for the application operator, when the latter uses resources based on
613:
by a botnet, the traffic produced by a consumer stresser can range anywhere from 5-50 Gbit/s, which can, in most cases, deny the average home user internet access.
3629:
350:
This wave of cyber aggression extended to Western allies like the UK, the US, and Germany. Particularly, the UK's financial sector saw an increase in DDoS attacks from
3481:
3237:
3075:
2112:
6247:
625:. A setting in which Markov-model based attacks are prevalent is online gaming as the disruption of the control packet undermines game play and system functionality.
5494:
3783:
2951:
634:
1126:
A distributed denial-of-service attack may involve sending forged requests of some type to a very large number of computers that will reply to the requests. Using
6440:
4514:
3233:
3071:
1657:
value of 1 or less than it does to forward a packet with a higher TTL value. When a packet is dropped due to TTL expiry, the router CPU must generate and send an
526:
5734:
2570:
5198:
1363:
Since the size of the request is significantly smaller than the response, the attacker is easily able to increase the amount of traffic directed at the target.
5784:
1471:. It exploits a weakness in TCP's re-transmission timeout mechanism, using short synchronized bursts of traffic to disrupt TCP connections on the same link.
6167:
5391:
4084:
2691:
918:
resources of the victim, which means the victim would still have enough network bandwidth and processing power to operate. Combined with the fact that the
6272:
879:, TCP ACK, and TCP floods. With TCP being the most widespread networking protocol, its attacks are expected to remain prevalent in the DDoS threat scene.
314:, revealed by Google on October 17, 2020. The record holder was thought to be an attack executed by an unnamed customer of the US-based service provider
1994:
during peak periods of activity, or does not have a lot of available bandwidth while being indexed, it can also experience the effects of a DoS attack.
4868:
Kuzmanovic, Aleksandar; Knightly, Edward W. (25 August 2003). "Low-rate TCP-targeted denial of service attacks: The shrew vs. The mice and elephants".
3266:
345:
said it blocked a HTTP pipelining DDoS attack on Sept. 5. 2021 that originated from unpatched Mikrotik networking gear. In the first half of 2022, the
6984:
6182:
4191:
1114:, a piece of malware that targeted IoT devices, used PDoS attacks to disable its targets. PhlashDance is a tool created by Rich Smith (an employee of
60:
5623:
4769:
2619:
6354:
1026:, thus slowing down the affected computer until it comes to a complete stop. A specific example of a nuke attack that gained some prominence is the
517:(ISO/IEC 7498-1) is a conceptual model that characterizes and standardizes the internal functions of a communication system by partitioning it into
1068:. With peer-to-peer there is no botnet and the attacker does not have to communicate with the clients it subverts. Instead, the attacker acts as a
3155:
1832:
3813:
3606:
2900:
2665:
5583:
5543:
1998:
6324:
2815:
850:
use them to deny the availability of well known websites to legitimate users. More sophisticated attackers use DDoS tools for the purposes of
6961:
5717:
5676:
5271:
5023:
3928:
3903:
3878:
3687:"Security challenges in internet of things: Distributed denial of service attack detection using support vector machine-based expert systems"
3357:
2414:
systems is much less capable of overwhelming a target, also the -l (size) flag does not allow sent packet size greater than 65500 in Windows.
367:
5176:
1852:
has a purpose-built system that can easily identify and obstruct denial of service attacks at a greater speed than a software-based system.
5874:
4971:
4966:
4107:
2790:
1118:
Systems Security Lab) used to detect and demonstrate PDoS vulnerabilities at the 2008 EUSecWest Applied Security Conference in London, UK.
5931:
4933:
4036:
1816:(null interface or a non-existent server). To be more efficient and avoid affecting network connectivity, it can be managed by the ISP. A
1787:. Application front-end hardware analyzes data packets as they enter the network, and identifies and drops dangerous or suspicious flows.
1703:. Many devices, including some residential routers, have a vulnerability in the UPnP software that allows an attacker to get replies from
4577:
1820:
routes traffic to a valid IP address which analyzes traffic and rejects bad packets. Sinkholing may not be efficient for severe attacks.
6992:
2116:
6347:
107:
7018:
6433:
6141:
4895:
3589:
3047:
2292:
2158:
4784:
3503:
79:
6924:
4744:
3431:
3209:
3182:
3138:
3013:
1694:
1686:
1298:
1015:
794:
before releasing the malware and no further interaction was necessary to launch the attack. A system may also be compromised with a
126:
3838:
Cambiaso, Enrico; Papaleo, Gianluca; Chiola, Giovanni; Aiello, Maurizio (2015). "Designing and modeling the slow next DoS attack".
2556:
4275:
4165:
6720:
4833:
Kolias, Constantinos; Kambourakis, Georgios; Stavrou, Angelos; Voas, Jeffrey (2017). "DDoS in the IoT: Mirai and Other Botnets".
4532:
3549:
1704:
1110:
security exploits on network-enabled embedded devices, this technique has come to the attention of numerous hacking communities.
972:
computer will be flooded with traffic. This overloads the victim's computer and can even make it unusable during such an attack.
5816:
3489:
2742:
86:
6974:
6211:
5957:
4253:
4222:
4140:
2209:
2134:
is unusual in that it specifically outlawed denial-of-service attacks and set a maximum penalty of 10 years in prison with the
1734:, causing traffic intended for the original authentic IP to be re-routed to that of the attacker, causing a denial of service.
1582:
1530:
with overlapping, oversized payloads to the target machine. This can crash various operating systems because of a bug in their
744:
implement an application-layer attack. Examples of threats are Slowloris, establishing pending connections with the victim, or
6142:"United States Code: Title 18,1030. Fraud and related activity in connection with computers | Government Printing Office"
2842:
939:
A Challenge Collapsar (CC) attack is an attack where standard HTTP requests are sent to a targeted web server frequently. The
501:
from security breaches. In 2013, application-layer DDoS attacks represented 20% of all DDoS attacks. According to research by
7028:
5068:
Ben-Porat, U.; Bremler-Barr, A.; Levy, H. (1 May 2013). "Vulnerability of Network Mechanisms to Sophisticated DDoS Attacks".
4407:
999:
182:
64:
4558:
3945:
3637:
963:
relies on misconfigured network devices that allow packets to be sent to all computer hosts on a particular network via the
589:
persistence over extended periods (combining all the above into a concerted, well-managed attack across a range of targets).
6297:
6787:
6426:
5518:
4870:
Proceedings of the 2003 conference on Applications, technologies, architectures, and protocols for computer communications
2345:
1464:
1039:
670:
93:
286:, figured out a proper defense. Another early demonstration of the DoS attack was made by Khan C. Smith in 1997 during a
278:
in the world, was the target of what is thought to be the first DoS attack. On September 6, 1996, Panix was subject to a
5979:
3447:
2977:
2108:
2078:
2006:
1731:
522:
4703:
3787:
3685:
Mubarakali, Azath; Srinivasan, Karthik; Mukhalid, Reham; Jaganathan, Subash C. B.; Marina, Ninoslav (26 January 2020).
6979:
6900:
6700:
5746:
5206:
2574:
2135:
1828:
998:
is based on sending the victim a malformed ping packet, which will lead to a system crash on a vulnerable system. The
940:
719:
346:
4438:
3660:
306:
and other major corporations in the year to follow. The largest DDoS attack to date happened in September 2017, when
75:
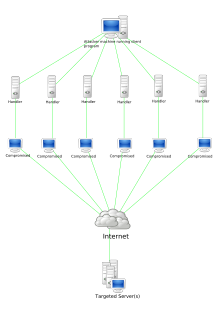
1726:
is a common DoS attack that involves a vulnerability in the ARP protocol that allows an attacker to associate their
6956:
6914:
6570:
5366:
2334:
2263:
2103:
laws to combat its widespread impact. Adoption rates vary by region, with Europe at a 91% rate, and Africa at 72%.
2046:
1373:
can also be exploited as reflectors in an amplification attack. An example of an amplified DDoS attack through the
559:
387:
5794:
4725:
van Rijswijk-Deij, Roland (2014). "DNSSEC and its potential for DDoS attacks: A comprehensive measurement study".
2372:
7033:
6817:
6535:
6163:
2040:
1428:
1055:
1019:
979:
275:
6024:
4348:
3089:
2925:
854: – including against their business rivals. It has been reported that there are new attacks from
790:. Its DoS mechanism was triggered on a specific date and time. This type of DDoS involved hardcoding the target
6802:
6575:
5841:
2139:
1946:
1562:
vulnerable to teardrop attacks is unable to reassemble the packets resulting in a denial-of-service condition.
1468:
931:
web application security project, released a tool to test the security of servers against this type of attack.
795:
571:
457:
4770:"P2P File-Sharing in Hell: Exploiting BitTorrent Vulnerabilities to Launch Distributed Reflective DoS Attacks"
4061:
1002:
attack is an example of an attack taking advantage of the required Destination Port Unreachable ICMP packets.
6047:
5341:
3251:
2886:"Settimo giorno di attacchi informatici all'Italia. NoName057(16) torna alle Banche e alle Telecomunicazioni"
2527:
2456:
6890:
6842:
6505:
2203:
1670:
1514:
53:
6298:"Anonymous DDoS Petition: Group Calls On White House To Recognize Distributed Denial Of Service As Protest"
5634:
4518:
4183:
2867:
4873:
1915:
730:. Another kind of application-level DoS attack is XDoS (or XML DoS) which can be controlled by modern web
1101:
with a modified, corrupt, or defective firmware image—a process which when done legitimately is known as
7023:
6931:
6665:
2239:
2185:
1836:
1577:
voice calls inexpensive and easily automated while permitting call origins to be misrepresented through
1374:
1370:
1201:
991:
706:
425:
307:
3448:"Gartner Says 25 Percent of Distributed Denial of Services Attacks in 2013 Will Be Application - Based"
2589:
5392:"New DDoS Attack Method Demands a Fresh Approach to Amplification Assault Mitigation – Blog | Imperva"
4353:
Distributed Denial of Service Attacks(DDoS) Resources, Pervasive Technology Labs at Indiana University
3817:
621:
A Markov-modulated denial-of-service attack occurs when the attacker disrupts control packets using a
100:
6951:
6863:
6812:
6757:
6625:
6598:
6580:
6545:
6478:
6449:
6098:
5502:
4381:
2432:
2301:
2281:
2251:
1861:
1784:
1630:
1502:
1424:
1043:
731:
702:
31:
4878:
4610:
4465:
1677:
researchers, the most effective way to stop this attack is for companies to lock down UPnP routers.
693:
In other cases a machine may become part of a DDoS attack with the owner's consent, for example, in
6735:
6510:
6468:
4646:
2287:
2036:
2019:
1895:
1878:
1395:
1127:
1106:
1090:
1076:
hubs to disconnect from their peer-to-peer network and to connect to the victim's website instead.
1011:
866:
642:
622:
586:
simultaneous multi-threaded OSI layer attacks (sophisticated tools operating at layers 3 through 7)
502:
441:
326:
3972:
1064:
servers to initiate DDoS attacks. The most aggressive of these peer-to-peer-DDoS attacks exploits
17:
6919:
6847:
6752:
5861:
5682:
5228:
5093:
5029:
4998:
Yu Chen; Kai Hwang; Yu-Kwong Kwok (2005). "Filtering of shrew DDoS attacks in frequency domain".
4901:
4850:
4750:
4330:
4318:
4017:
3753:
3714:
3404:
3363:
3335:
3227:
3065:
2497:
2389:
2310:
2215:
1658:
1638:
1609:
1578:
1359:
1086:
919:
855:
807:
682:
533:
below it. In an implementation, the application and presentation layers are frequently combined.
530:
445:
383:
359:
295:
165:
in which the perpetrator seeks to make a machine or network resource unavailable to its intended
5881:
5769:
5229:"Microsoft Security Advisory (975497): Vulnerabilities in SMB Could Allow Remote Code Execution"
4976:
2130:
countries, committing criminal denial-of-service attacks may, as a minimum, lead to arrest. The
722:
and can cause server-running software to fill the disk space or consume all available memory or
542:
packets. A common way of achieving this today is via distributed denial-of-service, employing a
4944:
2061:
refers to observing backscatter packets arriving at a statistically significant portion of the
577:
tactical execution (attack with both primary and secondary victims but the focus is on primary)
6967:
6725:
6660:
6610:
6557:
6515:
6463:
5713:
5672:
5603:
5563:
5293:
5267:
5085:
5019:
4891:
4740:
4584:
4322:
3924:
3899:
3874:
3706:
3585:
3427:
3353:
3292:
3215:
3205:
3134:
3053:
3043:
3007:"A Survey of Defense Mechanisms Against Distributed Denial of Service (DDoS) Flooding Attacks"
2411:
2155:
2054:
1809:
1139:
968:
964:
928:
816:
812:
698:
694:
518:
497:
437:
5898:
6936:
6876:
6640:
6630:
6525:
6367:
5705:
5664:
5510:
5259:
5149:
5139:
5077:
5051:
5011:
5003:
4883:
4842:
4732:
4314:
3998:
3745:
3698:
3394:
3345:
3308:
2612:"Distributed Denial of Service Attacks - The Internet Protocol Journal - Volume 7, Number 4"
2479:
2245:
1440:
1432:
449:
400:
178:
166:
6116:
3946:"SANS Institute – Intrusion Detection FAQ: Distributed Denial of Service Attack Tools: n/a"
2077:
Numerous websites offering tools to conduct a DDoS attack were seized by the FBI under the
1553:
prior to versions 2.0.32 and 2.1.63 are vulnerable to this attack. One of the fields in an
806:
is a classic example of a DDoS tool. It uses a layered structure where the attacker uses a
681:
is a classic example of a DDoS tool. It uses a layered structure where the attacker uses a
6827:
6807:
6530:
6520:
6406:
5047:
4791:
2316:
2284: – Open source network stress testing and denial-of-service attack application (LOIC)
2166:
1959:
1919:
1907:
1903:
1840:
1743:
1334:
1115:
1023:
799:
749:
741:
686:
563:
379:
363:
294:
for over an hour. The release of sample code during the event led to the online attack of
291:
213:
170:
141:
4675:
3734:"Risk-Sensitive Control Under Markov Modulated Denial-of-Service (DoS) Attack Strategies"
3686:
3178:
3006:
2642:
1585:, telephony denial-of-service (TDoS) has appeared as part of various fraudulent schemes:
819:. These attacks can use different types of internet packets such as TCP, UDP, ICMP, etc.
382:. On 14 January 2024, they executed a DDoS attack on Swiss federal websites, prompted by
282:
attack, which brought down its services for several days while hardware vendors, notably
6318:"Distributed Denial of Service Attacks Against Independent Media and Human Rights Sites"
6316:
Ethan Zuckerman; Hal Roberts; Ryan McGrady; Jillian York; John Palfrey (December 2011).
6229:
3332:
Proceedings of the 11th International Conference on Cloud Computing and Services Science
2200: – Collection of compromised internet-connected devices controlled by a third party
1406:, etc. As soon as this occurred, these websites were all unreachable for several hours.
967:
of the network, rather than a specific machine. The attacker will send large numbers of
6997:
6895:
6745:
6695:
6670:
6635:
6615:
6495:
6483:
6388:
4647:"CVE-2022-26143: A Zero-Day vulnerability for launching UDP amplification DDoS attacks"
4283:
4169:
2523:
2354:
2322:
2162:
2131:
2073:
1951:
1923:
1780:
1626:
1524:
839:
315:
186:
with a substantial amount of invalid data, to submitting requests with an illegitimate
174:
4488:
3840:
Computational Intelligence in Security for Information Systems Conference (CISIS 2015)
3522:
2022:
in 2016. This could be caused when a server provides some service at a specific time.
240:
145:
Diagram of a DDoS attack. Note how multiple computers are attacking a single computer.
7012:
6907:
6868:
6837:
6832:
6685:
6675:
6645:
6323:. The Berkman Center for Internet & Society at Harvard University. Archived from
5789:
5345:
4905:
4334:
4129:
3718:
3408:
3367:
3131:
An Investigation into the Detection and Mitigation of Denial of Service (DoS) Attacks
2978:"Unprecedented 3.15 Billion Packet Rate DDoS Attack Mitigated by Global Secure Layer"
2760:
2424:
2366:
2257:
2014:
1991:
1899:
1874:
1617:
1570:
1390:
1094:
995:
847:
583:
large computing capacity (access to substantial computer power and network bandwidth)
424:
A distributed denial-of-service (DDoS) attack occurs when multiple systems flood the
375:
5686:
5251:
5097:
4854:
4245:
4214:
1625:-867-5309 subscribers inundated by hundreds of calls daily in response to the song "
990:
hosts. It is very simple to launch, the primary requirement being access to greater
6941:
6797:
6500:
6186:
5263:
5112:
4754:
3757:
3197:
2120:
2090:
2010:
1911:
1817:
1723:
1654:
1538:
1436:
1386:
1250:
1143:
1073:
1061:
960:
835:
827:
803:
678:
473:
453:
351:
338:
162:
6005:
5033:
4415:
4085:"Cyber-Extortionists Targeting the Financial Sector Are Demanding Bitcoin Ransoms"
2478:
Elleithy, Khaled; Blagovic, Drazen; Cheng, Wang; Sideleau, Paul (1 January 2005).
2119:
handles cases of DoS and DDoS. In one example, in July 2019, Austin Thompson, aka
1452:
1448:
1444:
341:
that was up to 17.2 million requests per second. Russian DDoS prevention provider
6355:
PC World - Application Layer DDoS Attacks are Becoming Increasingly Sophisticated
6273:"Authorities across the world going after users of biggest DDoS-for-hire website"
5659:
Alqahtani, S.; Gamble, R. F. (1 January 2015). "DDoS Attacks in Service Clouds".
4919:
4562:
3949:
3296:
2952:"Google mitigated the largest DDoS attack to date, peaking above 398 million rps"
2666:"Google says it mitigated a 2.54 Tbps DDoS attack in 2017, largest known to date"
2107:
In the US, denial-of-service attacks may be considered a federal crime under the
900:
First discovered in 2009, the HTTP slow POST attack sends a complete, legitimate
6881:
6715:
6690:
6655:
6490:
6371:
6069:
5435:
4037:"HACKING ONLINE POLLS AND OTHER WAYS BRITISH SPIES SEEK TO CONTROL THE INTERNET"
3381:
Xu, Xiaoqiong; Li, Jin; Yu, Hongfang; Luo, Long; Wei, Xuetao; Sun, Gang (2020).
2816:"Cloudflare mitigates record-breaking 71 million request-per-second DDoS attack"
2269:
2095:
Many jurisdictions have laws under which denial-of-service attacks are illegal.
1727:
1594:
1527:
1310:
901:
871:
831:
685:
to connect to handlers which are compromised systems that issue commands to the
477:
271:
210:
42:
4808:
4624:
3733:
3399:
3382:
3179:"World's largest 1 Tbps DDoS Attack launched from 152,000 hacked Smart Devices"
2716:
1835:
based IPS may detect and block denial-of-service attacks because they have the
786:
can carry DDoS attack mechanisms; one of the better-known examples of this was
6946:
6762:
6710:
6593:
6473:
4651:
2480:"Denial of Service Attack Techniques: Analysis, Implementation and Comparison"
2165:
site asking that DDoS be recognized as a legal form of protest similar to the
2100:
2086:
2062:
1712:
1634:
1546:
1542:
1263:
1111:
1035:
975:
791:
334:
225:
202:
187:
6412:
6383:
5983:
5709:
5315:
5089:
4326:
4306:
3749:
3710:
3455:
3349:
3219:
3202:
DDoS attacks : evolution, detection, prevention, reaction, and tolerance
3057:
2194: – Prank fax transmission designed to waste the recipient's ink or paper
6822:
6777:
6772:
6620:
6588:
5514:
5467:
5449:
4736:
4355:. Advanced Networking Management Lab (ANML). 3 December 2009. Archived from
3779:
3504:"Q4 2014 State of the Internet - Security Report: Numbers - The Akamai Blog"
3312:
2360:
2339:
2275:
2233:
2227:
2191:
2188: – Denial-of-service attack at XML parsers, exploiting entity expansion
1883:
1661:
response. Generating many of these responses can overload the router's CPU.
1642:
1622:
1574:
1554:
1498:
1480:
clients' TCP receive buffer slowly, which causes a very low data flow rate.
1188:
987:
851:
843:
745:
727:
637:(US-CERT) has identified symptoms of a denial-of-service attack to include:
574:
and extensive decoyed scanning crafted to evade detection over long periods)
514:
299:
279:
221:
150:
5668:
4611:"An Analysis of Using Reflectors for Distributed Denial-of-Service Attacks"
6400:
4887:
4442:
1977:
Routers have also been known to create unintentional DoS attacks, as both
1593:
A scammer contacts consumers with a bogus claim to collect an outstanding
378:
targeted several Italian financial institutions, through the execution of
6782:
6740:
6603:
5913:
5000:
The IEEE Conference on Local Computer Networks 30th Anniversary (LCN'05)l
2377:
2179:
1963:
1601:
1098:
723:
599:
5007:
4846:
6792:
6767:
6730:
6418:
5081:
5015:
3780:"Cyber Security Tip ST04-015 - Understanding Denial-of-Service Attacks"
3702:
3262:
3040:
Theoretical and experimental methods for defending against DDoS attacks
2146:
2002:
1982:
1674:
1645:
or continuous fax transmission by using a loop of paper at the sender.
1431:(SACK) may be used by a remote peer to cause a denial of service by an
1403:
1399:
1346:
1214:
1031:
1027:
889:
876:
783:
674:
429:
371:
303:
287:
217:
6183:"Get rekt: Two years in clink for game-busting DDoS brat DerpTrolling"
5417:
5154:
3156:"Record-breaking DDoS reportedly delivered by >145k hacked cameras"
2169:, the claim being that the similarity in the purpose of both is same.
1042:
port 139 of the victim's machine, causing it to lock up and display a
6705:
6650:
6565:
6394:
5590:. NANOG23. 23 October 2001. Archived from the original on 15 May 2021
5316:"Internet Crime Complaint Center's (IC3) Scam Alerts January 7, 2013"
5144:
5131:
4938:
4728:
Proceedings of the 2014 Conference on Internet Measurement Conference
4680:
4356:
4215:"CC (challenge collapsar) attack defending method, device and system"
2254: – Use of espionage for commercial purposes rather than security
2197:
2127:
2096:
1987:
1978:
1967:
1708:
1531:
1322:
1065:
1056:
Direct Connect (protocol) § Direct Connect used for DDoS attacks
823:
787:
666:
543:
396:
391:
342:
5550:. NANOG28. 3 January 2003. Archived from the original on 15 May 2021
3852:
862:
has tools built for DDoS, named PREDATORS FACE and ROLLING THUNDER.
677:
and launch their attacks without the knowledge of the system owner.
3607:"38-Day Long DDoS Siege Amounts to Over 50 Petabits in Bad Traffic"
3340:
3012:. IEEE Communications Surveys & Tutorials. pp. 2046–2069.
2692:"US service provider survives the biggest recorded DDoS in history"
2065:
space to determine the characteristics of DoS attacks and victims.
2743:"Cloudflare Mitigated Record-Setting 17.2 Million RPS DDoS Attack"
2392: – Compromised computer used for malicious tasks on a network
2383:
2328:
2072:
1550:
1175:
924:
337:
boasted of protecting its client from a DDoS attack from a global
283:
140:
4578:"Amplification Hell: Revisiting Network Protocols for DDoS Abuse"
4062:"Who's Behind DDoS Attacks and How Can You Protect Your Website?"
3732:
Befekadu, Getachew K.; Gupta, Vijay; Antsaklis, Panos J. (2015).
3383:"Towards Yo-Yo attack mitigation in cloud auto-scaling mechanism"
3326:
Barr, Anat; Ben David, Ronen (2021). "Kubernetes Autoscaling: Yo
2484:
School of Computer Science & Engineering Faculty Publications
2435:
which is a higher layer than the TCP packets that teardrop used).
1812:, all the traffic to the attacked DNS or IP address is sent to a
1757:
All traffic destined to the victim is diverted to pass through a
370:(OTW) and reliant on donations, is unlikely to meet the $ 30,000
6025:"People Overload Website, Hoping To Help Search For Missing Jet"
4282:(in Simplified Chinese). 驱动中国网(北京). 24 July 2014. Archived from
2901:"Switzerland hit by cyberattack after Ukraine president's visit"
1997:
Legal action has been taken in at least one such case. In 2006,
1971:
1690:
1534:
1484:
Sophisticated low-bandwidth Distributed Denial-of-Service Attack
1366:
1276:
1238:
859:
757:
206:
6422:
5294:"FBI — Phony Phone Calls Distract Consumers from Genuine Theft"
3424:
Counterterrorism and Cybersecurity: Total Information Awareness
2926:"HTTP/2 Rapid Reset: deconstructing the record-breaking attack"
354:
actors and hacktivists, aimed at undermining Ukraine's allies.
6377:
5468:"Stupidly Simple DDoS Protocol (SSDP) generates 100 Gbps DDoS"
5450:"Stupidly Simple DDoS Protocol (SSDP) generates 100 Gbps DDoS"
4246:"CC (Challenge Collapsar) attack protection method and device"
4108:"Akamai warns of increased activity from DDoS extortion group"
3814:"The "stacheldraht" distributed denial of service attack tool"
2325: – Anti-distributed-denial-of-service (anti-DDoS) service
2319: – Use of bogus legal documents as a method of harassment
1886:
has optional features that can reduce the impact of flooding.
1226:
235:
36:
4307:"Danger Theory Based Risk Evaluation Model for Smurf Attacks"
3873:. Atlantic Publishers & Distributors. 2007. p. 397.
2099:
highlights that 156 countries, or 80% globally, have enacted
6544:
6415:
An Attempt to Bring SlowLoris and Slow Network Tools on LOIC
5733:
Patrikakis, C.; Masikos, M.; Zouraraki, O. (December 2004).
5661:
2015 48th Hawaii International Conference on System Sciences
5256:
New Age Cyber Threat Mitigation for Cloud Computing Networks
2843:"AO3 fanfiction site forced offline by wave of DDoS attacks"
2553:"Brand.com President Mike Zammuto Reveals Blackmail Attempt"
2369: – Interference with authorized wireless communications
1010:
A nuke is an old-fashioned denial-of-service attack against
3000:
2998:
1898:
capability. Some switches provide automatic or system-wide
1715:
has described SSDP as the "Stupidly Simple DDoS Protocol".
5624:"DDoS Mitigation via Regional Cleaning Centers (Jan 2004)"
4704:"DRDoS / Amplification Attack using ntpdc monlist command"
4016:
Zeifman, Igal; Gayer, Ofer; Wilder, Or (21 October 2015).
2272: – Software means of causing computer hardware damage
1839:
and the granularity to analyze the attacks and act like a
1060:
Attackers have found a way to exploit a number of bugs in
947:
for short. Consequently, this type of attack got the name
5584:"Diversion and Sieving Techniques to Defeat DDoS attacks"
2571:"Brand.com's Mike Zammuto Discusses Meetup.com Extortion"
2348: – Software for executing a denial-of-service attack
2230: – Denial-of-service attack directed at a DNS server
2222:
Distributed denial-of-service attacks on root nameservers
1018:
packets sent to the target, achieved by using a modified
978:
is based on sending the victim an overwhelming number of
6212:"International Action Against DD4BC Cybercriminal Group"
5495:"Protection Against Denial of Service Attacks: A Survey"
2363: – Interface enabling remote access to a web server
2212: – Denial of service attack against a Wi-Fi network
1614:
2002 New Hampshire Senate election phone jamming scandal
1085:
management interfaces of the victim's hardware, such as
5177:"CERT Advisory CA-1997-28 IP Denial-of-Service Attacks"
4515:"Permanent Denial-of-Service Attack Sabotages Hardware"
3542:"DDoS Attack Used 'Headless' Browser In 150-Hour Siege"
3297:"Yo-Yo Attack: Vulnerability In Auto-scaling Mechanism"
3038:
Khalifeh, Soltanian, Mohammad Reza (10 November 2015).
2350:
Pages displaying short descriptions of redirect targets
2306:
Pages displaying short descriptions of redirect targets
2297:
Pages displaying short descriptions of redirect targets
2111:
with penalties that include years of imprisonment. The
1653:
It takes more router resources to drop a packet with a
580:
explicit motivation (a calculated end game/goal target)
252:
5063:
5061:
2380: – Linux trojan malware with rootkit capabilities
1463:
The shrew attack is a denial-of-service attack on the
822:
These collections of compromised systems are known as
5418:"Multi-State Information Sharing and Analysis Center"
4559:"EUSecWest Applied Security Conference: London, U.K."
4408:"Prolexic Distributed Denial of Service Attack Alert"
436:
may be impossible to stop the attack simply by using
5958:"Story of a Reddit Hug of Death and Lessons Learned"
3252:"Imperva, Global DDoS Threat Landscape, 2019 Report"
2304: – 2016 cyberattack in Europe and North America
6856:
6556:
6456:
4934:"SACK Panic and Other TCP Denial of Service Issues"
4625:"Alert (TA14-017A) UDP-based Amplification Attacks"
3482:"What you should know about worsening DDoS attacks"
3475:
3473:
2331: – Regular expression denial-of-service attack
1999:
Universal Tube & Rollform Equipment Corporation
67:. Unsourced material may be challenged and removed.
6380:- Quarterly Security and Internet trend statistics
6078:Cooperative Association for Internet Data Analysis
496:) is a form of DDoS attack where attackers target
6234:legislation.gov.uk — The National Archives, of UK
5817:"Cyber security vulnerability concerns skyrocket"
5342:"TTL Expiry Attack Identification and Mitigation"
5252:"Solutions for DDoS Attacks on Cloud Environment"
5132:"TCP SYN Flooding Attacks and Common Mitigations"
3661:"Stress-Testing the Booter Services, Financially"
2868:"Archive of Our Own is down due to a DDoS attack"
2791:"2022 in review: DDoS attack trends and insights"
2789:Team, Azure Network Security (21 February 2023).
2717:"Amazon 'thwarts largest ever DDoS cyber-attack'"
2643:"5 Famous Botnets that held the internet hostage"
2236: – Type of denial-of-service software attack
1707:to a destination address of their choice. With a
1573:has made abusive origination of large numbers of
830:still use classic DoS attack methods centered on
734:(WAFs). All attacks belonging to the category of
374:ransom. In August 2023, the group of hacktivists
181:. Denial of service is typically accomplished by
6391:CERT's Guide to DoS attacks. (historic document)
5936:Google Product Forums › Google Search Forum
5875:"Some IoS tips for Internet Service (Providers)"
5608:: CS1 maint: bot: original URL status unknown (
5568:: CS1 maint: bot: original URL status unknown (
5544:"MPLS-Based Synchronous Traffic Shunt (NANOG28)"
4439:"Peer-to-peer networks co-opted for DOS attacks"
3109:
3107:
2528:"Empty DDoS Threats: Meet the Armada Collective"
2386: – Denial-of-service bot discovered in 2012
2113:Computer Crime and Intellectual Property Section
1669:A UPnP attack uses an existing vulnerability in
705:has typically been used in this way. Along with
6164:"Utah Man Sentenced for Computer Hacking Crime"
5199:"Windows 7, Vista exposed to 'teardrop attack'"
3784:United States Computer Emergency Readiness Team
3630:"Video games company hit by 38-day DDoS attack"
2423:Although in September 2009, a vulnerability in
2057:as indirect evidence of such attacks. The term
635:United States Computer Emergency Readiness Team
472:attack is a specific type of DoS/DDoS aimed at
362:(AO3) faced DDoS attacks, disrupting services.
5258:, BENTHAM SCIENCE PUBLISHERS, pp. 42–55,
2313: – Joint operation to close DDoS websites
2248: – Type of denial-of-service cyber attack
1014:consisting of fragmented or otherwise invalid
955:Internet Control Message Protocol (ICMP) flood
527:International Organization for Standardization
6434:
4809:"Alert (TA13-088A) DNS Amplification Attacks"
3999:"Hacking CCTV Cameras to Launch DDoS Attacks"
2761:"Yandex Pummeled by Potent Meris DDoS Botnet"
2342: – Experimental denial of service attack
2295: – Network protection device or software
2266: – Network protection device or software
718:Application-layer attacks employ DoS-causing
8:
6403:- The Well Known Network Stress Testing Tool
6378:Akamai State of the Internet Security Report
4489:"Phlashing attack thrashes embedded systems"
2242: – Denial-of-service attack tool (HOIC)
329:experienced an attack with a peak volume of
310:experienced an attack with a peak volume of
6117:"Cybercrime Legislation Worldwide | UNCTAD"
3807:
3805:
3236:) CS1 maint: multiple names: authors list (
3090:"Has Your Website Been Bitten By a Zombie?"
3074:) CS1 maint: multiple names: authors list (
2357: – Online civil disobedience technique
1791:Application level key completion indicators
1435:in the Linux kernel, potentially causing a
1038:. A string of out-of-band data was sent to
1030:, which exploited the vulnerability in the
448:. Some common examples of DDoS attacks are
6441:
6427:
6419:
6397:– Real-time global report of DDoS attacks.
6048:"Experts cast doubt on Census DDoS claims"
4319:10.4028/www.scientific.net/KEM.467-469.515
4130:"OWASP Plan - Strawman - Layer_7_DDOS.pdf"
3816:. University of Washington. Archived from
3540:Higgins, Kelly Jackson (17 October 2013).
3232:: CS1 maint: location missing publisher (
3070:: CS1 maint: location missing publisher (
3042:. Amiri, Iraj Sadegh, 1977-. Waltham, MA.
2899:swissinfo.ch, S. W. I. (17 January 2024).
1894:Most switches have some rate-limiting and
1549:operating systems, as well as versions of
842:(types of bandwidth consumption attacks).
811:with the owner's consent, for example, in
648:unavailability of a particular website, or
169:by temporarily or indefinitely disrupting
30:"DoS" redirects here. For other uses, see
6985:Security information and event management
6374:Internet Denial-of-Service Considerations
5153:
5143:
4877:
3398:
3339:
3301:ACM SIGCOMM Computer Communication Review
2457:"Understanding Denial-of-Service Attacks"
2278: – Punch card with all holes punched
1730:to the IP address of another computer or
617:Markov-modulated denial-of-service attack
290:event, disrupting Internet access to the
127:Learn how and when to remove this message
4828:
4826:
3973:"US credit card firm fights DDoS attack"
1157:
1132:distributed reflective denial-of-service
5735:"Distributed Denial of Service Attacks"
5548:Riverhead Networks, Cisco, Colt Telecom
5367:"New DDoS Attack Method Leverages UPnP"
4382:"What Is a Nuke? | Radware — DDoSPedia"
4376:
4374:
4018:"CCTV DDoS Botnet In Our Own Back Yard"
3871:Encyclopaedia Of Information Technology
3295:; Rosensweig, Elisha (17 August 2015).
3185:from the original on 30 September 2016.
3177:Khandelwal, Swati (26 September 2016).
3005:Taghavi Zargar, Saman (November 2013).
2498:"What is a DDoS Attack? - DDoS Meaning"
2448:
2403:
1873:Similar to switches, routers have some
6300:. HuffingtonPost.com. 12 January 2013.
6099:"FBI Seizes 15 DDoS-For-Hire Websites"
5601:
5561:
5493:Loukas, G.; Oke, G. (September 2010).
4513:Jackson Higgins, Kelly (19 May 2008).
3738:IEEE Transactions on Automatic Control
3330:Attack Vulnerability and Mitigation".
3225:
3063:
645:(opening files or accessing websites),
6962:Host-based intrusion detection system
5770:"How to prevent or stop DoS attacks?"
5633:. Sprint ATL Research. Archived from
4533:""BrickerBot" Results In PDoS Attack"
4137:Open Web Application Security Project
4106:Greenberg, Adam (14 September 2015).
3575:
3573:
3571:
3569:
3567:
2784:
2782:
368:Organization for Transformative Works
7:
5932:"We're Sorry. Automated Query error"
5899:"SSDP DDoS attack | Cloudflare"
5785:"How to defend against DDoS attacks"
5768:Popeskic, Valter (16 October 2012).
5250:Bhardwaj, Akashdeep (12 June 2023),
5111:orbitalsatelite (8 September 2016).
4783:Vaughn, Randal; Evron, Gadi (2006).
3997:Swati Khandelwal (23 October 2015).
3812:Dittrich, David (31 December 1999).
3790:from the original on 4 November 2013
3166:from the original on 2 October 2016.
570:advanced reconnaissance (pre-attack
195:distributed denial-of-service attack
65:adding citations to reliable sources
6993:Runtime application self-protection
6384:W3C The World Wide Web Security FAQ
4576:Rossow, Christian (February 2014).
4188:HUAWEI CLOUD-Grow With Intelligence
4146:from the original on 9 October 2022
3778:McDowell, Mindi (4 November 2009).
3387:Digital Communications and Networks
3272:from the original on 9 October 2022
1398:which is the ISP for sites such as
1080:Permanent denial-of-service attacks
6170:from the original on 10 July 2019.
6006:"YouTube sued by sound-alike site"
5205:. 8 September 2009. Archived from
5048:"What is a Slow Read DDoS Attack?"
4583:. Internet Society. Archived from
4083:Solon, Olivia (9 September 2015).
3971:Leyden, John (23 September 2004).
3480:Ginovsky, John (27 January 2014).
3454:. 21 February 2013. Archived from
2588:Halpin, Harry (17 December 2010).
2293:Network intrusion detection system
2206: – 2003 Windows computer worm
1860:In the case of a simple attack, a
1796:this path, through markers called
1128:Internet Protocol address spoofing
25:
18:Reflected denial-of-service attack
6925:Security-focused operating system
6046:Palmer, Daniel (19 August 2016).
5914:"Web slows after Jackson's death"
5842:"FP Network Processor Technology"
5436:"UDP-Based Amplification Attacks"
5231:. Microsoft.com. 8 September 2009
4468:. DC++: Just These Guys, Ya Know?
4256:from the original on 5 March 2019
4225:from the original on 5 March 2019
4194:from the original on 5 March 2019
3548:. InformationWeek. Archived from
3154:Goodin, Dan (28 September 2016).
3019:from the original on 7 March 2014
2841:Weatherbed, Jess (11 July 2023).
2182: – Malware for Linux systems
2138:, which amended Section 3 of the
1687:Simple Service Discovery Protocol
6721:Insecure direct object reference
4706:. support.ntp.org. 24 April 2010
4035:Glenn Greenwald (15 July 2014).
3948:. SANS Institute. Archived from
3605:Ilascu, Ionut (21 August 2014).
3521:Ali, Junade (23 November 2017).
1159:UDP-based amplification attacks
1022:utility to repeatedly send this
651:inability to access any website.
521:. The model is a product of the
239:
41:
6975:Information security management
6023:Bill Chappell (12 March 2014).
5912:Shiels, Maggie (26 June 2009).
4731:. ACM Press. pp. 449–460.
4676:"Memcached 1.5.6 Release Notes"
4561:EUSecWest. 2008. Archived from
4441:. SecurityFocus. Archived from
3921:Networking and Mobile Computing
3659:Krebs, Brian (15 August 2015).
2210:Clear channel assessment attack
1940:Unintentional denial-of-service
1685:In 2014 it was discovered that
1583:Federal Bureau of Investigation
1072:, instructing clients of large
935:Challenge Collapsar (CC) attack
604:Some vendors provide so-called
52:needs additional citations for
5982:. Social Keith. Archived from
5783:Froutan, Paul (24 June 2004).
5264:10.2174/9789815136111123010006
5070:IEEE Transactions on Computers
4943:. 17 June 2019. Archived from
4517:. Dark Reading. Archived from
4064:. Cloudbric. 10 September 2015
3919:Lu, Xicheng; Wei Zhao (2005).
3628:Gold, Steve (21 August 2014).
3196:Kumar, Bhattacharyya, Dhruba;
2573:. 5 March 2014. Archived from
2555:. 5 March 2014. Archived from
1775:Application front end hardware
764:Degradation-of-service attacks
594:Denial-of-service as a service
558:(APDoS) is associated with an
228:, can motivate these attacks.
1:
6070:"Backscatter Analysis (2001)"
5739:The Internet Protocol Journal
4466:"Denying distributed attacks"
2590:"The Philosophy of Anonymous"
2346:Slowloris (computer security)
2218: – Android based malware
1465:Transmission Control Protocol
1439:. Jonathan Looney discovered
782:classified as a DDoS attack.
490:application layer DDoS attack
333:. In July 2021, CDN Provider
6181:Smolaks, Max (4 July 2019).
5130:Eddy, Wesley (August 2007).
4487:Leyden, John (21 May 2008).
3114:"Layer Seven DDoS Attacks".
2690:Goodin, Dan (5 March 2018).
2373:XML denial-of-service attack
2224: – Type of cyber attack
2109:Computer Fraud and Abuse Act
2079:Computer Fraud and Abuse Act
2007:Malaysia Airlines Flight 370
1962:when receiving traffic from
1829:Intrusion prevention systems
1608:TDoS can exist even without
1469:man-in-the-middle techniques
941:Uniform Resource Identifiers
673:, the tools are embedded in
523:Open Systems Interconnection
6980:Information risk management
6901:Multi-factor authentication
6457:Related security categories
6344:"DDOS Public Media Reports"
4785:"DNS Amplification Attacks"
4464:Fredrik Ullner (May 2007).
3923:. Birkhäuser. p. 424.
3580:Kiyuna and Conyers (2015).
2136:Police and Justice Act 2006
1966:. It is also known as "the
1629:". TDoS differs from other
1566:Telephony denial-of-service
1467:where the attacker employs
1271:Fixed in libuTP since 2015
982:packets, usually using the
347:Russian invasion of Ukraine
318:, reaching a peak of about
7050:
6957:Intrusion detection system
6915:Computer security software
6571:Advanced persistent threat
6230:"Computer Misuse Act 1990"
6144:. gpo.gov. 25 October 2002
5745:(4): 13–35. Archived from
3691:Computational Intelligence
3400:10.1016/j.dcan.2019.07.002
3092:. Cloudbric. 3 August 2015
2459:. US-CERT. 6 February 2013
2335:Resource exhaustion attack
2264:Intrusion detection system
2084:
2034:
1804:Blackholing and sinkholing
1741:
1512:
1209:Fixed in version 4.2.7p26
1093:. The attacker uses these
1053:
597:
560:advanced persistent threat
492:(sometimes referred to as
388:Davos World Economic Forum
76:"Denial-of-service attack"
29:
7019:Denial-of-service attacks
6542:
6536:Digital rights management
6346:. Harvard. Archived from
5588:Cisco, Riverhead Networks
4768:Adamsky, Florian (2015).
4437:Robert Lemos (May 2007).
4412:Prolexic Technologies Inc
4311:Key Engineering Materials
3898:. ABC-CLIO. p. 325.
3894:Schwabach, Aaron (2006).
2260: – Programming idiom
2041:Internet background noise
1954:or spyware application".
1931:Blocking vulnerable ports
1798:key completion indicators
1689:(SSDP) was being used in
1535:fragmentation re-assembly
1429:selective acknowledgement
1074:peer-to-peer file sharing
896:HTTP slow POST DoS attack
815:, organized by the group
714:Application-layer attacks
562:and requires specialized
484:Application layer attacks
6681:Denial-of-service attack
6576:Arbitrary code execution
5862:Nokia Deepfield Defender
5710:10.5220/0004963006220628
3857:Amazon Web Services, Inc
3750:10.1109/TAC.2015.2416926
3523:"The New DDoS Landscape"
3350:10.5220/0010397900340044
2150:and other DDoS services.
2140:Computer Misuse Act 1990
760:attack is of this type.
155:denial-of-service attack
6891:Computer access control
6843:Rogue security software
6506:Electromagnetic warfare
6409:- A Simple HTTP Flooder
4872:. ACM. pp. 75–86.
4790:. ISOTF. Archived from
4737:10.1145/2663716.2663731
4349:"Types of DDoS Attacks"
3944:Boyle, Phillip (2000).
3582:Cyberwarfare Sourcebook
3313:10.1145/2829988.2790017
3129:Raghavan, S.V. (2011).
2795:Microsoft Security Blog
2592:. Radicalphilosophy.com
2204:Blaster (computer worm)
2026:Side effects of attacks
1970:hug of death" and "the
1671:Universal Plug and Play
1515:IP fragmentation attack
1196:Fixed in version 1.5.6
834:and amplification like
697:organized by the group
556:advanced persistent DoS
550:Advanced persistent DoS
476:applications which use
6937:Obfuscation (software)
6666:Browser Helper Objects
6550:
5669:10.1109/HICSS.2015.627
5663:. pp. 5331–5340.
5296:. FBI.gov. 11 May 2010
4811:. US-CERT. 8 July 2013
4627:. US-CERT. 8 July 2014
4305:Sun, Fei Xian (2011).
4276:"史上最臭名昭著的黑客工具 CC的前世今生"
4184:"What Is a CC Attack?"
4166:"OWASP HTTP Post Tool"
2082:
1916:deep packet inspection
1681:SSDP reflection attack
1581:. According to the US
1251:Quake Network Protocol
1097:to replace a device's
777:Distributed DoS attack
771:degradation-of-service
401:Minecraft game servers
146:
7029:Types of cyberattacks
6932:Data-centric security
6813:Remote access trojans
6548:
6407:High Orbit Ion Cannon
5887:on 10 September 2008.
5515:10.1093/comjnl/bxp078
4888:10.1145/863955.863966
4609:Paxson, Vern (2001).
4406:Paul Sop (May 2007).
2982:globalsecurelayer.com
2427:was referred to as a
2240:High Orbit Ion Cannon
2186:Billion laughs attack
2117:Department of Justice
2076:
1843:in an automated way.
1695:SSDP reflection attac
1375:Network Time Protocol
1167:Amplification factor
1089:, printers, or other
732:application firewalls
707:High Orbit Ion Cannon
386:'s attendance at the
144:
6864:Application security
6758:Privilege escalation
6626:Cross-site scripting
6479:Cybersex trafficking
6450:Information security
6401:Low Orbit Ion Cannon
6395:ATLAS Summary Report
6350:on 25 December 2010.
5980:"The Digg Effect v4"
5704:. pp. 622–628.
5640:on 21 September 2008
4797:on 14 December 2010.
4445:on 24 September 2015
4386:security.radware.com
4359:on 14 September 2010
4313:. 467–469: 515–521.
4172:on 21 December 2010.
3896:Internet and the Law
3842:. 249-259. Springer.
3422:Lee, Newton (2013).
2302:2016 Dyn cyberattack
2282:Low Orbit Ion Cannon
2252:Industrial espionage
2154:On January 7, 2013,
2059:backscatter analysis
1947:Michael Jackson died
1824:IPS based prevention
1785:bandwidth management
1693:attacks known as an
1631:telephone harassment
1503:half-open connection
1425:maximum segment size
1410:R-U-Dead-Yet? (RUDY)
1258:Fixed in version 71
1050:Peer-to-peer attacks
1044:Blue Screen of Death
703:Low Orbit Ion Cannon
61:improve this article
32:DOS (disambiguation)
27:Type of cyber-attack
6511:Information warfare
6469:Automotive security
6330:on 26 February 2011
5749:on 27 December 2015
5472:The Cloudflare Blog
5454:The Cloudflare Blog
5438:. 18 December 2019.
5008:10.1109/LCN.2005.70
4922:. 8 September 2016.
4847:10.1109/MC.2017.201
4565:on 1 February 2009.
4521:on 8 December 2008.
4244:曾宪力; 史伟; 关志来; 彭国柱.
3853:"Amazon CloudWatch"
3492:on 9 February 2014.
3486:ABA Banking Journal
3458:on 25 February 2013
3198:Kalita, Jugal Kumar
3181:. The Hacker News.
2930:The Cloudflare Blog
2820:The Cloudflare Blog
2767:. 10 September 2021
2288:Mixed threat attack
2037:Backscatter (email)
2020:Census in Australia
1639:obscene phone calls
1160:
1091:networking hardware
904:, which includes a
867:three-way handshake
643:network performance
623:hidden Markov model
503:Akamai Technologies
494:layer 7 DDoS attack
442:IP address spoofing
327:Amazon Web Services
274:, the third-oldest
6920:Antivirus software
6788:Social engineering
6753:Polymorphic engine
6706:Fraudulent dialers
6611:Hardware backdoors
6551:
6236:. 10 January 2008.
6218:. 12 January 2016.
6012:. 2 November 2006.
5986:on 22 October 2010
5821:ComputerWeekly.com
5209:on 6 November 2010
5082:10.1109/TC.2012.49
4684:. 27 February 2018
3703:10.1111/coin.12293
3640:on 1 February 2017
3552:on 22 January 2014
3334:. pp. 34–44.
3293:Bremler-Barr, Anat
3204:. Boca Raton, FL.
2822:. 13 February 2023
2664:Cimpanu, Catalin.
2390:Zombie (computing)
2311:Operation PowerOFF
2216:Dendroid (malware)
2083:
2055:network telescopes
1753:Upstream filtering
1738:Defense techniques
1701:with amplification
1659:ICMP time exceeded
1610:Internet telephony
1579:caller ID spoofing
1455:on June 17, 2019.
1158:
920:Apache HTTP Server
856:internet of things
826:. DDoS tools like
736:timeout exploiting
531:presentation layer
519:abstraction layers
446:terabit per second
384:President Zelensky
360:Archive of Our Own
325:In February 2020,
251:. You can help by
147:
7006:
7005:
6968:Anomaly detection
6873:Secure by default
6726:Keystroke loggers
6661:Drive-by download
6549:vectorial version
6516:Internet security
6464:Computer security
6105:. 6 January 2019.
5938:. 20 October 2009
5719:978-989-758-019-2
5702:CLOSER Conference
5678:978-1-4799-7367-5
5273:978-981-5136-11-1
5025:978-0-7695-2421-4
5002:. pp. 8 pp.
4139:. 18 March 2014.
3930:978-3-540-28102-3
3905:978-1-85109-731-9
3880:978-81-269-0752-6
3820:on 16 August 2000
3744:(12): 3299–3304.
3665:Krebs on Security
3359:978-989-758-510-4
3200:(27 April 2016).
3116:Infosec Institute
2958:. 10 October 2023
2956:Google Cloud Blog
2932:. 10 October 2023
2749:. 23 August 2021.
2622:on 26 August 2019
2559:on 11 March 2014.
2526:(25 April 2016).
2504:. 13 January 2021
2159:posted a petition
2145:In January 2019,
1847:DDS based defense
1810:blackhole routing
1649:TTL expiry attack
1523:involves sending
1389:works by using a
1357:
1356:
1140:ICMP echo request
1116:Hewlett-Packard's
1105:The intent is to
1012:computer networks
994:than the victim.
965:broadcast address
813:Operation Payback
695:Operation Payback
665:In cases such as
656:Attack techniques
509:Application layer
498:application-layer
458:DNS amplification
438:ingress filtering
269:
268:
137:
136:
129:
111:
16:(Redirected from
7041:
7034:Internet outages
6877:Secure by design
6808:Hardware Trojans
6641:History sniffing
6631:Cross-site leaks
6526:Network security
6443:
6436:
6429:
6420:
6351:
6339:
6337:
6335:
6329:
6322:
6302:
6301:
6294:
6288:
6287:
6285:
6283:
6269:
6263:
6262:
6260:
6258:
6244:
6238:
6237:
6226:
6220:
6219:
6208:
6202:
6201:
6195:
6193:
6178:
6172:
6171:
6160:
6154:
6153:
6151:
6149:
6138:
6132:
6131:
6129:
6127:
6113:
6107:
6106:
6095:
6089:
6088:
6086:
6084:
6066:
6060:
6059:
6057:
6055:
6043:
6037:
6036:
6034:
6032:
6020:
6014:
6013:
6002:
5996:
5995:
5993:
5991:
5975:
5969:
5968:
5966:
5964:
5954:
5948:
5947:
5945:
5943:
5928:
5922:
5921:
5909:
5903:
5902:
5895:
5889:
5888:
5886:
5880:. Archived from
5879:
5870:
5864:
5859:
5853:
5852:
5850:
5848:
5838:
5832:
5831:
5829:
5827:
5813:
5807:
5806:
5804:
5802:
5793:. Archived from
5780:
5774:
5773:
5765:
5759:
5758:
5756:
5754:
5730:
5724:
5723:
5697:
5691:
5690:
5656:
5650:
5649:
5647:
5645:
5639:
5628:
5620:
5614:
5613:
5607:
5599:
5597:
5595:
5580:
5574:
5573:
5567:
5559:
5557:
5555:
5540:
5534:
5533:
5531:
5529:
5524:on 24 March 2012
5523:
5517:. Archived from
5509:(7): 1020–1037.
5499:
5490:
5484:
5483:
5481:
5479:
5464:
5458:
5457:
5446:
5440:
5439:
5432:
5426:
5425:
5414:
5408:
5407:
5405:
5403:
5388:
5382:
5381:
5379:
5377:
5363:
5357:
5356:
5354:
5352:
5338:
5332:
5331:
5329:
5327:
5322:. 7 January 2013
5312:
5306:
5305:
5303:
5301:
5290:
5284:
5283:
5282:
5280:
5247:
5241:
5240:
5238:
5236:
5225:
5219:
5218:
5216:
5214:
5195:
5189:
5188:
5186:
5184:
5173:
5167:
5166:
5164:
5162:
5157:
5147:
5145:10.17487/RFC4987
5127:
5121:
5120:
5113:"Slow HTTP Test"
5108:
5102:
5101:
5076:(5): 1031–1043.
5065:
5056:
5055:
5052:NetScout Systems
5044:
5038:
5037:
4995:
4989:
4988:
4986:
4984:
4975:. Archived from
4967:"CVE-2019-11479"
4963:
4957:
4956:
4954:
4952:
4930:
4924:
4923:
4916:
4910:
4909:
4881:
4865:
4859:
4858:
4830:
4821:
4820:
4818:
4816:
4805:
4799:
4798:
4796:
4789:
4780:
4774:
4773:
4765:
4759:
4758:
4722:
4716:
4715:
4713:
4711:
4700:
4694:
4693:
4691:
4689:
4672:
4666:
4665:
4663:
4661:
4643:
4637:
4636:
4634:
4632:
4621:
4615:
4614:
4606:
4600:
4599:
4597:
4595:
4589:
4582:
4573:
4567:
4566:
4555:
4549:
4548:
4546:
4544:
4529:
4523:
4522:
4510:
4504:
4503:
4501:
4499:
4484:
4478:
4477:
4475:
4473:
4461:
4455:
4454:
4452:
4450:
4434:
4428:
4427:
4425:
4423:
4418:on 3 August 2007
4414:. Archived from
4403:
4397:
4396:
4394:
4392:
4378:
4369:
4368:
4366:
4364:
4345:
4339:
4338:
4302:
4296:
4295:
4293:
4291:
4272:
4266:
4265:
4263:
4261:
4241:
4235:
4234:
4232:
4230:
4210:
4204:
4203:
4201:
4199:
4180:
4174:
4173:
4168:. Archived from
4162:
4156:
4155:
4153:
4151:
4145:
4134:
4126:
4120:
4119:
4117:
4115:
4103:
4097:
4096:
4094:
4092:
4080:
4074:
4073:
4071:
4069:
4058:
4052:
4051:
4049:
4047:
4032:
4026:
4025:
4013:
4007:
4006:
3994:
3988:
3987:
3985:
3983:
3968:
3962:
3961:
3959:
3957:
3941:
3935:
3934:
3916:
3910:
3909:
3891:
3885:
3884:
3867:
3861:
3860:
3849:
3843:
3836:
3830:
3829:
3827:
3825:
3809:
3800:
3799:
3797:
3795:
3775:
3769:
3768:
3766:
3764:
3729:
3723:
3722:
3697:(4): 1580–1592.
3682:
3676:
3675:
3673:
3671:
3656:
3650:
3649:
3647:
3645:
3636:. Archived from
3625:
3619:
3618:
3616:
3614:
3609:. Softpedia News
3602:
3596:
3595:
3577:
3562:
3561:
3559:
3557:
3537:
3531:
3530:
3518:
3512:
3511:
3508:blogs.akamai.com
3500:
3494:
3493:
3488:. Archived from
3477:
3468:
3467:
3465:
3463:
3444:
3438:
3437:
3419:
3413:
3412:
3402:
3378:
3372:
3371:
3343:
3323:
3317:
3316:
3288:
3282:
3281:
3279:
3277:
3271:
3256:
3248:
3242:
3241:
3231:
3223:
3193:
3187:
3186:
3174:
3168:
3167:
3151:
3145:
3144:
3126:
3120:
3119:
3111:
3102:
3101:
3099:
3097:
3086:
3080:
3079:
3069:
3061:
3035:
3029:
3028:
3026:
3024:
3018:
3011:
3002:
2993:
2992:
2990:
2988:
2974:
2968:
2967:
2965:
2963:
2948:
2942:
2941:
2939:
2937:
2922:
2916:
2915:
2913:
2911:
2905:SWI swissinfo.ch
2896:
2890:
2889:
2888:. 6 August 2023.
2882:
2876:
2875:
2864:
2858:
2857:
2855:
2853:
2838:
2832:
2831:
2829:
2827:
2812:
2806:
2805:
2803:
2801:
2786:
2777:
2776:
2774:
2772:
2757:
2751:
2750:
2739:
2733:
2732:
2730:
2728:
2713:
2707:
2706:
2704:
2702:
2687:
2681:
2680:
2678:
2676:
2661:
2655:
2654:
2652:
2650:
2638:
2632:
2631:
2629:
2627:
2618:. Archived from
2608:
2602:
2601:
2599:
2597:
2585:
2579:
2578:
2567:
2561:
2560:
2549:
2543:
2542:
2540:
2538:
2520:
2514:
2513:
2511:
2509:
2494:
2488:
2487:
2475:
2469:
2468:
2466:
2464:
2453:
2436:
2431:, this targeted
2421:
2415:
2408:
2351:
2307:
2298:
2246:Hit-and-run DDoS
1837:processing power
1763:scrubbing center
1509:Teardrop attacks
1475:Slow read attack
1433:integer overflow
1161:
1122:Reflected attack
902:HTTP POST header
742:Slow DoS attacks
537:Method of attack
420:
419:
380:slow DoS attacks
332:
321:
313:
264:
261:
243:
236:
214:payment gateways
132:
125:
121:
118:
112:
110:
69:
45:
37:
21:
7049:
7048:
7044:
7043:
7042:
7040:
7039:
7038:
7009:
7008:
7007:
7002:
6852:
6552:
6540:
6531:Copy protection
6521:Mobile security
6452:
6447:
6364:
6359:
6342:
6333:
6331:
6327:
6320:
6315:
6311:
6309:Further reading
6306:
6305:
6296:
6295:
6291:
6281:
6279:
6271:
6270:
6266:
6256:
6254:
6246:
6245:
6241:
6228:
6227:
6223:
6210:
6209:
6205:
6191:
6189:
6180:
6179:
6175:
6166:. 2 July 2019.
6162:
6161:
6157:
6147:
6145:
6140:
6139:
6135:
6125:
6123:
6115:
6114:
6110:
6097:
6096:
6092:
6082:
6080:
6068:
6067:
6063:
6053:
6051:
6045:
6044:
6040:
6030:
6028:
6022:
6021:
6017:
6004:
6003:
5999:
5989:
5987:
5978:Plocek, Keith.
5977:
5976:
5972:
5962:
5960:
5956:
5955:
5951:
5941:
5939:
5930:
5929:
5925:
5911:
5910:
5906:
5897:
5896:
5892:
5884:
5877:
5873:Suzen, Mehmet.
5872:
5871:
5867:
5860:
5856:
5846:
5844:
5840:
5839:
5835:
5825:
5823:
5815:
5814:
5810:
5800:
5798:
5782:
5781:
5777:
5767:
5766:
5762:
5752:
5750:
5732:
5731:
5727:
5720:
5699:
5698:
5694:
5679:
5658:
5657:
5653:
5643:
5641:
5637:
5626:
5622:
5621:
5617:
5600:
5593:
5591:
5582:
5581:
5577:
5560:
5553:
5551:
5542:
5541:
5537:
5527:
5525:
5521:
5497:
5492:
5491:
5487:
5477:
5475:
5466:
5465:
5461:
5456:. 28 June 2017.
5448:
5447:
5443:
5434:
5433:
5429:
5416:
5415:
5411:
5401:
5399:
5390:
5389:
5385:
5375:
5373:
5365:
5364:
5360:
5350:
5348:
5340:
5339:
5335:
5325:
5323:
5314:
5313:
5309:
5299:
5297:
5292:
5291:
5287:
5278:
5276:
5274:
5249:
5248:
5244:
5234:
5232:
5227:
5226:
5222:
5212:
5210:
5197:
5196:
5192:
5182:
5180:
5175:
5174:
5170:
5160:
5158:
5129:
5128:
5124:
5110:
5109:
5105:
5067:
5066:
5059:
5046:
5045:
5041:
5026:
4997:
4996:
4992:
4982:
4980:
4979:on 21 June 2019
4965:
4964:
4960:
4950:
4948:
4947:on 19 June 2019
4932:
4931:
4927:
4918:
4917:
4913:
4898:
4879:10.1.1.307.4107
4867:
4866:
4862:
4832:
4831:
4824:
4814:
4812:
4807:
4806:
4802:
4794:
4787:
4782:
4781:
4777:
4767:
4766:
4762:
4747:
4724:
4723:
4719:
4709:
4707:
4702:
4701:
4697:
4687:
4685:
4674:
4673:
4669:
4659:
4657:
4645:
4644:
4640:
4630:
4628:
4623:
4622:
4618:
4608:
4607:
4603:
4593:
4591:
4590:on 4 March 2016
4587:
4580:
4575:
4574:
4570:
4557:
4556:
4552:
4542:
4540:
4531:
4530:
4526:
4512:
4511:
4507:
4497:
4495:
4486:
4485:
4481:
4471:
4469:
4463:
4462:
4458:
4448:
4446:
4436:
4435:
4431:
4421:
4419:
4405:
4404:
4400:
4390:
4388:
4380:
4379:
4372:
4362:
4360:
4347:
4346:
4342:
4304:
4303:
4299:
4289:
4287:
4286:on 5 March 2019
4274:
4273:
4269:
4259:
4257:
4243:
4242:
4238:
4228:
4226:
4212:
4211:
4207:
4197:
4195:
4182:
4181:
4177:
4164:
4163:
4159:
4149:
4147:
4143:
4132:
4128:
4127:
4123:
4113:
4111:
4105:
4104:
4100:
4090:
4088:
4082:
4081:
4077:
4067:
4065:
4060:
4059:
4055:
4045:
4043:
4034:
4033:
4029:
4015:
4014:
4010:
4003:The Hacker News
3996:
3995:
3991:
3981:
3979:
3970:
3969:
3965:
3955:
3953:
3943:
3942:
3938:
3931:
3918:
3917:
3913:
3906:
3893:
3892:
3888:
3881:
3869:
3868:
3864:
3851:
3850:
3846:
3837:
3833:
3823:
3821:
3811:
3810:
3803:
3793:
3791:
3777:
3776:
3772:
3762:
3760:
3731:
3730:
3726:
3684:
3683:
3679:
3669:
3667:
3658:
3657:
3653:
3643:
3641:
3627:
3626:
3622:
3612:
3610:
3604:
3603:
3599:
3592:
3579:
3578:
3565:
3555:
3553:
3539:
3538:
3534:
3527:Cloudflare Blog
3520:
3519:
3515:
3502:
3501:
3497:
3479:
3478:
3471:
3461:
3459:
3446:
3445:
3441:
3434:
3421:
3420:
3416:
3380:
3379:
3375:
3360:
3325:
3324:
3320:
3290:
3289:
3285:
3275:
3273:
3269:
3254:
3250:
3249:
3245:
3224:
3212:
3195:
3194:
3190:
3176:
3175:
3171:
3153:
3152:
3148:
3141:
3128:
3127:
3123:
3113:
3112:
3105:
3095:
3093:
3088:
3087:
3083:
3062:
3050:
3037:
3036:
3032:
3022:
3020:
3016:
3009:
3004:
3003:
2996:
2986:
2984:
2976:
2975:
2971:
2961:
2959:
2950:
2949:
2945:
2935:
2933:
2924:
2923:
2919:
2909:
2907:
2898:
2897:
2893:
2884:
2883:
2879:
2874:. 10 July 2023.
2866:
2865:
2861:
2851:
2849:
2840:
2839:
2835:
2825:
2823:
2814:
2813:
2809:
2799:
2797:
2788:
2787:
2780:
2770:
2768:
2759:
2758:
2754:
2741:
2740:
2736:
2726:
2724:
2715:
2714:
2710:
2700:
2698:
2689:
2688:
2684:
2674:
2672:
2663:
2662:
2658:
2648:
2646:
2640:
2639:
2635:
2625:
2623:
2610:
2609:
2605:
2595:
2593:
2587:
2586:
2582:
2577:on 13 May 2014.
2569:
2568:
2564:
2551:
2550:
2546:
2536:
2534:
2524:Prince, Matthew
2522:
2521:
2517:
2507:
2505:
2496:
2495:
2491:
2477:
2476:
2472:
2462:
2460:
2455:
2454:
2450:
2445:
2440:
2439:
2429:teardrop attack
2422:
2418:
2410:The -t flag on
2409:
2405:
2400:
2395:
2349:
2317:Paper terrorism
2305:
2296:
2175:
2167:Occupy protests
2093:
2071:
2043:
2033:
2028:
1960:Slashdot effect
1942:
1933:
1924:Martian packets
1920:bogon filtering
1908:delayed binding
1904:traffic shaping
1892:
1871:
1858:
1849:
1841:circuit breaker
1826:
1806:
1793:
1783:and as part of
1777:
1759:cleaning center
1755:
1749:the following.
1746:
1744:DDoS mitigation
1740:
1721:
1683:
1667:
1651:
1568:
1559:fragment offset
1521:teardrop attack
1517:
1511:
1495:
1486:
1477:
1461:
1421:
1412:
1383:
1152:
1124:
1095:vulnerabilities
1082:
1058:
1052:
1008:
957:
937:
898:
885:
840:fraggle attacks
779:
766:
750:cloud computing
716:
663:
658:
641:unusually slow
631:
619:
602:
596:
564:DDoS mitigation
552:
539:
525:project at the
511:
486:
466:
422:
418:Distributed DoS
417:
416:
409:
364:Anonymous Sudan
330:
319:
311:
292:Las Vegas Strip
265:
259:
256:
249:needs expansion
234:
177:connected to a
133:
122:
116:
113:
70:
68:
58:
46:
35:
28:
23:
22:
15:
12:
11:
5:
7047:
7045:
7037:
7036:
7031:
7026:
7021:
7011:
7010:
7004:
7003:
7001:
7000:
6998:Site isolation
6995:
6990:
6989:
6988:
6982:
6972:
6971:
6970:
6965:
6954:
6949:
6944:
6939:
6934:
6929:
6928:
6927:
6922:
6912:
6911:
6910:
6905:
6904:
6903:
6896:Authentication
6888:
6887:
6886:
6885:
6884:
6874:
6871:
6860:
6858:
6854:
6853:
6851:
6850:
6845:
6840:
6835:
6830:
6825:
6820:
6815:
6810:
6805:
6800:
6795:
6790:
6785:
6780:
6775:
6770:
6765:
6760:
6755:
6750:
6749:
6748:
6738:
6733:
6728:
6723:
6718:
6713:
6708:
6703:
6698:
6696:Email spoofing
6693:
6688:
6683:
6678:
6673:
6668:
6663:
6658:
6653:
6648:
6643:
6638:
6636:DOM clobbering
6633:
6628:
6623:
6618:
6616:Code injection
6613:
6608:
6607:
6606:
6601:
6596:
6591:
6583:
6578:
6573:
6568:
6562:
6560:
6554:
6553:
6543:
6541:
6539:
6538:
6533:
6528:
6523:
6518:
6513:
6508:
6503:
6498:
6496:Cyberterrorism
6493:
6488:
6487:
6486:
6484:Computer fraud
6481:
6471:
6466:
6460:
6458:
6454:
6453:
6448:
6446:
6445:
6438:
6431:
6423:
6417:
6416:
6410:
6404:
6398:
6392:
6386:
6381:
6375:
6363:
6362:External links
6360:
6358:
6357:
6352:
6340:
6312:
6310:
6307:
6304:
6303:
6289:
6264:
6239:
6221:
6203:
6173:
6155:
6133:
6108:
6090:
6061:
6038:
6015:
5997:
5970:
5949:
5923:
5904:
5890:
5865:
5854:
5833:
5808:
5797:on 2 July 2014
5775:
5760:
5725:
5718:
5692:
5677:
5651:
5631:SprintLabs.com
5615:
5575:
5535:
5485:
5474:. 28 June 2017
5459:
5441:
5427:
5409:
5396:Blog | Imperva
5383:
5358:
5333:
5307:
5285:
5272:
5242:
5220:
5190:
5168:
5136:Tools.ietf.org
5122:
5103:
5057:
5039:
5024:
4990:
4958:
4925:
4920:"R-u-dead-yet"
4911:
4897:978-1581137354
4896:
4860:
4822:
4800:
4775:
4760:
4745:
4717:
4695:
4667:
4656:. 8 March 2022
4638:
4616:
4601:
4568:
4550:
4524:
4505:
4479:
4456:
4429:
4398:
4370:
4340:
4297:
4267:
4250:Google Patents
4236:
4219:Google Patents
4205:
4175:
4157:
4121:
4098:
4075:
4053:
4041:The Intercept_
4027:
4008:
3989:
3963:
3952:on 15 May 2008
3936:
3929:
3911:
3904:
3886:
3879:
3862:
3844:
3831:
3801:
3770:
3724:
3677:
3651:
3634:SC Magazine UK
3620:
3597:
3591:978-1329063945
3590:
3563:
3532:
3513:
3495:
3469:
3439:
3432:
3414:
3393:(3): 369–376.
3373:
3358:
3318:
3307:(4): 103–104.
3283:
3243:
3210:
3188:
3169:
3146:
3139:
3121:
3103:
3081:
3049:978-0128053997
3048:
3030:
2994:
2969:
2943:
2917:
2891:
2877:
2859:
2833:
2807:
2778:
2765:threatpost.com
2752:
2734:
2723:. 18 June 2020
2708:
2682:
2656:
2641:Smith, Steve.
2633:
2603:
2580:
2562:
2544:
2515:
2489:
2470:
2447:
2446:
2444:
2441:
2438:
2437:
2416:
2402:
2401:
2399:
2396:
2394:
2393:
2387:
2381:
2375:
2370:
2364:
2358:
2355:Virtual sit-in
2352:
2343:
2337:
2332:
2326:
2323:Project Shield
2320:
2314:
2308:
2299:
2290:
2285:
2279:
2273:
2267:
2261:
2255:
2249:
2243:
2237:
2231:
2225:
2219:
2213:
2207:
2201:
2195:
2189:
2183:
2176:
2174:
2171:
2163:whitehouse.gov
2152:
2151:
2143:
2132:United Kingdom
2124:
2070:
2067:
2032:
2029:
2027:
2024:
2009:went missing,
1952:computer virus
1941:
1938:
1932:
1929:
1891:
1888:
1870:
1867:
1857:
1854:
1848:
1845:
1825:
1822:
1805:
1802:
1792:
1789:
1776:
1773:
1754:
1751:
1742:Main article:
1739:
1736:
1720:
1717:
1682:
1679:
1666:
1663:
1650:
1647:
1627:867-5309/Jenny
1606:
1605:
1599:
1591:
1567:
1564:
1510:
1507:
1494:
1491:
1485:
1482:
1476:
1473:
1460:
1457:
1420:
1417:
1411:
1408:
1382:
1379:
1355:
1354:
1352:
1349:
1343:
1342:
1340:
1337:
1335:Steam Protocol
1331:
1330:
1328:
1325:
1319:
1318:
1316:
1313:
1307:
1306:
1304:
1301:
1295:
1294:
1292:
1289:
1285:
1284:
1282:
1279:
1273:
1272:
1269:
1266:
1260:
1259:
1256:
1253:
1247:
1246:
1244:
1241:
1235:
1234:
1232:
1229:
1223:
1222:
1220:
1217:
1211:
1210:
1207:
1204:
1198:
1197:
1194:
1191:
1185:
1184:
1182:
1181:2,200,000,000
1179:
1172:
1171:
1168:
1165:
1151:
1148:
1123:
1120:
1081:
1078:
1051:
1048:
1007:
1004:
956:
953:
936:
933:
911:Content-Length
906:Content-Length
897:
894:
884:
883:DDoS extortion
881:
848:Script kiddies
808:client program
778:
775:
765:
762:
715:
712:
683:client program
662:
659:
657:
654:
653:
652:
649:
646:
630:
627:
618:
615:
598:Main article:
595:
592:
591:
590:
587:
584:
581:
578:
575:
551:
548:
538:
535:
510:
507:
485:
482:
465:
462:
421:
414:
408:
405:
316:Arbor Networks
312:2.54 Tb/s
267:
266:
246:
244:
233:
230:
135:
134:
49:
47:
40:
26:
24:
14:
13:
10:
9:
6:
4:
3:
2:
7046:
7035:
7032:
7030:
7027:
7025:
7022:
7020:
7017:
7016:
7014:
6999:
6996:
6994:
6991:
6986:
6983:
6981:
6978:
6977:
6976:
6973:
6969:
6966:
6963:
6960:
6959:
6958:
6955:
6953:
6950:
6948:
6945:
6943:
6940:
6938:
6935:
6933:
6930:
6926:
6923:
6921:
6918:
6917:
6916:
6913:
6909:
6908:Authorization
6906:
6902:
6899:
6898:
6897:
6894:
6893:
6892:
6889:
6883:
6880:
6879:
6878:
6875:
6872:
6870:
6869:Secure coding
6867:
6866:
6865:
6862:
6861:
6859:
6855:
6849:
6846:
6844:
6841:
6839:
6838:SQL injection
6836:
6834:
6831:
6829:
6826:
6824:
6821:
6819:
6818:Vulnerability
6816:
6814:
6811:
6809:
6806:
6804:
6803:Trojan horses
6801:
6799:
6798:Software bugs
6796:
6794:
6791:
6789:
6786:
6784:
6781:
6779:
6776:
6774:
6771:
6769:
6766:
6764:
6761:
6759:
6756:
6754:
6751:
6747:
6744:
6743:
6742:
6739:
6737:
6734:
6732:
6729:
6727:
6724:
6722:
6719:
6717:
6714:
6712:
6709:
6707:
6704:
6702:
6699:
6697:
6694:
6692:
6689:
6687:
6686:Eavesdropping
6684:
6682:
6679:
6677:
6676:Data scraping
6674:
6672:
6669:
6667:
6664:
6662:
6659:
6657:
6654:
6652:
6649:
6647:
6646:Cryptojacking
6644:
6642:
6639:
6637:
6634:
6632:
6629:
6627:
6624:
6622:
6619:
6617:
6614:
6612:
6609:
6605:
6602:
6600:
6597:
6595:
6592:
6590:
6587:
6586:
6584:
6582:
6579:
6577:
6574:
6572:
6569:
6567:
6564:
6563:
6561:
6559:
6555:
6547:
6537:
6534:
6532:
6529:
6527:
6524:
6522:
6519:
6517:
6514:
6512:
6509:
6507:
6504:
6502:
6499:
6497:
6494:
6492:
6489:
6485:
6482:
6480:
6477:
6476:
6475:
6472:
6470:
6467:
6465:
6462:
6461:
6459:
6455:
6451:
6444:
6439:
6437:
6432:
6430:
6425:
6424:
6421:
6414:
6411:
6408:
6405:
6402:
6399:
6396:
6393:
6390:
6387:
6385:
6382:
6379:
6376:
6373:
6369:
6366:
6365:
6361:
6356:
6353:
6349:
6345:
6341:
6326:
6319:
6314:
6313:
6308:
6299:
6293:
6290:
6278:
6274:
6268:
6265:
6253:
6249:
6243:
6240:
6235:
6231:
6225:
6222:
6217:
6213:
6207:
6204:
6200:
6188:
6184:
6177:
6174:
6169:
6165:
6159:
6156:
6143:
6137:
6134:
6122:
6118:
6112:
6109:
6104:
6100:
6094:
6091:
6079:
6075:
6071:
6065:
6062:
6049:
6042:
6039:
6026:
6019:
6016:
6011:
6007:
6001:
5998:
5985:
5981:
5974:
5971:
5959:
5953:
5950:
5937:
5933:
5927:
5924:
5919:
5915:
5908:
5905:
5900:
5894:
5891:
5883:
5876:
5869:
5866:
5863:
5858:
5855:
5843:
5837:
5834:
5822:
5818:
5812:
5809:
5796:
5792:
5791:
5790:Computerworld
5786:
5779:
5776:
5771:
5764:
5761:
5748:
5744:
5740:
5736:
5729:
5726:
5721:
5715:
5711:
5707:
5703:
5696:
5693:
5688:
5684:
5680:
5674:
5670:
5666:
5662:
5655:
5652:
5636:
5632:
5625:
5619:
5616:
5611:
5605:
5589:
5585:
5579:
5576:
5571:
5565:
5549:
5545:
5539:
5536:
5520:
5516:
5512:
5508:
5505:
5504:
5496:
5489:
5486:
5473:
5469:
5463:
5460:
5455:
5451:
5445:
5442:
5437:
5431:
5428:
5423:
5419:
5413:
5410:
5398:. 14 May 2018
5397:
5393:
5387:
5384:
5372:
5368:
5362:
5359:
5347:
5346:Cisco Systems
5343:
5337:
5334:
5321:
5317:
5311:
5308:
5295:
5289:
5286:
5275:
5269:
5265:
5261:
5257:
5253:
5246:
5243:
5230:
5224:
5221:
5208:
5204:
5200:
5194:
5191:
5178:
5172:
5169:
5156:
5151:
5146:
5141:
5137:
5133:
5126:
5123:
5118:
5114:
5107:
5104:
5099:
5095:
5091:
5087:
5083:
5079:
5075:
5071:
5064:
5062:
5058:
5053:
5049:
5043:
5040:
5035:
5031:
5027:
5021:
5017:
5013:
5009:
5005:
5001:
4994:
4991:
4978:
4974:
4973:
4968:
4962:
4959:
4946:
4942:
4940:
4935:
4929:
4926:
4921:
4915:
4912:
4907:
4903:
4899:
4893:
4889:
4885:
4880:
4875:
4871:
4864:
4861:
4856:
4852:
4848:
4844:
4840:
4836:
4829:
4827:
4823:
4810:
4804:
4801:
4793:
4786:
4779:
4776:
4771:
4764:
4761:
4756:
4752:
4748:
4746:9781450332132
4742:
4738:
4734:
4730:
4729:
4721:
4718:
4705:
4699:
4696:
4683:
4682:
4677:
4671:
4668:
4655:
4653:
4648:
4642:
4639:
4626:
4620:
4617:
4612:
4605:
4602:
4586:
4579:
4572:
4569:
4564:
4560:
4554:
4551:
4538:
4534:
4528:
4525:
4520:
4516:
4509:
4506:
4494:
4490:
4483:
4480:
4467:
4460:
4457:
4444:
4440:
4433:
4430:
4417:
4413:
4409:
4402:
4399:
4387:
4383:
4377:
4375:
4371:
4358:
4354:
4350:
4344:
4341:
4336:
4332:
4328:
4324:
4320:
4316:
4312:
4308:
4301:
4298:
4285:
4281:
4277:
4271:
4268:
4255:
4251:
4247:
4240:
4237:
4224:
4220:
4216:
4209:
4206:
4193:
4189:
4185:
4179:
4176:
4171:
4167:
4161:
4158:
4142:
4138:
4131:
4125:
4122:
4110:. SC Magazine
4109:
4102:
4099:
4086:
4079:
4076:
4063:
4057:
4054:
4042:
4038:
4031:
4028:
4023:
4022:incapsula.com
4019:
4012:
4009:
4004:
4000:
3993:
3990:
3978:
3974:
3967:
3964:
3951:
3947:
3940:
3937:
3932:
3926:
3922:
3915:
3912:
3907:
3901:
3897:
3890:
3887:
3882:
3876:
3872:
3866:
3863:
3858:
3854:
3848:
3845:
3841:
3835:
3832:
3819:
3815:
3808:
3806:
3802:
3789:
3785:
3781:
3774:
3771:
3759:
3755:
3751:
3747:
3743:
3739:
3735:
3728:
3725:
3720:
3716:
3712:
3708:
3704:
3700:
3696:
3692:
3688:
3681:
3678:
3666:
3662:
3655:
3652:
3639:
3635:
3631:
3624:
3621:
3608:
3601:
3598:
3593:
3587:
3583:
3576:
3574:
3572:
3570:
3568:
3564:
3551:
3547:
3543:
3536:
3533:
3528:
3524:
3517:
3514:
3509:
3505:
3499:
3496:
3491:
3487:
3483:
3476:
3474:
3470:
3457:
3453:
3449:
3443:
3440:
3435:
3433:9781461472056
3429:
3425:
3418:
3415:
3410:
3406:
3401:
3396:
3392:
3388:
3384:
3377:
3374:
3369:
3365:
3361:
3355:
3351:
3347:
3342:
3337:
3333:
3329:
3322:
3319:
3314:
3310:
3306:
3302:
3298:
3294:
3287:
3284:
3268:
3264:
3260:
3253:
3247:
3244:
3239:
3235:
3229:
3221:
3217:
3213:
3211:9781498729659
3207:
3203:
3199:
3192:
3189:
3184:
3180:
3173:
3170:
3165:
3161:
3157:
3150:
3147:
3142:
3140:9788132202776
3136:
3132:
3125:
3122:
3117:
3110:
3108:
3104:
3091:
3085:
3082:
3077:
3073:
3067:
3059:
3055:
3051:
3045:
3041:
3034:
3031:
3015:
3008:
3001:
2999:
2995:
2983:
2979:
2973:
2970:
2957:
2953:
2947:
2944:
2931:
2927:
2921:
2918:
2906:
2902:
2895:
2892:
2887:
2881:
2878:
2873:
2869:
2863:
2860:
2848:
2844:
2837:
2834:
2821:
2817:
2811:
2808:
2796:
2792:
2785:
2783:
2779:
2766:
2762:
2756:
2753:
2748:
2744:
2738:
2735:
2722:
2718:
2712:
2709:
2697:
2693:
2686:
2683:
2671:
2667:
2660:
2657:
2644:
2637:
2634:
2621:
2617:
2613:
2607:
2604:
2591:
2584:
2581:
2576:
2572:
2566:
2563:
2558:
2554:
2548:
2545:
2533:
2529:
2525:
2519:
2516:
2503:
2499:
2493:
2490:
2485:
2481:
2474:
2471:
2458:
2452:
2449:
2442:
2434:
2430:
2426:
2425:Windows Vista
2420:
2417:
2413:
2407:
2404:
2397:
2391:
2388:
2385:
2382:
2379:
2376:
2374:
2371:
2368:
2367:Radio jamming
2365:
2362:
2359:
2356:
2353:
2347:
2344:
2341:
2338:
2336:
2333:
2330:
2327:
2324:
2321:
2318:
2315:
2312:
2309:
2303:
2300:
2294:
2291:
2289:
2286:
2283:
2280:
2277:
2274:
2271:
2268:
2265:
2262:
2259:
2258:Infinite loop
2256:
2253:
2250:
2247:
2244:
2241:
2238:
2235:
2232:
2229:
2226:
2223:
2220:
2217:
2214:
2211:
2208:
2205:
2202:
2199:
2196:
2193:
2190:
2187:
2184:
2181:
2178:
2177:
2172:
2170:
2168:
2164:
2160:
2157:
2148:
2144:
2141:
2137:
2133:
2129:
2125:
2122:
2118:
2114:
2110:
2106:
2105:
2104:
2102:
2098:
2092:
2088:
2080:
2075:
2068:
2066:
2064:
2060:
2056:
2051:
2048:
2042:
2038:
2030:
2025:
2023:
2021:
2016:
2015:crowdsourcing
2012:
2008:
2004:
2000:
1995:
1993:
1992:search engine
1989:
1984:
1980:
1975:
1973:
1969:
1965:
1961:
1955:
1953:
1948:
1939:
1937:
1930:
1928:
1925:
1921:
1917:
1913:
1909:
1905:
1901:
1900:rate limiting
1897:
1889:
1887:
1885:
1880:
1876:
1875:rate-limiting
1868:
1866:
1863:
1855:
1853:
1846:
1844:
1842:
1838:
1834:
1830:
1823:
1821:
1819:
1815:
1811:
1803:
1801:
1799:
1790:
1788:
1786:
1782:
1774:
1772:
1769:
1764:
1760:
1752:
1750:
1745:
1737:
1735:
1733:
1729:
1725:
1718:
1716:
1714:
1710:
1706:
1705:UDP port 1900
1702:
1699:
1698:
1692:
1688:
1680:
1678:
1676:
1672:
1664:
1662:
1660:
1656:
1648:
1646:
1644:
1640:
1636:
1632:
1628:
1624:
1619:
1618:telemarketers
1615:
1611:
1603:
1600:
1596:
1592:
1588:
1587:
1586:
1584:
1580:
1576:
1572:
1571:Voice over IP
1565:
1563:
1560:
1556:
1552:
1548:
1544:
1540:
1536:
1533:
1529:
1526:
1522:
1516:
1508:
1506:
1504:
1500:
1492:
1490:
1483:
1481:
1474:
1472:
1470:
1466:
1458:
1456:
1454:
1450:
1446:
1442:
1438:
1434:
1430:
1426:
1423:Manipulating
1418:
1416:
1409:
1407:
1405:
1401:
1397:
1392:
1391:computer worm
1388:
1380:
1378:
1376:
1372:
1368:
1364:
1361:
1353:
1350:
1348:
1345:
1344:
1341:
1338:
1336:
1333:
1332:
1329:
1326:
1324:
1321:
1320:
1317:
1314:
1312:
1309:
1308:
1305:
1302:
1300:
1297:
1296:
1293:
1290:
1287:
1286:
1283:
1280:
1278:
1275:
1274:
1270:
1267:
1265:
1262:
1261:
1257:
1254:
1252:
1249:
1248:
1245:
1242:
1240:
1237:
1236:
1233:
1230:
1228:
1225:
1224:
1221:
1218:
1216:
1213:
1212:
1208:
1205:
1203:
1200:
1199:
1195:
1192:
1190:
1187:
1186:
1183:
1180:
1177:
1174:
1173:
1169:
1166:
1163:
1162:
1156:
1150:Amplification
1149:
1147:
1145:
1144:Smurf attacks
1141:
1137:
1133:
1129:
1121:
1119:
1117:
1113:
1108:
1104:
1100:
1096:
1092:
1088:
1079:
1077:
1075:
1071:
1070:puppet master
1067:
1063:
1057:
1049:
1047:
1045:
1041:
1037:
1033:
1029:
1025:
1021:
1017:
1013:
1005:
1003:
1001:
997:
996:Ping of death
993:
989:
986:command from
985:
981:
977:
973:
970:
966:
962:
954:
952:
950:
946:
942:
934:
932:
930:
926:
921:
917:
912:
907:
903:
895:
893:
891:
882:
880:
878:
873:
868:
863:
861:
857:
853:
849:
845:
841:
837:
836:smurf attacks
833:
829:
825:
820:
818:
814:
809:
805:
801:
798:containing a
797:
793:
789:
785:
776:
774:
772:
763:
761:
759:
755:
754:banana attack
751:
747:
743:
739:
737:
733:
729:
725:
721:
713:
711:
708:
704:
700:
696:
691:
688:
687:zombie agents
684:
680:
676:
672:
668:
660:
655:
650:
647:
644:
640:
639:
638:
636:
628:
626:
624:
616:
614:
611:
607:
601:
593:
588:
585:
582:
579:
576:
573:
569:
568:
567:
565:
561:
557:
549:
547:
545:
536:
534:
532:
528:
524:
520:
516:
508:
506:
504:
499:
495:
491:
483:
481:
479:
475:
471:
463:
461:
459:
455:
451:
447:
443:
439:
433:
431:
427:
415:
413:
406:
404:
402:
398:
393:
389:
385:
381:
377:
373:
369:
365:
361:
355:
353:
348:
344:
340:
336:
331:2.3 Tb/s
328:
323:
320:1.7 Tb/s
317:
309:
305:
301:
297:
293:
289:
285:
281:
277:
273:
263:
254:
250:
247:This section
245:
242:
238:
237:
231:
229:
227:
224:, as well as
223:
219:
215:
212:
208:
204:
200:
196:
191:
189:
184:
180:
176:
172:
168:
164:
160:
156:
152:
143:
139:
131:
128:
120:
117:February 2024
109:
106:
102:
99:
95:
92:
88:
85:
81:
78: –
77:
73:
72:Find sources:
66:
62:
56:
55:
50:This article
48:
44:
39:
38:
33:
19:
7024:Cyberwarfare
6942:Data masking
6680:
6501:Cyberwarfare
6348:the original
6332:. Retrieved
6325:the original
6292:
6280:. Retrieved
6276:
6267:
6255:. Retrieved
6251:
6242:
6233:
6224:
6215:
6206:
6197:
6192:27 September
6190:. Retrieved
6187:The Register
6176:
6158:
6146:. Retrieved
6136:
6124:. Retrieved
6120:
6111:
6102:
6093:
6081:. Retrieved
6073:
6064:
6052:. Retrieved
6041:
6029:. Retrieved
6018:
6009:
6000:
5988:. Retrieved
5984:the original
5973:
5963:24 September
5961:. Retrieved
5952:
5940:. Retrieved
5935:
5926:
5917:
5907:
5893:
5882:the original
5868:
5857:
5845:. Retrieved
5836:
5824:. Retrieved
5820:
5811:
5799:. Retrieved
5795:the original
5788:
5778:
5763:
5751:. Retrieved
5747:the original
5742:
5738:
5728:
5701:
5695:
5660:
5654:
5642:. Retrieved
5635:the original
5630:
5618:
5592:. Retrieved
5587:
5578:
5552:. Retrieved
5547:
5538:
5526:. Retrieved
5519:the original
5506:
5501:
5488:
5476:. Retrieved
5471:
5462:
5453:
5444:
5430:
5421:
5412:
5400:. Retrieved
5395:
5386:
5374:. Retrieved
5371:Dark Reading
5370:
5361:
5349:. Retrieved
5336:
5326:10 September
5324:. Retrieved
5319:
5310:
5300:10 September
5298:. Retrieved
5288:
5277:, retrieved
5255:
5245:
5233:. Retrieved
5223:
5211:. Retrieved
5207:the original
5202:
5193:
5181:. Retrieved
5179:. CERT. 1998
5171:
5159:. Retrieved
5135:
5125:
5116:
5106:
5073:
5069:
5042:
4999:
4993:
4981:. Retrieved
4977:the original
4970:
4961:
4949:. Retrieved
4945:the original
4937:
4928:
4914:
4869:
4863:
4841:(7): 80–84.
4838:
4834:
4813:. Retrieved
4803:
4792:the original
4778:
4763:
4727:
4720:
4708:. Retrieved
4698:
4686:. Retrieved
4679:
4670:
4658:. Retrieved
4650:
4641:
4629:. Retrieved
4619:
4604:
4592:. Retrieved
4585:the original
4571:
4563:the original
4553:
4541:. Retrieved
4539:. 4 May 2017
4536:
4527:
4519:the original
4508:
4496:. Retrieved
4493:The Register
4492:
4482:
4470:. Retrieved
4459:
4447:. Retrieved
4443:the original
4432:
4420:. Retrieved
4416:the original
4411:
4401:
4391:16 September
4389:. Retrieved
4385:
4361:. Retrieved
4357:the original
4352:
4343:
4310:
4300:
4288:. Retrieved
4284:the original
4279:
4270:
4258:. Retrieved
4249:
4239:
4227:. Retrieved
4218:
4208:
4196:. Retrieved
4187:
4178:
4170:the original
4160:
4148:. Retrieved
4136:
4124:
4114:15 September
4112:. Retrieved
4101:
4091:15 September
4089:. Retrieved
4078:
4068:15 September
4066:. Retrieved
4056:
4044:. Retrieved
4040:
4030:
4021:
4011:
4002:
3992:
3980:. Retrieved
3977:The Register
3976:
3966:
3954:. Retrieved
3950:the original
3939:
3920:
3914:
3895:
3889:
3870:
3865:
3856:
3847:
3839:
3834:
3822:. Retrieved
3818:the original
3792:. Retrieved
3773:
3761:. Retrieved
3741:
3737:
3727:
3694:
3690:
3680:
3668:. Retrieved
3664:
3654:
3642:. Retrieved
3638:the original
3633:
3623:
3611:. Retrieved
3600:
3584:. Lulu.com.
3581:
3554:. Retrieved
3550:the original
3546:Dark Reading
3545:
3535:
3526:
3516:
3507:
3498:
3490:the original
3485:
3460:. Retrieved
3456:the original
3451:
3442:
3426:. Springer.
3423:
3417:
3390:
3386:
3376:
3331:
3327:
3321:
3304:
3300:
3291:Sides, Mor;
3286:
3274:. Retrieved
3258:
3246:
3201:
3191:
3172:
3160:Ars Technica
3159:
3149:
3133:. Springer.
3130:
3124:
3115:
3096:15 September
3094:. Retrieved
3084:
3039:
3033:
3021:. Retrieved
2985:. Retrieved
2981:
2972:
2960:. Retrieved
2955:
2946:
2934:. Retrieved
2929:
2920:
2908:. Retrieved
2904:
2894:
2880:
2871:
2862:
2850:. Retrieved
2846:
2836:
2824:. Retrieved
2819:
2810:
2798:. Retrieved
2794:
2769:. Retrieved
2764:
2755:
2747:SecurityWeek
2746:
2737:
2725:. Retrieved
2720:
2711:
2699:. Retrieved
2696:Ars Technica
2695:
2685:
2675:16 September
2673:. Retrieved
2669:
2659:
2647:. Retrieved
2636:
2624:. Retrieved
2620:the original
2615:
2606:
2596:10 September
2594:. Retrieved
2583:
2575:the original
2565:
2557:the original
2547:
2535:. Retrieved
2531:
2518:
2506:. Retrieved
2501:
2492:
2483:
2473:
2461:. Retrieved
2451:
2428:
2419:
2406:
2153:
2121:DerpTrolling
2094:
2091:DPP v Lennon
2058:
2052:
2044:
2011:DigitalGlobe
1996:
1976:
1956:
1943:
1934:
1912:TCP splicing
1893:
1872:
1859:
1850:
1827:
1818:DNS sinkhole
1813:
1807:
1797:
1794:
1778:
1767:
1762:
1758:
1756:
1747:
1724:ARP spoofing
1722:
1719:ARP spoofing
1700:
1696:
1684:
1668:
1652:
1607:
1590:unreachable.
1569:
1558:
1539:Windows 3.1x
1528:IP fragments
1520:
1518:
1496:
1487:
1478:
1462:
1459:Shrew attack
1437:Kernel panic
1422:
1413:
1396:attacked Dyn
1387:Mirai botnet
1384:
1381:Mirai botnet
1365:
1358:
1153:
1135:
1131:
1125:
1102:
1083:
1069:
1062:peer-to-peer
1059:
1024:corrupt data
1009:
983:
974:
961:smurf attack
958:
948:
944:
938:
915:
910:
905:
899:
886:
864:
828:Stacheldraht
821:
804:Stacheldraht
800:zombie agent
780:
770:
767:
753:
740:
735:
717:
692:
679:Stacheldraht
664:
661:Attack tools
632:
620:
609:
605:
603:
555:
553:
540:
512:
493:
489:
487:
474:cloud-hosted
469:
467:
464:Yo-yo attack
454:SYN flooding
450:UDP flooding
434:
423:
410:
356:
352:nation-state
339:Mirai botnet
324:
308:Google Cloud
270:
257:
253:adding to it
248:
198:
194:
192:
163:cyber-attack
158:
154:
148:
138:
123:
114:
104:
97:
90:
83:
71:
59:Please help
54:verification
51:
6882:Misuse case
6716:Infostealer
6691:Email fraud
6656:Data breach
6491:Cybergeddon
6083:11 December
6050:. Delimiter
5942:11 February
5213:11 December
5117:SourceForge
5016:10722/45910
4613:. ICIR.org.
4363:11 December
4087:. Bloomberg
4046:25 December
3824:11 December
3794:11 December
3670:9 September
3259:Imperva.com
2771:23 December
2727:11 November
2649:20 November
2645:. tqaweekly
2508:5 September
2270:Killer poke
2031:Backscatter
2013:launched a
1990:or another
1728:MAC address
1665:UPnP attack
1635:prank calls
1595:payday loan
1268:4.0 - 54.3
1034:handler in
929:open source
872:SYN cookies
832:IP spoofing
478:autoscaling
211:credit card
203:web servers
199:DDoS attack
7013:Categories
6947:Encryption
6823:Web shells
6763:Ransomware
6711:Hacktivism
6474:Cybercrime
6282:29 January
6257:29 January
6248:"Newsroom"
6148:15 January
6121:unctad.org
6074:Animations
6054:31 January
6031:4 February
5990:20 October
5753:13 January
5644:2 December
5594:30 October
5554:10 January
5528:2 December
5503:Comput. J.
5478:13 October
5279:9 February
5235:2 December
5161:2 December
4652:Cloudflare
4594:4 February
4543:22 January
3982:2 December
3763:19 October
3644:4 February
3556:28 January
3462:28 January
3341:2105.00542
2962:13 January
2936:13 January
2826:13 January
2532:CloudFlare
2443:References
2115:of the US
2101:cybercrime
2087:Cybercrime
2085:See also:
2063:IP address
2047:IP packets
2035:See also:
1814:black hole
1713:Cloudflare
1547:Windows NT
1543:Windows 95
1513:See also:
1453:2019-11479
1451:, CVE-
1449:2019-11478
1447:, CVE-
1445:2019-11477
1419:SACK Panic
1264:BitTorrent
1231:up to 179
1138:) attack.
1112:BrickerBot
1054:See also:
1036:Windows 95
1000:BlackNurse
976:Ping flood
844:SYN floods
792:IP address
335:Cloudflare
226:hacktivism
188:IP address
159:DoS attack
87:newspapers
6778:Shellcode
6773:Scareware
6621:Crimeware
6581:Backdoors
6413:LOIC SLOW
6076:(video).
5826:13 August
5090:0018-9340
4906:173992197
4874:CiteSeerX
4472:22 August
4449:22 August
4422:22 August
4335:110045205
4327:1662-9795
3719:214114645
3711:0824-7935
3409:208093679
3368:233482002
3228:cite book
3220:948286117
3066:cite book
3058:930795667
2987:28 August
2847:The Verge
2626:26 August
2502:Kaspersky
2361:Web shell
2340:SlowDroid
2276:Lace card
2234:Fork bomb
2228:DNS Flood
2192:Black fax
2156:Anonymous
1974:effect".
1884:Cisco IOS
1856:Firewalls
1643:black fax
1633:(such as
1623:area code
1612:. In the
1598:agencies.
1575:telephone
1555:IP header
1499:SYN flood
1493:SYN flood
1189:Memcached
1178:MiCollab
1164:Protocol
1142:attacks (
1103:flashing.
992:bandwidth
988:Unix-like
949:CC attack
852:extortion
817:Anonymous
746:SlowDroid
728:fork bomb
699:Anonymous
671:Slowloris
515:OSI model
426:bandwidth
376:NoName057
300:EarthLink
280:SYN flood
260:July 2017
222:blackmail
151:computing
6952:Firewall
6857:Defenses
6783:Spamming
6768:Rootkits
6741:Phishing
6701:Exploits
6389:cert.org
6168:Archived
6010:BBC News
5918:BBC News
5687:32238160
5604:cite web
5564:cite web
5098:26395831
4855:35958086
4835:Computer
4710:13 April
4660:16 March
4254:Archived
4223:Archived
4213:刘鹏; 郭洋.
4192:Archived
4150:18 March
4141:Archived
3788:Archived
3267:Archived
3183:Archived
3164:Archived
3014:Archived
2721:BBC News
2378:Xor DDoS
2180:BASHLITE
2173:See also
2128:European
2069:Legality
1964:Slashdot
1890:Switches
1862:firewall
1781:switches
1602:Swatting
1281:10 - 50
1099:firmware
724:CPU time
720:exploits
629:Symptoms
610:stresser
600:Stresser
205:such as
183:flooding
171:services
6793:Spyware
6736:Payload
6731:Malware
6671:Viruses
6651:Botnets
6558:Threats
6334:2 March
6277:Europol
6252:Europol
6216:EUROPOL
6126:8 April
5847:15 June
5320:IC3.gov
5183:18 July
4983:21 June
4951:21 June
4815:17 July
4755:2094604
4688:3 March
4537:Radware
4498:7 March
4290:5 March
4280:NetEase
4260:5 March
4229:5 March
4198:5 March
3758:9510043
3613:29 July
3452:Gartner
3263:Imperva
3023:7 March
2910:8 April
2872:Polygon
2852:9 April
2800:7 April
2701:6 March
2412:Windows
2161:on the
2147:Europol
2003:YouTube
1983:Netgear
1869:Routers
1732:gateway
1675:Imperva
1557:is the
1525:mangled
1404:Netflix
1400:Twitter
1347:NetBIOS
1215:CHARGEN
1193:50,000
1087:routers
1032:NetBIOS
1028:WinNuke
916:logical
890:bitcoin
877:TCP SYN
824:botnets
784:Malware
675:malware
430:malware
372:Bitcoin
304:E-Trade
288:DEF CON
232:History
218:Revenge
179:network
161:) is a
101:scholar
6987:(SIEM)
6964:(HIDS)
6848:Zombie
6585:Bombs
6566:Adware
6370:
6103:Kotaku
5801:15 May
5716:
5685:
5675:
5402:29 May
5376:29 May
5351:24 May
5270:
5152:
5096:
5088:
5034:406686
5032:
5022:
4939:Ubuntu
4904:
4894:
4876:
4853:
4753:
4743:
4681:GitHub
4631:8 July
4333:
4325:
3927:
3902:
3877:
3756:
3717:
3709:
3588:
3430:
3407:
3366:
3356:
3218:
3208:
3137:
3056:
3046:
2537:18 May
2463:26 May
2198:Botnet
2097:UNCTAD
1988:Google
1979:D-Link
1968:Reddit
1709:botnet
1537:code.
1532:TCP/IP
1323:SNMPv2
1243:140.3
1219:358.8
1206:556.9
1170:Notes
796:trojan
788:MyDoom
701:. The
667:MyDoom
606:booter
544:botnet
397:Google
392:HTTP/2
343:Yandex
296:Sprint
103:
96:
89:
82:
74:
6833:Worms
6828:Wiper
6746:Voice
6594:Logic
6328:(PDF)
6321:(PDF)
6027:. NPR
5885:(PDF)
5878:(PDF)
5683:S2CID
5638:(PDF)
5627:(PDF)
5522:(PDF)
5498:(PDF)
5203:ZDNet
5094:S2CID
5030:S2CID
4902:S2CID
4851:S2CID
4795:(PDF)
4788:(PDF)
4751:S2CID
4588:(PDF)
4581:(PDF)
4331:S2CID
4144:(PDF)
4133:(PDF)
3956:2 May
3754:S2CID
3715:S2CID
3405:S2CID
3364:S2CID
3336:arXiv
3276:4 May
3270:(PDF)
3255:(PDF)
3017:(PDF)
3010:(PDF)
2670:ZDNet
2616:Cisco
2398:Notes
2384:Zemra
2329:ReDoS
2001:sued
1808:With
1761:or a
1551:Linux
1315:16.3
1303:30.8
1291:33.5
1288:ARMS
1255:63.9
1176:Mitel
1136:DRDoS
1107:brick
927:, an
925:OWASP
572:OSINT
470:yo-yo
407:Types
284:Cisco
272:Panix
207:banks
193:In a
173:of a
167:users
108:JSTOR
94:books
6599:Time
6589:Fork
6372:4732
6336:2011
6284:2019
6259:2019
6194:2019
6150:2014
6128:2024
6085:2013
6056:2018
6033:2016
5992:2010
5965:2024
5944:2012
5849:2024
5828:2018
5803:2010
5755:2010
5714:ISBN
5673:ISBN
5646:2011
5610:link
5596:2001
5570:link
5556:2003
5530:2015
5480:2019
5404:2018
5378:2018
5353:2019
5328:2013
5302:2013
5281:2024
5268:ISBN
5237:2011
5215:2013
5185:2014
5163:2011
5155:4987
5086:ISSN
5020:ISBN
4985:2019
4953:2019
4941:Wiki
4892:ISBN
4817:2013
4741:ISBN
4712:2014
4690:2018
4662:2022
4654:Blog
4633:2014
4596:2016
4545:2019
4500:2009
4474:2007
4451:2007
4424:2007
4393:2019
4365:2013
4323:ISSN
4292:2019
4262:2018
4231:2018
4200:2019
4152:2014
4116:2015
4093:2015
4070:2015
4048:2015
3984:2011
3958:2008
3925:ISBN
3900:ISBN
3875:ISBN
3826:2013
3796:2013
3765:2023
3707:ISSN
3672:2016
3646:2016
3615:2018
3586:ISBN
3558:2014
3464:2014
3428:ISBN
3354:ISBN
3278:2020
3238:link
3234:link
3216:OCLC
3206:ISBN
3135:ISBN
3098:2015
3076:link
3072:link
3054:OCLC
3044:ISBN
3025:2014
2989:2024
2964:2024
2938:2024
2912:2024
2854:2024
2828:2024
2802:2024
2773:2021
2729:2020
2703:2018
2677:2021
2651:2014
2628:2019
2598:2013
2539:2016
2510:2021
2465:2016
2433:SMB2
2089:and
2039:and
1981:and
1972:Digg
1918:and
1877:and
1833:ASIC
1691:DDoS
1637:and
1545:and
1427:and
1385:The
1369:and
1367:SNMP
1351:3.8
1339:5.5
1327:6.3
1299:SSDP
1277:CoAP
1239:QOTD
1066:DC++
1020:ping
1016:ICMP
1006:Nuke
984:ping
980:ping
860:GCHQ
838:and
758:LAND
669:and
633:The
513:The
456:and
220:and
175:host
153:, a
80:news
6604:Zip
6368:RFC
5706:doi
5665:doi
5511:doi
5422:CIS
5260:doi
5150:RFC
5140:doi
5078:doi
5012:hdl
5004:doi
4972:CVE
4884:doi
4843:doi
4733:doi
4315:doi
3746:doi
3699:doi
3395:doi
3346:doi
3309:doi
2126:In
1914:),
1896:ACL
1879:ACL
1768:bad
1655:TTL
1621:+1-
1441:CVE
1371:NTP
1360:DNS
1311:Kad
1227:DNS
1202:NTP
1040:TCP
608:or
554:An
488:An
276:ISP
255:.
209:or
149:In
63:by
7015::
6275:.
6250:.
6232:.
6214:.
6196:.
6185:.
6119:.
6101:.
6072:.
6008:.
5934:.
5916:.
5819:.
5787:.
5741:.
5737:.
5712:.
5681:.
5671:.
5629:.
5606:}}
5602:{{
5586:.
5566:}}
5562:{{
5546:.
5507:53
5500:.
5470:.
5452:.
5420:.
5394:.
5369:.
5344:.
5318:.
5266:,
5254:,
5201:.
5148:.
5138:.
5134:.
5115:.
5092:.
5084:.
5074:62
5072:.
5060:^
5050:.
5028:.
5018:.
5010:.
4969:.
4936:.
4900:.
4890:.
4882:.
4849:.
4839:50
4837:.
4825:^
4749:.
4739:.
4678:.
4649:.
4535:.
4491:.
4410:.
4384:.
4373:^
4351:.
4329:.
4321:.
4309:.
4278:.
4252:.
4248:.
4221:.
4217:.
4190:.
4186:.
4135:.
4039:.
4020:.
4001:.
3975:.
3855:.
3804:^
3786:.
3782:.
3752:.
3742:60
3740:.
3736:.
3713:.
3705:.
3695:36
3693:.
3689:.
3663:.
3632:.
3566:^
3544:.
3525:.
3506:.
3484:.
3472:^
3450:.
3403:.
3389:.
3385:.
3362:.
3352:.
3344:.
3328:Yo
3305:45
3303:.
3299:.
3265:.
3261:.
3257:.
3230:}}
3226:{{
3214:.
3162:.
3158:.
3106:^
3068:}}
3064:{{
3052:.
2997:^
2980:.
2954:.
2928:.
2903:.
2870:.
2845:.
2818:.
2793:.
2781:^
2763:.
2745:.
2719:.
2694:.
2668:.
2614:.
2530:.
2500:.
2482:.
1906:,
1902:,
1616:,
1541:,
1519:A
1497:A
1402:,
1046:.
969:IP
959:A
951:.
945:CC
738:.
468:A
460:.
452:,
403:.
322:.
302:,
298:,
216:.
190:.
6442:e
6435:t
6428:v
6338:.
6286:.
6261:.
6152:.
6130:.
6087:.
6058:.
6035:.
5994:.
5967:.
5946:.
5920:.
5901:.
5851:.
5830:.
5805:.
5772:.
5757:.
5743:7
5722:.
5708::
5689:.
5667::
5648:.
5612:)
5598:.
5572:)
5558:.
5532:.
5513::
5482:.
5424:.
5406:.
5380:.
5355:.
5330:.
5304:.
5262::
5239:.
5217:.
5187:.
5165:.
5142::
5119:.
5100:.
5080::
5054:.
5036:.
5014::
5006::
4987:.
4955:.
4908:.
4886::
4857:.
4845::
4819:.
4772:.
4757:.
4735::
4714:.
4692:.
4664:.
4635:.
4598:.
4547:.
4502:.
4476:.
4453:.
4426:.
4395:.
4367:.
4337:.
4317::
4294:.
4264:.
4233:.
4202:.
4154:.
4118:.
4095:.
4072:.
4050:.
4024:.
4005:.
3986:.
3960:.
3933:.
3908:.
3883:.
3859:.
3828:.
3798:.
3767:.
3748::
3721:.
3701::
3674:.
3648:.
3617:.
3594:.
3560:.
3529:.
3510:.
3466:.
3436:.
3411:.
3397::
3391:6
3370:.
3348::
3338::
3315:.
3311::
3280:.
3240:)
3222:.
3143:.
3118:.
3100:.
3078:)
3060:.
3027:.
2991:.
2966:.
2940:.
2914:.
2856:.
2830:.
2804:.
2775:.
2731:.
2705:.
2679:.
2653:.
2630:.
2600:.
2541:.
2512:.
2486:.
2467:.
2142:.
2081:.
1910:(
1697:k
1443:-
1134:(
262:)
258:(
197:(
157:(
130:)
124:(
119:)
115:(
105:·
98:·
91:·
84:·
57:.
34:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.